
How are enterprise customers using your software?
Getting a clear understanding of how customers use your products is vitally important for software suppliers. Product managers are best equipped to deliver valuable products if they have clear knowledge about this. Data-driven insights, available from entitlement management (EM) systems, are essential for optimizing product road mapping, packaging, provisioning, and pricing decisions, all with the aim of delivering the best customer experience possible. All of these contribute to achieving strategic goals, such as facilitating shifts in monetization and deployment models, streamlining the quote-to-cash (Q2C or QTC) process, and ultimately accelerating growth and increasing recurring revenue.
Key to these efforts: aligning price (the expense for the customer) and value (the perceived utility) of your product. But this proves to be tricky without understanding of who your users are. "Lack of insights into user personas and their priorities" and "disparate systems that make it difficult to achieve single customer view" are among the top hurdles, as reported in the Revenera Monetization Monitor: Software Monetization Models and Strategies 2022. A comprehensive approach to entitlement management can help provide the insights that contribute to improved operational efficiencies.

The key to an effective generative AI strategy: Human oversight
Generative artificial intelligence (AI) systems have witnessed significant advancements in recent years, offering remarkable capabilities in a variety of domains.
Generative AI is a powerful tool that can be used for both good and bad. Threat actors have been employing the latest technology to harm businesses in various ways for decades, but organizations have and must continue to find ways to use this same technology to their advantage, and ultimately outsmart these digital thieves as AI is becoming more accessible and accepted.

Watch Windows 10 being installed (and running) on Windows XP
Although most people have long since moved on from Windows XP, some people are still running the ancient OS, even though Microsoft stopped supporting it way back in 2014.
Although the lack of support means continuing to use XP is a risky endeavor, it’s a stable and capable operating system that’s even able to run Windows 10.
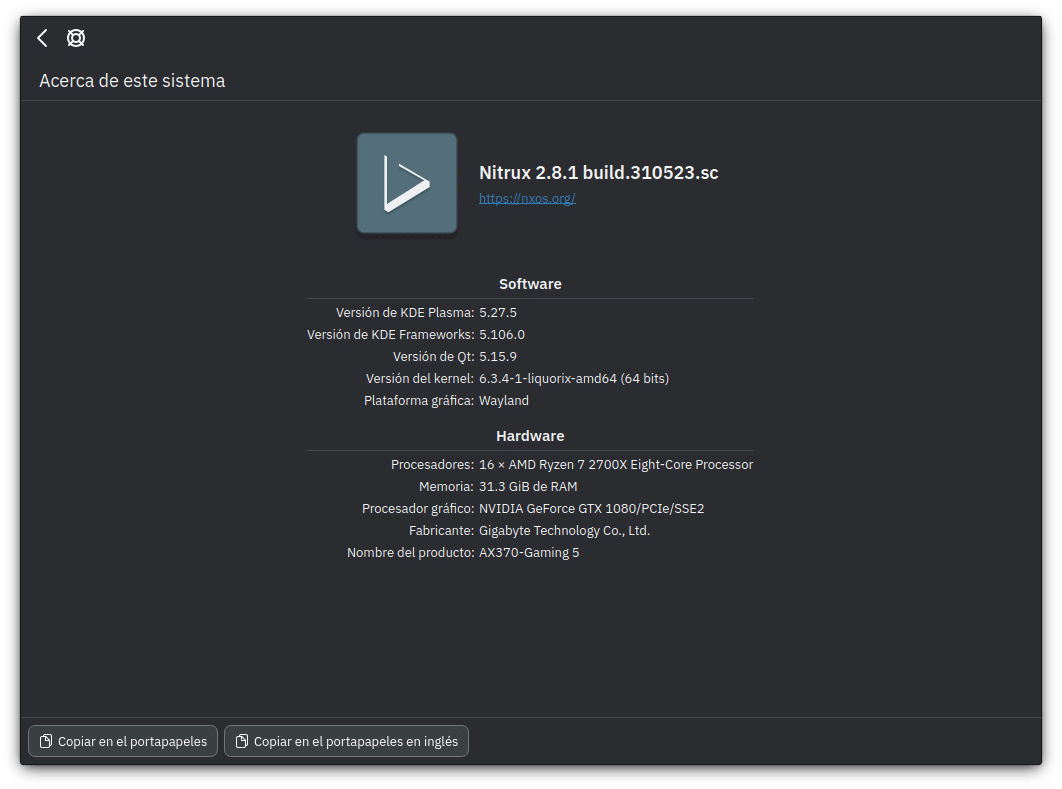
Nitrux 2.8.1 Linux distribution unleashes supercharged security and privacy powers
Nitrux 2.8.1, codenamed "sc" for "safer computing," has been released, offering enhanced privacy and security features. While the distribution does not claim to be impenetrable or unhackable, it aims to protect users' privacy and provide tools for online anonymization. The release is made possible through collaboration with packagecloud, which provides the necessary infrastructure for building the distribution.
New users are advised to perform a fresh installation using the latest media. For existing users of version 2.8.0, it is recommended to review the release notes for specific instructions. Notably, Nitrux 2.8.1 employs Linux 6.3.4-1 (Liquorix) as its kernel.

Beating the headache of SaaS sprawl [Q&A]
Moving to the cloud has always presented something of a challenge, but the pandemic made things even more difficult because of the need to manage more applications across a distributed workforce.
Add in the issue of shadow IT, and enterprises are increasingly struggling with SaaS sprawl. We spoke to BetterCloud CTO, Jamie Tischart to learn more about the problem and how to deal with it.
Debian 12-based MX Linux 23 Beta 1 'Libretto' is the Windows 11 alternative of your dreams
In a world dominated by Windows, it's refreshing to see alternative operating systems stepping up their game. MX-23 beta 1, built from Debian 12 "Bookworm" and MX repositories, offers a promising option for users seeking an alternative to the Windows experience. With a range of new features and improvements, MX-23 beta 1 presents itself as a reliable and user-friendly operating system. Let's delve into the details and explore why MX-23, code-named “Libretto,” is a compelling choice for those looking to break free from Windows.
The MX-23 beta 1 installer introduces several noteworthy improvements. One standout feature is the support for both swap partitions and swapfiles. The option to default to swapfiles during the auto installation process adds flexibility to system configuration. Additionally, the installer now features GUI adjustments and enhanced help guidance, making the installation process more intuitive for users. MX-23 beta 1 also introduces the -oem option, enabling user creation on the first boot after installation, further streamlining the setup experience.

Bid farewell to My Photo Stream and embrace the future with iCloud Photos
Change is an inevitable part of our technological landscape, and as we march forward, it's important to adapt and embrace the advancements that shape our digital lives. In the midst of these transformations, Apple has announced the imminent shutdown of My Photo Stream, marking a transition to a more comprehensive and streamlined solution: iCloud Photos. Join us as we explore the details of this transition and discover how you can seamlessly keep your photos up to date across all your devices while ensuring their safe storage in the iCloud.
On July 26, 2023, Apple will bid farewell to My Photo Stream, the beloved service that allowed users to effortlessly sync photos across their devices. However, it's essential to note that one month before the shutdown, on June 26, 2023, new photo uploads to My Photo Stream will cease. Any photos uploaded before this date will remain accessible in iCloud for 30 days from the upload date, provided My Photo Stream is currently enabled on your devices. By the time July 26 rolls around, all photos will be removed from iCloud, and the service will be officially shut down.

Windows 11 gains 'never combined mode' for taskbar buttons and the ability to see Wi-Fi passwords
If you've been holding off jumping on the Insider program for Windows 11, Microsoft just gave you two very good reasons for getting involved.
The latest build of the operating system on the Dev channel includes two long-awaited features. In addition to the option to stop the taskbar from combing app buttons, Windows 11 Insider Preview Build 23466 also includes, at long last, an easy way to view the password for wireless networks.

Why improving the developer experience holds the key to doing more with less
For some time now, there has been a trend pressing developers to take on more and more responsibilities outside of coding. They are expected to become experts in every domain – even security and cloud spend. Combine developers’ growing scope of work with a skills shortage and continued economic uncertainty, and it’s clear that they are reaching their limits. The result is developer burnout and churn. In fact, it is now thought that up to 83 percent of software developers feel burnout from their work. Developer job dissatisfaction is so high that only 48 percent of developers are confident they will be with the same company a year from now.
As the pressure mounts, it’s becoming increasingly difficult for developers to work effectively and keep up with the demands on their shoulders. To lighten the load, it is more important than ever that organizations focus on optimizing and improving the developer experience. Companies need to focus on how they can ease the pressure and allow developers to do what they do best: building innovative new software. To that end, there are three ways for organizations to create a better developer experience (DX).

Mageia 9 Beta 2 Linux distro raises the bar
In the ever-evolving landscape of Linux distributions, one project continues to shine as a beacon of community-driven excellence: Mageia. With the recent release of Mageia 9 Beta 2, the Mageia team reaffirms their commitment to delivering a stable and user-friendly operating system that rivals even the most established players in the Linux world.
Since the unveiling of Beta 1 back in February 2023, the developers and contributors behind Mageia have been hard at work. Their dedication has resulted in a myriad of bug fixes, security patches, and enticing new updates. Now, with Beta 2 in our hands, we are afforded a glimpse into the future of Mageia 9 Stable -- a future that holds great promise for Linux enthusiasts worldwide.

Cryptojacking: The high cost of free money
If I offered you free money, what would your first response be? For those of us in the security industry, the first thought is probably what the catch is. In the case of cryptojacking, the catch is that all the costs are covered by someone else.
Cloud infrastructure deployments are the bedrock below many companies today. However, that same infrastructure is getting targeted by threat actors that can spot opportunities to earn cash for themselves. Based on the activities of one threat actor, Team TNT, we can now estimate just how much that free money really costs.

The problem of unstructured data in foundation models [Q&A]
Artificial intelligence is only as good as the data that it has to work with and that means that large volumes of information are needed to train the software in order to get the best results.
Ensuring the quality of data therefore is a key task in any AI implementation. We talked to the CEO of Snorkel AI, Alex Ratner, to find out more about the issues involved and how organizations can overcome them.
Best Windows apps this week
Five-hundred-and-forty-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft has started the rollout of the latest Moments update for Windows 11. It introduces a bunch of new features and improvements, including extended live captions support, an option to display seconds in the system tray clock, and an easier way to copy two-factor authentication codes.

Belkin redefines portable power with BoostCharge Pro Fast Wireless Charger for Apple Watch + Power Bank 10K
Today, Belkin launches the BoostCharge Pro Fast Wireless Charger for Apple Watch + Power Bank 10K, a groundbreaking power bank that caters to the needs of Apple enthusiasts on the move. This first-of-its-kind charger offers simultaneous fast charging capabilities for newer Apple Watch models and iPhones, providing a seamless and convenient charging experience anytime, anywhere.
With meticulous engineering, this power bank effortlessly accommodates most Apple Watch band sizes and styles, ensuring a perfect fit for users across the board. It's clear that Belkin has left no stone unturned in their pursuit of creating an exceptional charging solution for Apple devotees.

MSI SPATIUM M570 PRO Series is the world's first 14GB/s SSD
When it comes to storage performance, MSI is often at the forefront, and their latest announcement further solidifies their commitment to pushing boundaries. Today, MSI introduces the SPATIUM M570 PRO Series, a groundbreaking SSD that features the revolutionary PHISON E26 PCIe Gen 5 SSD controller and state-of-the-art 3D NAND flash. This collaboration between MSI and PHISON has resulted in a record-breaking achievement -- a top read speed of 14 GB/s, setting new industry standards and leaving competitors in the dust.
The MSI SPATIUM M570 PRO Series SSD is a testament to the power of collaboration and cooperation. Both MSI and PHISON clearly share the same passion for innovation and the drive to push the envelope. K.S. Pua, CEO of Phison Electronics, commented on the partnership, stating, "The cooperation between Phison and MSI started from the SSD product line. Since both companies have their own expertise in NAND controller and computer system integration respectively, the two companies hit it off. The SPATIUM M570 Pro Series SSD announced by MSI this time adopted Phison's E26 SSD controller. In the future, Phison will continue to support MSI through controller technology."


