
Intuit launches agentic AI consumer platform for year-round money management
Intuit has introduced an all-in-one Agentic AI-driven consumer platform that combines Credit Karma and TurboTax into a single system to deliver year-round control of personal finances. The company says this unified platform will help users manage credit, debt, wealth building, and tax preparation in one place, powered by advanced AI and supported by a network of 13,000 human experts across the United States.
The platform is built to predict and automate key financial actions, offering what Intuit calls “done-for-you” daily management and wealth optimization. It uses Agentic AI to identify opportunities for users to improve their money situation while combining automation with personalized guidance from human experts. According to the company, this hybrid approach will provide faster access to cash, smarter tax management, and ongoing financial support tailored to individual circumstances.

Identity for AI aims to bring accountability and trust to enterprise AI systems
Ping Identity has introduced Identity for AI, a new enterprise solution aimed at securing and enabling the growing use of autonomous AI agents. The platform focuses on embedding trust, visibility, and accountability into agentic systems as businesses begin to adopt AI-driven processes across operations and commerce.
The company said the technology will help organizations manage the risks and opportunities of agent-based automation by making sure that each AI entity operates within defined, auditable boundaries.

CISO budgets increase with identity and data protection top priorities
A new study from RSAC finds most CISOs’ budgets increased between 2024 and 2025 and their top areas of investment for 2025-2026 are identity and data protection.
While 76 percent of CISOs report that their budgets for 2024-25 had increased, just 12 percent saw their budgets decrease.

IT leaders want to see AI integrated into their technology stack
A new survey of more than 830 global IT decision makers finds that 94 percent are looking for ways to integrate AI into their technology stack, with 33 percent naming it a top priority. However, only 19 percent say that demonstrating AI usage and effectiveness is a top priority for next year.
The study from Flexera also shows that 80 percent of IT leaders report increased spending on AI applications and over a third believe they’re overspending. Additionally, 73 percent say their SaaS and cloud infrastructure costs have risen, with 67 percent stating that cloud expenses weigh heavily on their IT budgets.
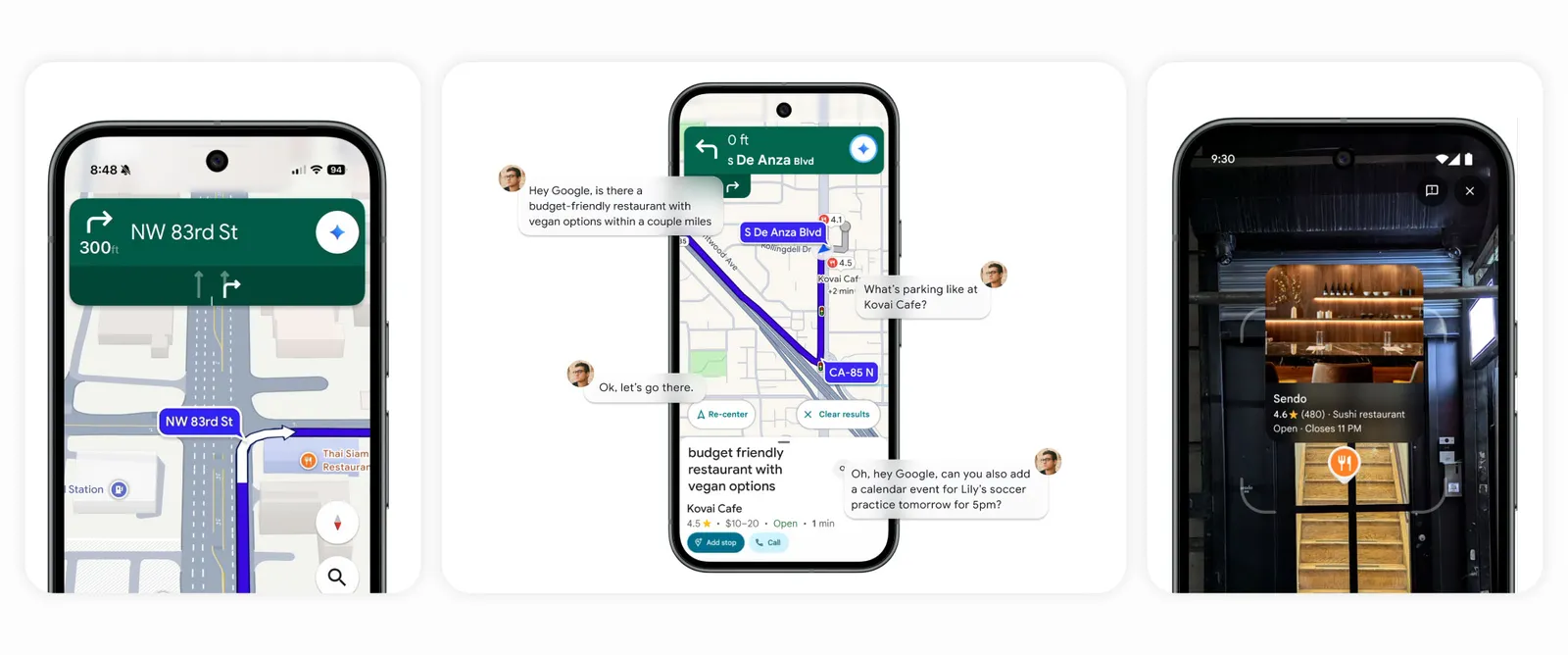
Google Maps to receive AI upgrade powered by Gemini
Google Maps is to receive an AI upgrade powered by the tech giant’s Gemini. This will add a conversational, hands-free experience to the app that is intended to make navigation smarter and less distracting.
It represents yet another step in Google’s ongoing integration of the generative model into its most widely used products. The firm added AI smarts to Google Earth not so long ago.

AI makes holiday shopping scams harder to spot
As we approach the busiest time of the year for online shopping, scammers and phisherfolk are also preparing for a seasonal bonanza. 1Password has surveyed 2,000 American adults to learn how people are protecting themselves -- or not -- from phishing scams.
It finds that 66 percent of respondents say they’ve noticed more 'scammy' messages, phone calls, and ads since AI became more prevalent. In addition 82 percent of respondents have been phished, or have come dangerously close to it.

81 percent of security teams lack visibility into AI coding
While AI adoption is now nearly universal, governance and visibility have failed to keep pace, according to a new report from Cycode.
The study shows that 97 percent of organizations are already using or piloting AI coding assistants, and all confirm having AI-generated code in their codebases. Yet, despite this near-total adoption, 81 percent lack visibility into AI usage and 65 percent report increased security risks associated with AI.

Cooler Master launches QUBE 540, a compact and customizable PC case for modern builders
Cooler Master has announced the QUBE 540, a new compact PC case that can be built vertically or horizontally to suit different spaces and setups. The case offers a modular interior and supports open-source, downloadable 3D-printable parts, allowing users to build their own unique custom system.
QUBE 540 can stand upright or lie flat, making it a useful choice for anyone with smaller living or working spaces. Cooler Master describes the case as suitable for small apartments, dorm rooms, and creator studios, reflecting a growing trend toward compact but powerful PC builds. It measures 425 x 225 x 425mm excluding protrusions, or 438.5 x 225 x 492.1mm with them. It has an internal volume of 40.64L.

UK police trial AI system to support frontline officers with procedural advice
Humberside Police in the UK has released results from a trial of an AI assistant designed to guide officers in the field, suggesting that it could save more than 23,000 officer hours per year. The “Project Moriarty” pilot with Coeus Software looked into how British police forces could use AI to boost efficiency and consistency.
AI is inevitably finding its way into frontline policing, as it is in other professions, and the results from the Humberside Police trial show both its promise and its limits.

82 percent of finserv organizations suffered a data breach in the last year
A new report, based on a global survey of 250 decision makers at large financial services organizations of over 5,000 employees, shows that 82 percent have suffered a data breach via cyberattack, or a data leak, an unintentional exposure of sensitive data, in the past year.
The report from Blancco Technology Group finds 43 percent of breaches or leaks were attributed to stolen devices and drives.

Experts warn AI tools are fueling a rise in scams targeting older adults
Experts are warning that the rapid development and growing availability of artificial intelligence tools is leading to an alarming rise in cybercrimes targeting older adults. Since technology alone cannot stop social engineering, specialists suggest that seniors learn to recognize the recurring scam patterns that criminals have used for decades to steal money and personal data.
The surge in AI is giving cybercriminals new ways to deceive people, with elderly users often among the main targets. According to The Hidden Cost of Scams [PDF] report by Independent Age, adults over 65 in the UK lose an average of nearly £4,000 each, with total losses reaching about £7.4 billion.

Microsoft is killing off Defender Application Guard for Office
More than a year-and-a-half after announcing its retirement, Microsoft has revealed its plans to fully remove Defender Application Guard from Office.
The journey has been a long a slow one for the this security feature which isolates untrusted Office documents in a virtualized contained. Deprecation was first announced way back in November 2023, and the process of complete removal will not be finished until the end of 2027.
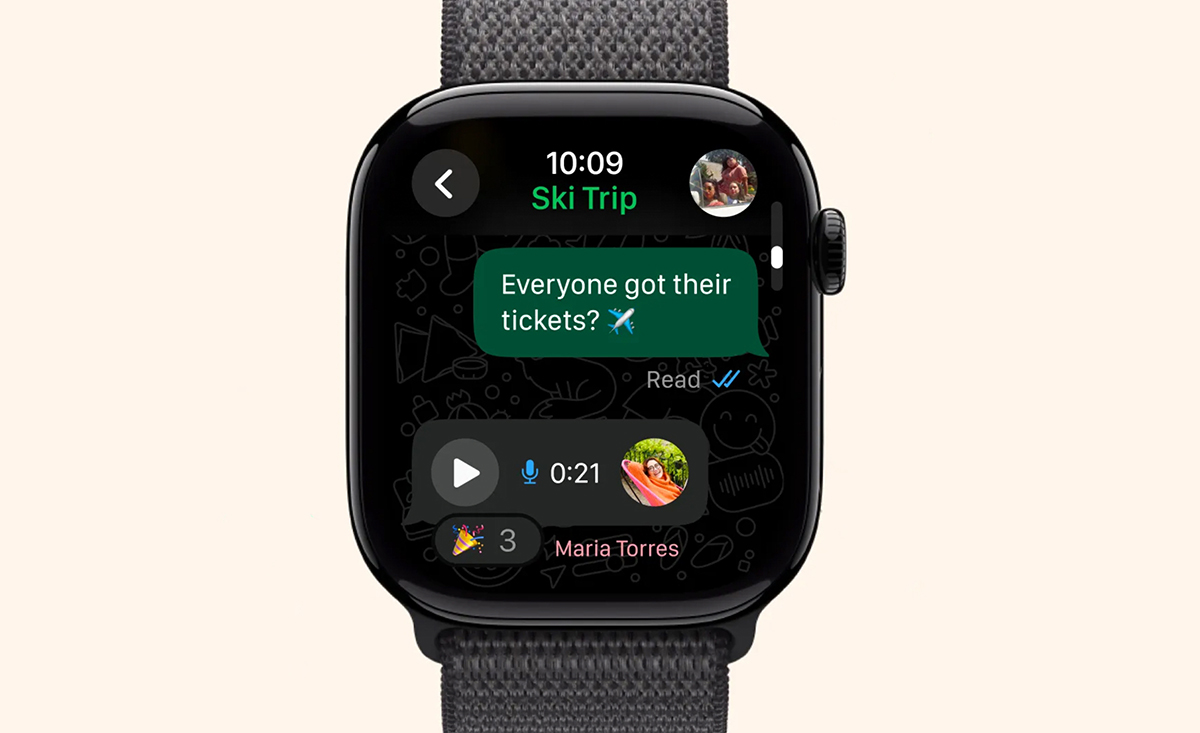
Finally! WhatsApp launches official Apple Watch app with messaging and voice note support
After years of requests, WhatsApp is finally, fully available on Apple Watch. The app gives users access to many of the core messaging functions found on the phone version, including reading and responding to chats, recording and sending voice messages, and viewing photos and stickers.
The new app will allow users to check messages, respond with quick replies, and listen to or send voice notes directly through the watch. If you rely on WhatsApp to stay in touch with friends, family or work, you can now use it while on a run, during a commute, or in situations where using a phone isn’t possible.

Why, finally, all eyes are on OT [Q&A]
Operational technology and IT have historically tended to follow separate paths. But in recent times the spread of Internet of Things devices has seen the two moving closer together.
We spoke to David Montoya, Paessler global business development manager OT/IoT, to discuss how the OT landscape has evolved and why businesses need to be on top of the change.

Microsoft hits Windows 10 users with misleading ‘end of support’ messages
Given the publicity Microsoft has given to the end of mainstream support for Windows 10, there are few users who are unaware if this fact. And with the promotion of the Extended Security Updates (ESU) program, most are also aware that there is still a way to get updates.
So, there was a mixture of surprise and anger when users signed up to receive Extended Security Updates started it see a message informing them that “Your version of Windows has reached the end of support”.
