
Unmanaged open source code could put companies at risk
More than half the code found in commercial software packages is open source, but if it isn’t properly tracked businesses might be in the dark on the number of vulnerabilities and license compliance issues that exist in their applications.
Software supply chain specialist Flexera has released a report looking into the state of open source license compliance, based on analyzing data from 134 software audits.

Phishing gets more personal and harder to detect
An analysis of phishing attacks in the final quarter of 2018 reveals the majority of attacks showed an increase in target personalization, making them considerably more difficult to detect.
The study by email protection start up INKY shows 12 percent of phishing attacks in the period took the form of corporate VIP impersonations, 10 percent were sender forgery and six percent were via corporate email spoofing.
Three stages of risk-based vulnerability management: Crawl, Walk, Run
The market is saturated with hundreds of security products, and companies spend billions of dollars each year on cybersecurity spend (expected to top $100 billion by 2020). Yet breaches and hacks are still in the news every day, because cybersecurity is such a tough problem. Organizations have a massive and exponentially growing attack surface -- there are a myriad of ways by which networks can be breached. Analyzing and transforming the enterprise cybersecurity posture is not a human-scale problem anymore. An enterprise vulnerability management program is the cornerstone for any modern cybersecurity initiative and helps security teams proactively understand and improve their security posture to avoid breaches and protect the business from brand and reputation damage, as well as loss of customer trust.
Understanding and acting on data output from your vulnerability assessment scanner is a critical component of your vulnerability management program. However, if your scanner is identifying vulnerabilities by the thousands every time a scan completes, your team will soon be left overwhelmed and struggling with how to proceed. Failure to address vulnerabilities in a timely manner due to the high volume of alerts is very problematic. And of course, most of these vulnerabilities are bogus or merely theoretical. Traditional vulnerability management programs leave you drowning in data, but starving for insights.

Machine learning tool helps prioritize vulnerabilities
One of the keys to keeping systems secure is to effectively prioritize vulnerabilities. Given the volume, with 16,500 new vulnerabilities disclosed in 2018 alone, though this is a tough task.
To help businesses focus on the highest risks, Tenable is launching a new Predictive Prioritization tool that uses machine learning to zoom in on the three percent of vulnerabilities with the greatest likelihood of being exploited in the next 28 days.

New cloud app helps businesses understand their IT environments
As systems become more complex it can be hard for enterprises to understand their IT environment, which presents a problem for operations and security teams.
Cloud-based security specialist Qualys is launching a new IT Asset Inventory cloud application to provide quick analysis of complex and interconnected global IT environments, and help collaboration on security remediation efforts.

Number of DDoS attacks falls but sophistication improves
2018 saw a decline of 13 percent in the overall number of DDoS attacks when compared to the previous year, but cybercriminals are turning to longer, more sophisticated, mixed and HTTP flood attack techniques.
This is revealed in Kaspersky Lab's DDoS Q4 2018 Intelligence Report, which also shows the average attack duration has grown. Compared with the beginning of the year, the average length of attacks has more than doubled -- from 95 minutes in Q1 to 218 minutes in Q4 2018.

Trakt tardily notifies users of data breach that took place over four years ago
Users of Trakt -- a service for "scrobbling", or tracking the movies and TV shows you watch in the likes of Plex and Kodi -- have received emails from the company notifying them of a data breach that took place way back in 2014.
Trakt says that although the security breach took place over four years ago, it only recently discovered it. The company says that an investigation is underway, but that it believes a "PHP exploit was used to capture data", including users' emails, usernames, encrypted passwords, names and locations.

Microsoft continues to beat Google in battle of the enterprise apps
A new survey from identity platform Okta shows that 67 percent of knowledge workers prefer Microsoft Word over Google Docs, while only 15 percent report the opposite.
Another 16 percent identify Google Docs as a top-three most frustrating app. When it comes to email, 49 percent prefer Microsoft Outlook over Gmail, while 35 percent report the opposite.
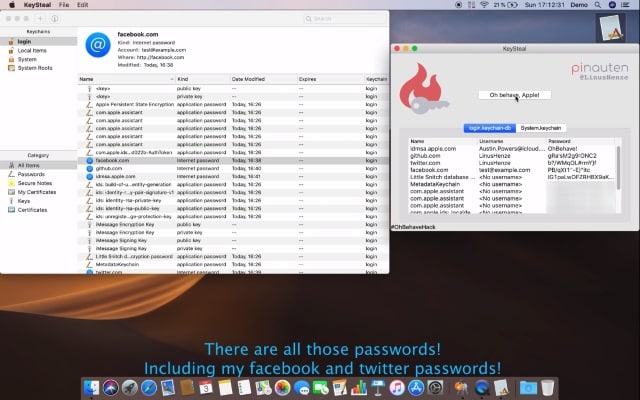
KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain.
Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS.

Airline e-ticketing systems put passenger data at risk
Airlines could be putting the personal data of their passengers at risk by using unencrypted links, according to a new report.
Researchers at security and data management company Wandera have uncovered a vulnerability affecting a number of e-ticketing systems that could allow third parties to view, and in some cases even change, a user's flight booking details, or print their boarding passes.
Google launches new tools to help protect your accounts
To coincide with Safer Internet Day, search giant Google is launching two new tools to help users detect if their username and password have been compromised.
Google's own research published today shows that many people still reuse passwords. The new tools are designed to raise awareness of account issues.

Most people believe they're more secure online than they really are
New research commissioned by Google, carried out by Harris Poll and released to coincide with Safer Internet Day suggests there is a gap between perception and reality when it comes to online security.
The majority of people (69 percent) give themselves an A or B when it comes to protecting their online accounts -- only five percent give themselves a D or an F. In fact, most people (59 percent) believe that their accounts are safer from online threats than the average person and 61 percent say they are too smart to fall for a phishing scam.

Instagram to introduce 'sensitivity screens' to hide self-harm images
The head of Instagram has announced plans to introduce "sensitivity screens" in the wake of concerns about the spread of photos of self-harm on the image-based social network.
Adam Mosseri says that Instagram will use image-blurring similar to that used on Facebook to hide graphic content. The move comes in the wake of the suicide of a British teenager, the parents of whom said self-harm images on Instagram were a contributing factor.

New tool makes it easier to secure IoT devices
Internet of Things devices are appearing in more and more companies, but with them comes the threat of cyberattacks.
To reduce this risk Extreme Networks is launching a simple security solution to help organizations protect unsecured IoT devices.

Cisco joins Apple in calling for a US version of GDPR data protection and privacy laws
The roll out of GDPR (General Data Protection Regulation) has changed the face of privacy and data protection for millions of people across Europe. The regulation not only grants people access to the personal data companies hold about them, but also controls how this data can be used and transferred.
Apple's Tim Cook has already voiced his support for GDPR and said that the rest of the world should implement similar regulation. Now he has been joined by Cisco in calling for data laws to be embraced by the US as they have been in Europe.
