
The future of managed file transfer (MFT) in the era of digital transformation [Q&A]
In a time when there's a greater need than ever for remote and online collaboration, the secure transfer of information and digitized records is a non-negotiable essential.
As more enterprise employees create and share increasing amounts of sensitive content, organizations need to be able to manage all of their sensitive data transfers between partners, customers, users and systems, have complete visibility and control over where data goes and ensure the highest levels of security.

Dynabook unveils ultra-light Portégé X30W-M with Intel Core Ultra processors and AI features
Dynabook Americas has introduced the Portégé X30W-M, a 13.3-inch 2-in-1 convertible laptop designed for business professionals, educators, and hybrid workers. This ultra-light laptop, weighing less than 1kg, combines flexibility, productivity, and durability with its ability to function as both a laptop and a tablet.
The Portégé X30W-M is powered by Intel’s U- and H-series Core Ultra processors and features built-in AI tools like Copilot, which streamlines workflows with intelligent recommendations. The device also includes a dedicated Copilot key for enhanced productivity. With up to 32GB of 6,400 MHz LPDDR5x memory and SSD storage options reaching 2TB, the X30W-M delivers premium performance for demanding tasks.

70 percent of cybersecurity leaders worry about personal liability
Stories of CISOs being held personally liable for cybersecurity incidents has negatively affected their opinion of the role for 70 percent of respondents to a new survey.
At the same time 34 percent in the study for BlackFog, of 400 IT decision makers across the US and UK, believe that the trend of individuals being prosecuted following a cyberattack was a 'no-win' situation for security leaders: facing internal consequences if they report failings and prosecuted if they don't.

'I know Excel!' -- become a spreadsheet master with 'Microsoft 365 Excel' (worth $14.99) -- free for a limited time
Unlock the full potential of Microsoft 365 Excel with this extensive guide, crafted for both beginners and seasoned users alike.
Microsoft 365 Excel begins by revealing the foundational reasons behind Excel’s creation and its unmatched significance in the business world. Dive deep into the structure of Excel files, worksheets, and key concepts that underscore the application’s versatility. As you progress, you'll master efficient workflows, keyboard shortcuts, and powerful formulas, making Excel an indispensable tool for solving complex problems.

Demand for AI could exceed computing capacity
AI, and generative AI in particular, is expected to greatly enhance productivity within work processes. Some studies estimate that generative AI could contribute between $2.6 trillion and $4.4 trillion annually to the economy.
However, AI infrastructure is costly because the underlying algorithmic problems are extremely computationally intensive and this means there's a potential gap between demand and the capacity needed to meet it.

YouTube TV price hike coming January 2025
In a move sure to rattle some subscribers, YouTube TV has announced a price increase for its Base Plan. Starting January 13, 2025, the monthly subscription cost will jump from $72.99 to $82.99. The search giant cites the rising costs of content and investments in service quality as the primary reasons for this adjustment.
This change is set to affect subscribers during their first billing cycle on or after the January date. However, promotional and trial offers will remain intact for their original duration, ensuring current deals are honored. Subscribers concerned about the new pricing can review their plans by navigating to Settings > Membership within their accounts.

The skills that cybersecurity leaders need
A new cybersecurity leadership survey from ISC2 shows 85 percent of all respondents identify communication as the most important leadership quality, followed by strategic thinking (41 percent), open-mindedness (37 percent), technical expertise (33 percent) and decisiveness (21 percent).
However, the findings reveal that formal leadership training remains largely inaccessible for most respondents, with fewer than 63 percent reporting they have received such formal training. Instead, 81 percent say they primarily developed leadership skills through on-the-job experiences with supervisors and managers.

Linux Mint 22.1 Xia beta debuts with new features and refinements
Linux Mint recently surpassed MX Linux to become the most popular distribution on DistroWatch. Now, with the arrival of Linux Mint 22.1 "Xia" in beta, users get an exciting preview of the features and improvements in the next future stable release.
This long-term support release will eventually be supported until 2029, providing a solid foundation for those seeking reliability and usability. Built on the Ubuntu 24.04 package base and powered by the Linux kernel 6.8, this beta showcases several key improvements and updates.

Neglect of endpoints presents a major security gap for enterprises
A new report shows that endpoint platform security -- securing the hardware and firmware of PCs, laptops and printers -- is often overlooked, weakening cybersecurity posture for years to come.
The report from HP Wolf Security is based on a global study of over 800 IT and security decision-makers (ITSDMs) and over 6,000 work-from-anywhere (WFA) employees, it shows that platform security is a growing concern with 81 percent of ITSDMs agreeing that hardware and firmware security must become a priority to ensure attackers cannot exploit vulnerable devices.

Santa Claus may be coming to town but bots are getting all the best Christmas presents
New research from Imperva shows that 71 percent of UK consumers believe bad bots are ruining Christmas by snapping up all the most wanted presents.
It finds that 40 percent of consumers surveyed say they have been thwarted when trying to buy a gift in the past, only to find that it was completely sold out.

Microsoft releases KB5048667 update, removing another Windows 11 24H2 block and introducing a questionable change
There are still various obstacles in the way of updating to Windows 11 24H2, but Microsoft has just removed one of them. Until now, systems with a USB scanner that used the eSCL scan protocol were blocked from installing the update, but this block has now been lifted.
This is not all that is to be found in the update, of course. There is a somewhat controversial switch to a shortened date format in the taskbar as well as a batch of important security fixes.

Ohsnap announces MCON mobile gaming controller for MagSafe smartphones
Ohsnap has introduced MCON, a compact gaming controller designed for MagSafe-enabled smartphones. Set to launch on Kickstarter on January 2, 2025, and make its debut at CES 2025, MCON aims to provide a portable option for mobile gaming enthusiasts.
Developed by 19-year-old inventor Josh King in collaboration with Ohsnap CEO Dale Backus, MCON features a minimalist design that prioritizes portability and ease of use. With a “launch” button that slides out full-sized hall-effect joysticks and tactile buttons, the device connects via Bluetooth without requiring clamps, cables, or complex pairing.

Google unveils Gemini 2.0 -- is it better than ChatGPT?
Google has finally unveiled Gemini 2.0, an evolution of its AI models designed to usher in a so-called “agentic era.” Sundar Pichai, CEO of Google and Alphabet, has described this as a major leap forward for AI, emphasizing the model’s advanced reasoning, multimodal capabilities, and its potential to revolutionize tools like Google Search, among others. While Google is making big promises, my own experience with Gemini has left me wondering if it’s really a match for the historically superior ChatGPT.
Gemini 2.0 builds on the successes of previous iterations, like Gemini 1.5, and aims to push boundaries with native image and audio output, text-to-speech capabilities, and native integration with tools like Google Search and coding functions. Google is pitching this as more than just an AI chatbot. The model is described as a foundation for creating AI agents capable of handling complex, multi-step tasks, from generating research reports to serving as a developer assistant. Projects like Astra, Mariner, and Jules further showcase Google’s ambition to embed AI into everyday workflows and beyond.
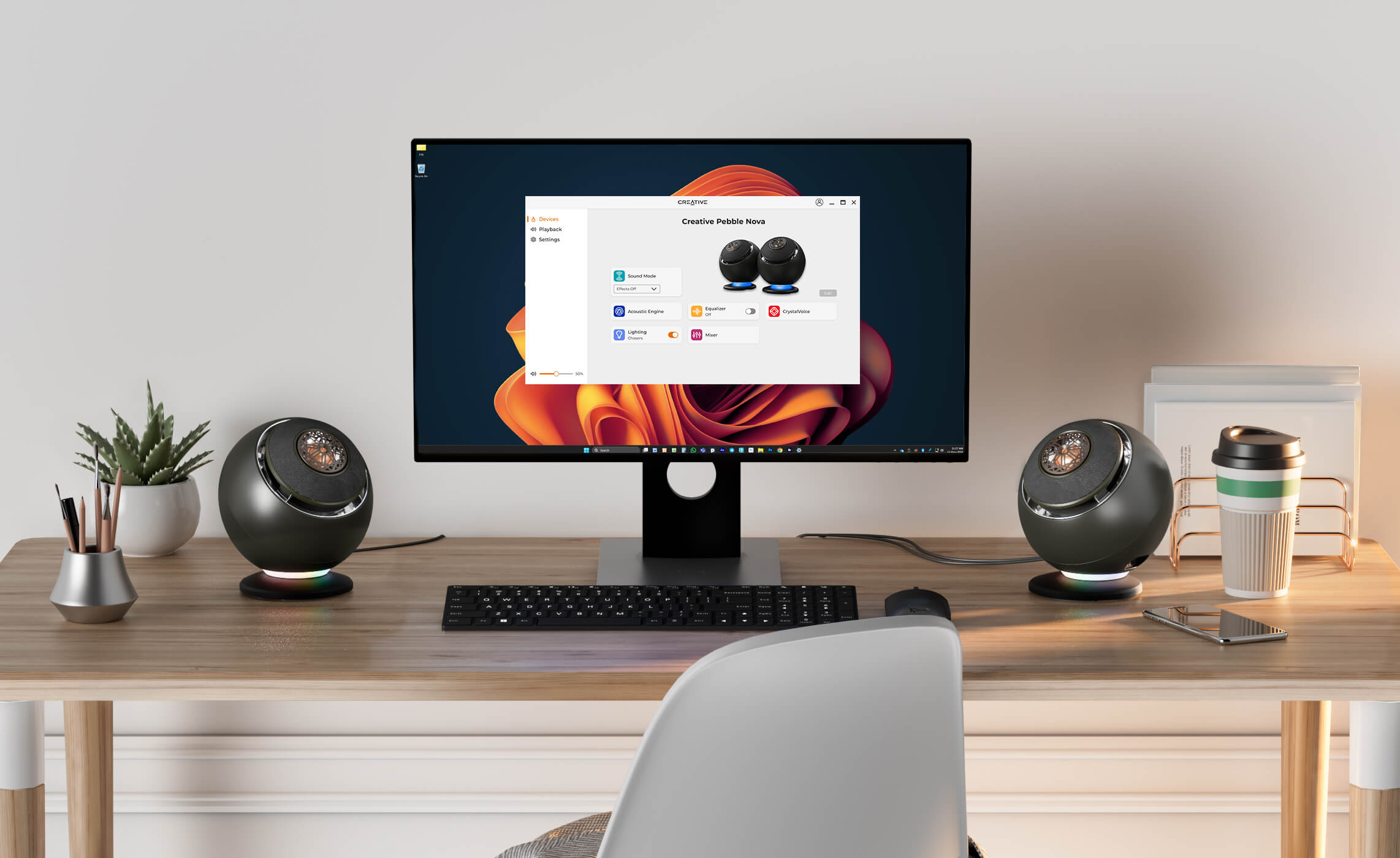
Creative releases premium Pebble Nova desktop speakers with RGB lighting
Creative has launched Pebble Nova, the latest addition to its desktop speaker lineup. Positioned as an upgrade within the Pebble series, the Nova offers updated design elements, versatile connectivity options, and RGB lighting.
The Pebble Nova features a coaxial driver design that aligns the tweeter and woofer, delivering balanced sound across the audio spectrum. Its 45-degree elevated drivers are intended to direct sound toward the listener, and an included stand allows for further elevation and improved projection.

From a Generative AI winter to the revival of automation -- 4 enterprise tech predictions for 2025
While enterprise AI adoption boomed in 2024, 45 percent of US employees fear their company does not categorize AI applications based on the risk of potential harm to employees and customers. In the year ahead, business leaders must contend with the real data privacy and intellectual property risks that generative AI poses and chart a more pragmatic path forward.
Here are four trends I see shaping the enterprise technology landscape in 2025:



