Apple: iCloud is safe, but your passwords may not be

A group of hackers that goes by the name Turkish Crime Family, claims to have access to hundreds of millions of iCloud accounts, and it wants Apple to pay $75,000 in Bitcoin or Ethereum or $100,000 in iTunes gift cards to delete the compromised credentials.
This may lead one to believe that the collective has managed to hack iCloud, but according to Apple there "have not been any breaches" in any of its systems. "The alleged list of email addresses and passwords appears to have been obtained from previously compromised third-party services."
Facebook Messenger borrows from Slack with Reactions and mentions
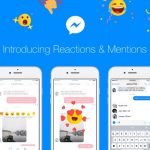
Facebook is not shy about stealing features from other messaging tools, and it's usually Snapchat that is used as inspiration. With the latest update to Facebook Messenger, it's Slack that is being borrowed from.
Today Facebook Messenger gets two new features: Reactions and mentions. These work in very much the way you would expect, and Reactions make a successful transition from the Facebook newsfeed to Messenger after having made a brief appearance to a testing group recently.
Why ethical hacking is the top job of 2017

61 percent of UK businesses believe they will suffer from cyber crime in 2017, according to new research from Mimecast. These anxieties are justified: two thirds of large UK businesses were targeted by cyber criminals last year.
As the threat posed by cyber crime increases, businesses now invest more than ever in training, technology and skills -- global cyber spending is predicted to reach $1 trillion by 2021.
Apple buys automation tool Workflow, tweaks some features, and offers it to iOS users for free
Automation tools like IFTTT continue to be popular, and as if to prove this, Apple has just bought the iOS app Workflow. Working in a similar way to Automator for macOS, Workflow brings task-oriented automation to iPhone and iPad users.
There's good news to top off the acquisition revelation. Apple is not only keeping Workflow up and running rather than shutting it down, it's also hanging onto the original team of developers behind the app. Even better, Apple is making Workflow available free of charge, dropping the previous $2.99 price tag.
What challenges do Industrie 4.0 projects face?

Algorithms are at the heartbeat of Industrie 4.0 projects, according to Gartner, and that’s going to result in 30 percent of Industrie 4.0 projects sourcing algorithms from leading algorithm marketplaces by 2020.
That means a jump of less than five per cent, compared to what we currently have in the market.
New platform protects industrial IoT devices

Internet of Things devices are the latest threat vector that businesses have to deal with, introducing a potential extra weakness into corporate networks and leading experts to warn of increased risk.
To help guard against the threat, Mocana Corporation is introducing a new security platform designed to protect IoT devices and associated device-to-cloud communications.
Cobbler stores secret notes in an encrypted file

Cobbler is a tiny portable utility which stores plain text notes -- passwords, bank details, whatever you need to keep private -- in a secure and encrypted file.
Launch the program and you’re prompted for a master password. Enter something lengthy and secure, or press Ctrl+G to generate a strong passphrase for you, and a basic editor appears.
The role of IT decision makers in purchasing new technology

IT decision makers (ITDM) in the EMEA region serve as their company's "gatekeepers" and primary influencers, when it comes to choosing new technology purchases for the company. This is according to a new report by Spiceworks, which digs deeper into the roles of ITDMs and business decision makers (BDMs) when it comes to purchasing new technologies.
The study, "ITDM vs. BDM: Tech Purchase Superheroes," says BDM’s role is to "give final approval for technology funds and purchases."
71 percent of Android phones on major US carriers have out of date security patches

Slow patching of security flaws is leaving many US mobile users at risk of falling victim to data breaches according to the findings of a new report.
The study from mobile defense specialist Skycure analyzed patch updates among the five leading wireless carriers in the US and finds that 71 percent of mobile devices still run on security patches more than two months old.
5 things to keep in mind when building an Alexa skill

A team of us at Red Badger, which consisted of myself, Marcel, Graham and Roman, had two weeks to play around with Amazon’s Alexa and build a sommelier skill to recommend wine pairings to your food. We’re writing a four-part series to take you through what we learned from our varied perspectives.
There’s been so many blog posts written about the rise of chatbots and Voice User Interface (VUI), some even marking 2017 to be the year of the bots.
GNOME 3.24 Linux desktop environment is here
My absolute favorite desktop environment for Linux is GNOME. Quite frankly, if the DE went away tomorrow, I might have to rethink my use of Linux entirely. Yeah, I am that passionate about it. Environment aside, the GNOME also includes a collection of applications, creating a coherent user experience.
Today, GNOME reaches version 3.24, code-named "Portland." While it looks great, it is hardly a monumental change. Moving from 3.22, we see some new features and applications, but on the UI front, there are improved icons too. In fact, they have doubled from 256×256px to 512×512px! Not only can these icons scale larger, but they are more vibrant and intricate too. Overall, there are many new aspects of GNOME to excite fans.
User-Agent based attacks are a low-key risk that shouldn't be overlooked

Old, unpatched vulnerabilities allow hackers to take over systems using the User-Agent string -- an elementary part of virtually every HTTP request.
It is a known fact that while the majority of vulnerabilities discovered or reported are fixed by the vendor and a patch is issued, many systems end up not being patched in a timely manner or even at all, for that matter. There are many possible reasons for that, the most common being:
DoubleAgent exploit uses Windows' Microsoft Application Verifier to hijack antivirus software

Security researchers at Cybellum have revealed details of a zero-day exploit that makes it possible for an attacker to take full control of antivirus software. The technique can be used to take control of just about any application, but by focusing on antivirus tools, the illusion of safety offered to victims means they are likely to be completely unaware of what is happening.
The attack works by exploiting the Microsoft Application Verifier that's built into Windows. It is possible to replace the tool with a custom verifier which can then be used to inject malicious code into any chosen application. A number of well-known antivirus tools -- including Avast, BitDefender, ESET, Kaspersky, and F-Secure -- are vulnerable, while patches have been released for others.
Three penetration testing tips to out-hack hackers

It should come as no surprise that hackers have been busy lately. According to my go-to resource on hacking stats, the Identify Theft Resource Center, breaches jumped from 780 in 2015 to 1,093 in 2016. Is there a way to take a proactive approach to data security that doesn’t involved investing in more firewalls or virus protection software and ultimately get to the real-source of vulnerabilities?
Yes and yes. The answer is penetration testing, or pen testing for short. It’s a white-hat approach that challenges organizations to expose the vulnerabilities inside their own systems by understanding how a cybercriminal could exploit their internal information.
Three UK suffers new data breach

A couple of bizarre incidents happened to Three users in the UK recently, and the media are suspecting the company might be facing a new data breach.
According to a report by The Guardian, some customers, logging into their accounts, were "presented with the names, addresses, phone numbers and call histories of strangers."
Recent Headlines
Most Commented Stories
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.