Blender 3.3 unveils latest LTS release with multiple new and improved tools
The Blender Foundation has unveiled its first Long Term Support release of the Blender 3.x series with the release of Blender 3.3 LTS. LTS releases are supported for two years from release.
Also available as a portable Windows build, this is the third major point release in the 3.x series since it debuted in December 2021.
How improving the application experience can deliver for business [Q&A]

Spending on cloud services is showing no sign of slowing down, but IT and security leaders are realizing that applications need to have high availability and strong performance in order to be effective.
Application experience management is therefore becoming a key element of enterprise strategy. We spoke to Jason Dover, VP product strategy at Progress, to find out why.
How DNS security can kick-start the process of managing shadow IT

Shadow IT, or the use of IT systems, software, devices, applications, as well as services without the approval of the IT department, is one of the serious reasons why companies face grave security hazards.
But before it is too late, many organizations may not be aware that shadow IT is creating a gap in their structure. The security teams now have a dilemma since they may not have the tools to keep track of a shadow IT issue that affects the entire organization. So, what exactly are the security issues and how can organizations solve them?
KB5012170 update for Windows is even more problematic than first thought… Boot issues and BitLocker irks abound

Microsoft may have issued a warning that the recently released KB5012170 update for Windows might cause 0x800f0922 errors, but it seems that the update is even more problematic. Users who have been able to install the update are complaining of numerous other issues including boot problems.
Among the issues being reported are the appearance of BitLocker recovery screens, slow boot times and more.
Why security training is key to improving cybersecurity posture

The threat landscape is constantly evolving and the shift to hybrid has only widened the attack surface. Today, organizations continue to be in the firing line as cybercriminals exploit their most used application: emails. The proliferation of phishing and business email attacks have seen hackers targeting the biggest corporate security weakness; employees.
Threat actors target workers because they are seen as the weakest link. Cybercriminals are thriving by targeting and exploiting staff, especially those who haven’t received effective user education and training. As the attack surface expands and threats become more sophisticated, organizations must reinvent the wheel by changing their approach to cybersecurity. Where should they start? With training employees and providing omnipresent tools and technology to prevent, detect, and recover from even the most sophisticated of attacks.
How businesses can improve their cyber resilience [Q&A]

Governments are keen for enterprises to improve their cyber resilience, but research from Skurio finds just under half of private and public sector organisations surveyed say that lack of resources and in-house expertise prevent their organisation from keeping up with and protecting against new cyber threats.
We talked to Jeremy Hendy, CEO of Skurio, about the barriers to businesses becoming more cyber resilient and the calls to action for C-suite, info-security departments, and the industry
DuckDuckGo to block Microsoft tracking scripts after user uproar about recent revelations

DuckDuckGo likes to bill itself as a privacy-centric search engine and web browser, and it is hard to deny that it is more private than the likes of Google search and Chrome. But earlier this year, it came to light that there was an agreement in place between the company and Microsoft that meant the DuckDuckGo browser did not block all trackers from the maker of Windows 11.
When users learned that DuckDuckGo was granting a level of leniency to Microsoft there was an understandable backlash. Now the company has announced it is to offer "more privacy and transparency" after failing to meet users expectations, and will block Microsoft tracks -- most of the time.
Microsoft 'fixes' language bar problems caused by KB5014666 update

It has not gone unnoticed that Microsoft's quality control for updates for Windows has been found somewhat wanting of late, particularly when it comes to Windows 11. We have reported numerous times about problems caused by updates, and then the subsequent fixes -- and, sometimes, additional issues they cause -- that Microsoft releases.
Windows 10 users are also affected by problematic updates, and the recently released KB5014666 update caused issues with printing. But this was not the only problem caused by this devilish update; it was also found to lead to problems with the Input Indicator and Language Bar. Now Microsoft has issued a fix -- of sorts.
94 percent of companies have had security incidents with production APIs

According to a new report 94 percent of companies have experienced security problems in production APIs in the past year, with 20 percent saying the organization suffered a data breach as a result.
The latest State of API Security Report from Salt Security also finds that found that API attack traffic has more than doubled in the past 12 months with a 117 percent increase. In the same period overall API traffic grew 168 percent, highlighting the continued explosion of enterprise API usage.
Microsoft beefs up Defender security with new Threat Intelligence and External Attack Surface Management tools
Microsoft has launched two new security products, bolstering the capabilities of Microsoft Defender. The company says that the aim of the two tools is to help organizations lock down their infrastructure and reduce their overall attack surface.
The tools, Microsoft says, also provide "deeper context into threat actor activity" making it easier to predict malicious activity and secure resources. Microsoft Defender Threat Intelligence works by mapping the internet every day, so that security teams have the data needed to understand current attack techniques, while with Microsoft Defender External Attack Surface Management lets security teams see their system as attackers do.
Microsoft releases Windows 11 Build 25151 with useful fixes for annoying problems

Last week's new Windows 11 flight for Insiders in the Dev Channel -- Build 25145 -- introduced a number of new features, including a OneDrive storage alert, subscription management in Settings, and a Local Administrator Password Solution ("LAPS").
Build 25151, released today, is much less exciting but does offer a set of fixes designed to improve the overall experience for users.
Enterprises lack confidence in managing attack surface risk

According to a new report, 60 percent of enterprises have low confidence in their ability to manage attack surface risk.
The study from technology management firm Oomnitza finds businesses increasingly dealing with a hybrid workplace, hybrid cloud, and digital business growth, which makes the ability to manage cyber risk more challenging.
Choose your partners carefully to protect your security

Choosing a partner business with a poor security posture makes an organization 360-times more likely to be at risk compared to choosing a top security performer, according to a new study.
The risk surface research from Cyentia Institute and RiskRecon shows that single demographic factors, such as industry, size and region, aren't enough to assess the risk posed by third parties.
Microsoft's new Surface Laptop Go 2 is available to pre-order today from $599

Just yesterday, we reported that Microsoft was readying a new Surface Laptop Go, with many of the specs revealed early on a Korean website.
We said that Microsoft was planning to announce the new device "in the coming weeks", but it turns out we don't have to wait anywhere near that long as the software giant today introduces the new Surface Laptop Go 2, with a starting price of $599.
Microsoft Entra is a new identity and access-focused family of products
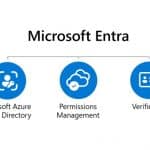
Microsoft has launched a new family of products called Entra. Microsoft Entra encompasses a number of identity and access management solutions including the existing Azure AD. The launch comes after the acquisition of CloudKnox Security last year, and is Microsoft's attempt to help boost security across multicloud environments -- or "secure access for a connected world".
Bolstering the product family, the company has also launched cloud permission management tool Microsoft Entra Permissions Management, and Microsoft Entra Verified ID -- a system that allows for more secure interactions, based on decentralized identity standards. Microsoft has also announced public previews of Workload Identities and Lifecycle Workflows.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.