
Modern workforce integration -- why AI agents need the same oversight as their human counterparts [Q&A]
Agentic AI is rapidly moving from concept to reality, prompting organizations globally to rethink how they integrate these technologies into their business operations. The use of AI agents in daily workflows is set to rise dramatically in the coming years, raising questions over what organizations need to do to manage them effectively, and what might happen if they fail to do so.
We spoke with Ann Maya, EMEA CTO at Boomi, about the evolution of AI agents, the steps businesses should be taking ahead of deployment, and why the principles of human workforce management may hold the key to responsible use.

Mobile threats increase ahead of holiday shopping season
New research from the Zimperium zLabs team reveals a sharp rise in mobile threats tied to the holiday shopping season.
The report shows that mishing (mobile phishing) remains the most widespread and effective mobile attack vector. Smishing messages and fake delivery alerts impersonating trusted retail and logistics brands surged up to fourfold during the 2024 holiday shopping period, with attackers using urgency-driven messages like ‘Your package is delayed, click here’ to trick users into revealing credentials or downloading malicious apps.

Rise in agentic identities leads to increased risk
The AI wave is translating into an increased number of AI agents in the workplace, which equates to a surge of both non-human identities (NHIs) and agentic identities. This is resulting in an urgent focus for CIOs and CISOs on identity threats and recovery.
New research from Rubrik Zero Labs, based on a survey by Wakefield Research of over 1,600 IT security decision makers, finds 89 percent of respondents have fully or partially incorporated AI agents into their identity infrastructure, and an additional 10 percent have plans to.

How AI is changing the role of IT leaders
Artificial intelligence has redefined what it means to lead in IT, with 63 percent of IT leaders
reporting that their roles have evolved due to advances in AI.
A study, from IT management platform Atera, finds today’s IT leaders are increasingly responsible for driving business value. 49 percent cite business value leadership -- shaping strategy and translating AI into revenue and growth – as the top area of increased importance, and 47 percent point to orchestrating human-AI collaboration as a key change in their roles.

Say goodbye to Microsoft Windows 11 and hello to Nitrux Linux 5Wi
Windows 11 remains familiar territory for many users, but it continues to frustrate those dealing with sluggish performance and high system demands on older machines. Frequent updates often fix some problems while introducing others, leaving users searching for an alternative. For those ready to move away from Windows, there's Nitrux Linux 5.
After a long wait, the latest version of the Debian-based Linux distribution has arrived, bringing with it a wealth of changes and improvements. Top of the list is the Hyprland desktop which replaces KDE Plasma.
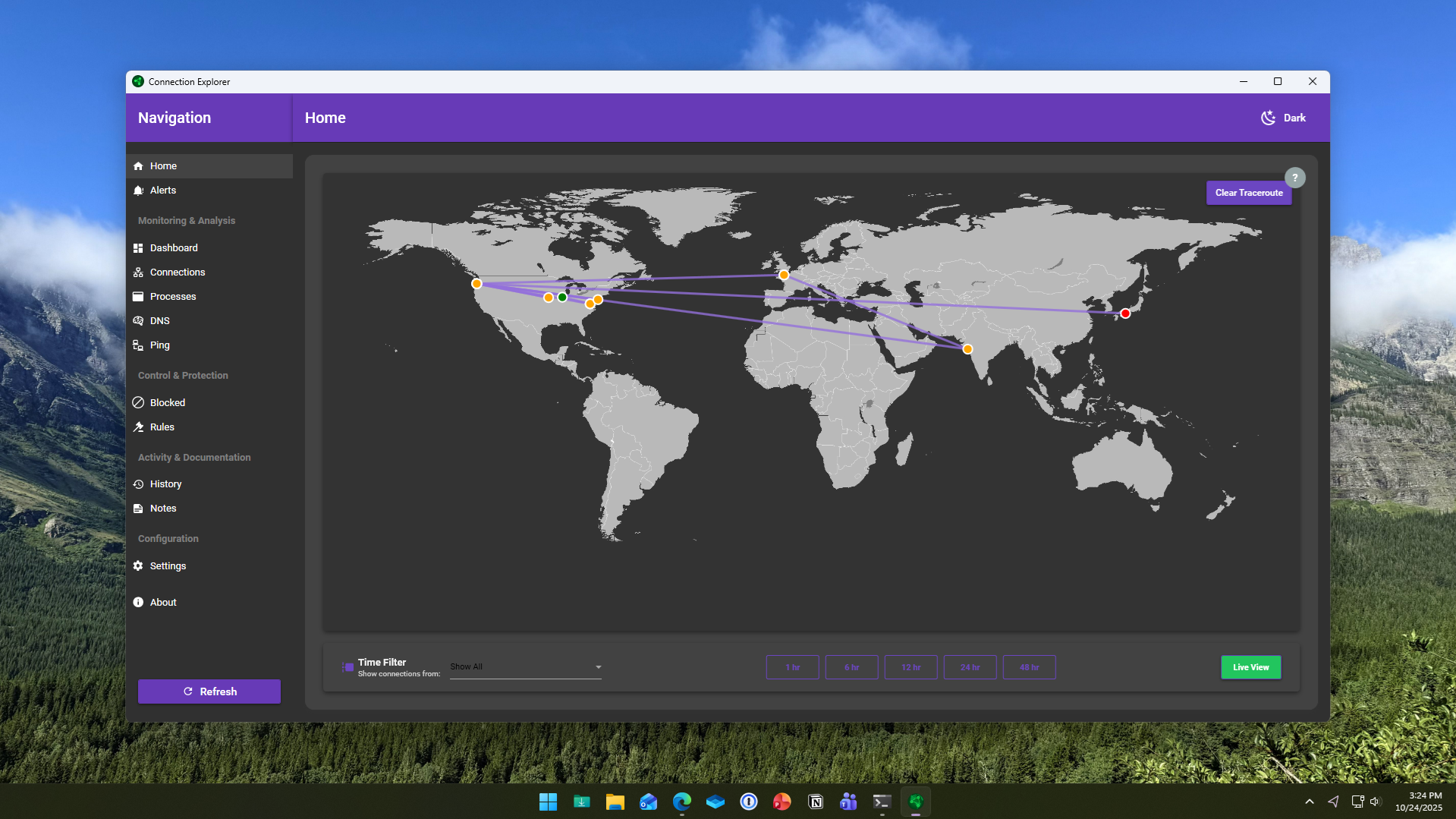
Connection Explorer shows where your PC is sending data in real time
Stardock has launched a new application for Windows called Connection Explorer, a beta tool designed to reveal and visualize every network connection made by a PC. Aimed at improving data transparency, it allows users to monitor, understand, and control how their devices communicate online.
The software maps out every connection a computer makes, transforming complex background activity into a readable visual interface. Stardock says the goal is to give users direct insight into how data flows between their systems and the internet, removing the guesswork from identifying unfamiliar or unwanted activity.
New year, new Microsoft OS -- the stunning Windows 26 is everything Windows 12 should be
Every so often, we get hints about Windows 12, but Microsoft has yet to announce it. Now that the tech giant is only officially supporting one Windows OS, perhaps that will change.
But as 2025 draws to a close, and with a new year on the horizon, it’s time to look forward to fresh beginnings and groundbreaking innovations. It’s time for a new Microsoft operating system. Let me introduce you to Windows 26.

Better cyber hygiene could have prevented 92 percent of incidents
A new report reveals that 92 percent of organizations that experienced a security incident in the past year believe stronger cyber hygiene could have prevented it, underscoring how persistent execution gaps continue to leave organizations exposed to preventable risk.
The study by Sapio Research for Swimlane shows that despite unprecedented spending on cybersecurity tools and services, foundational security practices remain inconsistent and often overlooked.

OWC expands Thunderbolt 5 range with StudioStack and Mercury Helios 5S
Other World Computing has added two new products to its Thunderbolt 5 lineup with the launch of the OWC Mercury Helios 5S and OWC StudioStack. Both devices are designed to provide professionals with faster data transfer, expanded connectivity, and flexible upgrade options across Mac and PC.
SEE ALSO: OWC's latest portable SSD offers up to 8TB in a palm-sized design

1 in 7 consumers fall victim to online scams
A new survey from Bitdefender, of more than 7,000 consumers worldwide, finds that 14 percent of respondents (one in seven) report falling victim to scams in the past year, with an additional four percent unsure.
Based on an average scam loss of $545, that equates to over $534,000 lost among survey participants alone. The US led in scam victims at 17 percent, followed by the UK (16 percent) and Australia (16 percent), while France had the lowest at 11 percent.

More than half of IT leaders lack resources despite increasing budgets
Although 74 percent of IT leaders expect budgets to rise in 2026 more than half say they still lack the internal resources to fix issues quickly or drive innovation.
A new report from DataStrike also finds 60 percent of organizations now rely on MSPs to manage data infrastructure, more than double the rate reported last year. This highlights a growing dependence on external expertise as teams tackle modernization and technical debt.
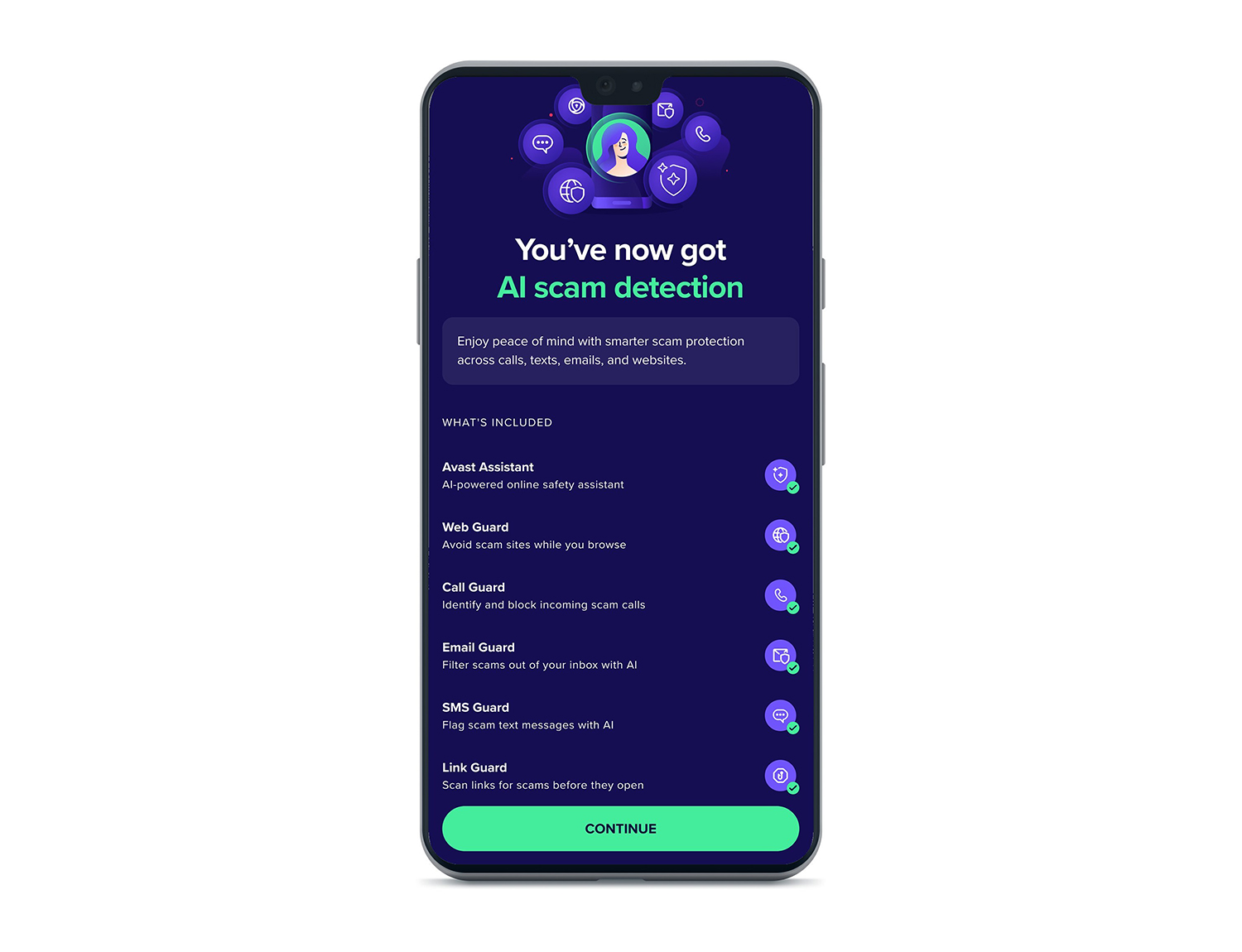
Avast launches Scam Guardian for smartphones and tablets
Avast has introduced Scam Guardian and Scam Guardian Pro for mobile devices, expanding its AI-driven scam protection from desktop to smartphones and tablets. The new tools, part of Avast Mobile Security and Avast Premium Mobile Security, aim to address the rising wave of scam and social engineering attacks on mobile platforms.
Avast, part of Gen, said that over 80 percent of mobile threats blocked by Gen Threat Labs this year were scams. In fact, on average, four mobile scam attempts are stopped every second. Scam Guardian and its Pro version extend Avast's existing protection ecosystem to mobile users on Android and iOS.

AI use in the workplace soars with testing leading the way
A new report, based on data from 3.9 million skills tests taken by employment candidates globally, reveals a dramatic shift towards AI proficiency and cognitive capability across the global workforce.
The data from TestGorilla shows AI testing recorded the highest growth, up 166 percent in comparison to the previous year. Following closely are coding debugging (+133 percent), computer literacy (+77 percent) and data structures/arrays (+73 percent). Together, these underline the urgent demand for practical coding competence and AI fluency.
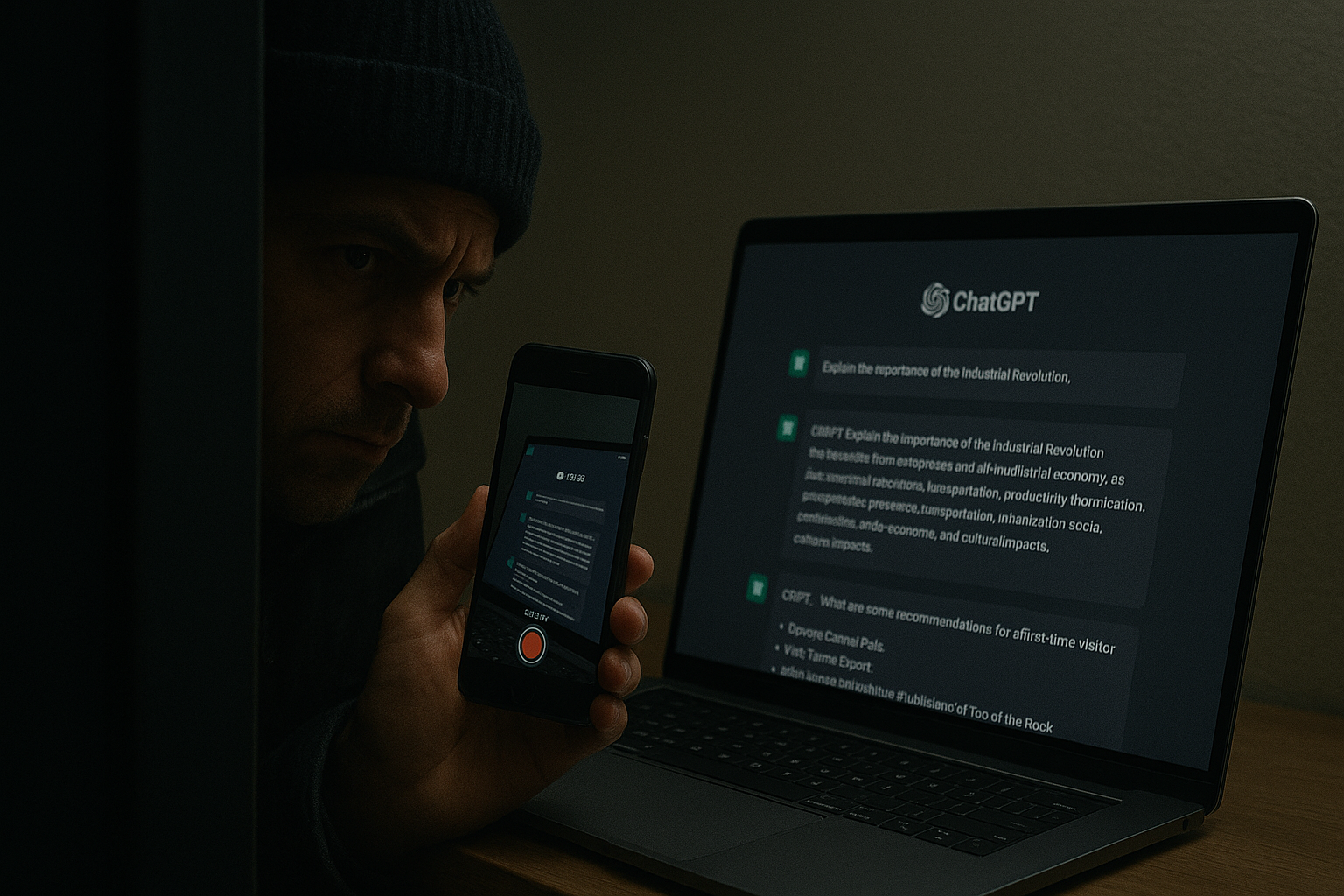
Your company might be secretly recording your ChatGPT conversations -- here's why
A new compliance report shows a sharp rise in financial institutions capturing ChatGPT communications. Global Relay’s Communication Capture Trends Report 2025 found a 3,000 percent increase in the number of firms recording ChatGPT data compared with a year ago.
The report analyzed data from more than 12,000 financial institutions and over 200 communication channels to see how firms are adapting to changing workforces and the introduction of new communication tools.

Maximizing AI ROI In healthcare by establishing an automation-first mindset [Q&A]
AI use cases in healthcare continue to expand, and organizations are identifying opportunities to leverage automation technologies to improve existing workflows.
However, after years of implementing new tooling and expanding tech stacks for better efficiency and backend processes, most organizations are left with disparate systems and datasets that make AI initiatives difficult to put into practice. IT teams are now forced to work backwards, embarking on time and resource consuming efforts to determine how automation can work within the parameters of these fragmented processes.



