
Battery saving app infects over 60,000 Android devices
Researchers at RiskIQ have uncovered a scam app that seeks to steal information and launches advert clicking to make money for the scammers.
The app is advertised as a battery saver. The twist here is that though it will actually do what it says and cut battery use, it does a lot of nasty stuff too.

New tool provides email protection for Office 365
Office 365's dominant share of the online business tools market has made it a popular target for cybercriminals launching phishing and malware attacks.
To offer users extra protection, email security specialist Vade Secure is launching a new solution that's fully integrated into Office 365 and offers filtering powered by artificial intelligence.

Attackers use hidden tunnels to steal financial data
Global financial services organizations are targeted by sophisticated cyber attackers in an attempt to steal critical data, according to a new report.
The study from threat hunting company Vectra says attackers build 'hidden tunnels' masquerading as other web traffic to break into networks and access critical data and personal information. These tunnels are used to remotely control an attack and steal data while remaining largely undetected.

Automation of endpoint security is top priority for IT pros
A new survey of IT professionals finds that automating endpoint detection and response processes is a top priority.
The study from cyber security training company, the SANS Institute, shows 42 percent of the IT professionals surveyed say their endpoints had been breached, and 82 percent of that group say their breaches involved desktops, while 69 percent cited corporate laptops and 42 percent claimed involvement of employee-owned laptops (42 percent).

Website attacks up as smaller businesses are targeted
Website attacks increased 14 percent in the first quarter of 2018 compared to the final quarter of 2017 as cybercriminals set their sights on independent websites and small businesses.
Figures from website security specialist SiteLock show that one percent of sampled sites are infected at any one time. This may not sound much, but it means 18.7 million sites are infected.

Fans targeted by phishing campaign as World Cup gets underway
As the FIFA World Cup tournament enters its second week, cybercriminals are using a phishing campaign to trick fans into opening an infected attachment.
Emails identified by Check Point attempt to lure would-be victims into downloading a schedule of fixtures and a result tracker, but doing so will prove to be an own goal.

Android emulator Andy OS seems to be secretly installing a Bitcoin miner
Cryptocurrency mining malware has become a serious problem recently, and it seems the latest people to fall victim to the threat are users of the Android emulator Andy OS -- also referred to as AndY and Andyroid.
The emulator makes it possible to run Android software within Windows or macOS, but it appears that the installation harbors a dark secret -- a GPU miner trojan that secretly mines for Bitcoin. Over on Reddit there are large numbers of upset users trying to find out what's going on.

72 percent of people fear the theft of their data from company hacks
A new survey of 2,000 UK adults reveals that almost three quarters worry that their details will be stolen every time they hand over bank details and email addresses to companies.
What’s more around one in five have already had their data stolen according to the study commissioned by BullGuard, and almost a third of these had been out of pocket as a result.

Researchers develop SafeSpec to overcome vulnerabilities like Spectre and Meltdown
Computer scientists from the University of California, the College of William and Mary, and Binghamton University have published a paper detailing a new "design principle" that avoids speculative execution vulnerabilities.
Researchers says that the SafeSpec model supports "speculation in a way that is immune to the sidechannel leakage necessary for attacks such as Meltdown and Spectre". Importantly, the design also avoids the problems associated with other Meltdown/Spectre fixes.

Kaspersky: Chinese hackers LuckyMouse hit national data center
Kaspersky Lab has published a report in which it reveals that a Chinese hacking group has attacked the national data center of an unnamed Central Asian country.
The cyberattacks are said to have been carried out by a group known as LuckyMouse -- but also goes by the names Iron Tiger, Threat Group-3390, EmissaryPanda and APT27. The attacks started in 2017, and Kaspersky says that malicious scrips were injected into official website to conduct country-level waterholing campaign.

Apple is updating iOS to lock out police iPhone hacking tools
Apple says that it is planning to release an iOS update that will block a loophole used by police to access iPhones.
Law enforcement agencies and hackers have been able to exploit a handset's Lightning port to get around passcode limits and brute force their way into a phone. But with the upcoming update, Apple will shut down data access via the Lightning port after an hour if the correct passcode is not entered.
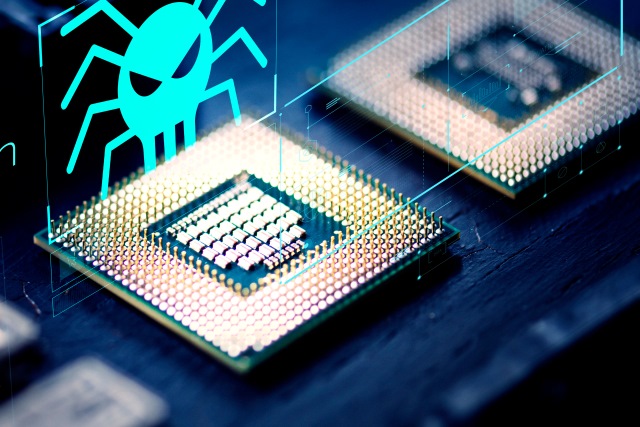
CVE-2018-3665: Floating Point Lazy State Save/Restore vulnerability affects Intel chips
There has been something of a spate of chip vulnerability discoveries recently, and now another one has emerged. Known as Floating Point Lazy State Save/Restore, the security flaw (CVE-2018-3665) is found in Intel Core and Xeon processors and it is another speculative execution vulnerability in a similar vein to Spectre.
The security flaw takes advantage of one of the ways the Linux kernel saves and restores the state of the Floating Point Unit (FPU) when switching tasks -- specifically the Lazy FPU Restore scheme. Malware or malicious users can take advantage of the vulnerability to grab encryption keys. Linux kernel from version 4.9 and upwards, as well as modern versions of Windows and Windows Server are not affected.

Free Chrome extension helps internet users spot fake news
The rise of fake news has affected many people's faith in the internet as a reliable source. In order to help with the problem, Adblock Plus maker eyeo is launching a new browser extension called Trusted News.
Available free for Chrome browsers, the extension works by checking domains, websites, and news sources against the world's largest network of fact-checking databases.

95 percent of parents worry about the risks children face from online games
Although a large majority of parents (95 percent) say they’re concerned about the risks online gaming poses, they admit to allowing games to entertain their offspring.
A new study by McAfee finds 92 percent of parents allow their children to play at least one hour of video games every day, with eight percent admitting that they allow their children to play more than five hours a day. On average, children play video games for 2.13 hours a day or nearly 15 hours a week.

Dixons Carphone suffers two major security breaches exposing customers' bank card details and personal information
Another week, another cyberattack. This time around, it's the Dixons Carphone group which says it has fallen victim to not one but two major breaches.
The bank card details of 5.9 million customers have been accessed by hackers in the first breach. In the second, the personal records of 1.2 million people have been exposed.
