
Navigating 20 years of cybersecurity: The evolution of patch management
As we approach the 20th anniversary of Cybersecurity Awareness Month, it's crucial to reflect on the progress made in patch management, a fundamental cybersecurity practice aimed at helping organizations mitigate the risk of unpatched vulnerabilities -- the primary gateway for attackers to breach organizational systems and deploy ransomware and other malware.
In 2003, patch management awareness was low, but it wasn't as critical to global cybersecurity as today because cybercrime was less developed. Automated exploits for known vulnerabilities and ransomware, which now monetizes attacks, hadn't emerged yet.
This week sees Microsoft starting to embrace a password-free future for Windows 11
Passwords are a blessing and a curse, serving to secure files, devices and more, while simultaneously being burdensome and, to some extent, offering a false sense of security. With the update that is rolling out to Windows 11, Microsoft is fully embracing the passwordless future the company so desires.
Microsoft points out that passwords are nowhere near as secure as people might think, citing the statistic of 4,000 password attacks every second as proof. The Windows 11 update introduces greater password free security thanks to Windows Hello and wider support for passkeys.

Staying safe online by bringing nonstandard applications into the identify lifecycle
This year marks the 20th Cybersecurity Awareness Month, and today, the prevailing theme, "It’s easy to stay safe online," remains a timely reminder. The message is clear: online safety can be achieved with the proper knowledge and tools. This comes with a bit of a caveat, however, as many of our current security processes are manual and rely on the end user's discretion and action, such as turning on MFA. Adding further complexity is the ever-growing challenges posed by nonstandard applications, which do not work with established security standards like single sign-on.
A report by Netskope paints a grim picture with its concerning findings. For instance, the report found that 97 percent of apps used within enterprises operate outside the traditional identity perimeter. While the ubiquity of these nonstandard applications is undeniable, the lack of oversight in their security is alarming. The Ponemon Institute's research reveals that only 34 percent of organizations are proactive in prioritizing the security of nonstandard applications. When educated on the risks, this figure jumps dramatically to 82 percent. People care once they understand the impact on the business.

You can't win: Learning to live with security pessimism
Cybersecurity can, at times, feel like a thankless and invisible task. The punishment for a mistake is immediate and ruthless, the reward for success next to non-existent, because how do you recognize the absence of a breach? But this isn’t a new scenario; the IT industry has dealt with this outlook for decades. The job of an IT department is to be invisible, but when something does go wrong all eyes are inevitably on them to fix it.
In a threat landscape where there exists a constant push to innovate, adapt and breach, there are only three possible outcomes for the IT industry: defeat, indefinite struggle, or complete structural collapse.

Microsoft releases KB5030219 update to fix a cornucopia of security issues and other Windows 11 problems
It's the time of the month when Microsoft releases its regular security updates, and this September is no different. As the KB5030219 update is a security update, it is rolling out automatically to all Windows 11 users.
As well as numerous security fixes, the KB5030219 update removes a blank item from the Sticky Keys menu, a problem introduced by the previously released KB5029351 update.

How machine learning safeguards organizations from modern cyber threats
2024 is fast approaching, and it seems likely that the new year heralds the same torrent of sophisticated malware, phishing, and ransomware attacks as 2023. Not only are these long-standing threats showing few signs of slowing down, but they're increasing by as much as 40 percent, with federal agencies and public sector services being the main targets.
Meanwhile, weak points like IoT and cloud vulnerabilities are making it tougher for cybersecurity pros to secure the wide attack surface that these edge devices create.

Hiding undetected: Why security teams can no longer overlook HTTPS decryption
Decrypting HTTPS (TLS/SSL) traffic at the network perimeter is a vital step in protecting against malware and other online threats. Most of today’s web traffic is encrypted and presents an obvious hiding place for threat actors to deliver cyberattacks, since many network security controls aren’t set to inspect encrypted traffic. Consider recent findings from WatchGuard’s Threat Lab in its Q4 2022 Internet Security Report (ISR). While the report showed an apparent decline in overall malware volume, the Threat Lab analysts found a much higher prevalence of malware being delivered over encrypted connections when they looked closer at decrypted HTTPS traffic. These results came from a mere 20 percent of devices decrypting TLS and indicate the other 80 percent would also show malware volume is up, but hidden -- which mirrors findings from previous quarters.
Despite this trend, it’s common for teams not to enable decryption at the firewall due to the complications it can present. The process requires resources to decrypt and then re-encrypt traffic passing through a gateway device, as well as next-gen firewalls (NGFW) or unified threat management (UTM) appliances that use significant computing horsepower, all which impact network performance. Then, introducing decryption while managing the performance of other security tools and their varying uses could be difficult. Today, however, tabletop UTM/NGFW solutions can perform this process at the speed of the incoming WAN connection. So now, users’ main objection is the initial configuration of TLS/SSL decryption, and the need for exceptions for certain applications.
Millions of Freecycle users need to change their passwords following a huge data breach
Swap-unwanted-stuff-for-free site Freecycle has acknowledged a security breach that took place at the end of last month. Hackers were able to access a wealth of data including usernames, User IDs, email addresses and passwords.
The organization says that it has notified the "appropriate US authorities" of the incident, as well as the Information Commissioner's Offier (ICO) in the UK. Few details of what happened have been revealed, but Freecycle is advising all members to change their account passwords as a security measure.

Microsoft jogs users' memories about disabling old TLS protocols in Windows
Hot on the heels of a reminder about the end of support for Windows 11 21H2, Microsoft has reminded everyone that Windows will soon have TLS 1.0 and TLS 1.1 disabled.
Transport Layer Security (TLS) has been around for a number of years, with TLS 1.0 not only dating back to 1999, but having been superseded by far more secure versions. TLS 1.2 and TLS 1.2 are now very much the norm, so Microsoft is following others in the industry by dropping 1.0 and 1.1.

You can't win: Learning to live with security pessimism
Cybersecurity can, at times, feel like a thankless and invisible task. The punishment for a mistake is immediate and ruthless, the reward for success next to non-existent, because how do you recognize the absence of a breach? But this isn’t a new scenario; the IT industry has dealt with this outlook for decades. The job of an IT department is to be invisible, but when something does go wrong all eyes are inevitably on them to fix it.
In a threat landscape where there exists a constant push to innovate, adapt and breach, there are only three possible outcomes for the IT industry: defeat, indefinite struggle, or complete structural collapse.
Chrome password sharing feature makes it easier to share login credentials... with limitations
There are many reasons for wanting to share passwords, and it is surprising -- and also a source of irritation -- that doing so is not easier. But Google is looking to change this by introducing a dedicated password sharing option to Chrome.
Users of the browser will soon be able to use the Password Manager function of the browser to quickly share login details with others. To start with, it appears that Google will limit sharing to people you have added to your Google Family Group, but it is possible that this will be opened up further in future.

Microsoft reveals how to mitigate the Downfall vulnerability affecting Intel processors running Windows 10 and Windows 11
Following on from the Meltdown flaw and other related vulnerabilities, a more recent security issue was discovered in the form of Downfall. Tracked as CVE-2022-40982, exploitation of the flaw is known as a transient execution attack and it affects Intel CPUs.
Microsoft has not only acknowledged that the problem exists, but has now provided details of mitigation techniques that can be used. In security advisory KB5029778, the company gives instructions for users of Windows 10, Windows 11 and Windows Server.
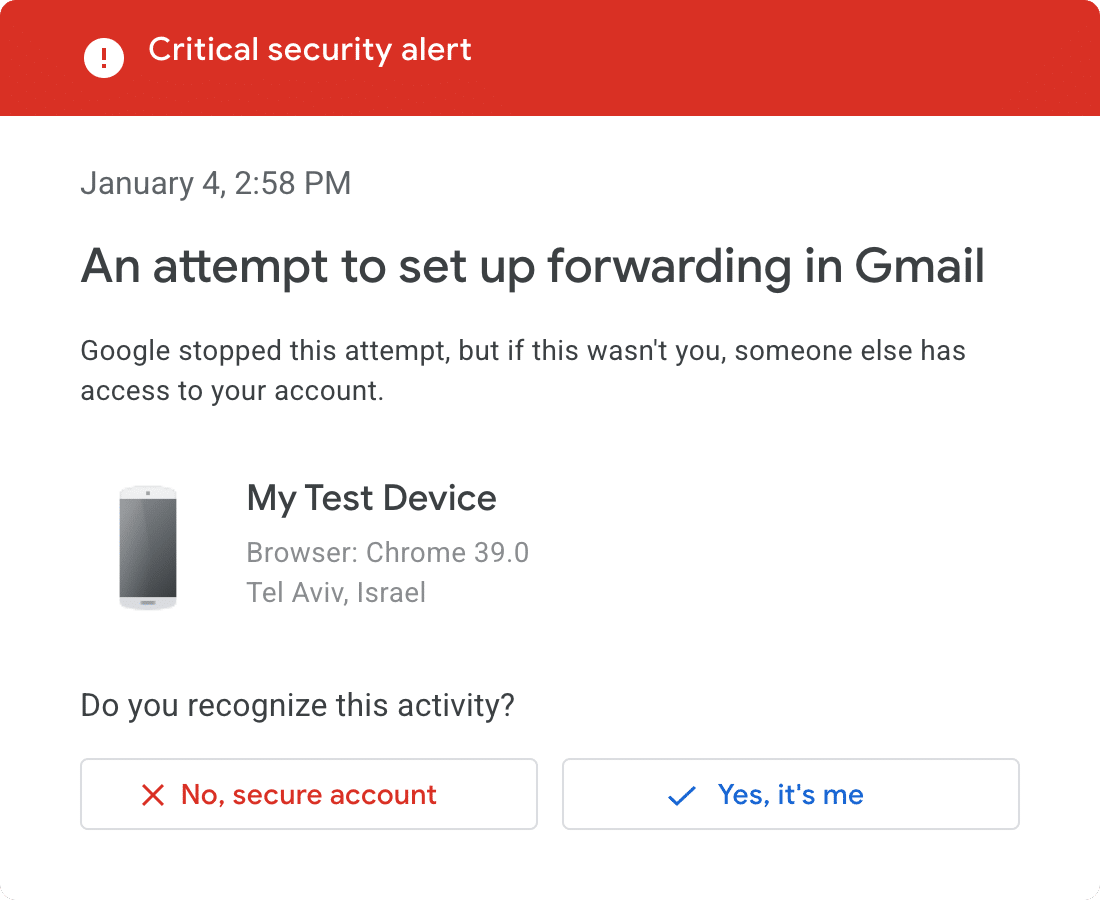
Google is ramping up Gmail security by requiring verification for filters, forwarding and IMAP
Google is introducing what it is referring to as "stronger protection for additional sensitive actions taken in Gmail".
It's a security measure that builds on safeguards added to Google Workspace accounts last year. It means you will start to see "Verify it's you" warnings when you try to do certain things with your Gmail account, requiring user verification before particular settings can be changed.

Meta is expanding WhatsApp-style end-to-end encryption to Messenger
Security is vital for digital communication, and that's why the likes of Telegram and WhatsApp's end-to-end encryption (E2EE) is so important and popular. Meta has long been keen to expand this security feature to its various other messaging platforms, and now the Facebook-owner has announced that it is implementing E2EE for all Messenger users.
The company points out that this is currently a test phase, so while more and more people will see immediate security enhancements, the rollout will not be complete until the end of the year.

Update WinRAR right now to patch high-severity security flaw
Users of the archiving utility WinRAR are being advised to update their software as soon as possible following the discovery of a serious Remote Code Execution vulnerability.
Tracked as CVE-2023-40477, the security flaw was discovered back in June and it allows malicious code to run when opening a RAR archive. Two months on, the issue has been fixed, but users of the software will have to ensure that they have the latest update installed to guarantee protection.
