
Samsung T7 USB-C SSD is finally here
Back in January, we told you about the Samsung T7 USB-C SSD — a fast and svelte portable storage drive. There are two variants of the drive — a “T7 Touch” model which has a fingerprint reader for decryption, and a non-touch “T7” model that uses a password for the same thing.
While the touch model has been available for purchase for some time, Samsung promised the non-touch variant would hit stores in Q2 of 2020, meaning April, May, or June. Well, the T7 USB-C SSD is thankfully meeting that promised deadline, as it is available beginning today!
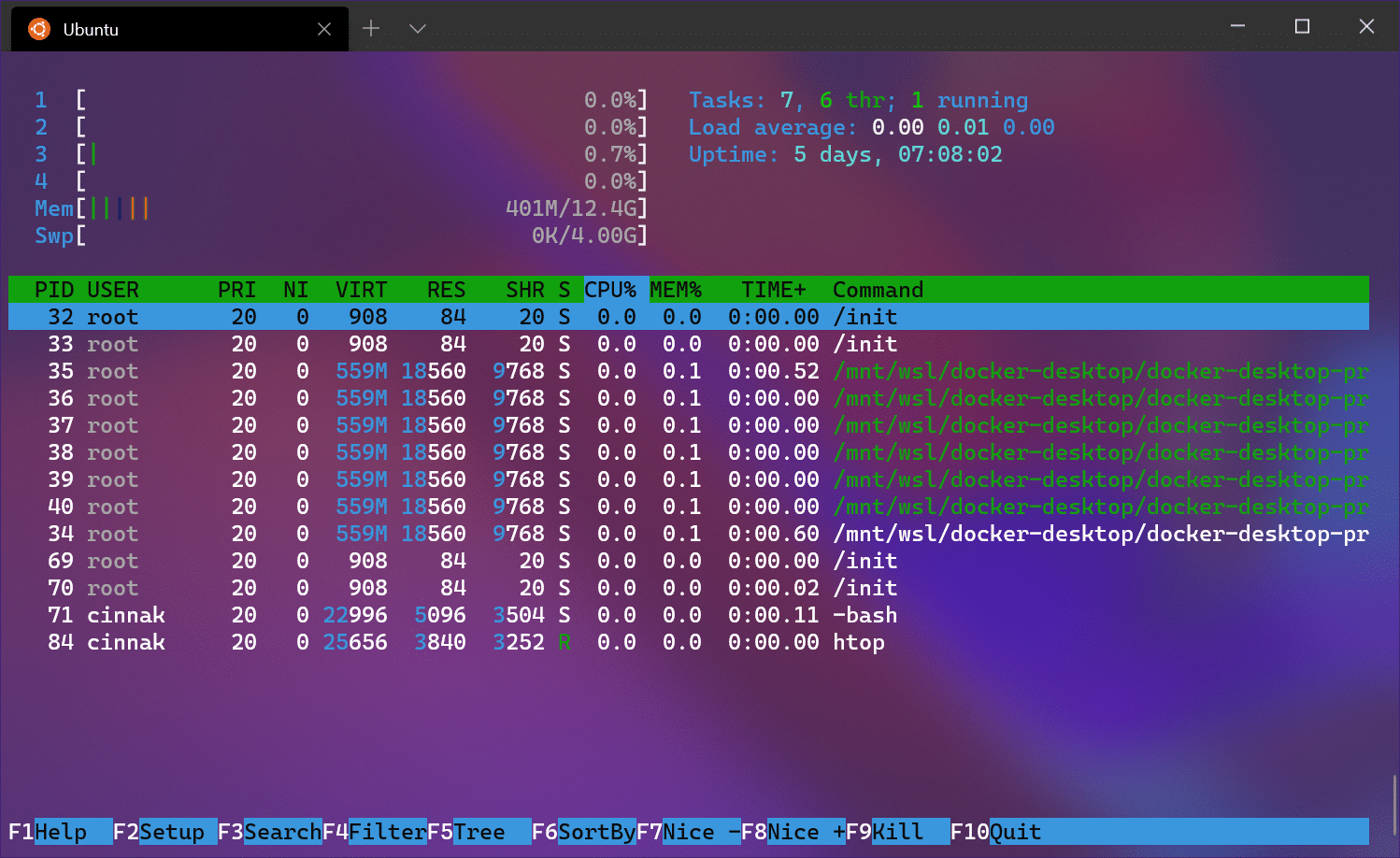
Microsoft releases Windows Terminal 1.0, download it now
At its Build developer conference last year, Microsoft took the wraps off its Linux-inspired Windows Terminal. This lets users access the Command Prompt, PowerShell, and WSL (Windows Subsystem for Linux) in the one place.
Since then, Microsoft has been adding additional features, such as multiple panes and tab re-ordering, across a number of preview versions. Most recently the software giant added mouse support and duplicate panes. Today, at the virtual Build 2020, the company announces that Terminal has hit the 1.0 milestone.
IoT: With great convenience comes even greater risk
IoT devices are skyrocketing in popularity -- almost everything can connect to the internet these days. You may have some of these in your home or business and not even realize it. Smart bulbs that sync with home management apps, IP camera systems, weather displays on smart refrigerators, smart thermostat -- basically all of the devices you would not expect to have an internet connection that do. This is highlighted further by the ongoing coronavirus pandemic now that the workforce is 100 percent remote and IT teams had to quickly enable remote work, all while ensuring security.
IoT devices make our lives a little easier and more convenient, but they come at a price as they provide new attack vectors for savvy cyber attackers. Gartner forecasts that there will be over 20.4 billion connected IoT devices in 2020, giving those attackers a lot of targets to choose from. On top of that, recent research indicated that IoT device hacks have increased by 300 percent, furthering the point that unprepared home network devices are easy targets for cybercriminals.

Majority of CEOs lose sleep over cybersecurity worries
Over 76 percent of CEOs are consistently losing sleep over the fear of becoming the next headline-grabbing security breach, yet less than half of them have a firm cybersecurity strategy in place.
A new study from cybersecurity company Forcepoint in partnership with WSJ Intelligence surveyed 200 senior executives from a range of industries to find the major cybersecurity stresses and areas of disconnect for business and security leaders.

Dark Web scams seek to cash in on COVID-19
With cybercriminals ever keen to exploit the latest trends to their advantage, it should come as no surprise that the latest research from Trustwave SpiderLabs shows a raft of Dark Web activity based around COVID-19.
Scams range from adverts for supposed vaccines to malicious infection maps. But there's also evidence that Dark Web activities are being hit by the pandemic in much the same way as legitimate businesses.

SD cards are about to get insanely fast
When it comes to data storage, drives can never be "fast enough" or have capacity that is "large enough." We need manufacturers to continually push boundaries, making sure that technology never stops evolving. For instance, SD cards have been in use for many years now, but they are far faster than when they first hit the scene.
And today, The SD Association announces that SD cards are about to get faster than ever, thanks to the SD 8.0 Specification. With SD Express technology, which is based on NVMe and PCIe, you will eventually be able to buy an SD card with speeds nearing 4GB/s!

easyJet hit by 'highly sophisticated' cyberattack: 9 million customers' details exposed
Budget airline easyJet has fallen victim to a cyberattack in which personal information of 9 million customers was exposed. Included in this personal data were details of travel plans, email addresses and, in some cases, credit card information.
The company is now in the process of contacting all of those who have been affected by the data breach, but says that anyone whose credit card details were stolen by hackers has already been contacted.

GlobalSign reveals new platform to ease PKI management
Public Key Infrastructure (PKI) is essential to handling the issuing of digital certificates and managing public-key encryption, but it can prove a burden for businesses.
To make the process easier, certificate authority GlobalSign is launching a new automated PKI platform called Atlas.

Open source security flaws found in 70 percent of applications
New research from application security specialist Veracode finds seven in 10 applications have a security flaw in an open source library on initial scan, highlighting how use of open source can introduce flaws, increase risk, and add to security debt.
The study analyzed the component open source libraries across the Veracode platform database of 85,000 applications, accounting for 351,000 unique external libraries. Nearly all modern applications, including those sold commercially, are built using some open source components.

Microsoft and Sony team up to create AI-powered smart camera solutions
Microsoft and Sony Semiconductor Solutions have announced details of a new partnership that will see the two companies working on AI-powered smart cameras and video analytics together.
The partnership means that Microsoft Azure AI capabilities will be embedded on Sony’s intelligent vision sensor IMX500. Additionally, Sony will create an enterprise-focused smart camera managed app that will be powered by Azure IoT and Cognitive Services.

Logitech Circle View HomeKit security camera is only for the Apple faithful
Apple’s HomeKit was supposed to simplify the smart home, putting the controls for all internet-connected devices in one place. The iPhone-maker’s solution largely delivered what it promised, but not all developers got onboard. And so, many homeowners found themselves unable to use HomeKit exclusively, as not all of their devices were compatible. Thankfully, Apple hasn’t yet given up on it.
Today, Logitech launches a new smart home security camera called “Circle View” that isn’t just compatible with Apple HomeKit — it is exclusive to it. In other words, if you aren’t an Apple hardware user, you shouldn’t even bother, as it requires the HomeKit Secure Video platform.

IBM launches free developer toolkit to promote more accessible design
In case you hadn't noticed, today is Global Accessibility Awareness Day, focusing on digital access and inclusion for people with disabilities and impairments.
To mark the event IBM is launching an Equal Access Toolkit to deliver role-based guidance to all members of an IT project team -- not just developers or designers -- to ensure that the whole team is working together towards an accessible solution.

Windows 10 has a secret network packet sniffer -- here's where to find it and how to use it
With Windows 10 having been with us for a number of years, you would think that all of its secrets had been discovered by now. Of course, Microsoft has released numerous updates to the operating system but it's hard to imagine anything included in these going unnoticed, right?
Maybe not. You may not be aware that with Windows 10 October 2018 Update, Microsoft added a network packet sniffer, Packet Monitor or Pktmon. No one seemed to notice... until now.

The hidden cost of GDPR data access requests
UK businesses are spending £1.59 million and 24 person-years annually on processing data subject access requests in compliance with Article 15 of GDPR, according to a new study commissioned by privacy specialist Guardum.
Data Subject Access Requests (DSARs) require data controllers to provide data subjects with a copy of their personal data within 30 days, or risk a fine of €20 million or four percent of turnover.

You can finally record 4K60 video with Google’s Pixel 4 -- for a $15 fee!
I don’t care what any so-called pundits or “experts” say — Google’s Pixel 4 is a great smartphone. It is well-designed and decently priced, although I will admit its “Motion Sense” radar technology is very gimmicky and unnecessary. If you are an Android fan, you can really never go wrong with a Pixel.
With that said, in our review of the Pixel 4, we noted a deficiency in its video recording capabilities — it cannot do 4K at 60 frames per second. In comparison, Apple’s flagship iPhone models can do 4K60, so it was a bit disappointing to see Google fall short in that regard.
