
Enterprises need to start planning now for post-quantum security
The power that quantum computing makes available offers benefits in many areas, but it also means cracking encryption becomes much easier, which poses an enormous threat to data and user security.
At its annual Trust Summit conference, DigiCert has released the results of a global study exploring how organizations are addressing the post-quantum computing threat and preparing for a safe post-quantum computing future.

Meta is expanding WhatsApp-style end-to-end encryption to Messenger
Security is vital for digital communication, and that's why the likes of Telegram and WhatsApp's end-to-end encryption (E2EE) is so important and popular. Meta has long been keen to expand this security feature to its various other messaging platforms, and now the Facebook-owner has announced that it is implementing E2EE for all Messenger users.
The company points out that this is currently a test phase, so while more and more people will see immediate security enhancements, the rollout will not be complete until the end of the year.

Why CSOs are prioritizing PKI infrastructure as they adapt to post-quantum cryptography [Q&A]
A growing number of machine identities leaves organizations with the task of managing increasingly complex PKI infrastructure.
We spoke to Chris Hickman, CSO of Keyfactor, about how organizations can go about reducing PKI complexity as well as other trends to keep in mind as they adapt to an era of post-quantum cryptography.

Three quarters of organizations risk their data with poor backup and protection policies
Just 25 percent of IT professionals are following industry best practices for backing up data, according to a new study from hardware-encrypted storage maker Apricorn.
The survey details data backup, encryption and resiliency protocols for over 250 IT professionals in the United States and Canada over the last 12 months. It finds that while 93 percent of respondents say that they factor in data backups as part of their cyber security strategy, only one in four follow the 3-2-1 rule, in which they keep three copies of data, on two different formats, one of which is stored off-site and encrypted.

Is this the year we take quantum threats seriously? [Q&A]
Quantum computing is something that seems to have been hovering just out of reach for a decade or so -- in fact research into the concept first began back in the 1980s.
More recently quantum has come closer to a commercial reality, with big players like IBM publishing a road map with a clear, detailed plan to scale quantum processors and build the hardware necessary to take advantage of the technology and other big players like Google, Amazon, and Microsoft having since followed suit.

Proton Pass is a new password manager from encryption specialists Proton
Proton, the company behind the security- and privacy-focused Proton Mail and Proton VPN, has launched a beta version of its new password manager.
Going under the unsurprising moniker of Proton Pass, the software is described as "perhaps the first one built by a dedicated encryption and privacy company". What this means in practice is that security is greater than in other password managers, with end-to-end encryption on all fields of forms.
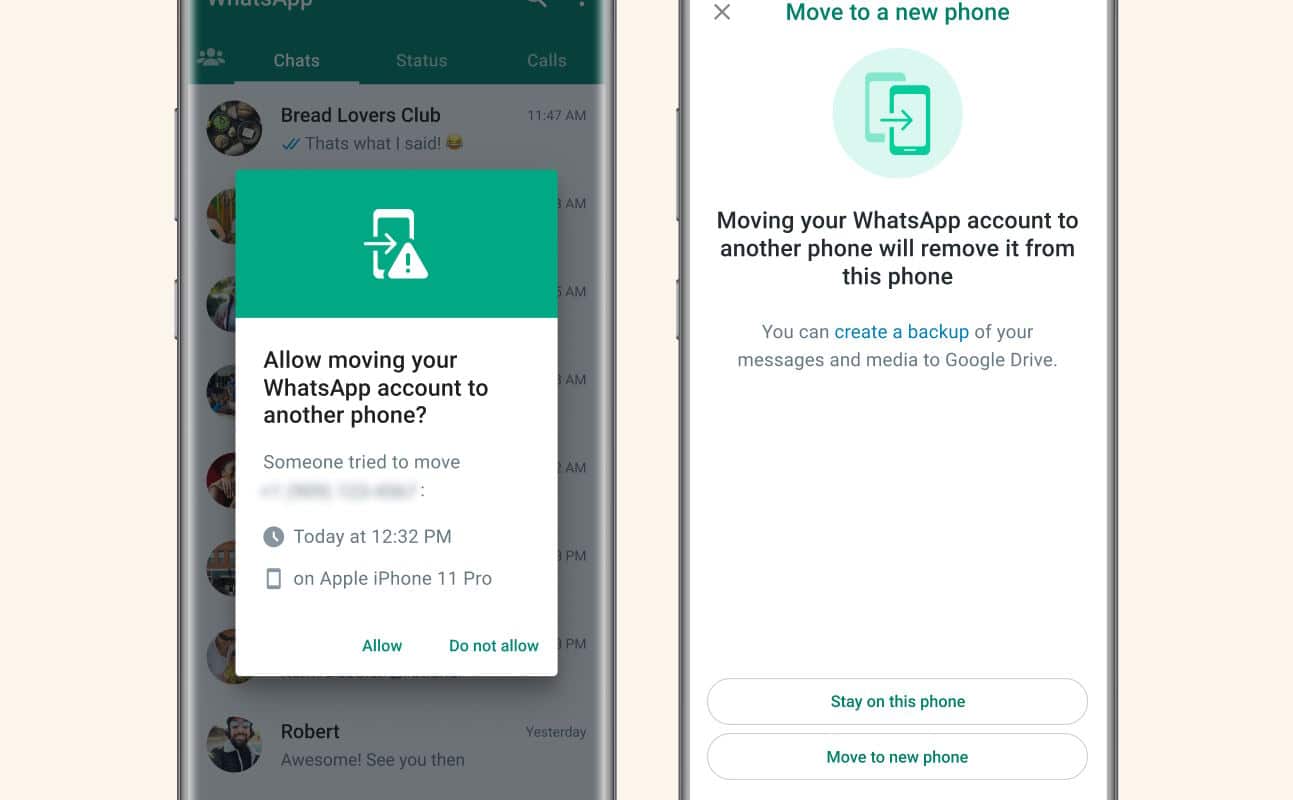
WhatsApp announces a raft of new security features -- Account Protect, Device Verification and Automatic Security Codes
WhatsApp has announced a series of new privacy and security features to help protect against account hijacking and more.
The company says that it believes "your messages should be as private and secure as an in-person conversation", and it is with this in mind that it is launching Account Protect, Device Verification and Automatic Security Codes. Until now, we have only seen signs of these security features in beta versions of the chat app, but now an official announcement has been made promising an imminent rollout.

UK government loses hundreds of IT devices
UK government departments are losing hundreds of devices each year according to Freedom of Information (FoI) requests submitted by encrypted drive manufacturer Apricorn.
The Home Office declared 469 lost and stolen devices between September 2021 and September 2022, with the Ministry of Defence not far behind with 467 mobiles, tablets and USB devices unaccounted for.

Twitter to roll out direct message updates including encryption and 'any emoji reactions'
Things have been undeniably chaotic at Twitter since the arrival of Elon Musk, but the social network is still rolling out new features. Next in line for an update are direct messages.
DMs are due to receive a batch of new features and functionality, not least of which is a much-requested security feature -- encryption. But there is much more to look forward to. And if all goes according to plan, the new features will roll out later this month.
The challenges of network detection and response
Even as we've seen a shift towards remote working, networks remain the part of an organization that are most at risk from cyber attacks.
In a new infographic LiveAction looks at evolving network security challenges and how the right Network Detection and Response (NDR) solution can be used to tackle them.

Why quantum computing threatens security as we know it [Q&A]
Much of our current IT infrastructure relies on DNS to safely route traffic. Securing that infrastructure is in turn heavily reliant on cryptography, but there's a threat looming on the horizon.
Quantum computing will offer a level of processing power that could render current cryptographic techniques obsolete, and that's a problem for the entire internet and networking world. We spoke to Peter Lowe, principal security researcher at DNSFilter, to discuss the possible impact of quantum computing on security and what can be done to address the threat.

New solution secures encrypted data for a post-quantum world
The advent of quantum computing offers a serious threat to the safety of encrypted information. But current post-quantum cybersecurity (PQC) solutions either can't reach edge devices like laptops and mobile phones or required software installation on these devices which is cumbersome and hard to manage.
Now though QuSecure is launching a new solution for protecting encrypted private data on any website or mobile application with quantum-resilient connections and sessions, all with no end-user installation required.

A hybrid approach and risks to security -- quantum computing predictions for 2023
Quantum computing holds the promise of much faster processing speeds but is still widely viewed as still being some way in the future as a commercial proposition. It could boost machine learning and AI, and unlock the power of unstructured data.
Of course quantum also comes with security challenges thanks to its potential to crack passwords and break encryption. Here's what industry experts expect to see happening in the quantum world in 2023.

Encrypted attacks breach 70 percent of organizations
New research from Vectra AI finds 70 percent of organizations have fallen victim to an attack that used encrypted traffic to avoid detection, and 45 percent admit they've been victims more than once.
It's concerning that 66 percent say they don't have visibility into all their encrypted traffic, leaving them highly vulnerable to further encrypted attacks.

Half of IT pros believe quantum computing could put their data at risk
A new study from Deloitte shows 50.2 percent of professionals at organizations considering quantum computing benefits believe that their organizations are at risk from 'harvest now, decrypt later' (HNDL) cybersecurity attacks.
In HNDL attacks, threat actors harvest data from unsuspecting organizations, anticipating that data can be decrypted later when quantum computing gets sufficiently mature to render some existing cryptographic algorithms obsolete.
