Navigating Linux security and management in a multi-OS landscape [Q&A]
While Windows remains the most targeted operating system, Linux, once regarded as 'secure by default', has now emerged as the second-most infected OS, according to the 2024 Elastic Global Threat Report.
Linux's expanding use beyond servers has broadened its attack surface. Plus, its open-source nature, while great for developers, can also lead to mistakes and security holes. We spoke to Apu Pavithran, founder and CEO of Hexnode, to find out more about why Linux is being targeted and how it can be defended.

Neglect of endpoints presents a major security gap for enterprises
A new report shows that endpoint platform security -- securing the hardware and firmware of PCs, laptops and printers -- is often overlooked, weakening cybersecurity posture for years to come.
The report from HP Wolf Security is based on a global study of over 800 IT and security decision-makers (ITSDMs) and over 6,000 work-from-anywhere (WFA) employees, it shows that platform security is a growing concern with 81 percent of ITSDMs agreeing that hardware and firmware security must become a priority to ensure attackers cannot exploit vulnerable devices.

HP offers enhanced protection for enterprise endpoints
The rise of remote and hybrid work has increased the risk of PCs being compromised by attackers with brief physical access, underscoring the need for protection and visibility into the integrity of devices throughout their lifetimes.
To combat this, HP is launching a new HP Enterprise Security Edition, a unique suite of capabilities designed to enhance the physical security of PC endpoints.

Almost a third of IT assets lack some security controls
New research shows that nearly 30 percent of enterprise IT assets are missing at least one critical security control, such as endpoint security or patch management.
The study from Sevco Security also shows more than six percent of all IT assets have reached the end-of-life stage, creating instances of known-but-unpatched vulnerabilities.

The dynamics of modern Windows device management [Q&A]
Despite Apple and Linux gaining ground in recent years Windows still commands over 50 percent of the endpoint desktop market.
This means that Windows device management is a key priority for enterprises. We spoke to Apu Pavithran, founder and CEO of Hexnode, to learn more about device management and how it can be used effectively.

Improving visibility into end-user computing [Q&A]
In the wake of the coronavirus pandemic we've seen greater focus on workplace flexibility with many employees being in the office for fewer days each week.
But to make this work, enterprises must be able to track the state of their end-user computing to understand their access, performance and user satisfaction.

In a hybrid world, enterprises need 'always-on' endpoint management
In the era of hybrid work, endpoints act as the nerve center of business operations -- distributed across multiple locations and networks. While this has bolstered employee productivity and flexibility, the shift has also increased IT challenges, and the exposure to cyber threats targeting remote employees. As the workplace evolves, security must too. To minimize cyber risk and navigate compliance, it’s up to IT teams to intensively monitor, safeguard, and manage employee devices.
As the world of work continues to transform, IT departments are facing increasing demands, compounded by a shortage of skilled staff. They must find ways to boost their operational efficiency. In response, organizations are turning to always-on endpoint management. This approach ensures continuous oversight and control, which is vital as organizations shift to global digital workforces.

2024 technology advancements in endpoint security
Cybercrime and data breaches have escalated to alarming levels, with the global estimated cost of cybercrime in the cybersecurity market reaching over $8 Trillion in 2023. Projected to rise by an additional $5.7 trillion (+69.94 percent) by 2028, the urgency for advanced endpoint security solutions has never been more apparent.
Cybercrime and data breaches have become some of the most significant threats individuals and organizations face in the modern business world. As technology continually advances, so do the methods employed by cybercriminals to exploit it. As a result, endpoint security solutions have become a vital tool for businesses and individuals seeking to protect their devices and sensitive data from harm.
AWS launches its own thin client for enterprises
As more and more organizations turn to SaaS and cloud solutions, having a powerful PC as a desktop solution becomes hard to justify, not to mention the support and security issues that come along with it.
Step forward AWS with the launch of the Amazon WorkSpaces Thin Client, aimed at enterprise workers in order to reduce an employer's technology costs and provide enhanced security.
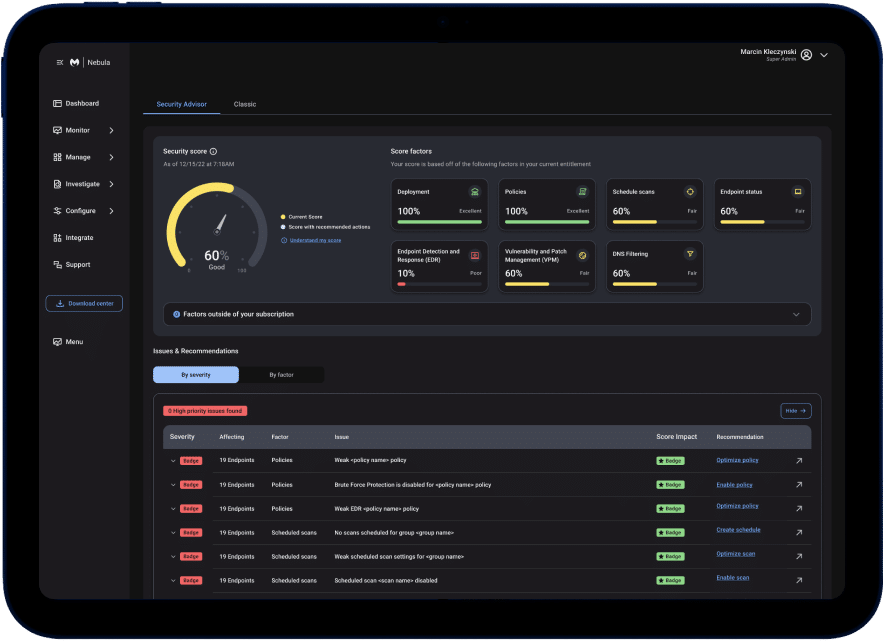
Malwarebytes for Business rebrands as 'ThreatDown'
In a bid to distinguish between its consumer and business offerings, Malwarebytes is relaunching its endpoint security platform for business as ThreatDown.
ThreatDown comes with a new Security Advisor dashboard and is available as a number of bundles that combine protection, threat intelligence, and expertise for IT-constrained organizations, reducing complexity and offering user-friendly security solutions.

How endpoint management can support your cyber resilience strategy
Despite considerable efforts by business leaders to protect their digital assets, in today’s cybersecurity landscape, a security breach is all but inevitable. According to reports, threat actors have already compromised hundreds of millions of records in 2023, and IBM says 83 percent of businesses had more than one breach in 2022. Companies must prepare themselves to respond and seamlessly recover post-attack in this climate and starting at the endpoint could help bolster their cyber resilience.
Endpoint management plays a pivotal role in supporting a robust cyber resilience strategy. By maintaining an up-to-date inventory of all devices connected to your network, endpoint management allows for the rapid identification and isolation of potentially compromised systems, preventing the spread of security incidents and minimizing their impact.
An endpoint management approach to cyber resilience is also supported by principles found in the MITRE Corporation’s Cyber Resiliency Engineering Framework (CREF) Navigator. Their cyber resilience framework focuses on sharing an understanding of what it takes to maintain and inform preparedness and is guided by four pillars. These include:

Three-quarters of organizations struggle with remote work challenges
The shift to remote and hybrid working models has magnified IT operational challenges for 75 percent of organizations.
A new study by Forrester Consulting for HP surveyed over 300 IT and security decision makers and finds the main challenges companies face when managing remote endpoints are ensuring data security (60 percent), keeping software on remote devices up to date (55 percent), and maximizing the accuracy of asset databases (55 percent).

Three lesser-known endpoint vulnerability strategies you might be missing
Modern IT environments continue to become more and more distributed, driving the growth of endpoints across the enterprise. Some research estimates that enterprises now manage more than 135,000 endpoints and Enterprise Strategy Group estimates that more than 70 percent of employees use more than four devices daily for work. That’s a lot of endpoints. And when you combine this endpoint growth with the fact that 560,000 new pieces of malware are detected every day, how can you not wonder if your organizations is the next target for a ransomware or phishing attack.
Security pros are overwhelmed by endpoints and struggle to find the right mix of solutions and strategies that can effectively secure their organizations. The more diverse they are, the more difficult they are to manage and secure (especially with mobile and IoT device proliferation). Just look at recent attacks against Twitter, Slack, Taco Bell, and more. For many organizations, endpoint security is really hard. This is why their security teams need to constantly assess and adjust their endpoint security strategies.
Automation challenges unpacked -- Part 1: Endpoint diversity
Overall, 96 Percent of IT leaders in the State of Process Orchestration report say process automation is critical to helping them accelerate their digital transformation goals. Even so, 72 Percent agree that their real-world, business-critical processes are becoming more difficult to maintain. Why is that the case? For many companies, process automation challenges tie to two core concepts: endpoint diversity and process complexity.
I’ll cover process complexity in part two of this series, but for now, let’s dig into some of the challenges that stem from endpoint diversity and how to solve them.
