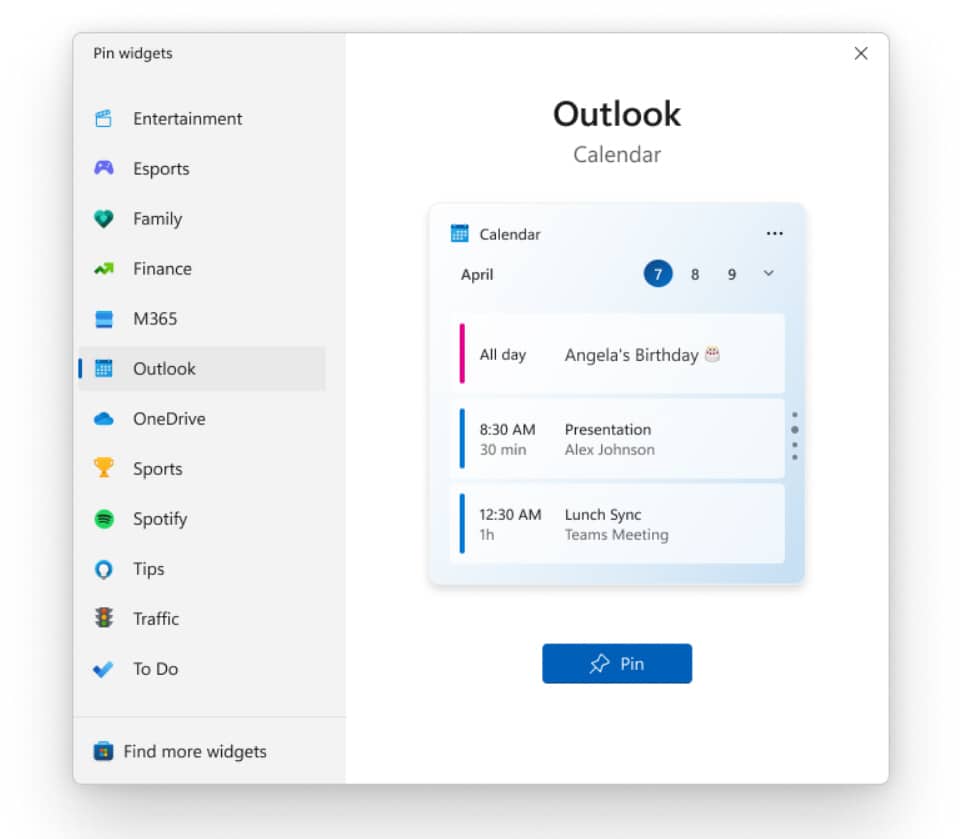
Experimental Windows 11 build comes with a new widget picker
Arriving just in time for the weekend, Microsoft has released a new Windows 11 build for Insiders in the Canary Channel.
From this flight, Microsoft has changed the name of the branch shown in the desktop watermark to ZN_RELEASE. The build also comes with new widget picker experience.
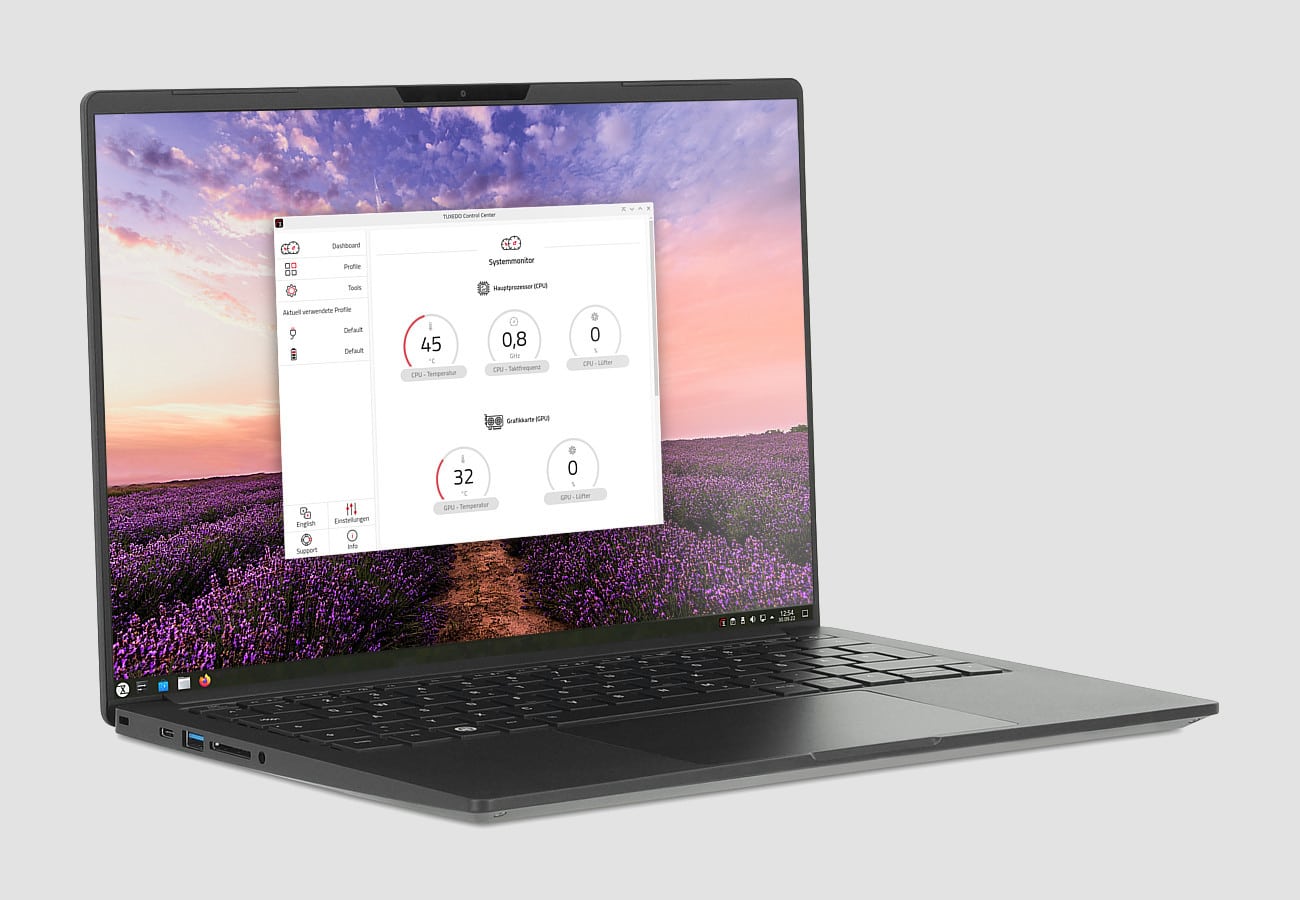
TUXEDO unveils next-gen InfinityBook Pro 14: A powerful, ultra-mobile Linux laptop
TUXEDO has announced the latest generation of its popular InfinityBook Pro 14, an ultra-mobile yet powerful business laptop featuring a 16:10 3K display, massive 99 Wh battery, and full Linux support.
The new 8th generation InfinityBook Pro 14 boasts a combination of an ultra-light and slim magnesium body, a high-end processor, and the maximum battery capacity allowed for airplane carry-on. This combination ensures maximum mobility and strong performance for business, multimedia, and even image and video editing on a premium 14-inch high-resolution display.

The key to developer job satisfaction: Give them a handle on observability
The developer talent gap is very real. According to IDC, there will be a global shortfall of four million developers by 2025. Other analyses are more dire, estimating the current shortage at 40 million developers worldwide and expected to reach more than 85 million by 2030.
While the U.S. Bureau of Labor Statistics currently indicates there are more than 1.6 million developers employed in the U.S., this number is expected to grow by 25 percent to more than two million by 2031, much faster than the average for all occupations. Despite this growth, developer demand is expected to exceed skills availability for many years to come. There are numerous causes for this, including the rapid growth of digital transformation, increasing software development complexity and more. But one thing is for certain - the fight for talent is going to be fierce, and it’s going to be essential for organizations to focus on keeping their developer talent happy and right where they are.

Cybersecurity teams are overconfident of their ability to deal with threats
A study from Immersive Labs finds that while businesses have high confidence in their overall resilience, teams are insufficiently prepared for threats.
The study, carried out by Forrester, surveyed 316 global cybersecurity training strategy decision-makers in the UK, US, Canada, Germany, and Sweden, finds that 82 percent agree they could have mitigated some to all of the damage of their most significant cyber incident in the last year if they were better prepared.
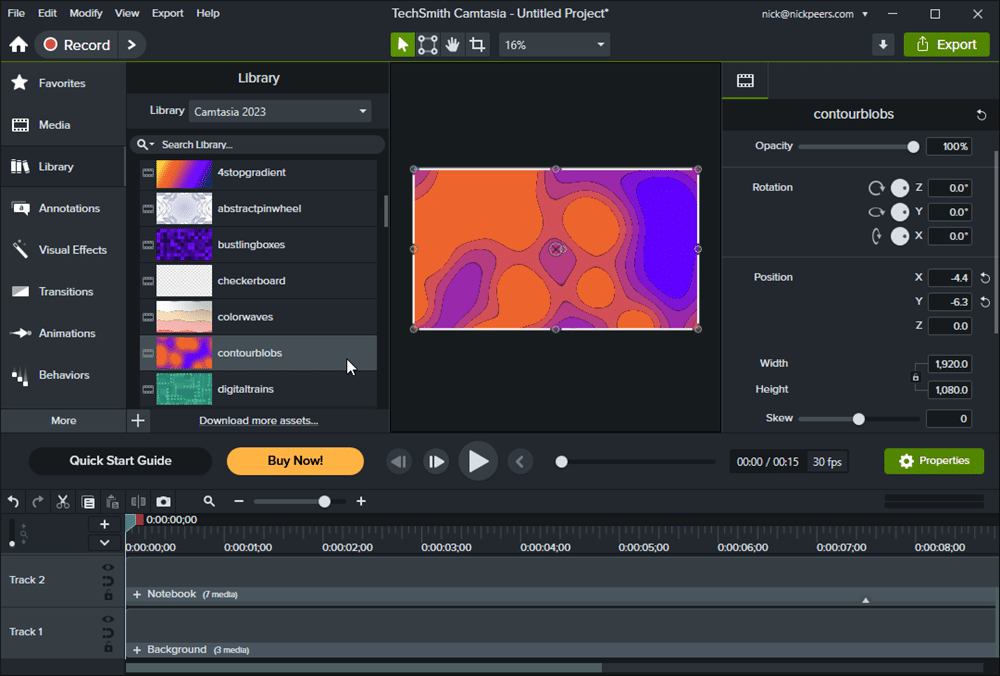
Camtasia 2023 adds new visual effects, filters and other major improvements to its roster
Michigan-based TechSmith has launched Camtasia 2023, a major new release of its professional screen recording and video editing tool for Mac and Windows.
The 2023 release focuses on two specific areas: offering enhanced visual effects and implementing various user feature requests.

Why 5G/LTE network security needs a different approach [Q&A]
The continuing rollout of 5G offers faster mobile networking which will pave the way for new apps and devices connecting to the internet and to corporate networks.
Liron Ben-Horin VP of systems engineering at OneLayer argues that this world of faster connections and more devices will need a new approach to security. We spoke to him to find out more.

Get 'Working Smarter with Microsoft Outlook' (worth $20.99) for FREE
Millions of users across the globe spend their working hours using Microsoft Outlook to manage tasks, schedules, emails, and more
Post-pandemic, many organizations have started adopting remote working, and the need to stay productive in workspace collaboration has been increasing. Working Smarter with Microsoft Outlook takes you through smart techniques, tips, and productivity hacks that will help you become an expert Outlook user. This book brings together everything you need to know about automating your daily repetitive tasks.

Don't get stuck in a honeypot
Honeypots have been around for years and are a tried and tested cybersecurity mechanism. By creating a fake environment with attractive assets, organizations use honeypots to lure attackers into a trap where their actions can be studied and learned from to improve cybersecurity measures. Simultaneously, they are protecting the business’ real assets by preoccupying the attacker with the decoys.
However, honeypots have a narrow field of view as the only activity that they detect is those that target them directly. If an attacker gains access to a network, but not through the honeypot, the business would be none the wiser. It is, therefore, crucial to have more than one honeypot -- a honeynet -- to make it effective. Yet, honeypots are very time-consuming to apply as they need to be installed in networks and systems in data centers. It can take as long as an hour to install just one and it lacks any level of scalability.

Deepfake fraud hits a third of businesses
Deepfake fraud is on the rise, with 37 percent of organizations experiencing voice fraud and 29 percent falling victim to deepfake videos, according to a survey by identity verification specialist Regula.
Fake biometric artifacts like deepfake voice or video are perceived as real threats by 80 percent of companies, with businesses in the USA most concerned, about 91 percent of organizations considering them to be a growing threat.

New community helps businesses to collaborate like scammers
Cybercriminals and fraudsters have long relied on a dark web community to exchange information on vulnerable businesses and individuals as well as trading fraud-as-a-service schemes.
In an effort to turn the tables, Sift is launching a new online community called 'Sifters' to allow its customers to learn from, interact with, and share information with each other, including on any emerging fraud threats they encounter.

Modern Attack Surface Management means going beyond the surface
Security teams today are contending with an ever-increasing attack surface and an exponentially growing volume of vulnerabilities. Yet most teams are still equipped with the cybersec equivalent of a bucket to shovel out an ocean of CVEs. Buying them another shiny new bucket pales in comparison to plugging the actual leak in your ship (or enterprise).
Vulnerabilities can’t all be patched, so prioritizing these based on business risk is the most grounded approach. While leading security teams have begun to implement more advanced vulnerability management (VM) programs, others are struggling with outdated, manually intensive and less effective ways of managing vulnerabilities without context or insights on the true risk they pose. This can only work for so long, as it requires the continuous process of monitoring, discovering, analyzing, and remediating vulnerabilities across all potential attack vectors. Even then, good old human error sneaks its way in.

Get 'Mastering Windows Security and Hardening -- Second Edition' (worth $41) for FREE
Are you looking for the most current and effective ways to protect Windows-based systems from being compromised by intruders?
This updated second edition of Mastering Windows Security and Hardening is a detailed guide that helps you gain the expertise to implement efficient security measures and create robust defense solutions using modern technologies.
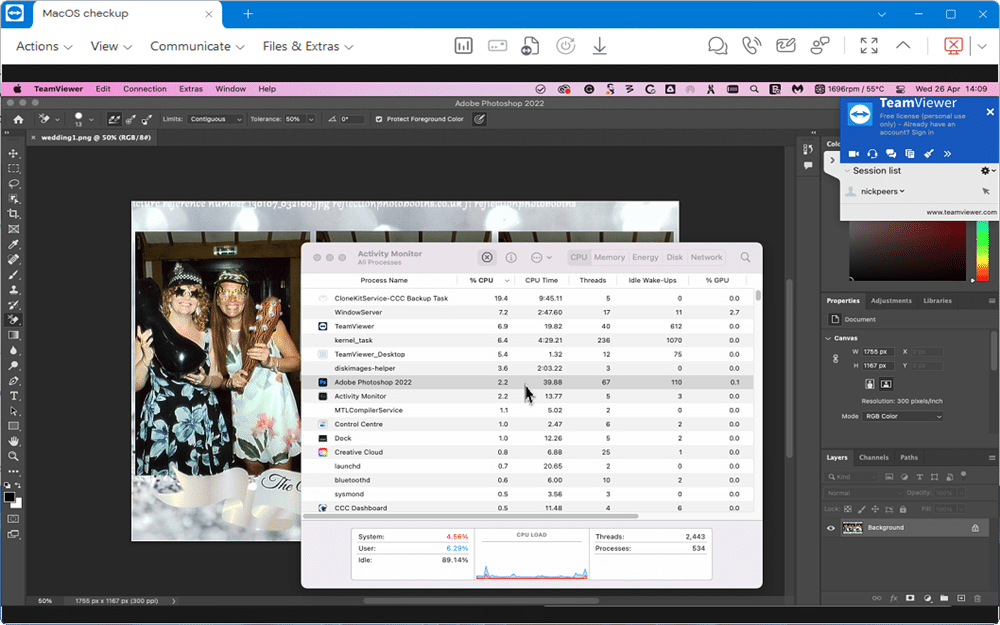
TeamViewer Remote promises to improve the performance and security of your remote desktop connections
Accessing your home or work devices from a remote location just got a lot easier -- and more secure -- with the launch of TeamViewer Remote 15.41.7, out now for Windows, Mac and Linux.
The headline new feature is a major revamp of how TeamViewer connects one user to another’s device. In place of a password-based system, users make use of session links to connect directly, and adds a new option that allows users to connect and control remote devices through any web browser.

Microsoft now lets you get Windows 11 updates faster
Updates to Windows 11 are a necessary part of using the operating system, and Microsoft releases them on a predictable schedule. Patch Tuesday (the second Tuesday of the month) is when updates are usually released to everyone, but there are exceptions.
In the case of important security updates, Microsoft may choose to release them on an out-of-band basis, but the company also releases preview versions of updates each month which anyone who seeks them out is free to install. However, Microsoft has just introduced a way to have these preview updates installed automatically if this is your preference. Here's how to do it.
Phone Link for iPhone is now rolling out to all Windows 11 users
Microsoft today announces the expansion of its Phone Link feature, finally allowing iPhone users to connect to -- and interact with -- Windows 11 PCs.
Microsoft Phone Link for iOS on Windows 11 is beginning to roll out today in 39 languages across 85 markets, with the process expected to be completed by mid-May.
