
The challenge of syncing virtual economies across platforms [Q&A]
As people increasingly demand seamless experiences across platforms, developers face growing complexity in managing unified virtual economies.
In the games sector in particular companies need to leverage distributed architecture, virtual currencies, and real-time inventory reconciliation to ensure consistent user experiences and secure transaction flows.

Microsoft makes it easier for Windows 11 users to type em and en dashes with keyboard shortcuts
Depending on where you are typing, entering an em dash or an en dash can be simple, or a nightmare. In the latest Insider builds of Windows 11, however, it is getting a whole lot easier thanks to keyboard shortcuts being added.
Microsoft has quietly added a couple of new keyboard shortcuts that can be used to type these handy punctuation marks. For now, they are hidden away in the Dev and Beta builds; here is how to access them.

As Windows 10 reaches end of life, Windows 11 is LOSING market share
Next month sees Windows 10 finally reaching the end of (mainstream) support. Microsoft has been pushing people towards Windows 11 for what feels like forever, and it worked – for a while.
The latest market figures show that this is changing. The statistics for August 2025 from statcounter Global Stats show a marked drop in Windows 11’s share of the desktop market.

EU fines Google €2.95 billion over adtech abuses
The European Commission has fined Google €2.95 billion (about $3.19 billion) for abusing its dominance in online advertising technology. The penalty, announced on Friday, September 11, follows findings that the search giant favored its own services at the expense of rivals, advertisers, and publishers.
The Commission ordered the company to end the practices and submit a plan within 60 days to address conflicts of interest in the adtech supply chain.

Poor data quality is hindering AI adoption
A new report reveals that although 84 percent of IT leaders say a Configuration Management Database (CMDB) is essential to driving decision-making and operations, a majority feel their current systems lack the data quality, accuracy and completeness they need, hindering the ability to maximize enterprise AI implementations.
The study from Device42 polled IT leaders across industries including finance, healthcare, government, and technology, and finds that over 50 percent of respondents use CMDBs, monitoring tools, or manual discovery processes, to gain insights about their infrastructure, yet 58 percent report a lack of confidence in their visibility.

Timekettle W4 AI Interpreter Earbuds offer tourists near real-time translation on the go
Timekettle has launched the W4 AI Interpreter Earbuds which combine bone-conduction voice sensors with AI translation models to provide near real-time multilingual communication.
The W4’s bone-voiceprint sensor filters out background sounds, improving clarity in crowded or noisy settings and cuts audio leakage, offering more privacy.

Brits warned of scams ahead of emergency alert test
This Sunday, September 7th, the UK will test its emergency alert system, sending a message that will cause 4G and 5G mobile phones and tablets to emit a loud siren sound and vibrate for about 10 seconds.
But Marc Porcar, CEO of QR Code Generator, is warning that fraudsters are likely to exploit the upcoming government test, particularly targeting elderly and vulnerable people who may be confused by the alerts.
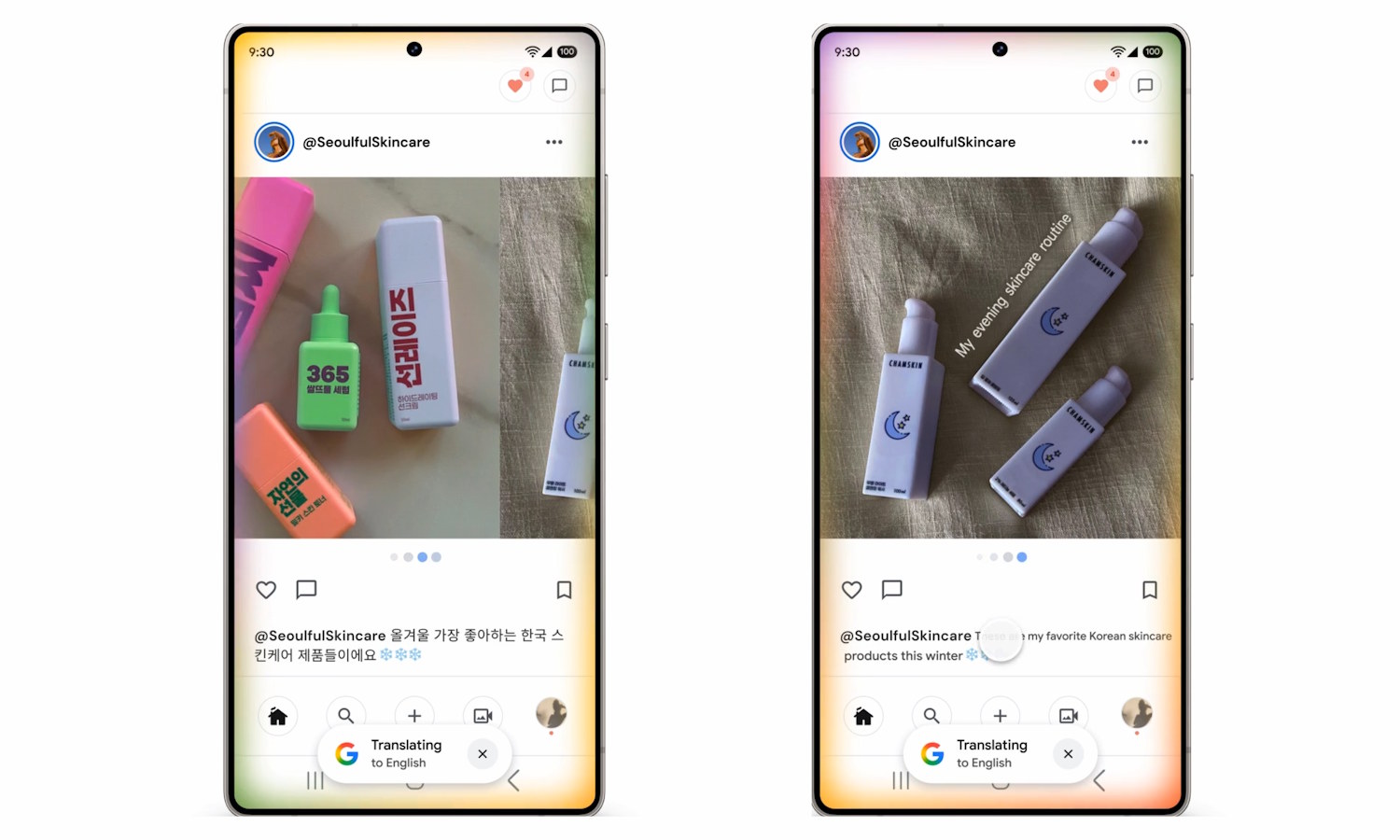
Scrolling support for Google Translate arrives in Circle to Search
Google has added an important feature to the popular translation feature of Circle to Search. While the dedicated Google Translate app or web site are perfect for translating between languages in numerous scenarios, Circle to Search provides another means of accessing the handy functionality.
The fact that Circle to Search offers translation is not new – so much so that Google is quick to point out that “translation is one of the most-used features in Circle to Search”. What is new is the ability to translate while scrolling.

Rethinking AppSec for the AI era [Q&A]
The application security landscape has always been a complex one and can lead to teams spending too much time hunting down vulnerabilities. With AI becoming more popular there are even greater risks to consider.
We spoke to Yossi Pik, co-founder and CTO at Backslash Security, to discuss how AppSec needs to adapt to the greater use of AI.
Facebook Pokes are back – and your guess is as good as ours
Anyone who was a Facebook user in the early days of the social platform (at least when it was a global platform, not just one limited to students) will remember Facebook Pokes. Poking someone on Facebook (oh, do grow up!) was a wordless – slightly creepy – way of interacting with another person.
A Soke did not really serve any purpose beyond reminding someone of your existence in a somewhat passive-aggressive way. Having experimented with reviving the Poke, Facebook is having another go at making the idea relevant in 2025. This is more than just the return of the Poke; this is the Poke on steroids.

Microsoft fesses up to Windows update that caused UAC prompts
Microsoft has admitted that the security updates released for Windows in August caused problems for a lot of users. Affected users experienced a series of unexpected UAC (User Account Control) prompts.
The scale of the issue is large. This is not a problem that is limited to a particular version of Windows – every supported version of Windows that received the August 2025 security update is affected. This means that Windows 10, Windows 11, Windows Server 2022 and Windows Server 2025 have all been hit with the UAC prompts.

Atlassian moves into AI browsers with $610 million purchase of The Browser Company
Workplace collaboration and productivity tool maker Atlassian has agreed to acquire The Browser Company, the developer of Arc and Dia, in a deal valued at around $610 million in cash. The transaction is expected to close in the second quarter of Atlassian’s 2026 fiscal year, subject to the usual regulatory approval and closing conditions. The acquisition will reportedly be funded in cash from Atlassian’s balance sheet.
The deal will bring The Browser Company’s two products under Atlassian’s umbrella. Arc has drawn interest as an alternative to Chrome, while Dia is described as an AI-powered browser designed for work. Neither product is particularly well known, but Atlassian wants to transform Dia into a tool that changes how knowledge workers interact with SaaS applications.

Truecaller adds AI to caller ID to show you not just who's calling but why -- and while the phone is still ringing
Truecaller has announced an AI-powered expansion of its caller ID service, aiming to reveal not only who is on the other end of the line, but also why they are phoning you.
The company says the new feature brings real-time context to incoming calls, with the goal of reducing uncertainty for its 450 million global users. The update comes as scam calls and fraud attempts continue to skyrocket worldwide.

This is what's new and changed in the first new Kodi 22 'Piers' release
It’s been two weeks since the Kodi Foundation rolled out the first alpha release of Kodi 22 'Piers', the latest generation of its hugely popular home theater software.
At the time, it arrived with little fanfare and no details regarding what was new or changed in the release. Finally, though, we now have a detailed breakdown of what's different in this 'significant' update.

New enterprise browser aimed at securing BYOD and third-party devices
Check Point is launching a new Enterprise Browser, extending zero trust security to unmanaged devices like BYOD, contractors, and third-party partners.
The new feature, available to Check Point Harmony SASE customers from today, delivers full visibility, granular policy enforcement, and compliance-ready data protection without persistent agents or endpoint ownership.



