
What to look for in a third-party vendor while cutting budgets
At the end of 2022, many companies (83 percent) feared a recession in 2023, with 60 percent of enterprise-level and 45 percent of SMB-level businesses preparing by tightening budgets, reducing non-essential spending, renegotiating payment terms and other strategies. Yet SWZD’s 2023 State of IT Report also found that over 50 percent of companies planned to increase YOY IT spending, with budgets expected to grow 13 percent YOY.
That same report indicated that 23 percent of companies had already implemented -- or planned to form -- strategic partnerships.

Google's journey: From Stanford to Silicon Valley -- a revolution in the digital world
The history of Google, a company that has significantly transformed the digital world, is an inspiring tale of innovation, ambition and an unyielding quest for information. The story unfolds in the heart of Silicon Valley, California, in 1996, where two Stanford University students, Sergey Brin, a Russian immigrant, and Larry Page, crossed paths. Brin was tasked with showing Page around the university.
Despite some initial disagreements, they found common ground in their shared passion for data mining and retrieval. This shared interest would eventually lead to the creation of a search engine that revolutionized the way people interact with the internet.

74 percent of cloud and web applications with PII are vulnerable to exploits
New research reveals a high proportion of vulnerable public cloud, mobile and web applications exposing sensitive data, including unsecured APIs and personal identifiable information (PII).
The study from CyCognito, based on analysis of 3.5 million assets across its enterprise customer base, finds 74 percent of assets with PII are vulnerable to at least one known major exploit, and one in 10 have at least one easily exploitable issue.

Looking over the edge -- how edge computing will impact business decisions [Q&A]
Earlier this year, AT&T's Cybersecurity Insights Report found that business and technology leaders are finally coming together not just to understand the new edge computing ecosystem, but to make more predictable, data-informed business decisions.
We spoke to head of cybersecurity evangelism at AT&T Business, Theresa Lanowitz, to find out more about the edge journey ahead and how it will affect businesses.

Best Windows apps this week
Five-hundred-and-fifty-six in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Windows 11 users may soon uninstall more native applications. Microsoft unlocked the apps Camera, Cortana, Photos, People and Remote Desktop (MSTSC) in the latest development builds.

PNY DUO LINK iOS USB 3.2 Flash Drive: The ultimate storage solution for Apple iPhone
In a world increasingly dominated by mobile devices, the ability to manage and transfer data effortlessly across platforms is crucial. PNY's DUO LINK iOS drive absolutely rises to this challenge. With a Lightning connector tailored for iOS devices and a USB 3.2 Type-A connector for broader compatibility, the DUO LINK ensures that file transfers are not just limited to one platform.
With the DUO LINK iOS drive, gone are the days of frantically searching for storage space during a critical moment or a valuable photo op. The drive provides instant access to your media, allowing you to save precious content on the go. It elegantly removes the need to juggle multiple devices, making travel or day-to-day commuting a breeze.
The future of AI lies in open source
I'm almost getting sick of hearing about AI and its ability to change the world for the better, for the worse, for who knows what? But when you get to the heart of what AI is and how it can be applied to unlock value in businesses and everyday life, you have to admit that we're standing on the edge of a revolution. This revolution is likely to change our lives significantly in the short term, and perhaps tremendously so in the medium term.
It wasn't that long ago I felt short-sold by the promise of AI. About eight years ago I saw someone demonstrating a machine's ability to recognize certain flowers. Although impressive, it was a clunky experience, and while I could imagine applications, it didn't excite me. Fast forward a few years, my real moment of surprise came when I found thispersondoesnotexist. My brain couldn't work out why these were not real people, and it stuck with me. My next big moment was podcast.ai and their first AI generated discussion between Joe Rogan and Steve Jobs. But just like everyone else on the planet, the real breakthrough was ChatGPT and the conversation I had with the 'Ghost in the Machine'.

Sabrent USB-C Docking Station with M.2 Port (DS-SDNV) is the ultimate dock for Steam Deck and ASUS ROG Ally
When it comes to docks, we often seek versatility and capability in one neat package. Enter the Sabrent USB Type-C 6-Port Docking Station with M.2 Port (DS-SDNV). This isn’t just any dock; it’s an all-in-one solution for your Steam Deck, ROG Ally, and other USB-C devices.
The DS-SDNV isn’t picky about operating systems. Whether you’re on Windows, Linux, or macOS, it’s got your back. If you have USB-C devices with DisplayPort Alternate (DP Alt) Mode support, you can harness the power of HDMI 2.0 (HDCP 1.4) for seamless output.

How financial services cyber regulations are hotting up for API security
Financial services firms deploy an increasingly complicated mix of technologies, systems, applications, and processes to serve customers and partners and to solve organizational challenges. Focused heavily on consumer hyper-personalization, banks are evolving more and more digital assets and services to meet and exceed growing customer experience expectations.
As a result, the modern banking environment is heavily reliant on APIs to the point that they are now indispensable. APIs allow financial banks to connect with their ecosystem, while inspiring innovative developers to create new products, improve existing services, and work more efficiently.

Satechi Dual Dock Stand provides NVMe SSD storage and multi-screen flexibility
Today, Satechi launches its newest product, the Dual Dock Stand – a fusion of a docking station with an NVMe SSD Enclosure. The Dual Dock can transform an Apple MacBook or Windows laptop into a makeshift desktop. The stand, built from robust aluminum, sports a space-gray and black finish.
The Dual Dock Stand boasts two HDMI ports and a DisplayPort, allowing users the flexibility to expand their screen capacity with a crisp 4K/60Hz resolution. This expansion can accommodate up to two monitors, although those with Mac M1/M2 systems should note the limitation of just one external display.

New tool helps IT teams measure their environmental footprint
All organizations are under pressure to make their operations greener and more sustainable. But sometimes it can be hard to accurately measure the impact of your operations, especially if you're relying on cloud services.
Nutanix is launching a new tool to help organizations understand how different factors can influence their environmental footprint by estimating annual power and emissions for various solutions and locations.

Why composability is the key to delivering outstanding digital experiences
In today’s fast-paced digital world, it’s tough enough for organizations to attract customers and keep them loyal let alone to build sustainable and profitable growth. Being up against competitors that invest further in tech, it’s a challenge to deliver the innovative and highly personalized experiences customers expect.
One of the biggest tech drivers for digital experiences, a Content Management System (CMS), is the digital transformation tool for elevating digital experiences. With the availability of modern (hybrid and/or headless) CMS , brands are realizing they need to reassess their approach if they are to deliver for users’ expectations and evolving business requirements.

Enterprises struggle with basic security hygiene
Both ransomware groups and APTs continue to exploit vulnerabilities in public-facing applications, particularly in security appliances, business email technologies and enterprise file transfer products.
The latest mid-year threat review from Rapid7, based on the company's threat analytics and underground intelligence data, shows almost 40 percent of incidents Rapid7 managed services teams saw in the first half of 2023 were the result of missing or lax enforcement of multi-factor authentication, particularly for VPNs and virtual desktop infrastructure.

Google launches new Transparency Center as a central hub for policy information
Google has announced a new online hub called Transparency Center, where it will provide information about the policies that relate to its various products and services, including AI-related policies.
The company says that in the Transparency Center, visitors can find details about the decisions and processes that resulted in certain policies, access transparency reports and more. The hub can also be used to report policy violations to Google.
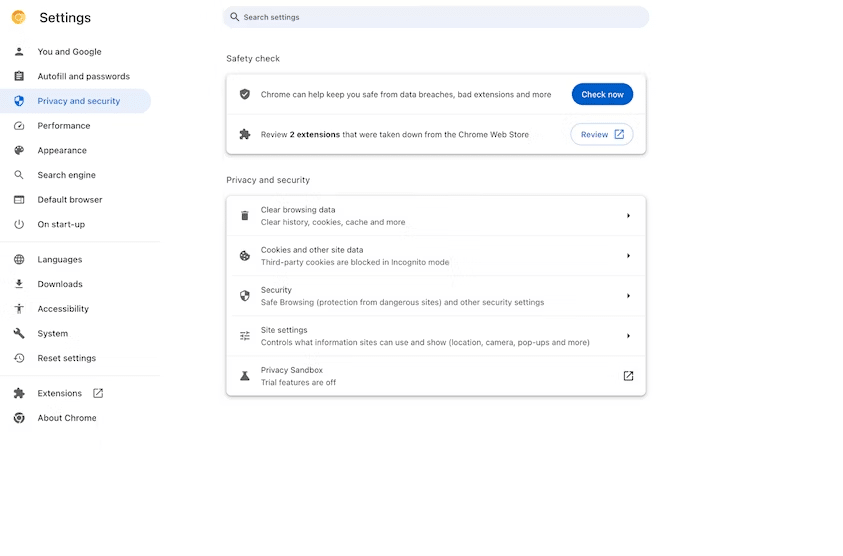
Google Chrome to warn users about problematic extensions
Google Chrome 117, the next major version of Google's dominant web browser, will inform users if an installed extension is no longer available on the Chrome Web Store.
Browser extensions may be removed from the official Chrome Store for extensions for a number of reasons: extension developers may pull them from the Store, Google may remove them because of malware or policy violations.



