Over 30 percent of mobile users encounter phishing attacks

According to data from Lookout, 2022 has seen the highest percentage of mobile phishing encounter rates ever, with an average of more than 30 percent of personal and enterprise users exposed to these attacks every quarter.
Since 2021, mobile phishing encounter rates have increased by around 10 percent for enterprise devices and more than 20 percent for personal devices.
Welcome to Twitter, who are you again?
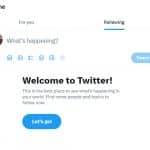
If you've visited Twitter this morning you may have found that the platform appears to have forgotten that you exist.
Users around the world are being presented with a friendly 'Welcome to Twitter' message urging them to find some people to follow, despite having been on Twitter for years and already following hundreds of people.
Is it worth paying for an enterprise browser? [Q&A]

Why would you pay for a browser when all of the popular ones are available for free? If you're an enterprise it could be because a paid browser can address some key problems.
We spoke to CEO and co-founder of enterprise browser specialist Island, Mike Fey, to find out more about this category and what benefits it can offer.
Twitter updates its Violent Speech Policy to ban wishing ill on others... unless it is hyperbolic

Twitter has announced its latest update that limits what users may and may not post on the social platform. In the latest version of its Violent Speech Policy, the company now bans not only threats of harm, but also wishes of harm to others.
The policy still prevents users from posting what Twitter describes as "violent threats", "incitement of violence" and "glorification of violence". The update adds that users also "may not wish, hope, or express desire for harm", going on to explain that "this includes (but is not limited to) hoping for others to die, suffer illnesses, tragic incidents, or experience other physically harmful consequences".
Microsoft warns of Windows 11 startup problems after installing Moment 2 (KB5022913 update)
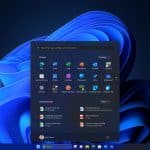
The release of the latest big update for Windows 11 has been eagerly anticipated for some time, and yesterday Microsoft released Moment 2. It brings massive innovations to the operating system -- as well as problems.
Also known as the KB5022913 update, Moment 2 includes an updated Taskbar search tool, improved touch optimizations, an enhanced system tray, revamped Task Manager and much more. But the update is also causing problems, with Microsoft acknowledging that having certain apps -- notably ExplorerPatcher and StartAllBack -- installed may mean that Windows 11 will not start.
YEYIAN launches ODACHI gaming PCs powered by AMD Ryzen 9 7900X3D and 7950X3D processors

AMD's new Ryzen 9 7900X3D and 7950X3D desktop processors are getting rave reviews for their impressive gaming performance, and PC enthusiasts are chomping at the bit to get their hands on them. Intel should be quite worried about these chips!
If you are wanting to own a PC powered by one of these new processors, but you don't feel like building a computer yourself, I have some fabulous news. Today, YEYIAN launches a trio of pre-built ODACHI gaming PCs powered by these new AMD chips. While these computers are rather pricey, they are also very impressive -- both aesthetically and from a specification perspective.
Logitech G launches Mandalorian Edition ASTRO A30 wireless gaming headset

If you are a gamer, there's a good chance you like Star Wars too. After all, both things are integral parts of nerd culture. These days, Star Wars fans are very much obsessed with popular Disney+ show The Mandalorian. Even people that don't normally love Star Wars love the show thanks to the undeniably cute "Baby Yoda" (aka Grogu).
Gaming brand Logitech G has wisely chosen to tap into The Mandalorian fandom with a special edition headset. Fans of the show are sure to go gaga over this new Mandalorian Edition version of the popular ASTRO A30 Wireless gaming headset.
Microsoft's huge update to Windows 11 arrives today, with many new features, including AI-powered Bing on the taskbar
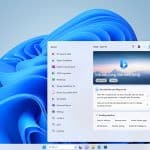
Windows 11 has been a hard sell for Microsoft. It has demanding system requirements which means it won’t run on older hardware, and it feels a bit unfinished in places. With its Moments releases, Microsoft is trying to make the new operating system more appealing, and today it adds a raft of new features.
With the latest Windows 11 feature release, Microsoft is focusing on innovation "in a few key areas". These include:
Known vulnerabilities pose the biggest threat

Known vulnerabilities for which patches have already been made available are the primary vehicle for cyberattacks, according to a report released today by Tenable.
The Tenable Research team analyzed cybersecurity events, vulnerabilities and trends throughout 2022, including 1,335 data breach incidents publicly disclosed between November 2021 and October 2022.
88 percent of organizations have suffered cyber breaches in the last two years

A new survey of 300 CIOs, CISOs, and security executives from enterprises across Europe and the USA shows that 88 percent of organizations admit to being compromised by a cyber incident over the past two years.
The study from Pentera reveals that this is despite organizations having an average of almost 44 security solutions in place.
Plugable launches UD-3900PDH and UD-768PDZ premium docking stations

USB-C docking stations are very common these days. Hell, websites like Amazon are littered with countless makes and models. Of course, not all of them are good, nor do they offer the same things. Features can vary from dock to dock, such as the number of USB ports or video outputs. I recommend sticking with reputable brands such as Kensington, StarTech.com, and Plugable to name a few.
Speaking of Plugable, today, that company launches two new USB-C docking stations. Called "UD-3900PDH" and "UD-768PDZ," both offer 100W power delivery and feature triple monitor support. While they both have SD card readers, only the UD-3900PDH has a dedicated micro SD reader as well.
GDPR, liability and email security management in the digital age

On the 25th of May, 2018, the General Data Protection Regulation (GDPR) was passed, bringing into law a number of privacy and data protection regulations for those within the EU. Any business that operated within the EU had to immediately begin to respect the regulations laid out by this law.
Yet, even businesses outside of the EU are impacted, due to the fact that anyone that does business with someone within the EU area still must fall under these regulations. This meant that the vast majority of international companies, stretching from Asia and South America to North America and beyond, all had to start abiding by these laws.
Tips for developing a better SASE strategy

Secure Access Service Edge (SASE) architecture has become a cornerstone for IT and security teams in recent years. SASE became important when demand for cloud-based operations soared, and organizations needed a better way to ensure consistent, fast, and secure access to resources on any device at any location. Today, SASE architecture continues to grow and by 2024, at least 40 percent of enterprises will have strategies in place to adopt SASE. But managing architecture that combines secure access and SD-WAN capabilities with cloud-native security functions, like web gateways, cloud access security brokers, firewalls, and zero-trust network access, is no small feat.
Understandably, SASE deployments can be complex and make end-to-end visibility challenging for IT. In this article, I’d like to explore some of the key criteria to consider when implementing SASE (outside of the obvious cyber security requirements). But first, I’d like to review a few foundational elements including integration, visibility, and remote access.
Threat actors move beyond ransomware to exploit new (and old) techniques

Cybercrime actors are shifting away from ransomware to new, innovative techniques, according to the latest CrowdStrike Global Threat Report released today.
The report shows 71 percent of attacks detected in the last year were malware-free (up from 62 percent in 2021) and interactive intrusions (hands on keyboard activity) increased 50 percent in 2022. This shows how sophisticated human adversaries are increasingly looking to evade antivirus protection and outsmart machine-only defenses.
Making zero trust a reality in 2023: why identity-first security will be a 'must have'

In today’s mobile and cloud-first world, zero trust has become a key requirement for organizations looking to secure the digital infrastructures where their applications, data, users and devices reside.
There’s little doubt that COVID-19 changed the rules of the game where enterprise security is concerned. Historically, security models were based on 'castle and moat' style architectures where the enterprise’s network and data center were guarded by firewalls on the perimeter. When users left the 'trusted' enterprise network, VPNs were used to extend the enterprise network to them.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




