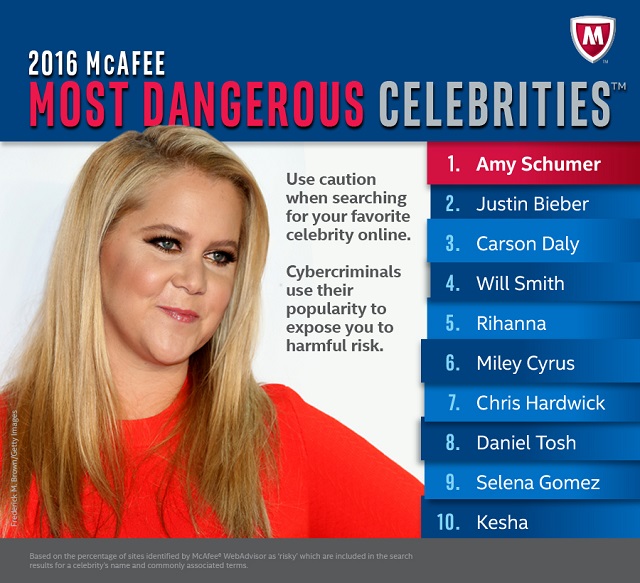
Amy Schumer and Justin Bieber top the 2016 McAfee 'Most Dangerous Celebrities' list
When people think of online malware, they sometimes think infections only come from 'bad' websites, such as pornography and warez. Yeah, those types of sites can definitely house malware, but so can any site. In fact, bad guys will often target users through seemingly wholesome places, where a person may let their guard down.
Today, McAfee announces its annual 'Most Dangerous Celebrities' list. No, the celebrities themselves are not a danger to the public -- as far as I know, at least. Actually, these are people that, when their names are entered as search terms, can cause an increased chance of leading to malware. For 2016, McAfee lists Amy Schumer as the most dangerous in this regard.

Malware attacks are declining but getting cleverer
In the first six months of 2016 users were twenty percent less likely to encounter malware than in the same period last year. But although attacks are decreasing they’re getting more sophisticated and often disappear within hours having achieved their aims.
These are the key findings of the latest Webroot Quarterly Threat Report, based on information collected from millions of endpoints, released today.
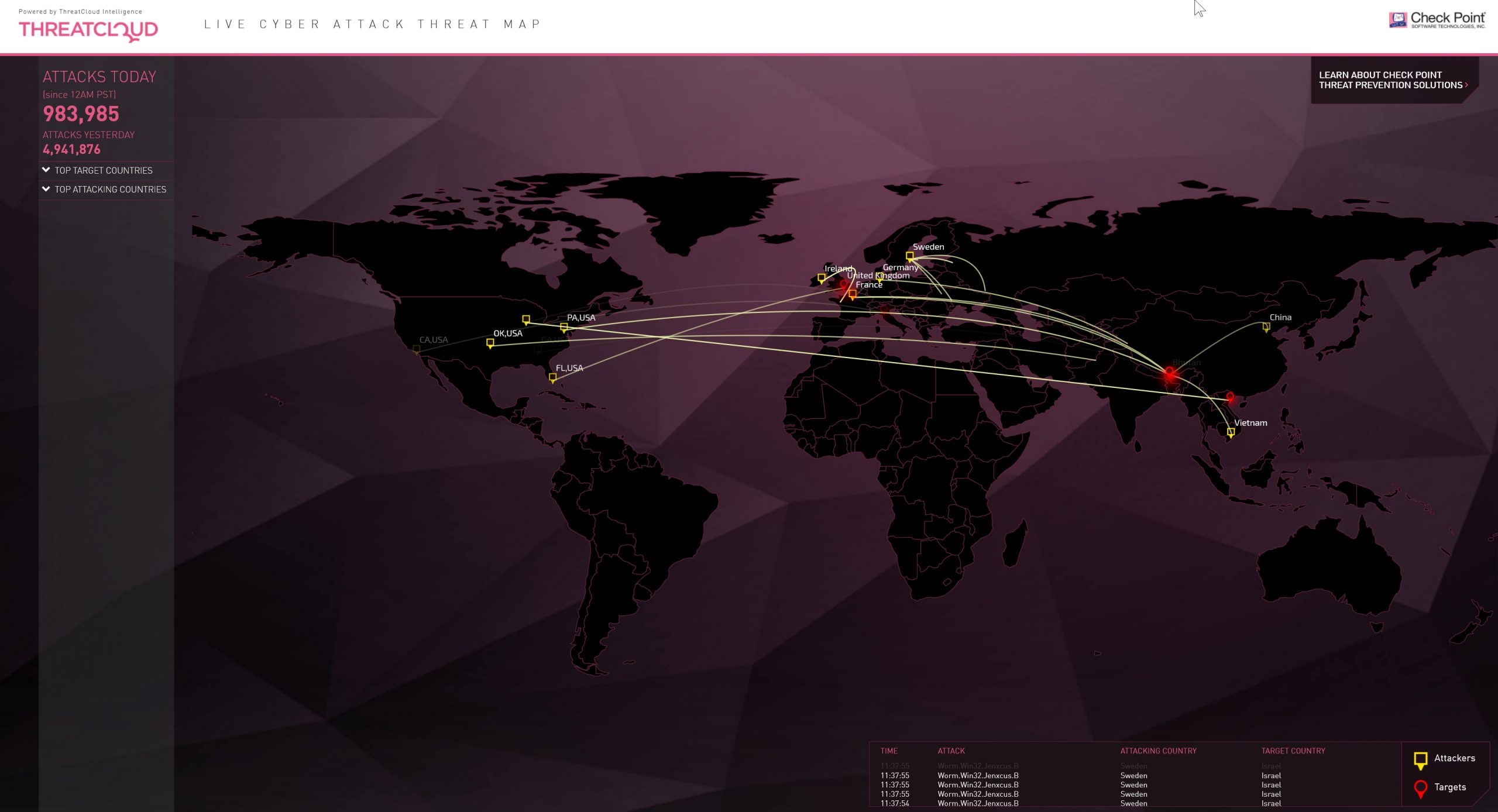
Traditional malware falls as mobile malware rises in July
The number of active malware families attacking businesses fell by five percent in July, but mobile malware now accounts for nine percent of the total -- up 50 percent from June.
These figures come from threat prevention company Check Point based on intelligence drawn from its ThreatCloud World Cyber Threat Map.

Eddie Bauer point of sale systems hit by malware, customers notified
If you aren't thinking twice every time you swipe your card at a retail location, be it a store or restaurant, then you haven't been paying attention lately. It should give you reason for pause, but sadly you still have to do it. Just cross your fingers on the other hand.
Previous examples have included Target and Home Depot to name just two. The latest is retailer Eddie Bauer. The company is warning customers it’s point of sale system was hit by malware.

Hacker group Shadow Brokers auctions off NSA malware
The NSA has (or had...) a collection of malware in its cyber arsenal. It has been stolen by hackers. It is now available to buy.
A group of hackers going by the name of Shadow Brokers claims to have stolen a range of hacking and malware tools from Equation Group's servers -- Equation Group is itself closely linked with the NSA. The group is offering the tools for auction and will sell them to the highest bidder. If bidding reaches one million Bitcoins, however, the group says it will make the tools publicly available to all.

Malware hits 20 major hotels, customer data may be stolen
As many as 20 hotels in the US have been hit by malware, and fears are spreading that customer data, including credit card information, was stolen.
According to a Reuters report, hotels under attack include Starwood, Marriott, Hyatt and Intercontinental -- all part of the HEI Hotels & Restaurants.

Kaspersky finds advanced cyber-espionage malware that hid for five years
Kaspersky Lab's security researchers have found a new cyber-espionage malware, most likely built by a nation-state to use against other states' organizations.
Dubbed "ProjectSauron", it is "particularly interested" in accessing encrypted communications. The malware hunts such communications down using an "advanced modular cyber-espionage platform", comprised of a number of different and unique tools.

Ransomware makes up half of all malware
Ransomware is no longer a quick and easy way for cyber-criminals to get their hands on some money. It is now considered a "permanent fixture on the threat landscape" -- at least according to PhishMe’s Q2 2016 Malware Review.
The security experts’ new report says ransomware now accounts for 50 percent of all malware configurations, meaning it is now a mature business model. It also says it shows no outward signs of diminishing.

New malware campaign avoids detection to target major financial brands
Updated versions of the Gozi malware are being used in currently active campaigns targeting global financial brands according to threat intelligence experts buguroo Labs.
Targets of the attack include PayPal, CitiDirect BE, ING Bank, Société Générale, BNP Paribas, and the Bank of Tokyo. It's expected that attacks currently being perfected in Poland, Japan and Spain, will soon be launched in the US and Western Europe.

Beware of Pokemon Go malware in Google Play
It may be easy to dismiss reports of Android malware as nothing more than fear mongering by clickbait-loving journalists and security companies, but not even apologists can argue with the fact that the threat is real when malware is approved on Google Play.
ESET's security researchers have uncovered a fake lockscreen app, called Pokemon Go Ultimate, which takes advantage of the game's mindblowing popularity to mislead users into installing it ultimately generating revenue by clicking on porn ads.

Stampedo ransomware available for just $39
A new variant of ransomware has been found for sale on the dark web for an incredibly low price that allows its victims 96 hours to pay a fee.
This new piece of ransomware is called Stampedo and it is available for only $39 which includes a lifetime license. Once it has infected a user’s system, a fee must be paid within the allotted time in order to regain access. If a user fails to pay the fee, Stampedo begins to delete random files on their computer within six hour intervals.

Malware attack targets European energy companies
The Labs team at malware protection company SentinelOne has discovered a sophisticated malware campaign that's specifically targeting at least one European energy company.
The malware, called SFG, is the mother ship of an earlier malware sample called Furtim, which targets the industrial automation control systems with sophisticated malware and acts as dropper to deliver a payload which could be used to extract data or potentially shut down the energy grid.

90 percent of security events are caused by bots
Bots account for 49 percent of all internet traffic, most of which is from malicious 'bad bots' according to website security company Incapsula.
Of course there are good bots too, such as the crawlers used by major search engines, but according to Incapsula’s figures 90 percent of all security events are caused by bots, and 66 percent of all bot activity is malicious.

Facebook malware infects 10,000 users in two days
A new malware was spotted by security researchers at Kaspersky Lab, targeting Facebook users. According to the researchers’ new report, there have been 10,000 victims in two days.
The malware has two stages: firstly, an unsuspecting victim gets a message from a Facebook friend, saying they had mentioned them in a comment. But when the victim clicks to see the comment, they instead download a bunch of malware, including a Chrome add-on which can take over the victim’s Facebook account, once they log back in.

New macOS malware gives hackers complete access to your files
For security reasons, out of the box macOS is configured to only allow software from the App Store and identified developers to be installed. However, there are times when users may also want to run apps from other sources, in which case it is possible to enable a no holds barred setting. But, along with the extra freedom, it also exponentially increases the risk of running into malware.
You may be inclined to believe that you can stay safe by sticking to known download websites, but that is not always the case. Bitdefender has uncovered a new Mac malware, called Backdoor.Mac.Eleanor, that poses as a document converter on what the security company calls "reputable sites". When installed, it gives hackers complete access to your Mac.
