
Four reasons you should go digital in your asset management
Managing assets is an important but laborious task. It can be difficult to track the location, condition or repair history of individual assets, and surveys are highly costly and time-consuming.
It’s likely your work is being doubled-up and digging out asset data requires you to locate the one CAFM super-user on your site, or you end up relying on pieces of paper, only to input the data at a later time.

How Fortune 1000s can get privileged access management right
Privileged access management is not a new concept to most IT and security leaders, but we’ve seen a surge in cyber incidents focused on exploiting privileged access that have renewed its importance. From the Windows Print Spooler vulnerability of 2021 to the Okta breach that impacted hundreds of companies earlier this year, attackers continue to gain access through vulnerable credentials and use that access to move laterally and cause trouble at rapid speeds for Fortune 1000 organizations. While breaches happen, it’s unfortunate when something as simple as privileged access management could have thwarted the attackers.
As geopolitical tensions continue to rise on the cybersecurity front, it’s clear no one is spared from cyberattacks. With that, it’s more critical than ever before for organizations to closely review current privileged access management policies and solutions. Here are some best practices to think about when deciding how to approach PAM properly and securely.

HP chooses Ubuntu-based Pop!_OS Linux for its upcoming Dev One laptop -- could System76 be an acquisition target?
Rumors have been swirling lately that HP was planning to release a laptop running the Pop!_OS operating system. Today, System76's CEO Carl Richell shared on Twitter that this is absolutely happening -- a 14-inch developer-focused notebook called "Dev One." While this is good news for the Linux community overall, it is quite curious. After all, System76 doesn't just maintain the Pop!_OS operating system, it sells computers running the distribution too. In other words, HP and System76 are competitors in the hardware business.
So, what does this tell me? Well, it is purely speculation, but as the old adage says, "where there is smoke, there is fire." And so, it is safe to assume that HP acquiring System76 could be a possibility in the future -- if this new relationship pans out at least. HP could be testing the waters with the upcoming Dev One. Keep in mind, System76 does not even build its own laptops, so we could see the company leave the notebook business and focus on desktops only -- let HP handle the Pop!_OS laptops.

MINISFORUM HX90G Windows 11 mini PC is powered by an AMD Ryzen 9 5900HX CPU and RX 6650M GPU
MINISFORUM is a computer manufacturer that has been cranking out a lot of mini PCs lately. Its machines are looked upon favorably by many consumers that prefer diminutive desktops. Not only are its computers well-made and small, but often quite powerful too. These machines can be good servers, retro-gaming machines, office workstations, home theater PCs, and more.
Many MINISFORUM computers are powered by capable Intel processors, but lately, the company has been making mini PCs with AMD chips too. In fact, the company now has several AMD-powered options. Today, MINISFORUM announces an upcoming AMD desktop that is notable for using discrete graphics. Called "HX90G," the tiny Windows 11 PC is powered by an AMD Ryzen 9 5900HX CPU and RX 6650M GPU. Yeah, this diminutive computer is going to rock!

The challenge of shifting left: Why AIOps is essential
Development teams are being forced to 'shift left'-- under pressure from the business to move more and more work closer to the design and development phase, earlier in the process.
The idea is to catch bugs earlier, before they turn into costly production outages, and should improve efficiency while minimizing risk within the software development cycle. Yet this demand puts even more pressure and responsibility on developers.

The Art of Cyberwarfare [Review]
In recent years cyberattacks have evolved from being the preserve of individual hackers to something much more serious, carried out by organized criminals and even nation states with the aim of espionage and financial gain.
This makes the process of investigating and defending against attacks more important than ever, but the sophistication of the methods used doesn't make the process any easier. This new book from security strategist Jon DiMaggio offers an investigator's guide to understanding the latest generation of threats.

UK police force becomes first to deploy new digital forensics solution
Thanks to increased use of computers and mobile phones almost every crime now has some form of digital element. This has put a strain on the police's ability to investigate effectively and inevitably led to delays.
West Midlands Police in the UK has become the first to deploy a new cloud-based digital forensic solution from Exterro which allows greater collaboration between officers and means cases can be worked on remotely and resolved at greater speed.
Best Windows apps this week
Four-hundred-ninety-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Windows 11 reached broad deployment status this week; this means that Microsoft believes that the operating system is ready now for organizations and all devices that meet the operating system's requirements.

What is unified observability and why is it important? [Q&A]
There has been much discussion around observability in the past few months. With the adoption of hybrid work models and cloud systems, IT leaders have quickly realized the business and security value of creating transparency within their existing tech infrastructure.
Digital experience company Riverbed has announced a business move towards a market it's calling 'unified observability'. The company's vice-president Mike Marks spoke to us about the unified observability concept, why it's integral to IT decision-makers' strategies and offers some thoughts on how enterprises can begin integrating it within their current operations.

Microsoft announces that Windows 11 is now ready for (almost) everyone
Some seven-and-a-half months after the original release, Microsoft has announced that Windows 11 is now "designated for broad deployment".
We use the word "announced" fairly loosely here; the revelation was made in a status change on the release health page for Windows 11. It means that any computer that meets the minimum requirements will now be offered the upgrade, and it lays the groundwork for the rollout of Windows 11 22H2 in the coming months.

Microsoft releases emergency patches for Windows authentication issues
The updates released for Windows in May have been incredibly problematic. The KB5013943 update has been causing various issues, one of which has forced Microsoft to push out emergency to fix things.
There are several out-of-band patches fixes available as the authentication issue they address affect various versions of Windows. In all, there are no fewer than eight patches available: KB5014986, KB5014987, KB5014990, KB5014991, KB5015013, KB5015018, KB5015019 and KB5015020.
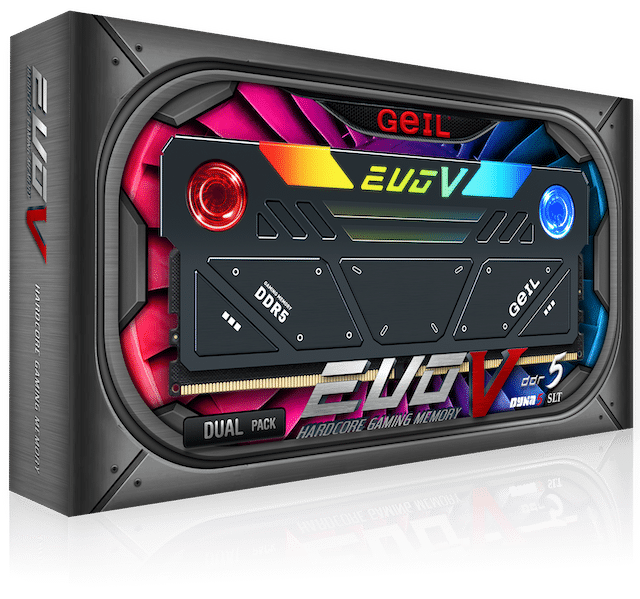
GeIL EVO V DDR5 RGB Hardcore Gaming Memory has integrated cooling fans
Actively-cooled computer memory is nothing new. For many years, companies have offered add-on fans that clip onto your RAM sticks in an effort to reduce heat. Some computer-makers even sell machines with these fans installed from the factory.
Today, however, GeIL takes actively-cooled RAM to a whole new level. You see, its new "EVO V DDR5 RGB Hardcore Gaming Memory" (yes, that is the full product name) comes with little fans built into the heat spreaders! Apparently, these fans are powered by the RAM slot and no additional power source is needed. How friggin' sweet is that? And yes, as the product name implies, this RAM offers customizable RGB lighting too.

IT staff suffering from burnout? Here's how a specialized managed service provider can help
As businesses across industries continue to grapple with staffing shortages due to the ongoing "Great Resignation," many IT workers feel the stress of additional hours and increasing workloads. Put simply, IT workers are suffering from burnout, and businesses are buckling under the weight of unfinished projects and are unable to keep up with the essential maintenance of their database environments.
Recent trends -- such as the rise in resignations, the skyrocketing demand for IT services, the rapid acceleration of digital transformation, and the growing need for new initiatives surrounding data security -- further complicate this situation. To say that IT departments have been overworked would be the understatement of the century.

Hybrid and remote working have become a mega-trend -- what are the security implications for today's enterprise?
Remote and hybrid working patterns have extended the corporate world into every home and user device, and as the global pandemic recedes, this is a trend that is here for the long term.
In fact, it is hard to overstate the pace and extent of digital transformation undergone by the enterprise environment in the past two years. As 2022 unfolds, the daily working experience for employees looks very different to the way it looked before the pandemic.

Want a well-paid a career? Have you considered cybercrime?
OK, so there may not be a pension scheme and a company car, but rookie fraudsters are taking home approximately $18,700 (£15,000) a month with 'cybercriminal CEOs' making up to three times as much as their counterparts in legitimate businesses. According to a new report from Arkose Labs.
The return on investment for launching cyber attacks or committing online fraud is larger than ever before. Some of the highest earning fraudsters are known to be making around $7.5 million (£6 million) a year according to even the most conservative estimates. This is almost three times the amount that FTSE 100 chief executives were paid in 2020, when they earned an average $3.4m (£2.7m).



