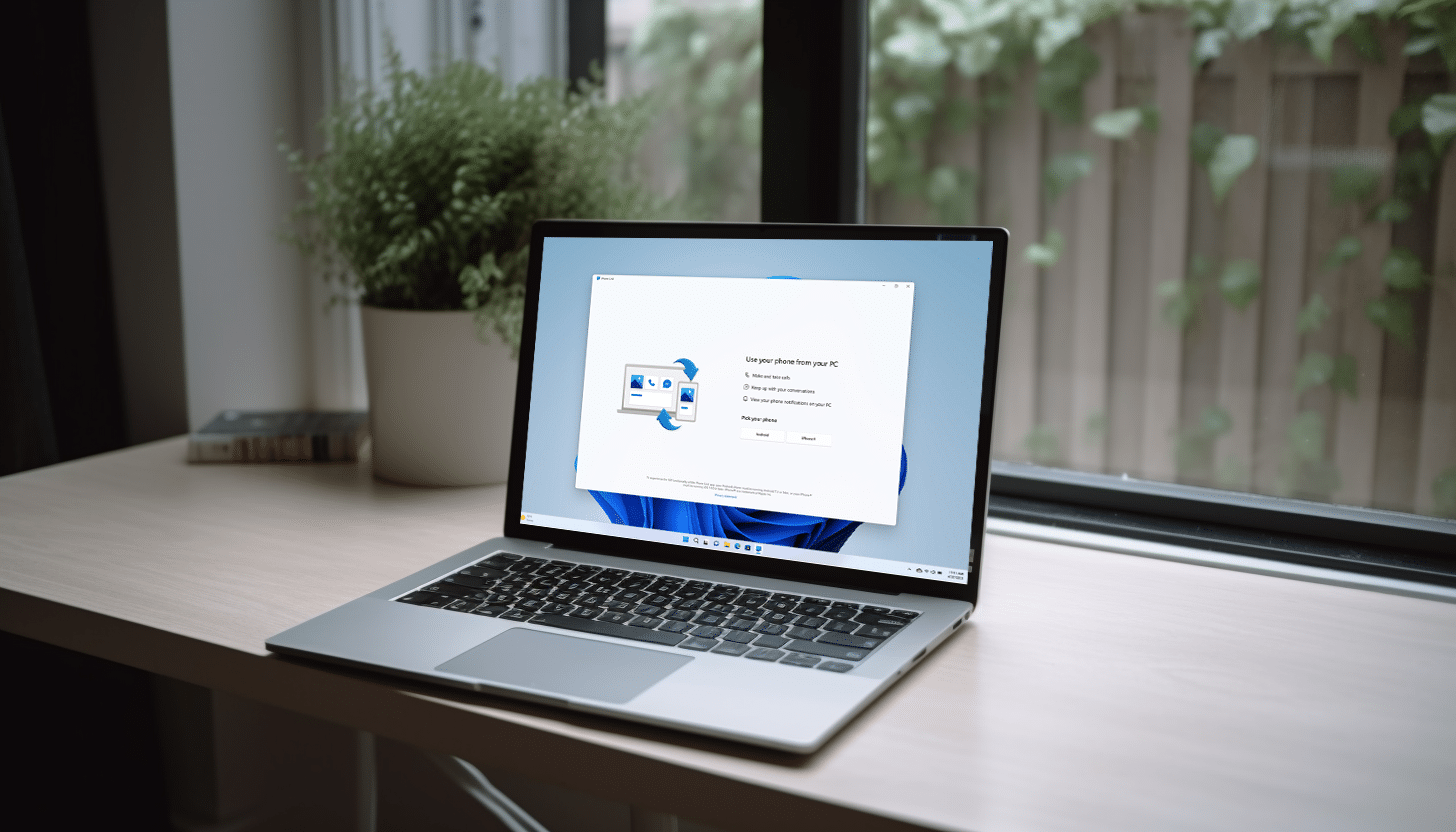
Phone Link for iPhone is now rolling out to all Windows 11 users
Microsoft today announces the expansion of its Phone Link feature, finally allowing iPhone users to connect to -- and interact with -- Windows 11 PCs.
Microsoft Phone Link for iOS on Windows 11 is beginning to roll out today in 39 languages across 85 markets, with the process expected to be completed by mid-May.

Java retains its popularity in a changing landscape
The Java programming language dates back to 1996, released by Sun Microsystems as a way of developing multimedia applications in a portable and interactive way.
That Java is still immensely popular almost 30 years on suggests that it must have got something right. New Relic's 2023 State of the Java Ecosystem report takes an in-depth look at the use of one of the most popular programming languages.

Versa delivers zero trust access across the enterprise
Hybrid cloud and hybrid work have changed where and how we access systems, challenging organizations to find ways to secure the enterprise while delivering the best user experience.
While cloud-delivered Zero Trust Network Access (ZTNA) solutions are now widely adopted to secure remote work, they don't deliver the application performance and inline policy enforcement needed for workers at the office.
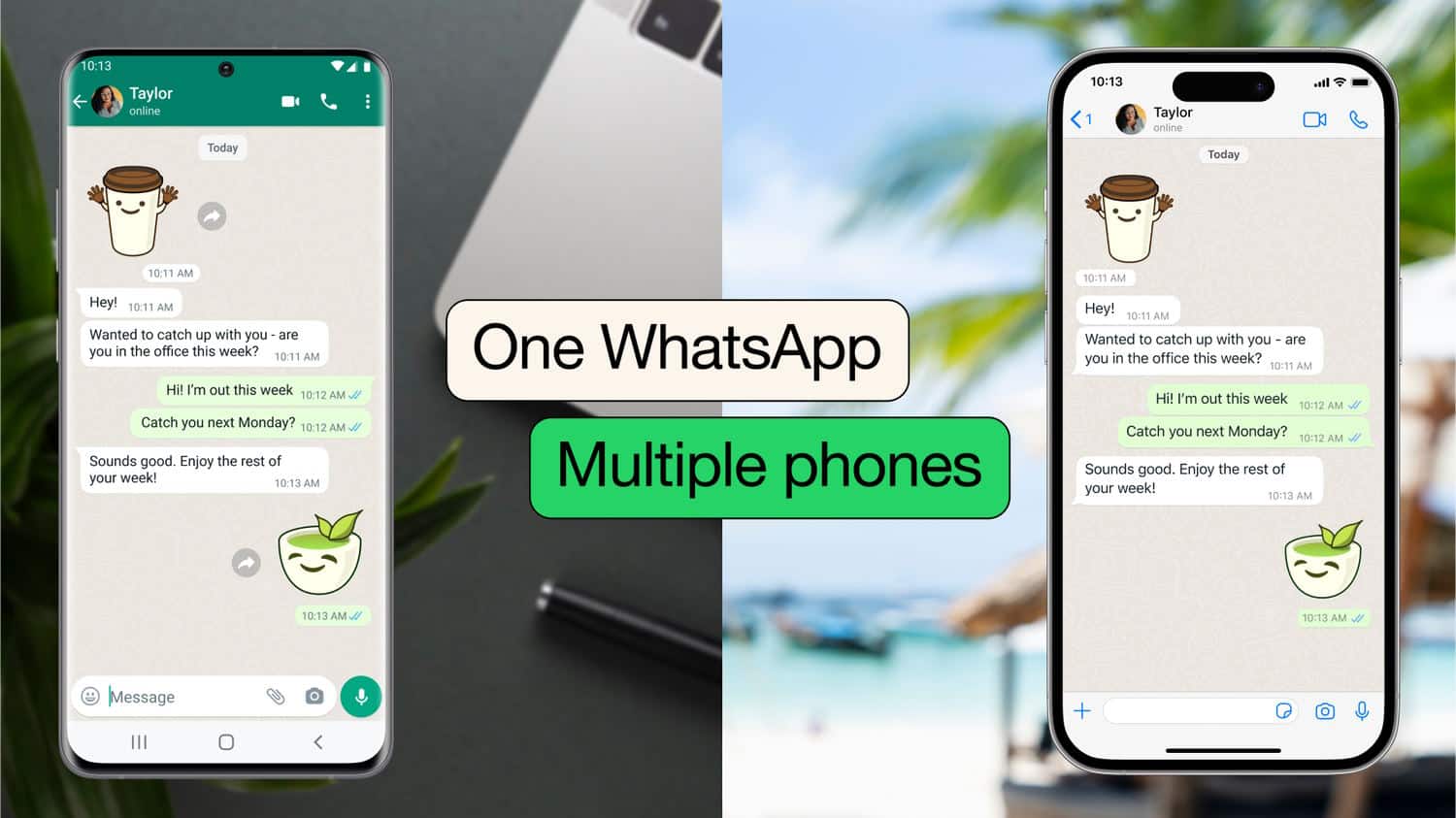
WhatsApp rolls out multi-phone support to all users
It is only very recently that WhatsApp beta users were given the ability to use the chat app across multiple phones. Now the company has announced that the feature is being rolled out globally to all users.
It has been possible for some time to sign into a single WhatsApp account on multiple device, but only one phone was permitted. This is something that, for numerous reasons, users have complained about -- and now it changes for everyone.
How analytics can boost the supply chain [Q&A]
Whether you're building software or building cars, all businesses rely on some sort of supply chain. For the business to run smoothly the supply chain needs to be as efficient as possible.
We spoke to Fabio Pascali, regional vice president of Cloudera, to find out more about how analytics can contribute to making the supply chain work more efficiently.

Microsoft treats Windows 11 21H2 users to the bug-bashing KB5025298 update
While Microsoft is keen for everyone to run Windows 11 22H2, older versions of the operating system remain supported. And it is with this in mind that the company has released the preview version of next month's KB5025298 update for Windows 11 21H2.
This is a non-security update, just like the KB5025305 update released for Windows 11 22H2, and it addresses a range of problems. The update also introduces firewall settings changes that mean it is now possible to configure application group rules.

Microsoft releases KB5025305 update for Windows 11, adding Widgets icon animations and Windows Update changes
We've reached the point of the month when Microsoft releases previews of the updates that will get a wider launch next month. As such, the company has released the KB5025305 update for Windows 11 22H2, and although this is not a security update, it includes a number of important changes and additions.
Microsoft draws attention to the arrival of animations to icons on the Widgets taskbar button when hovering over them, or when there is an announcement. This update also makes it easier to get hold of non-security updates faster, and makes a key change to Windows firewall as well as fixing numerous bugs and issues.
AMD Ryzen Z1 Series processors make Valve's Steam Deck obsolete
Valve's Steam Deck is a very popular handheld computer that allows people to play modern PC games on the go. Powered by a Zen 2-based AMD APU, Steam Deck also makes a great emulation machine. The Linux PC can play thousands of ROMs from classic consoles, such as N64, PS1, and more. Hell, it can even run modern Nintendo Switch games!
Unfortunately for Valve, the Steam Deck is about to become obsolete. You see, earlier today, AMD launched its all-new new Zen 4-based Ryzen Z1 Series processors. These chips are designed to provide a high-end gaming experience for handheld PC consoles. Make no mistake, the gaming systems powered by Z1 will make the current Steam Deck old hat.

Behavioral AI platform defends against multi-channel attacks
While email remains the most common path to target an organization, we're increasingly using other tools like Slack, Teams and Zoom too, so cybercriminals are steadily shifting their tactics and targeting these additional entry points across the enterprise.
AI-based email security platform Abnormal Security is launching a range of new additions to its product focused on expanding security detection for these collaboration tools.

Why UI/UX is significant for SaaS development in 2023
UI/UX design is crucial for SaaS products because it directly impacts the user's experience with digital technology. Today's users demand a seamless and intuitive experience when using any software or application. A confusing or cluttered user interface (UI) can quickly turn users away, causing them to search for alternative options. On the other hand, a well-designed UI/UX can make all the difference in whether a user decides to continue using a SaaS product or switch to a competitor.
Good UI/UX design can also improve the overall functionality and efficiency of a SaaS product, leveraging the power of digital technology to increase productivity and satisfaction among users, create a positive brand perception, and reduce support costs, improving customer retention. To remain competitive in the age of digital technology, SaaS companies need to prioritize UI/UX design as an ongoing process to ensure that the interface meets the changing needs of users and the industry.

86 percent of developers knowingly deploy vulnerable code
According to a new study, 86 percent of software developers and AppSec managers surveyed have or know someone who has knowingly deployed vulnerable code.
What's more the study from Checkmarx shows 88 percent of AppSec managers surveyed have experienced at least one breach in the last year as a direct result of vulnerable application code.

71 percent of businesses hit with insider attacks from malicious employees
Insider attacks including fraud, sabotage, and data theft, plague nearly three quarters (71 percent) of US businesses, according to Capterra's 2023 Insider Threats Survey.
Perhaps unsurprisingly companies that allow excessive data access are much more likely to report falling victim to insider attacks. However, only 57 percent of companies limit data appropriately while 31 percent allow employees access to more data than necessary and 12 percent allow employees access to all company data.

Integration is a top priority for enterprises
A new report finds that 71 percent of enterprises are actively planning to implement integration technology this year.
The study from enterprise integration platform as a service (iPaaS) company Digibee surveyed over 1,000 US and Canada-based CIOs, CTOs, developers, and enterprise architects, and finds integration strategies being hampered by technology that isn't cloud-native and lack the agility to respond quickly.

First release of Kodi 21 'Omega' available to download NOW
Three months ago, The Kodi Foundation rolled out the first stable version of Kodi 20 'Nexus', the latest iteration of its popular home theater software,
Today, the team makes the first build of its successor, Kodi 21 'Omega', available to download, and it’s described as a "major release" with lots of new features.
Google Authenticator gains cloud backup of one-time codes
Google has released an important update for its Authenticator app. The latest versions of Google Authenticator for iOS and Android can now synchronize one-time codes to the cloud.
In offering Google Account synchronization, the 2FA tool is now easier to use across multiple devices. This is something Google points out as being useful in the case of a lost or stolen device.



