
Windows 10 Insider Preview Build 14366 and Mobile Build 14364 arrive on the Fast ring
With the planned release date for the Windows 10 Anniversary Update drawing ever nearer, Microsoft is hard at work squashing as many bugs as it can.
Naturally, this means new builds released to Windows Insiders won’t offer any significant new features, but they will contain important fixes, general improvements and welcome performance boosts.
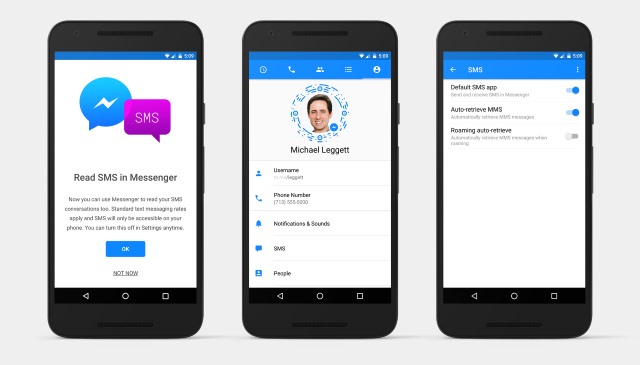
Facebook Messenger for Android can now send SMS and MMS
Facebook has upset a lot of people by effectively forcing its Messenger app onto people by removing the messaging option from the mobile website. Today, to help soften the blow a little, the social network announces that Android users will be able to use the app to not only chat with their Facebook friends, but also to send and receive SMS and MMS.
It's a feature that has been available in the beta version of Facebook Messenger for a little while, but now it is rolling out to everyone. While it will help keen chatters to reduce the number of apps they use, there is now yet another decision to make when it comes to texting -- stick with the default app on your phone, use Hangouts, use Facebook Messenger, or use one of the endless other messaging tools. If you opt for Facebook's offering, there are a couple of things you need to do.

EMEA businesses too slow to detect a data breach
It takes businesses in the EMEA region (Europe, Middle East, Africa) three times longer than businesses elsewhere in the world to detect a breach, mostly because they’re forced to detect such hits themselves instead of relying on outside help.
Those are the general conclusions of the first Mandiant M-Trends EMEA Report. The report, released by security experts FireEye, is based upon the statistics collected during investigations in the region, done by Mandiant’s leading consultants in 2015.

Microsoft rolls out enterprise improvements to IE11 on Windows 7 and Windows 8.1
Since the launch of Microsoft Edge, numerous changes and updates have been made to Microsoft's latest web browser. The arrival of ad-blocking was a real crowd-pleaser, but Microsoft is mindful of the fact that many enterprise users are going to be sticking with Internet Explorer for some time yet.
Today the company announces that some of the enterprise-specific enhancements and tweaks made to the Windows 10 version of IE11 will also be making their way to Windows 7 and Windows 8.1. In fact, the improvements are rolling out to more Windows 10 users as well. Changes made to Internet Explorer 11 in Windows 10 version 1511 are also coming to version 1507 as part of the cumulative updates released today.

UK businesses lose over £1 billion thanks to cybercrime
New figures released by Get Safe Online and Action Fraud, the UK’s national fraud and cyber crime reporting center, reveal the cybercrime cost for British businesses over in the last year.
In total, businesses reported £1,079,447,765 in loses as a result of cybercrime, which is a 22 percent increase from the previous year. Each police force in the UK recorded around £19.5 million in losses but this number may in fact be slightly higher as some businesses may not have reported or disclosed the full extent of the losses they incurred to the authorities.

Seven things I learned from Apple's WWDC 2016 keynote
Apple's annual developer conference is underway in San Francisco. Yesterday's opening keynote was the best since before cofounder Steve Jobs' death nearly 5 years ago. While pundits poo-poo what's missing (shiny gadgets), new and improved software and services matter more—and they showcase priorities properly placed.
CEO Tim Cook kicked off the event, by asking attendees to stand and offer a moment of silence for the mass murder victims the previous day in Orlando, Fla. Forty-nine people are confirmed dead and as many hospitalized from the nightclub shooting. He then went on to lay out a clear agenda for the keynote and the conference—four platforms: iOS 10, macOS "Sierra" (formerly OS X), tvOS 10, and watchOS 3.
Alienware chooses HyperX as exclusive memory brand for Aurora gaming desktop upgrades
When you build or upgrade a computer, you may be attracted to the low prices of cheap components. While getting a good deal is great, seasoned PC builders know that you should never go low-quality. This advice is not for any specific component, but for all of them. Understandably, you should stay within your budget, but make sure you target reputable brands for power supply units, memory, motherboards, and more.
One such brand that I absolutely adore is HyperX. This is Kingston's gaming moniker for things like memory, solid state drives, and headsets. Its memory in particular is very dependable -- many PC builders and gamers trust the RAM. Today, Alienware -- Dell's gaming subsidiary -- announces that it will offer HyperX DDR4 (up to 2400MHz) exclusively for memory upgrades on its Aurora mid-tower desktops. In other words, consumers will be assured quality RAM when upgrading the memory on these Alienware gaming rigs from the factory.

Symantec buys Blue Coat Systems
Symantec has decided to purchase Blue Coat Systems for $4.65 billion in a move that will allow it to more thoroughly protect its users from a variety of threats online.
The deal will also see Blue Coat’s CEO, Greg Clark, become Symantec’s new CEO. This will help the company fill the role which has been vacant since its previous chief executive, Michael brown stepped down in April due to poor financial results.
IoT has too many devices and not enough security
As Internet of Things devices expand their reach into the enterprise, they make greater demands on security.
New research from cyber security specialist ForeScout Technologies reveals that while IT professionals acknowledge the growing number of IoT devices on their networks, they are unaware of how to properly secure them.

iHome announces new line of outdoor speakers
If you are looking for an outdoor speaker for this summer then you want something proven to withstand the elements. iHome is a premier maker of such devices and is now announcing a new line that it claims is perfect for outdoor use.
The Weather Tough line is being called "military grade" portable Bluetooth speakers. They were announced back in January at the Consumer Electronics Show, but are just hitting the market now.

More than half of board members are willing to sack security execs for poor reporting
The decisions that board level executives make on cyber security are very dependent on the quality of the reports they receive from front line management.
A new report from cyber risk analysis specialist Bay Dynamics, carried out in conjunction with Osterman Research, looks at how boards of directors see cyber security reports. Among its findings are that 59 percent of board members say that one or more IT security executives will lose their job as a result of failing to provide useful, actionable information.

Ransomware now targets your smart TV
While the ransomware threat is growing at an alarming rate, many consumers remain oblivious to the dangers posed by this form of malware. It is no wonder that infections are at a record level. And things will only get worse as ransomware creators target new types of devices.
Security researchers at Trend Micro have discovered a new ransomware, referred to as FLocker, that targets Android-powered smart TVs. When activated, it locks the device and asks the user to pay "a fine" to enable full functionality again. Interestingly enough, it takes the ransom in iTunes gift cards, not Bitcoin or another cryptocurrency.
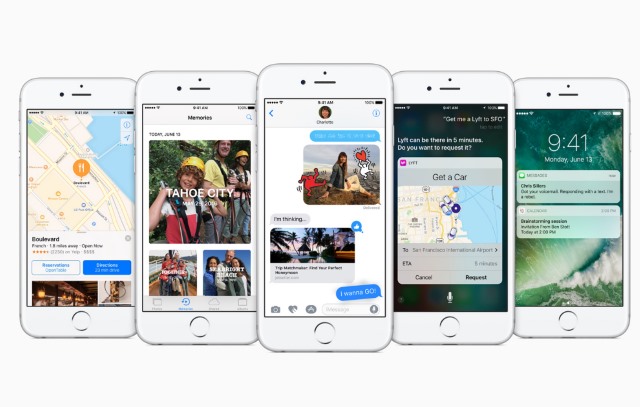
Apple doesn't seem to have decided which devices will support iOS 10
When Apple announced iOS 10 yesterday, there was one question that people around the world were asking themselves: will my device run it? The company sent out rather confusing signals yesterday in answer to this question.
Slides shown during the announcement presentation revealed the iPads, iPhones and iPods that will be able to upgrade to iOS 10. But the official iOS 10 preview page told a different story. Devices that were previously absent from the support list -- such as 3rd generation iPad -- were suddenly listed as supporting iOS 10. Now Apple has changed its mind again, and updated the list once more.

Portworx launches enterprise-class storage for containers
The use of containers has done much to transform the deployment of applications. However, storage hasn't kept pace as it's difficult to scale up to cope with increased workloads.
Data storage specialist Portworx is launching new purpose-built, enterprise-class storage solution for containers. PX-Enterprise will enable IT to match the agility of application developers and deliver lower costs compared to legacy solutions.

SailPoint extends open identity management platform
Since threats to enterprise systems often come from stolen or compromised credentials, managing user identity is a vital part of modern security.
Access control specialist SailPoint is announcing a plugin framework for its SailPoint IdentityIQ platform that will allow customers and partners to develop extensions to the core product features, so they can move towards a more identity-aware organization.



