How to check to see if your data was part of the Marriott Starwood Hotel hack

When hackers hit Marriott's Starwood Hotel database last year, it was first thought that half a billion customers might be affected. This estimate was later downgraded to 383 million guests, but this is still a very large number, and it is understandable that many people are concerned that their data may have been accessed.
There was particular concern about whether passport numbers had been accessed, and this is what a new checking tool lets you check. Marriott has teamed up with security firm OneTrust to enable customers to check if their data was included in the security breach.
User data exposed in 500px security breach... that happened in the middle of last year

The photo sharing site 500px has revealed details of a security breach that took place in mid-2018.
The company says that its engineering team only became aware of the breach -- which is thought to have taken place around July 5, 2018 -- a few days ago. 500px launched an investigation in conjunction with a third party and police, and says that "an unauthorized party gained access to our systems and acquired partial user data".
VFEmail hack wipes out all of the email provider's US servers
Email provider VFEmail has been hit by a huge attack that resulted in all of the data it stores in the US being wiped out.
Describing the attack as "catastrophic", VFEmail revealed that a hacker had breached its security and succeeded in deleted not only primary data systems, but also the backups. The attacker was caught in the act, and it was possible to intervene before damage was caused to servers in other countries. But for VFEmail users whose data was stored in the US, the news is far from good.
Trakt tardily notifies users of data breach that took place over four years ago

Users of Trakt -- a service for "scrobbling", or tracking the movies and TV shows you watch in the likes of Plex and Kodi -- have received emails from the company notifying them of a data breach that took place way back in 2014.
Trakt says that although the security breach took place over four years ago, it only recently discovered it. The company says that an investigation is underway, but that it believes a "PHP exploit was used to capture data", including users' emails, usernames, encrypted passwords, names and locations.
KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
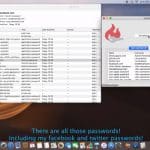
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain.
Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS.
Huge Collection #1 database leak exposes 773 million email addresses and 21 million passwords

A massive database leak -- dubbed Collection #1 -- has made its way to hacking forums, exposing millions of email addresses and passwords. The news was first shared by Troy Hunt -- the man behind Have I Been Pwned? -- who explains that the leak comprises, "many different individual data breaches from literally thousands of different sources".
Hunt explains that there are "1,160,253,228 unique combinations of email addresses and passwords", so there are a very large number of people that may have been affected by the leak.
Get 'Advanced Penetration Testing -- Hacking the World's Most Secure Networks' ($26 value) FREE for a limited time

Typical penetration testing consists of low-level hackers attacking a system with a list of known vulnerabilities, and defenders preventing those hacks using an equally well-known list of defensive scans.
The professional hackers and nation states on the forefront of today's threats operate at a much more complex level -- and this book shows you how to defend your high security network, including:
New Fortnite vulnerabilities put users' privacy at risk

Researchers at security firm Check Point have uncovered vulnerabilities in the popular online game Fortnite that would allow attackers to intercept and steal Fortnite users’ login credentials without them being aware of the theft.
The attack manipulates Fortnite's login process to capture usernames and passwords. Armed with these details attackers could view any data stored in the game, buy more V-Bucks in-game currency at users' expense, and access all the user’s in-game contacts as well as listen in on and record conversations taking place during game play.
Marriott hack update: attackers accessed fewer user records than first thought, but 5.3 million passport numbers were unencrypted

Back in late November, Marriott International went public with news that its Starwood Hotel reservation database had been hacked. At the time, the company suggested that up to 500 million customer records had been put at risk as a result, but now it has provided an update with a reduced estimate.
The company now says that it believes up to 383 million guests may have been affected; but the news is not all good. Marriott also reveals that over 5 million unencrypted passport numbers were stolen by hackers.
Major US newspapers hit by cyberattack, disrupting printing and distribution

A number of major US newspapers -- including the Los Angeles Times, Chicago Tribune, Wall Street Journal and New York Times -- have been hit by a cyberattack that is said to originate from another country.
Malware was first detected on Thursday by Tribune Publishing, the owner of some of the affected titles, but unsuccessful attempts at quarantining meant that there was disruption well into Saturday. The Department of Homeland Security is currently investigating the incident which is not thought to have exposed any personal customer details.
Following 'unusual activity' from China and Saudi Arabia, Twitter reveals user country codes may have leaked

Twitter has discovered what it describes as "unusual activity" stemming from China and Saudi Arabia. The social networking company says that it noticed a large number of enquiries involving a support API coming from individual IP addresses in the two countries.
The discovery came as Twitter investigated a bug in a support form. The problem, Twitter says, dates back to November 15, and it was fixed the next day, but a security researcher says he reported the issue two years ago. As a result of the bug, Twitter says that the country code of users' phone numbers could have been discovered by malicious actors.
Popular VTech children's tablet can be easily controlled by hackers

Risk management and cybersecurity specialist SureCloud has discovered that the popular VTech Storio Max children's tablet can easily be hacked, enabling criminals to take control of the devices and snoop on unsuspecting victims.
This can be done by simply adding an image or link to a website. When accessed by a child via the tablet's web browser, the exploit would attack the tablet and enable the attacker to take full control of the device.
Marriott's Starwood Hotel database hacked, putting 500 million customers at risk

Marriott International has revealed that its Starwood Hotel reservation database has been hacked. An investigation carried out by the company revealed that hackers have had unauthorized access to the Starwood network since 2014.
The astonishing revelation means that information of half a billion guests could have been exposed -- including sensitive personal data such as home address and passport number -- and Marriott says there is evidence that data has been copied from its network.
Dell resets customer passwords following cyberattack on its website

Dell has announced that it has instigated a mandatory password reset for customers after it suffered a cyberattack earlier in the month.
In a statement, the company confirmed that its network had been subject to "unauthorized activity" on November 9 in which attackers tried to gain access to customer information. Dell says that data was limited to names, email addresses and hashed passwords, adding there is "no conclusive evidence" that data was extracted. The forced password reset is described as a measure to "limit the impact of any potential exposure".
Protecting the US voting infrastructure [Q&A]

It's two years since international forces interfered with the security of the US elections. However, with the US midterm elections behind us and the presidential elections ahead, vulnerabilities in the country’s voting infrastructure still remain.
Simply put, it's not hard to hack into US voting systems. Don't believe it? Just ask the 11-year old who hacked a replica of the Florida election website to change results in under 10 minutes. We might not have seen widespread cyberattacks on the day of the midterms, but as we saw multiple opportunities for hacking and disruption in the run up, the presidential elections are already at risk.
Recent Headlines
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.