Don't have cable and want to watch March Madness? Here's how
Now that we've had Selection Sunday, people can begin filling out their brackets and putting their money where their mouths are. From number one ranked Villanova all the way back to number 68 Mt St. Mary, and all of the schools in between.
But what if you don't have cable or satellite to watch the action? You have some viewing options. Using a set-top box like Roku you need never miss a moment.

What small businesses need to know about Enterprise Resource Planning software
For many business managers who are making their first foray into researching ERP software, the subject can see daunting. Search the internet for "ERP software" and you’ll be inundated with dozens of pages of information and opinion; it’s a big subject and there is no shortage of commentators, experts and marketers, all vying for your attention and, of course, a share of your IT budget.
The good news is that despite the technical acronym, the basic principles of ERP software are easily defined and once understood, a business manager is in a solid position to begin considering the different options available to their company.

Mint SIM delivers mobile for the cord-cutting generation -- 20 percent discount for BetaNews readers
Choosing the right mobile plan can be a minefield, requiring you to balance your needs for voice, texts and data against the performance of the service provider and the monthly costs.
US company Mint SIM is seeking to shake things up with a phone service for today's agile, digitally savvy generation. It offers a model that is platform agnostic and not tied to a particular phone or OS.

StExBar extends Windows Explorer with some time-saving extras
StExBar is a tiny freeware tool which extends Windows Explorer with some handy features.
The program has been around for years, but it’s just been updated to work fully on Windows 10, so we grabbed a copy to see how it would perform.

Microsoft is disgustingly sneaky: Windows 10 isn't an operating system, it's an advertising platform
Don't believe what Microsoft tells you -- Windows 10 is not an operating system. Oh, sure, it has many features that make it look like an operating system, but in reality it is nothing more than a vehicle for advertisements. Since the launch of Windows 10, there have been numerous complaints about ads in various forms. They appear in the Start menu, in the taskbar, in the Action Center, in Explorer, in the Ink Workspace, on the Lock Screen, in the Share tool, in the Windows Store and even in File Explorer.
Microsoft has lost its grip on what is acceptable, and even goes as far as pretending that these ads serve users more than the company -- "these are suggestions", "this is a promoted app", "we thought you'd like to know that Edge uses less battery than Chrome", "playable ads let you try out apps without installing". But if we're honest, the company is doing nothing more than abusing its position, using Windows 10 to promote its own tools and services, or those with which it has marketing arrangements. Does Microsoft think we're stupid?

Worldwide web inventor Tim Berners-Lee's biggest concerns: privacy, fake news and political ads
It was 28 years ago that Tim-Berners-Lee submitted his proposal for the worldwide web. What he envisioned as an open platform that would break down global barriers has become a wild beast with endless problems. Talking on the anniversary of his invention, Berners-Lee has spoken about his concerns for the web.
He has three problems in his crosshairs, and he says the trio of issues is something "we must tackle in order for the web to fulfil its true potential as a tool that serves all of humanity." But he does not come armed with solutions; it's at least partly down to us to sort things out.

Your Samsung, LG, Xiaomi, or other Android smartphone could be pre-loaded with malware
Despite being based on the very secure Linux kernel, Android isn't necessarily a very secure operating system. Unlike iOS which does a great job of shielding its users from installing apps from outside Apple's own App Store, it is far too easy to do so on Google's mobile OS. Also, there is nothing requiring manufacturers to issue device updates, meaning many users are forced to use outdated and vulnerable versions of the operating system.
For the most part, however, Android users can remain safe by acting intelligently, such as only installing apps from the Play Store. Well, that might not be so true anymore. You see, it has been discovered that many models of Android smartphones -- from manufacturers such as Samsung, LG, and even Google's own Nexus line -- are being sold with malware pre-installed. This is particularly bad malware, as it can steal user information. Some devices even came pre-loaded with ransomware!

Intel Security releases EFI rootkit checker for MacBooks after CIA hacking leaks
The Vault 7 leaks this week suggest that the CIA has been able to exploit vulnerabilities in a wide range of popular hardware and software, including Windows, macOS and Linux. One of the suggestions is that the agency produced EFI (Extensible Firmware Interface) rootkits for MacBooks called DarkMatter.
To help calm the fears of MacBook owners, Intel Security has pushed out a tool to check for such rootkits. Apple issued a statement earlier this week indicating that it had addressed "many of the issues" exposed by WikiLeaks, but Intel Security's further intervention will bring some peace of mind to concerned users.

Microsoft releases Windows 10 Creators Update Build 15055 for PC and Mobile to the Fast ring
Last week, Microsoft pushed out multiple Windows 10 Insider Preview updates -- Builds 15046 and 15048 for PC, and 15047 for Mobile. Yesterday, Mobile users got Build 15051, and today the software giant announces Build 15055 for both PC and Mobile.
The flurry of new builds shows we’re getting ever closer to the launch of the Creators Update which is due next month.
Using machine learning to secure identity and access management systems
We’ve been losing the war on cybercrime for some time. Research firm Forrester reports over a billion accounts stolen in 2016 alone, and these data breaches are going up, not down. We are having to wade through more incident data, and people cannot keep up. Could machine learning help solve the problem?
For years, researchers hoped that artificial intelligence would produce human-like machines. Now, they focus on a subset of AI that can solve more realistic and useful challenges. Machine learning cannot do everything a human can, but it doesn’t have to. Instead, we can train it to be good at narrowly-defined tasks -- even better at them than humans, in some cases.

Microsoft admits mistake, pulls problematic Windows 10 driver
Microsoft pushed out a mysterious driver to Windows users on Wednesday that caused big problems for some.
The driver, listed as "Microsoft -- WPD -- 2/22/2016 12:00:00 AM -- 5.2.5326.4762," wasn’t accompanied by any details, although we knew from the name that it related to Windows Portable Devices and affected users who had phones and tablets connected to the OS.

Major League Soccer comes to Facebook Live
Soccer is a very popular sport globally, especially in places like Europe and South America. With that said, it is not a huge deal in the United States. True, there are fans of the sport in the USA, but its popularity comes nowhere near, say, baseball, basketball, or football. Unfortunately, this means that many televised matches do not reach all markets. Heck, some matches don't even get broadcast in the English language!
If you are a fan of professional soccer in the USA, however, I have some very good news for you. Some Major League Soccer matches will soon be broadcast on Facebook Live. These are games that would have only been broadcast on TV in Spanish, but will now get the English treatment on the social network. In other words, English-speaking soccer fans are getting increased access to the sport.

Ever Sentinel notifies you when companies change privacy policies or terms and conditions
Changes to terms and conditions or privacy policies happen all the time, and this presents a few problems for consumers. As well as having to negotiate through the often impenetrable language used in these documents, it can be near impossible to work out what has changed, and what the implications are. This is where Ever Sentinel can help.
The service monitors the terms and policies for a number of popular websites and services, and not only alerts you when they change, but highlights exactly what has changed. It's part of a drive to encourage greater transparency in terms and conditions and privacy policies, and it's free for you to use to keep yourself informed.

One in five websites uses insecure SHA-1 certificate
More than a fifth (21 percent) of all websites are still using an insecure certificate, which is leaving them open to different types of cyberattacks. This is according to a new report from cyber security experts Venafi.
The report says many sites are still using the SHA-1 certificate, which means they’re vulnerable to man-in-the-middle attacks, brute force attacks and collision attacks, all of which can expose the site’s sensitive data.
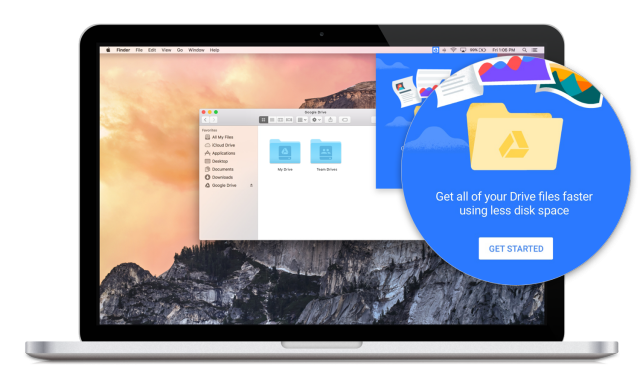
Google beta testing placeholders on Google Drive
Google has announced that it plans to introduce placeholders on Google Drive. The search giant is currently beta testing the new feature, which is officially called Drive File Stream, with the help of G Suite users as part of the Early Adopter Program.
Drive File Stream enables users to access content stored in their Google Drive account without actually downloading it on their device. It works similarly to Dropbox Smart Sync or OneDrive placeholders on Windows 8.


