
Data mobility -- why it's a must and how to achieve it [Q&A]
Data is still essential for enterprises, but the rise of hybrid working and the adoption of multi-cloud environments has made data mobility and migration a hot topic.
We spoke to Mark Greenlaw, VP of product strategy for Cirrus Data, to discuss data mobility, what's driving it and how organizations need to adapt.

Microsoft releases KB5025239 update for Windows 11, adding new Windows Local Administrator Password Solution (LAPS), security fixes and more
Microsoft has released the cumulative KB5025239 update for Windows 11 22H2, bringing with it not only security and bug fixes, but also general improvements and new features.
Among the highlights are the addition of the new Windows Local Administrator Password Solution (LAPS) as a Windows inbox feature. This update also adds new notifications about Microsoft account to the Start menu, improves Microsoft Defender for Endpoint, and provides easy access to the Bing chat experience in Microsoft Edge via the taskbar.

Samsung's newest PRO Plus memory cards are faster than their predecessors
Today, Samsung has released refreshed memory cards designed for professionals. The faster PRO Plus microSD and SD cards now offer read speeds up to 180MB/s and write speeds up to 130MB/s. These cards offer the ability to capture 4K ultra-high definition (UHD) and Full HD (FHD) videos and photos, making them an ideal choice for content creators and other professionals, such as photographers and videographers.
The new microSD cards are currently available in capacities up to 512GB, while the full-size SD cards are being offered at a maximum capacity of 256GB. The Samsung PRO Plus memory cards also support a video speed class rating of V30, enabling professionals to quickly move large video files while editing.

Microsoft brings PC Game Pass to 40 additional countries
Microsoft may be an American company, but make no mistake, the Windows-maker will happily accept money from consumers in any country. And so, today, Microsoft announces its popular PC Game Pass service is expanding to 40 new countries, opening up the platform to millions of additional gamers around the world.
The service will now be available in new countries including Albania, Bolivia, Costa Rica, Croatia, Cyprus, Estonia, Guatemala, Iceland, Kuwait, Latvia, Libya, Liechtenstein, Malta, Oman, Panama, Peru, Qatar, Romania, Serbia, Slovenia, Tunisia, Ukraine, and more.

Multiple-threat ransomware attacks become more common
It used to be the case that all you had to worry about with ransomware was encrypted data, but the latest Cyberthreat Defense Report (CDR) from CyberEdge Group reveals that last year 78 percent of ransomware victims faced the consequences of one, two or three additional threats unless they paid the ransom.
Additional threats include launching distributed denial of service (DDoS) attacks (42 percent), notifying customers or the media of the data breach (42 percent), and publicly releasing exfiltrated data (40 percent).

Growing digital ecosystems, increasing cybersecurity risk, fragmented regulations and economic challenges emphasizes need for holistic API security
The challenges that the global business community has faced in the last few years have been unprecedented. A pandemic, inflation, an energy crisis, war, an economic downturn, and fragmented and delayed supply chains have all created issues for organizations and have left no industry, market, or region untouched.
Yet, despite these issues, our digital ecosystems and footprint grows ever bigger and increasingly complex. The global digital transformation market was worth $731.13 billion in 2022, and it is now expected to grow at a CAGR of 26.7 percent by 2030; driven in the main by businesses trying to gain competitive advantage. However, it is the size and intricacy of our digital world that makes cyber risks and threats both more present and more potent.

Recovering from ransomware is a long-term commitment -- and a long-term expense
According to Forrester, nearly two-thirds of organizations (63 percent) were breached by ransomware in 2021, up 4 percent from the previous year. Recovery was a long, hard road for many of those enterprises -- while for others, the downstream effects of ransomware were ultimately insurmountable. The alarming rise in ransomware must guide IT leaders' cybersecurity decisions in 2023.
Why is ransomware on the rise? For one, bad actors are becoming far more advanced and prolific. Ransomware gangs continued to make headlines in 2022 for their high-profile attacks and advancements in post-breach encryption. On the other end of the spectrum, the barrier to entry for ransomware is lower than ever before. Ransomware as a service (RaaS) -- which allows bad actors to deploy ransomware for a fee -- has ushered in a new generation of hackers who can target enterprises of all sizes despite their relative inexperience with cybersecurity protocols.

Plugable releases AMS-5IN1E Apple MacBook USB-C hub with MagSafe charger cutout
Today, Plugable launches its latest USB-C hub for Apple laptops. Called "AMS-5IN1E," it is a 5-in-1 USB-C hub that adds five ports to your MacBook Pro or MacBook Air, while still providing access to the MagSafe charging port. The hub includes a full-featured USB-C port that is capable of anything the MacBook port can do, such as connecting a 6K 60Hz display, transferring data up to 40Gbps, and pass-through charging up to 100W.
This 5-in-1 USB-C hub is designed to connect to any MacBook that has two USB-C or Thunderbolt ports next to each other. It is ideal for 14-inch and 16-inch MacBook Pros, introduced in 2021, or MacBook Airs, introduced in 2022. The hub was crafted deliberately to complement Apple’s MagSafe power connector; it features a cutout to avoid impeding the functionality or connection of the MagSafe charger.

Browsing threats top list of CISO concerns
When asked to select the most significant cyber threats to their organizations, browsing Threats topped the list, with 43 percent of CISOs ranking it as a top concern.
A new report from RedAccess, based on responses from 300 chief information security officers across the US and UK, looks at the impact of hybrid working on security posture and the new threats that it introduces. Insecure browsing is ranked as the #1 hybrid/remote work security concern that puts organizations at the most risk.

Firefox 112 delivers Intel GPU performance improvements on Windows builds
Mozilla has released Firefox 112.0 alongside Firefox ESR 102.10.0, the latest versions of its open-source, cross-platform browser.
Version 112 introduces performance improvements for those running Intel GPUs on Windows, plus makes it possible to restore the previous session using the Cmd/Ctrl + Shift + T shortcut.

Automation challenges unpacked -- Part 2: Process complexity
In my last article about automation challenges, I covered how to manage endpoint diversity -- all of the people, systems and devices that execute tasks within an end-to-end automated process. In this piece, I’ll focus on process complexity, which is closely intertwined with endpoint diversity.
Many organizations share the ambitious goal of automating their processes as much as possible. However, in reality, processes are often automated “locally,” or within a single software system, team, or group of devices. To execute a process, you need to coordinate the execution of all of its tasks, based on a certain logic. Most processes -- even if they sound simple -- follow a more complex logic than the straightforward series of steps involved in a confined local process.

BEC attacks rose 72 percent in 2022 with smaller businesses in the firing line
Business Email Compromise attacks increased dramatically last year with a 72 percent rise year-on-year over 2021.
The 2023 Email Security Threat Report from Armorblox shows high volumes of language-based and socially engineered attacks targeting organizations of all sizes and across industries.

Microsoft is changing the function of the Print Screen key in Windows 11
Microsoft is not shy about introducing controversial changes to its software, even if feedback forces it to reverse course further down the line. Windows 11 has seen a huge number of modifications, not all of which have proved popular, and a proposed change to the functionality of a key in Windows 11 is likely to be a divisive move.
The key in question the Print Screen (or Prt Scr and numerous other variations) which currently takes a screenshot and copies it to the clipboard. But in the latest builds of Windows 11, pressing the key does something different by default.
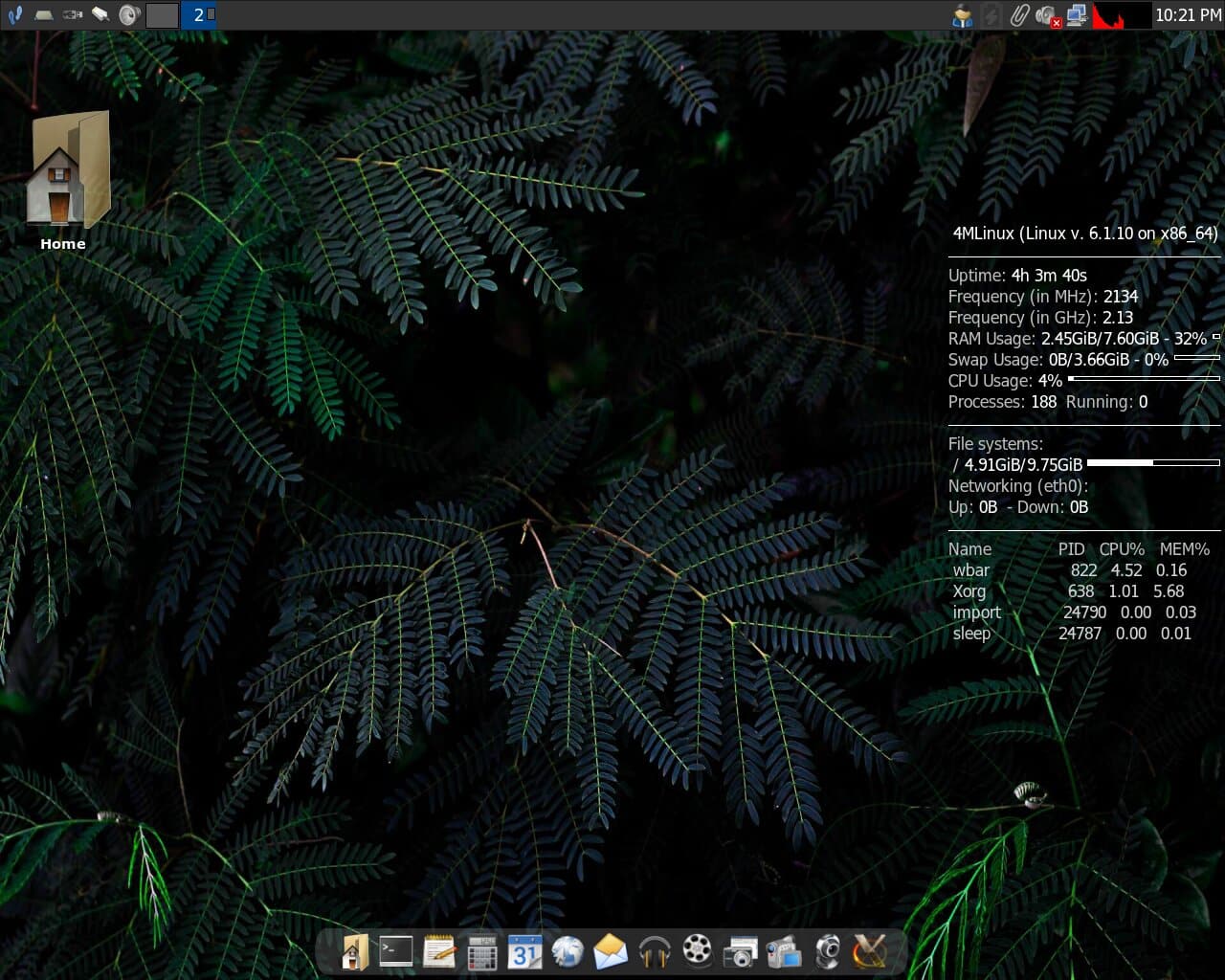
4MLinux 42.0 now available
4MLinux is a lightweight Linux distribution that is known for its versatility and ease of use. The latest version, 4MLinux 42.0, has been released, and the operating system is chock full of new features and improvements.
One of the most significant changes in this release is the status of the 4MLinux 42.0 series, which has been changed to STABLE. This means that users can expect a stable and reliable operating system that they can use for their day-to-day tasks.
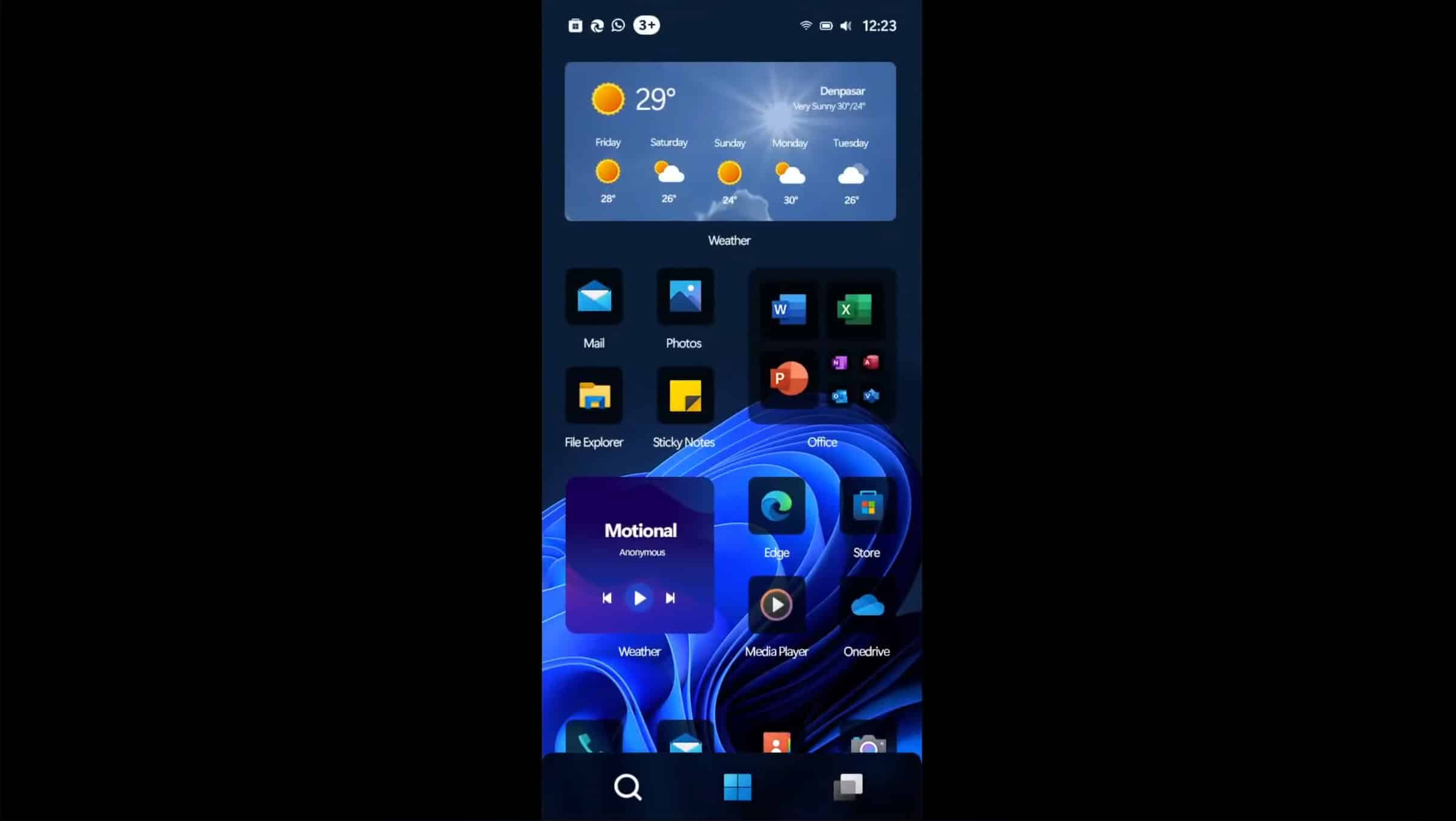
Windows 11 Mobile is everything a phone operating system should be
Microsoft made a significant investment in Windows 10 Mobile, including acquiring Nokia to produce its own handsets. Despite the strengths of the tiled mobile operating system, it was unable to compete with the dominant iOS and Android platforms. While Windows 10 became a successful operating system for PCs and tablets, Microsoft was eventually abandon its mobile ambitions
As Windows 11 gradually replaces Windows 10, the question remains whether it would perform better than its predecessor in the mobile space.



