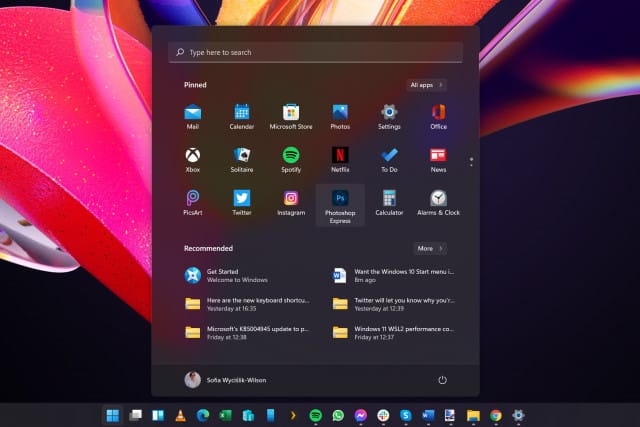
Want the Windows 10 Start menu in Windows 11? Tough... Microsoft has removed it
When the first build of Windows 11 appeared, the new Start menu was loved by some and hated by others. Those that didn't like it fell into two camps. Those who were unhappy with the centring of the Start menu could move it to the of the screen; those unhappy with the updated look could revert to the look of Windows 10.
But when the second Insider build emerged, there were changes. Yes, it's still possible to move the Start menu to the left of the taskbar, but the registry hack that could be used to show the classic Start menu has now been blocked.

Here are the new keyboard shortcuts in Windows 11
With the upcoming release of Windows 11, there is a lot of attention focused on certain areas of the operating system -- notably centering of the Start menu, the arrival of widgets, and the visual tweaks that Microsoft has introduced.
But there are also new keyboard shortcuts. These provide easy access to many of the new features of Windows 11 and are a faster way of getting around than using a mouse or trackpad. Not only are there completely new shortcuts to learn, but some key combinations have changed from Windows 10, and have inherited new functions in Windows 11.

Twitter will let you know why you're not worthy (of being verified)
Twitter may delight and infuriate in just about equal measure, but if there's one thing that the majority of users can agree on it is that it would be great to have a tick of verification. For many people, getting verified on Twitter has been a goal for a long time, and the company only recently re-opened applications after a lengthy period of suspension.
Being able to apply for Twitter verification is, of course, absolutely no guarantee of being verified, and huge number of people have been disappointed to be rejected. Unhelpfully, Twitter has -- until now -- failed to make it clear why a request for a blue badge has been denied. But now the company says it will be providing more detail.

Without training one in three users fall for phishing scams
New research finds that, if they haven't received security awareness training, one in three users will likely fall for a phishing or social engineering scam that could put their organization at risk.
The study from awareness training specialist KnowBe4 set out to measure organizations' phish-prone percentage (PPP) and found an initial baseline of 31.4 percent across all industries and sizes.
Best Windows 10 apps this week
Four-hundred-forty-six in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft plans to release Windows 11 and Windows 10 version 21H2 later this year. If you intend to stay on Windows 10 for the time being, check out Sofia's article on the changes in the new Windows 10 feature update.

Microsoft's KB5004945 update to fix PrintNightmare is breaking some printers
The PrintNightmare vulnerability that was accidentally revealed recently has led to an almost laughable chain of events. After Microsoft suggested a workaround, a third-party released a patch, an official patch was eventually released, and said patch was found to not actually do the job it was supposed to.
The patch is not only ineffective -- although Microsoft disagrees -- it is also, very much in the tradition of patches for Windows, causing issues. People installing the KB5004945 patch report that they then have problems with printing.

How stopping lateral movement can defend against ransomware [Q&A]
Over the last couple of years the number of ransomware attacks has soared. While high profile attacks make the headlines organizations of all sizes are at risk.
One of the keys to stopping attacks is to prevent them from moving laterally through networks. We spoke to Amit Serper, area VP of security research for North America at microsegmentation specialist Guardicore to get his view on how businesses can protect themselves.

Windows 11 WSL2 performance compares very favorably with bare metal Ubuntu Linux in benchmarks
Windows Subsystem for Linux has been both a revelation and a revolution. Now in its second iteration (WSL2), the technology has advanced dramatically in recent years and increasing numbers of people are using it to enjoy Linux distros and apps within Windows.
With the launch of the first Insider builds of Windows 11, there is interest from the Linux community about what progress Microsoft has made. Benchmarks pitting WSL2 against "bare metal" Ubuntu show that performance is pretty impressive... but there are still improvements to be made.

Ubuntu Linux-maker Canonical is 2021 Microsoft Partner of the Year finalist
Microsoft has been getting more and more friendly with both the Open Source and Linux communities in recent years. For instance, the Windows 11-maker offers its some of its popular software for Linux-based operating systems these days, such as Windows Calculator and the Chromium-based Edge web browser. No to mention, Linux is essentially integrated into Microsoft's desktop operating system thanks to the Windows Subsystem for Linux.
To show just how close-knit Microsoft and the Linux community are, today, something fairly shocking is announced. You see, Ubuntu-maker Canonical is a 2021 Microsoft Partner of the Year finalist. Wow.

Microsoft releases a new Windows 11 build with loads of changes, fixes and improvements
Last week, shortly after confirming its existence, Microsoft rolled out the first preview build of its new, forthcoming operating system, Windows 11.
Today, the software giant releases Windows 11 Build 22000.65 to those Insiders in the Dev Channel and it comes with a long list of changes and improvements, as well as plenty of fixes. As you might expect, there are lots of known issues to be aware of too.

Download Linux Mint 20.2 today and tell Microsoft you don't want Windows 11
With Windows 11 on the horizon, many consumers will find themselves unable to upgrade due to the crazy system requirements the operating system has. And so, some of those people will look for alternatives, such as Linux distributions. While Ubuntu is a wise choice for those interested in switching to Linux, it isn't the best choice. Actually, Windows-switchers should instead give Linux Mint (which is based on Ubuntu) a try.
Wouldn't you know it, today, the all-new Linux Mint 20.2 becomes available for download. Named "Uma," it can be had with your choice of three great desktop environments -- Cinnamon 5.0, MATE 1.24, and Xfce 4.16. Mint 20.2 is based on Ubuntu 20.04 and uses Linux kernel 5.4.
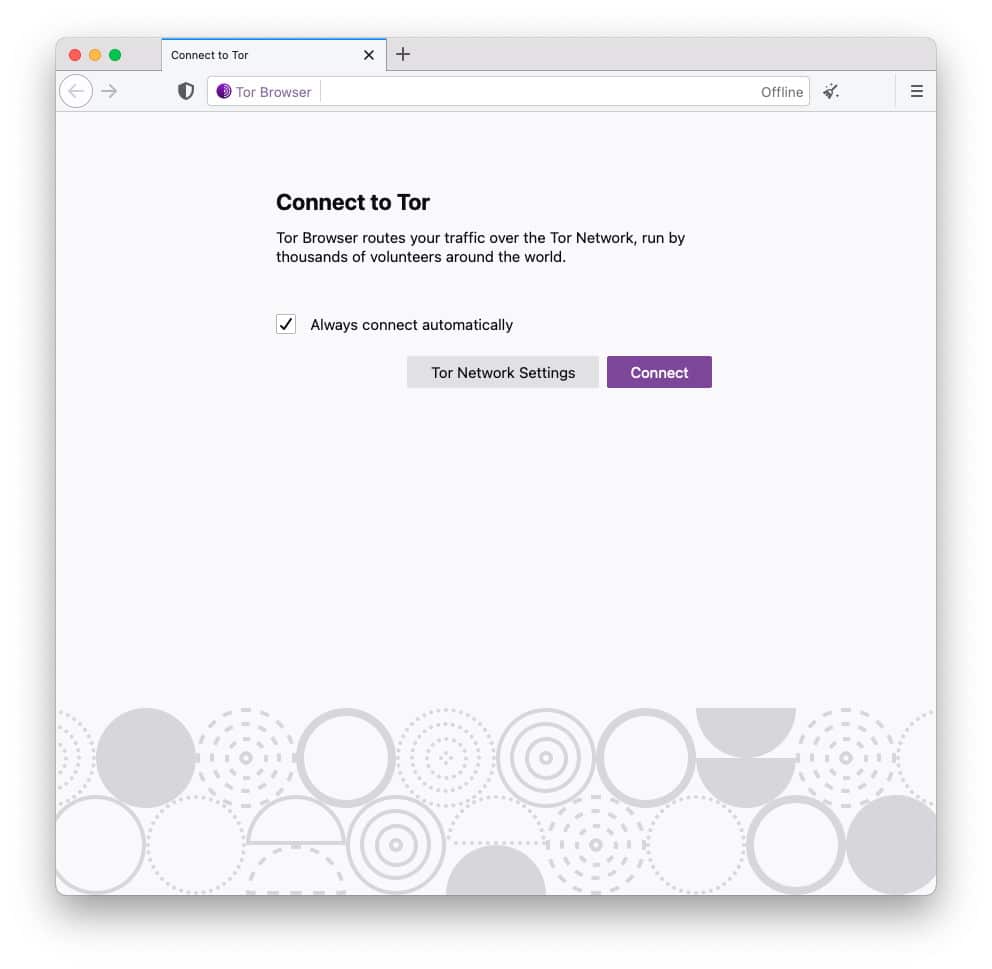
Tor Browser 10.5 is here... and it kills off support for older Onion services
Web users' interest in privacy and security has gradually increased over the years, and demand for secure, anonymity-offering browsers like Tor is also on the up. Now a new version of Tor Browser is upon us, introducing various protection methods.
Perhaps most apparent in Tor Browser 10.5 is the improved experience of connecting to Tor. While the Tor Network has undeniably rocketed in popularity, there are still plenty of people who like the idea of the security and privacy it offers, but feel uncomfortable with getting started. In particular, this latest version of the browser makes life easier for people forced to use censored connections.

Ransomware gangs get more professional
Ransomware, and indeed malware generally, used to be something of a cottage industry, the preserve of individuals or small groups. But new research from threat intelligence company KELA shows that it's becoming a highly professionalized industry.
Many cybercriminals are now specializing in different areas, so that the coding, spreading, extracting and monetizing processes might all be carried out by different people.

Plugable launches USBC-HUB7BC 7-in-1 USB Charging Hub
USB-A ports used to be ubiquitous, but nowadays, they are becoming less common. Make no mistake, USB-A isn't disappearing anytime soon, but fewer laptops are coming with the ports. Instead, many notebooks come with USB-C only these days. And if a laptop does come with USB-A, it may only be one or two ports at most.
Thankfully, one of the best things about USB is the ability to utilize hubs -- you can turn one USB port into several. Today, Plugable launches its latest powered hub, and it is designed for both data and charging. Called "USBC-HUB7BC," it can convert either a USB-A or USB-C port into seven USB-A ports. If you need more than seven USB 3.0 5Gbps ports, you can use more than one USBC-HUB7BC with one PC -- they are designed to be neatly stacked on top of each other.

Microsoft is seeking feedback in a new Windows 11 bug bash
It has been a while since Microsoft held a Bug Bash to discover problems with Windows and gather feedback about features. In fact, the last one was back in May.
But with the impending launch of Windows 11, it is perhaps not surprising that it is Bug Bash time again. Over the next week, Insiders using Windows 11 preview builds are invited to take part in quests and earn themselves an exclusive badge in return for helping out.



