
Cloud spend soars as organizations adapt to COVID-19
The latest State of the Cloud report from Flexera reveals that 59 percent of enterprises expect their cloud usage to exceed prior plans due to COVID-19.
Organizations are over budget for cloud spending by an average of 23 percent, and expect cloud spend to increase by 47 percent next year. However, respondents estimate that 30 percent of their cloud spend gets wasted.

IBM Cloud boosts security and productivity with Red Hat OpenShift enhancements
As businesses move to the cloud, they want choice, flexibility, and the ability to easily manage and migrate their critical workloads securely across public clouds, private clouds, and on-premise environments.
To help them achieve this IBM is enhancing the Red Hat OpenShift container platform on IBM Cloud by making OpenShift 4.3 generally available as part of its fully managed service.

Free security analytics helps fight remote worker threats
We've seen many companies offering free software during the current crisis. Now security and risk analytics company Gurucul is launching two free services to help organizations protect themselves against cyberattacks that target their remote workers and third-party identities.
These deliver the Gurucul Unified Security and Risk Analytics platform as a cloud service with pre-configured and tuned algorithms that can detect unusual and high risk behavior patterns exhibited by remote workers as well as third party identities and devices.
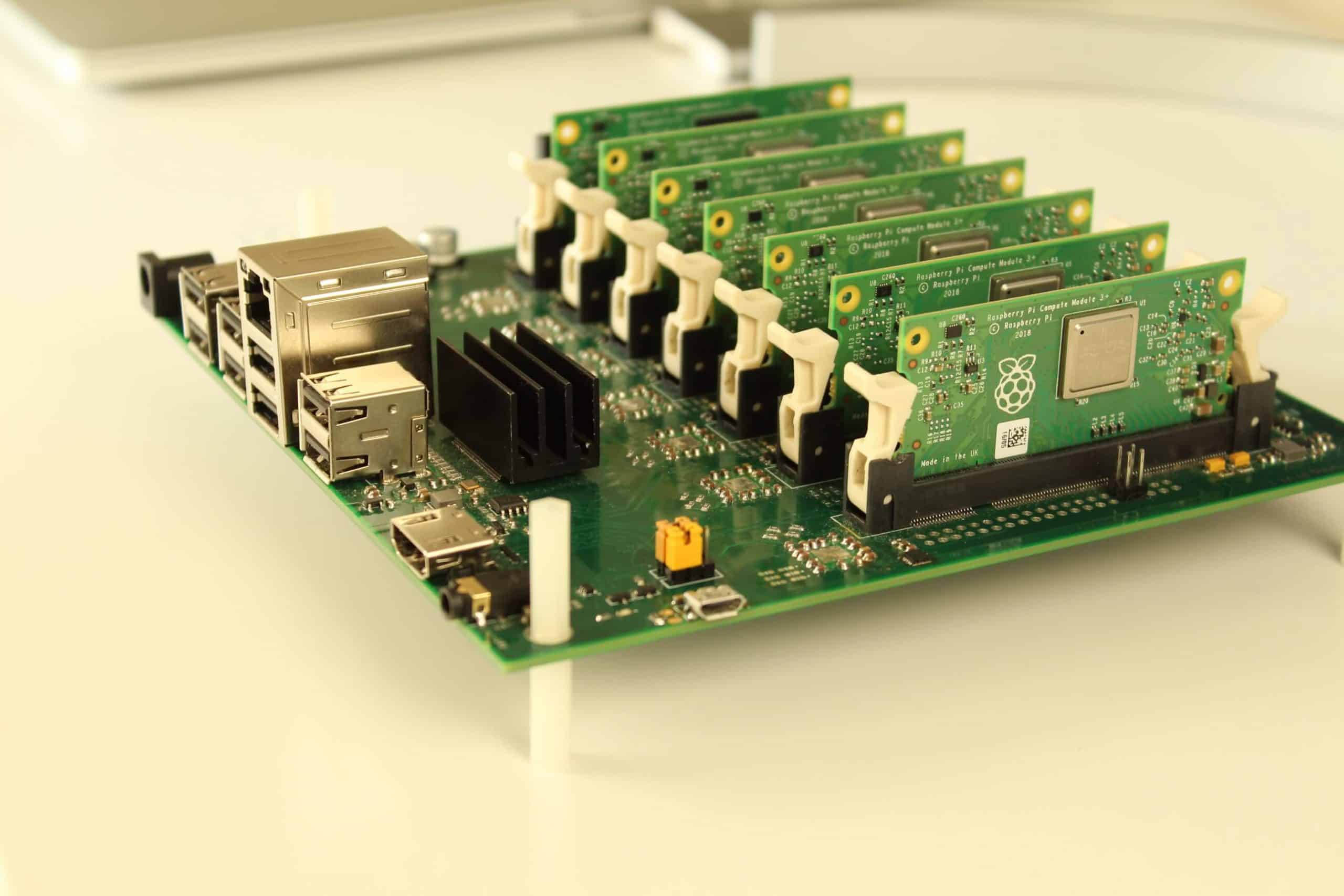
The Raspberry Pi-based server that could transform edge computing
Cloud servers, you might think, are big expensive pieces of kit. But you’d be wrong, at least where the Turing Pi project is concerned.
This mini ITX format board costing under $200 allows seven Raspberry Pi systems to be combined into a desktop Kubernetes cluster that's smaller than a sheet of A4 paper.

Fewer than half of companies operate securely in the cloud
A new survey finds that 85 percent of companies believe embracing the public cloud is critical to fuel innovation. But of those who have already adopted public cloud, only 40 percent have in place an approach to managing cloud and container security.
The study by DivvyCloud finds only 58 percent say their organization has clear guidelines and policies in place for developers building applications and operating in the public cloud. Of those, 25 percent say these policies are not enforced, while 17 percent confirm their organization lacks clear guidelines entirely.

Ubuntu Linux publisher Canonical launches Managed Apps for enterprise DevOps teams
Ubuntu creator Canonical is launching a new Managed Apps platform, allowing enterprises to have their apps deployed and operated by Canonical as a fully managed service.
At launch the service will cover ten widely used cloud-native database and LMA (logging, monitoring and alerting) apps on multi-cloud Kubernetes but also on virtual machines across bare-metal, public and private cloud.

Employees reluctant to adopt data-driven working methods
New research commissioned by analytics database Exasol finds that 63 percent of UK data decision makers experience resistance from employees in adopting data-driven methods.
Key drivers of this resistance are anxiety over job redundancy if all decisions are based on data (39 percent), a lack of understanding (39 percent), and a lack of education on the positive impact data can have (36 percent).

Microsoft clarifies a slightly misleading claim about a leap in cloud service usage during coronavirus pandemic
Over the weekend, Microsoft post an article on its Azure blog announcing that there had been an astronomical 775 percent surge in the use of its cloud services. Despite the massive increase in traffic, the company added, uptime was good. But the blog post wasn't entirely correct.
Since we published a story about the claims, Microsoft has contacted us to say that it had not been "was not as clear as they intended to be with the previous statement". The company has provided updated stats explaining what it meant to say -- and it's rather different.

Coronavirus has led to a 775 percent increase in usage of Microsoft Azure cloud services
This weekend, Microsoft has given an insight into the impact the coronavirus pandemic has had on its services. The company says that there has been a huge increase in Teams usage, and there are not over 44 million daily users.
In regions where there are isolation and home sheltering orders in place, Microsoft says that there has been a colossal 775 percent increase in usage of its cloud services. Despite the surge in demand, there have not been any significant service disruptions.

Get AOMEI Backupper Professional free for a year
Next Tuesday is World Backup Day and to mark the event AOMEI is offering a 12 month free subscription to its Backupper Professional product. The offer is available from now until April 2nd.
With more people working at home on their own machines due to the Coronavirus, security and protection of data is more important than ever.

New decentralized cloud storage service set to take on AWS
Cloud storage company Storj Labs is launching a new decentralized service aimed at storing data more efficiently and providing additional revenue-generating opportunities for storage node operators.
Called Tardigrade -- in case you were wondering a tardigrade is an eight-legged water dwelling micro animal (or if you've watched 'Star Trek: Discovery' a sort of massive space-travelling flea) -- it offers cloud object storage that's S3 compatible, high performing, easily implemented, exceptionally durable, and with high availability.

How AI can save companies millions on cloud spend
The cloud has revolutionized making it easy to build, launch, and scale a service. That's driven a wave of spending on the major cloud providers, as made evident by the latest earnings reports from Microsoft (Azure), Amazon (AWS), and Google (Google Cloud). Microsoft just reported 62 percent QoQ growth for Azure, AWS brought in nearly $10 billion for Amazon in Q4 2019, and Google reported cloud earnings for the first time in January.
Companies of all sizes are clearly investing billions on the cloud and there doesn't seem to be a ceiling. Gartner predicts that by 2022 overall cloud spend will reach more than $330 billion, and that number grows every year. But at the same time, current estimates reveal that billions of this spend is the result of needless and wasted outlay. A recent survey of companies that spend at least $5 million on the cloud annually found that a vast majority (69 percent) regularly overspend on their cloud budget by 25 percent or more.

CIOs believe the pace of digital transformation will increase in 2020
A new survey of over 300 enterprise chief information officers (CIOs) shows that more than 90 percent expect the pace of digital transformation to increase in 2020.
The report from Flexera shows that customer experience is the top driver of digital transformation efforts with 69 percent rating it very important, but only 36 percent considering themselves very mature in this area.

New structured data service allows faster access for applications
As enterprises make more use of widely-available analytics engines such as Presto, Apache Spark SQL or Apache Hive, they often run into inefficient data formats and face performance challenges as a result.
Open source cloud data software company Alluxio is launching a new Structured Data Service (SDS) that will allow developers and data scientists to benefit from a more simplified data platform that enables connections to different catalogs for access to structured data, with less copies and pipelines and more compute-optimized data.

Almost a third of businesses lose up to $1 million a year to integration issues
A new study reveals 30 percent of businesses estimate they lose between $100,000 and $1 million per year as a result of integration-related issues such as data errors, technology impediments, or SLA violations.
The report from cloud platform Cleo shows 10 percent claim to lose $1 million or more on an annual basis from such causes. As for productivity costs, nearly half (46 percent) say it takes them a month or longer to onboard a new trading partner, causing slowdowns in their business.
