
Slightly confusingly, Apple stores are now just called Apple
Apple's latest branding move messes with syntax and established convention as it changes the way it refers to its physical stores. While Apple Store, Fifth Avenue made perfect sense to just about anyone with common sense, Apple has now decided that Apple Fifth Avenue is better.
The change to retail labelling is a little, well, odd frankly, but it's sure to gain Apple some more of the attention it so craves. After all, Apple World Trade Center sounds rather more grand than Apple Store, World Trade Center doesn't it?

Chrome apps to disappear from Windows, Mac and Linux while Chrome OS gains new launcher icon
Google has come to the realization that hardly anyone is using Chrome apps. As such, the company plans to phase out support for the apps on Windows, Mac and Linux over the next couple of years.
While admitting that packaged apps are used by just 1 percent of users of the three platforms, Google says that the decision comes after a drive to integrate the feature of apps into web standards. Chrome apps will live on in Chrome OS "for the foreseeable future", but a wind-down timetable has been set out for everyone else.

Webcam stopped working? You could blame Windows 10 Anniversary Update (plus, a workaround!)
Windows 10 Anniversary Update has been gradually rolling out to computers around the world and like any big software update it has caused its fair share of problems. The latest issue to rear its head sees Anniversary Update killing webcams.
The problem comes about as the update prevents USB webcams from using MJPEG or H264 encoded streams, instead requiring the use of YUY2 encoding. Microsoft is aware of the issue and is working on a fix that should be released in September, but all is not lost in the meantime.

Businesses struggle to prevent data breaches
Data breaches are everywhere, and companies feel they’re not doing a good job at preventing them. They are, however, taking steps to try and counter the trend. This is according to a new report by business documents management organization M-Files Corporation and the Association for Information and Image Management (AIIM).
According to the report, more than a third (38 percent) of organizations have suffered at least one data breach in the past 12 months. Almost a third (31 percent) feel their company isn’t doing all it can to protect sensitive information, and 36 percent say their company doesn’t have a "formally documented policy" regarding data storage, management and sharing.

Windows 10 Anniversary Update reinstalls bundled apps you've previously removed
Windows 10 has a history of interfering with user choice when it comes to software. The operating system was found to be uninstalling some user programs without permission shortly after the November Update arrived, a problem that persisted for some time.
Now it seems as if the Anniversary Update is doing the reverse, and bringing back bundled apps that users have previously uninstalled. Is it a mistake on Microsoft’s behalf, or is the company, once again, running roughshod over user choice?

Smart plugs have major security issues
Plugging things into a smart electrical plug might not be the wisest of choices at the moment, because they could easily be hacked, putting both your physical and digital life at risk.
This is according to a new report by Bitdefender, which says that smart electrical plugs could be hacked, and the attacker could not only gain access to your personal data, but also reprogram the plug.

Twitch is exposing your activity by default -- here's how to fix the privacy issue
As someone that grew up playing video games in the 1980s, I am rather intrigued by the current trend in watching other people play. It is not so different from when I was a kid actually -- upwards of ten children from the neighborhood would all gather around one NES waiting for their turn to play. If you think about it, we probably spent more time watching others playing than doing so ourselves.
One of the most popular video game streaming platforms is Twitch. There are countless folks broadcasting themselves playing games, and even more spectating. The service has introduced a new feature that some folks might not like. By default, it will expose your activity on friend lists. Don't like that? Luckily, there is a fix.

ImBatch 5 adds multithreading for 400% speed increase
High Motion Software has updated its powerhouse image processor ImBatch with multithreading support for even greater performance. The new feature is only available in the $29.95 licensed edition, but is it worth the money? We took a look.
We used a test set of 345 PNG images, 918 megapixels in total, and set up only two processing tasks: just a "Sharpen" and a "Save as JPG".

Nvidia slams Intel for fudging CPU vs GPU benchmark results
Intel’s recent claims that CPUs are better than GPUs when it comes to deep learning on neural networks has sparked a rebuttal from Nvidia. In case you don’t know what this is all about, here’s a short recap:
Machine learning is currently a really big deal. It’s a huge market with untapped potential in many industry verticals, which is why a lot of different companies are trying to get in on the action. It is widely taken as a fact that GPUs are a better solution than CPUs when it comes to deep learning, because neural networks require low precision computation, and not high-precision, which is what CPUs are usually made for.

EFF: T-Mobile One plan may break net neutrality rules
The Electronic Frontier Foundation believes that T-Mobile's new One plan, which offers unlimited data, calls, and texts, may fall afoul of net neutrality rules due to the restrictions that it imposes on how customers can consume data.
T-Mobile One, which was announced yesterday, is claimed to do away with data "buckets", which CEO John Legere calls "the single biggest pain point in wireless", but limits the quality of video streams for customers who do not wish to pay an additional monthly fee to enjoy high-definition content.

Stress-test your PC with HeavyLoad
Jam Software’s quick and easy PC stress-tester HeavyLoad has just been updated to version 3.4, its first release in more than two years. The package is as easy to use as ever, maxing out your CPU, allocating RAM and drive space and stressing your GPU with a click.
This release is mostly about compatibility, in particular improving results with the latest OpenGL drivers and handling individual cores in Windows 10.
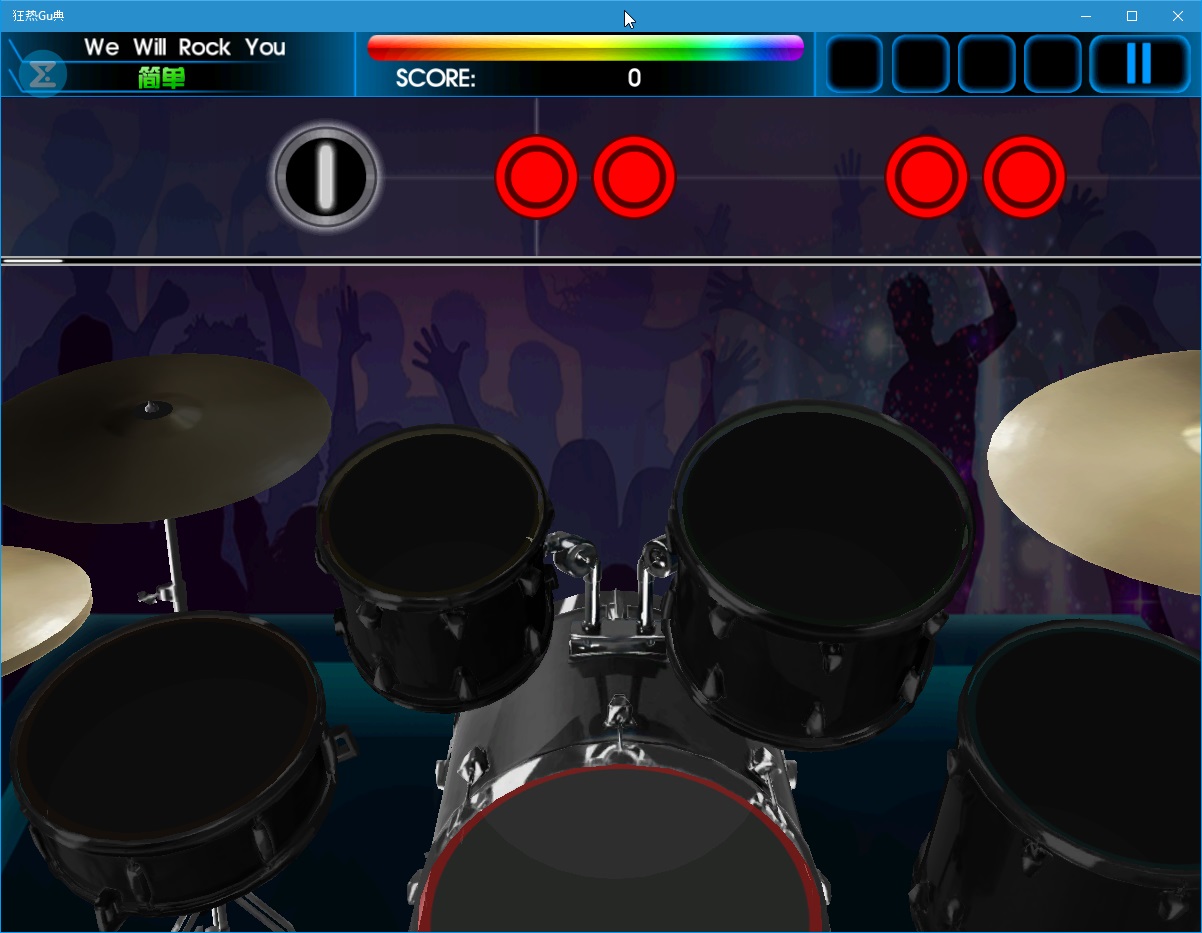
Best Windows apps this week
One-hundred and ninety-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 8.x and Windows 10 in the past seven days.
Several promising apps and games were released this week, such as the Agricoal 2-player game and the Rockband-like game Gu.
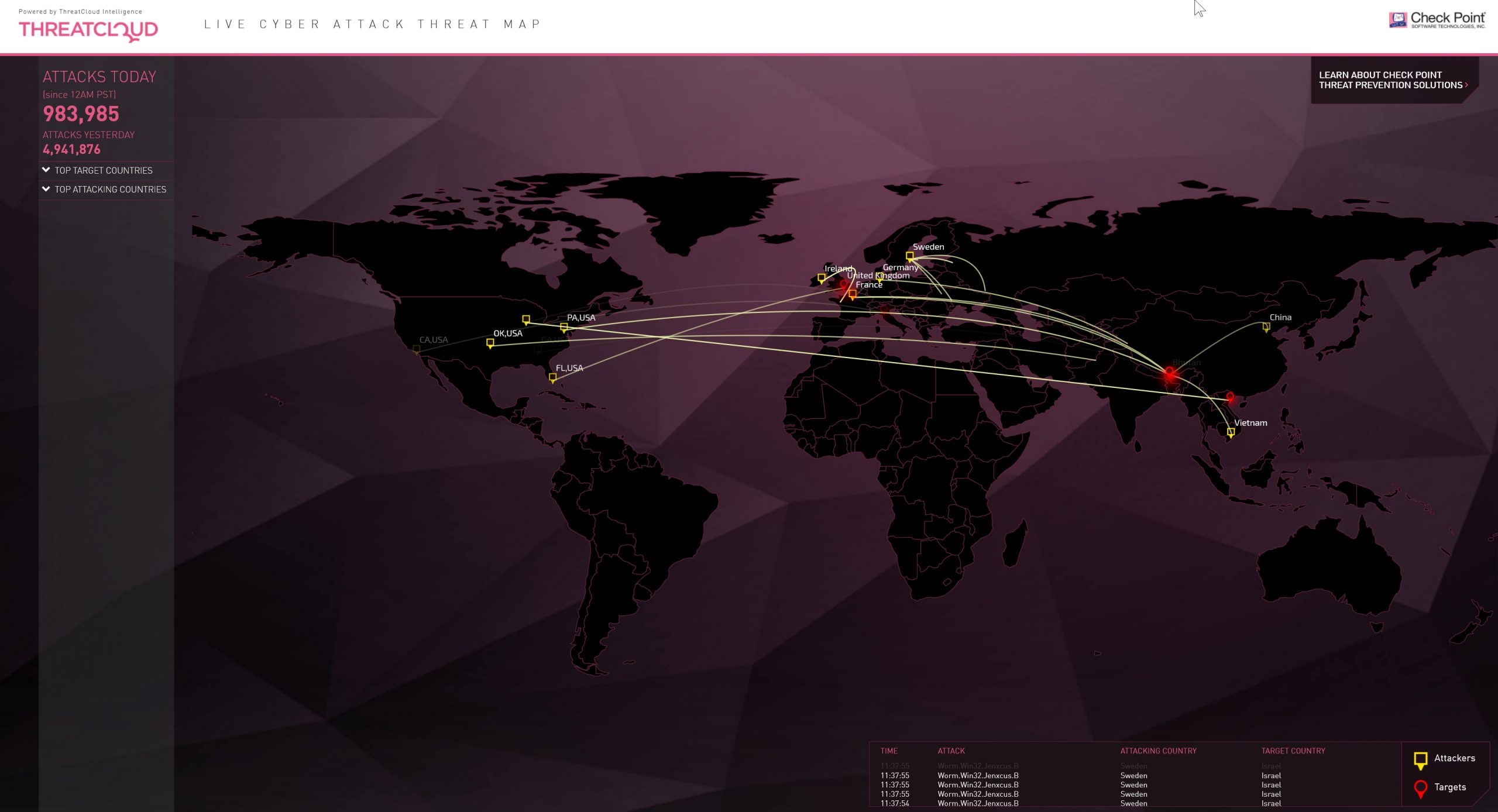
Traditional malware falls as mobile malware rises in July
The number of active malware families attacking businesses fell by five percent in July, but mobile malware now accounts for nine percent of the total -- up 50 percent from June.
These figures come from threat prevention company Check Point based on intelligence drawn from its ThreatCloud World Cyber Threat Map.

Security researcher accuses Microsoft of 'sneaky data mining' in Windows 10
Ah, you can never get enough paranoia nowadays, can you? Security researcher Mike Patterson -- founder and CEO of security analytics organization Plixer -- says Microsoft's Windows 10 sends encrypted data from your machine every five minutes, and there’s basically very little you can do to stop it.
Even when he opted out of everything he could find, regarding data transfer, the OS still continued to do it. The weirdest part about it is that you can’t really determine what is being sent. The content was encrypted so that it is impossible to know what’s going out, essentially hiding this information from the end-user.

China wants to monitor and control all live streams in real time
China's overarching control of the internet, technology, and its people in general is nothing new. The Great Firewall of China is famous for placing huge restrictions on what citizens are able to access online, and recently the government banned the use of social media as a news source.
The latest target for the Chinese government is the increasingly popular activity of live streaming. The proposal includes a requirement for all live streamed content to be monitored around the clock.


