
IT leaders want action on AI
A new report shows that 83 percent of IT leaders believe GenAI technology will transform every facet of society and business, with 78 percent saying that understanding its potentially disruptive impact is a top business priority.
The study from Appsbroker and CTS shows 86 percent of organizations have already been impacted by GenAI, with a better understanding of the potentially disruptive impacts of the technology a top priority for 78 percent of them.

New ransomware groups account for a quarter of all leaks
The world of cybercrime and ransomware never stands still, and a new report from WithSecure shows more advertised data leaks in the first nine months of this year than all of 2022.
‘New’ groups accounted for about a quarter of all the leaks, with Akira and 8base being particularly prominent sources.
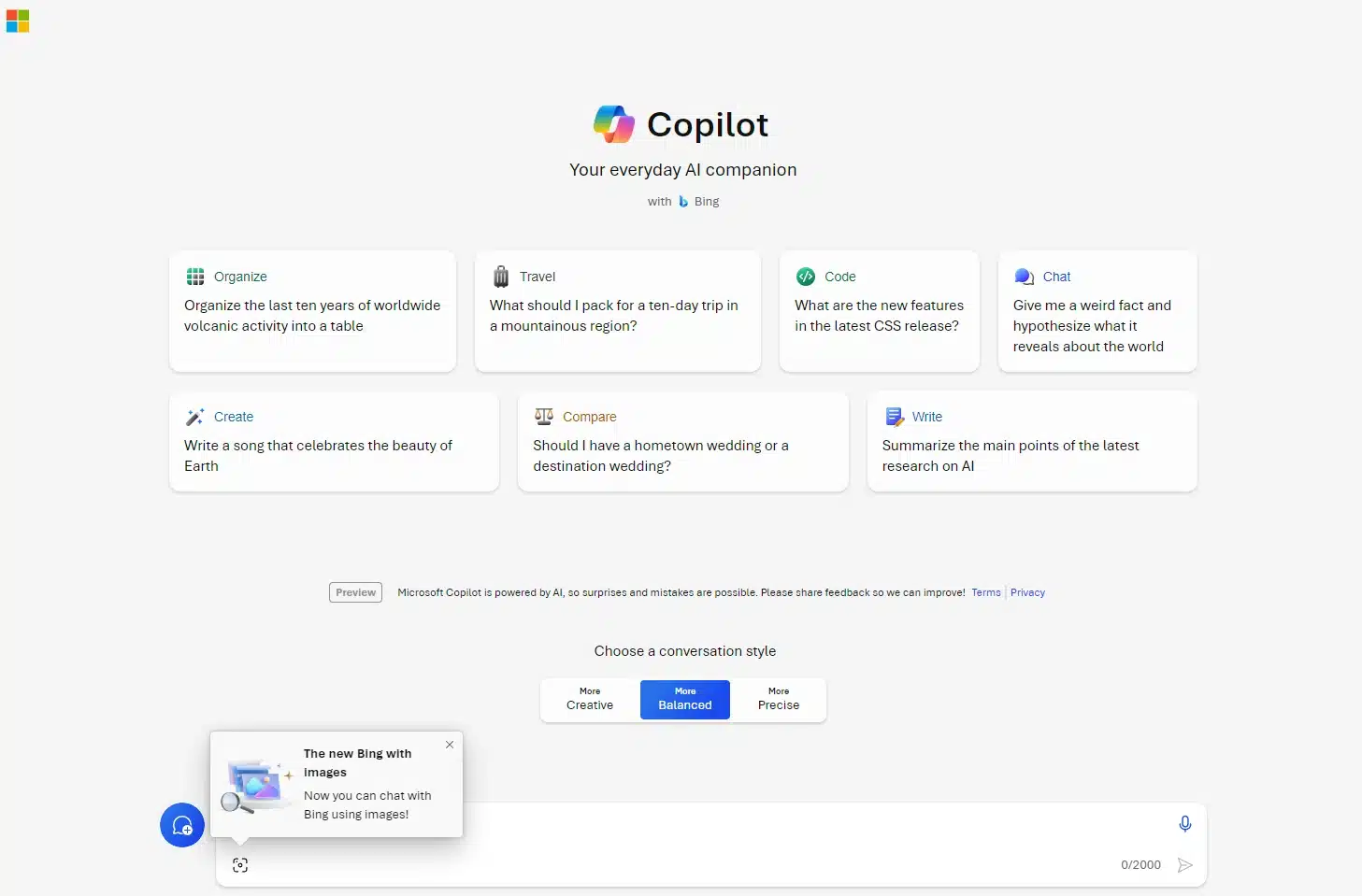
Bing Chat is reborn as Copilot as Microsoft continues its AI push with a rebrand
Microsoft has announced a rebranding of Bing Chat and Bing Chat Enterprise to Copilot as part of its "vision to bring Microsoft Copilot to everyone". There is now a lengthy list of products under the Copilot banner, including Microsoft Copilot and Copilot in Windows, but this latest rebrand feels a little odd.
Despite describing Bing as "our leading experience for the web" Microsoft has opted to ditch much of the Bing branding as it embraces Copilot more fully. The company has also revealed that Copilot will become generally available on December 1.
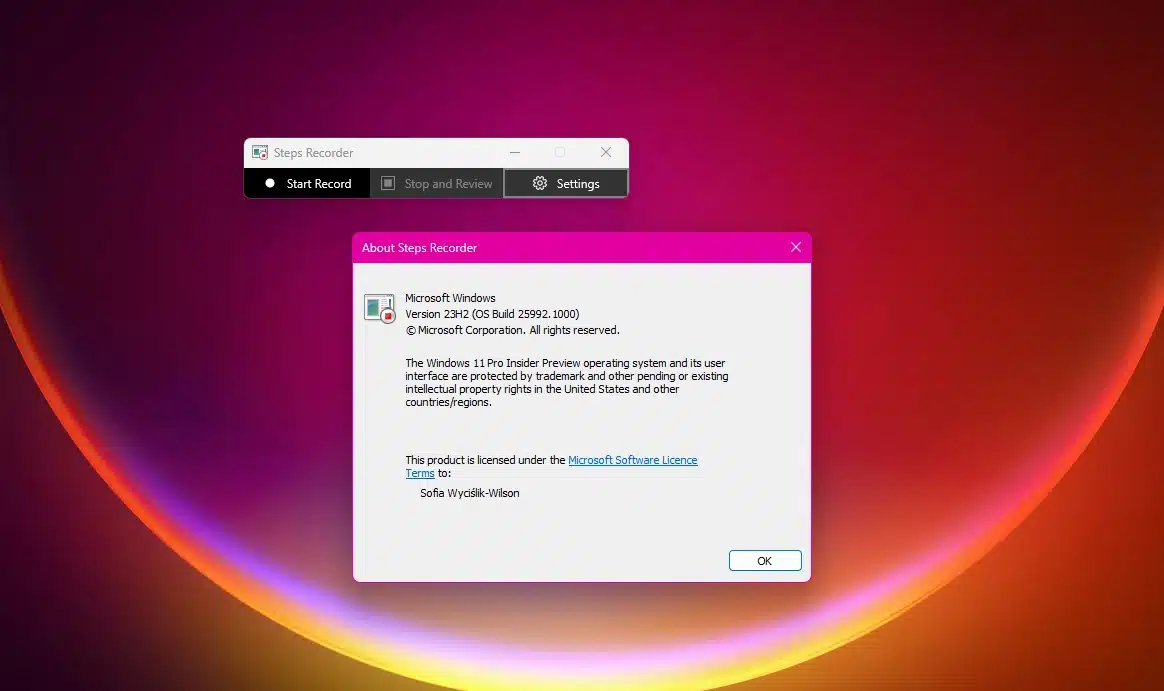
Microsoft uses Windows 11 update to announce it is killing off Steps Recorder screen recording app
Microsoft is slowly but surely trimming the fat away from Windows 11. Over the course of recent months, the company has either removed or announced the future removal of numerous app components, including the Tips and WordPad apps.
Now a new victim has been added to the list. With the release of Windows 11 Insider Preview Build 23590 to the Dev Channel, Microsoft has revealed that screen recording stalwart Steps Recorder is no longer being updated and is lined up for removal further down the line.

Thermaltake unveils TOUGHRAM XG RGB D5 DDR5 7600/8000 MT/s memory
Today, Thermaltake announces its 32GB (16GB x2) TOUGHRAM XG RGB D5 DDR5 7600/8000 MT/s memory kits, which are available in both black and white. The TOUGHRAM XG RGB D5 RAM is distinguished by its unique X-shaped light bar with 16 LEDs, offering a visually striking design.
The high-frequency capability of the TOUGHRAM XG RGB D5 DDR5 7600/8000 MT/s modules makes them ideal for next-gen PC components. Performance is the highlight of the TOUGHRAM XG RGB D5 series, with the modules built using superior components. Tightly-screened ICs and a 10-layer PCB with a 2oz copper inner layer are key to its fast response time and overclocking capabilities.

ChatGPT one year on: Why IT departments are scrambling to keep up
We’re nearly one year on since ChatGPT burst onto the scene. In a technology world full of hype, this has been truly disruptive and permanently changed the way we work. It has also left IT departments scrambling to keep up – what are the risks of using AI? Can I trust the apps with my data?
Should we ban altogether or wait, and see? But if we ban it, is there a risk of being left behind as other companies innovate?

Understanding LLMs, privacy and security -- why a secure gateway approach is needed
Over the past year, we have seen generative AI and large language models (LLMs) go from a niche area of AI research into being one of the fastest growing areas of technology. Across the globe, around $200 billion is due to be invested in this market according to Goldman Sachs, boosting global labor productivity by one percentage point. That might not sound like much, but it would add up to $7 trillion more in the global economy.
However, while these LLM applications might have potential, there are still problems to solve around privacy and data residency. Currently, employees at organisations can unknowingly share sensitive company data or Personal Identifiable Information (PII) on customers out to services like OpenAI. This opens up new security and data privacy risks.

Embracing the future: How AI is transforming security and networking
Network management and security should go hand in hand. However, making these services work has become more complicated and riskier due to the growth of the public cloud, the use of software applications, and the need to integrate different solutions together.
This complex network security domain requires more skilled cybersecurity professionals. But as this need becomes obvious, so does the glaring skills gap. In the UK, half of all businesses face a fundamental shortfall in cybersecurity skills, and 30 percent grapple with more complex, advanced cybersecurity expertise deficiencies.

Amazon Kindle to replace Comixology app
Amazon today announces big news for comic book fans and digital readers. Starting December 4, 2023, the Comixology app will be no more. That’s right, folks, it’s joining forces with the Kindle app on iOS, Android, and Fire OS. It’s like when Batman and Superman team up -- unexpected but potentially awesome.
Your beloved comics, graphic novels, and manga won't be vanishing like a villain in a puff of smoke. They’re simply moving to the Kindle app. Same Amazon login, new home. It’s like moving from Gotham to Metropolis -- a change of scenery but the adventure continues.

Google launches FIDO2 compatible security key
Today sees the launch of Google's new Titan Security Key which can be used as a second authentication factor and also to store your passkeys.
Unlike the earlier FIDO1 key, Titan will also work with all other FIDO-enabled services (such as Microsoft accounts). You can also store credentials for up to 250 accounts on this key, compared to current keys which can typically only store around 25.

Get 'Beginning Software Engineering, 2nd Edition' (worth $33) for FREE
In the newly updated second edition of Beginning Software Engineering, expert programmer and tech educator Rod Stephens delivers an instructive and intuitive introduction to the fundamentals of software engineering. In the book, you’ll learn to create well-constructed software applications that meet the needs of users while developing the practical, hands-on skills needed to build robust, efficient, and reliable software.
The author skips the unnecessary jargon and sticks to simple and straightforward English to help you understand the concepts and ideas discussed within. He also offers you real-world tested methods you can apply to any programming language.

90 percent of SMBs fear ransomware but 65 percent don't think they're a target
According to a new report, 90 percent of SMBs are extremely or somewhat concerned about a ransomware attack, yet 65 percent don't think or aren't sure that they're a ransomware target.
The latest Cybersecurity Global Ransomware Survey from OpenText show a similarity in how small-to-medium sized businesses (SMBs) and enterprises (more than 1,000 employees) think about ransomware attacks, including this disconnect about who is a target and growing concern about the use of AI by threat actors.
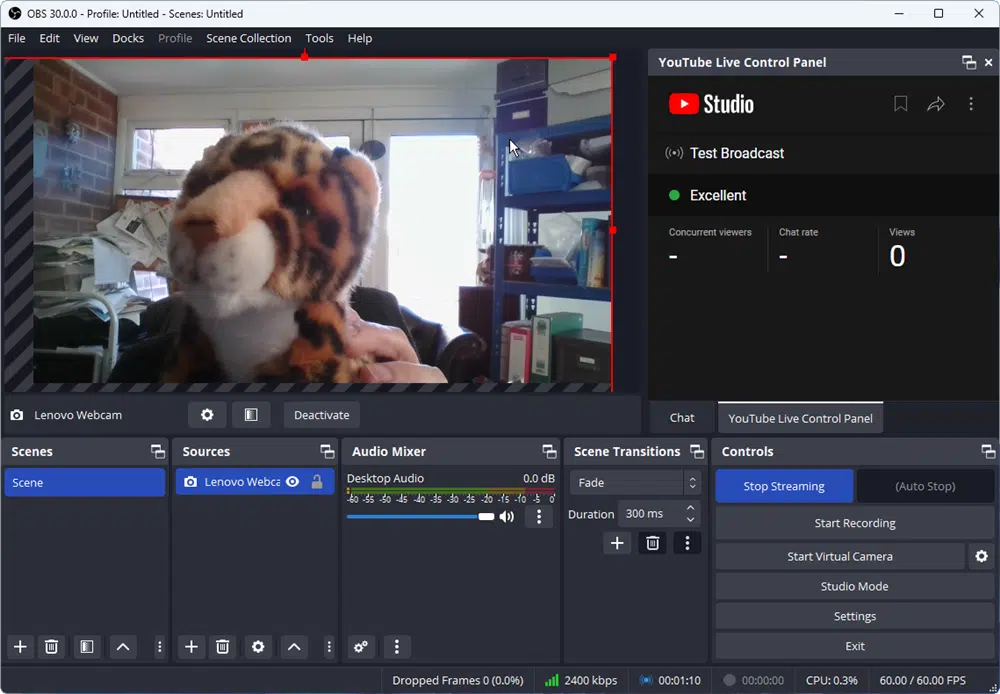
OBS Studio 30.0 improves web-streaming capabilities, adds fallback Safe Mode
Open-source video broadcasting, recording and streaming tool OBS Studio 30.0 has been released for Windows, macOS and Linux.
The new release highlights include support for WebRTC output and improved YouTube integration. There’s also a new Safe Mode to help troubleshoot problems with plugins, scripts and other elements among a slew of another new features and other improvements.

The eight common weaknesses of IT security
Every organization in the 21st century understands that keeping proprietary data safe is crucial to its success. However, while business leaders tend to believe their current security products and policies are truly secure, breaches continue to climb. It is clear that despite an ever-increasing number of companies maintaining formalized security programs and annually increasing security budgets, there are gaps that continue to go unnoticed and unaddressed.
Through hundreds of assessments and breach analyses, we have concluded there are eight common weaknesses that most commonly enable threat actors to penetrate organizations’ security armor, move through networks to elevate privileges, and ultimately allow them to compromise defenses. These weaknesses are continuously probed by threat actors, and while they may seem secure at deployment, they often are not; and even if initially secure, they frequently become obsolete due to missed updates, upgrades, changes to the enterprise environment, and evolving threat tactics. A frequent misconception is that security products and processes can be set and then forgotten; but since threat actors’ tactics evolve at an alarming pace, security controls must also be continually adjusted to ensure that organizations’ security armor continues to envelop and protect. In the absence of continuous evolution, the armor and its contents become vulnerable and, often, more at risk due to a false sense of security.

Microsoft releases KB5032190 update bringing an abundance of new features to all Windows 11 users
It is that time of the month again; Microsoft has released a slew of updates including the KB5032190 update for Windows 11.
As this is a cumulative update that includes security fixes, it is therefore mandatory. But the security patches, while nice, are far from being the highlight. KB5032190 is the update with which Microsoft is giving all Windows 11 users access to the new features of Moment 4, including Taskbar changes and Windows Copilot.


