
'Unknown' antivirus tool tops independent tests
German independent testing institute AV Test has released the results of its latest test of Windows home user antivirus programs.
In a surprise result, Kaspersky Internet Security shares first place in the test with relative unknown AhnLab V3 Internet Security. Both achieved an 18/18 rating, the only two programs in the test to do so.

Over 90 percent of cryptocurrency mobile apps contain vulnerabilities
In the week when cryptocurrency values have reached new levels some worrying research from web security firm High-Tech Bridge reveals that more than 90 percent of the most popular cryptocurrency mobile apps on Google Play have common vulnerabilities and weaknesses.
The company used its free Mobile X-Ray service to test apps for security flaws and design weaknesses that can endanger the user, data stored on the device or sent and received via the network, or the mobile device itself.
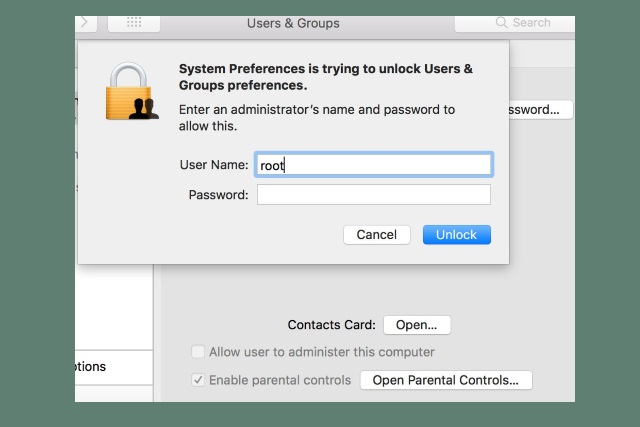
Security: macOS High Sierra bug lets you log in as 'root'... without a password
If you thought that you needed a password to access a password-protected Mac, think again. A massive security hole has been discovered in macOS High Sierra that makes it possible to log in with admin rights without the need to provide a password.
The problem appears to be specific to High Sierra, and the ease with which it is possible to gain unfettered access to a system has many people -- understandably -- concerned.

Most people would stop dealing with companies following a data breach
If a company suffered a data breach, 70 percent of consumers would stop doing business with it, according to a new survey of 10,000 people worldwide.
The study carried out for digital security company Gemalto also reveals that 37 percent now believe that they could be a victim of a breach at any time, compared to those surveyed in 2016 (35 percent) and 2015 (27 percent).

The strangest ways of stealing data
Most data thefts are down to relatively simple techniques, like phishing, in order to get hold of login credentials. But even where systems are well protected, hackers can find ingenious ways of breaching security.
VPN advice site Top 10 VPN has compiled information from research and from real world attacks to highlight some of the more innovative ways of stealing data in an infographic.

Number of stolen credentials at top UK companies triples in 2017
A new study from threat intelligence platform Anomali reveals that the volume of credential exposures among FTSE 100 companies in the UK has dramatically increased to 16,583 from April to July 2017, compared to 5,275 in last year’s analysis.
According to the findings 77 percent of the FTSE 100 -- the 100 largest companies listed on the London stock exchange -- were exposed, with an average of 218 usernames and passwords stolen, published or sold per company.

New solution automates container security
Businesses are increasingly turning to technology to speed up application development and delivery, but this has placed additional pressure on making sure they’re secure.
Cloud security specialist CloudPassage is launching a new set of automated compliance and security controls for containers designed to protect container images, running containers and the container engine/host.

Time to change your password: Imgur was hacked in 2014
While much of the US was celebrating Thanksgiving, social image hosting site Imgur was made aware of a security breach that took place back in 2014. Around 1.7 million user accounts were affected.
This is a relatively small percentage of Imgur users, and COO Roy Sehgal points out that the site has never asked for "personally-identifying information." Nevertheless, the company is contacting the owners of affected accounts, advising them to change their passwords.

The role of education in fighting security breaches [Q&A]
When securing systems most people's thoughts turn to the technology of firewalls, anti-virus programs and so on. What’s often neglected is the human aspect.
Many breaches are down to poor password practices or falling for phishing emails, things which can be prevented with better education. We spoke to Stephen Burke, founder and CEO of security awareness specialist Cyber Risk Aware to get his views on how awareness training can be used to drive better behavior and make businesses more secure.

Half of UK adults want to stop using the Uber app following breach
The news that ride hailing service Uber has suffered, and covered up, a major hack means that millions of people could unknowingly have had their data put at risk.
Data security company Egress Software Technologies ran a flash survey of 500 UK adults this morning to find their reactions to the story.

Intel firmware contains serious Management Engine vulnerabilities, affecting millions of systems
Security researchers have discovered critical issues with the hidden firmware used in some Intel chips. Security firm Positive Technologies discovered a series of serious vulnerabilities in Intel's Management Engine (ME), Server Platform Services (SPS) and Trusted Execution Engine (TXE).
The security flaw could allow an attacker to run code that would be invisible to the operating system, opening up the possibility of invisible rootkit or malware infections, as well as the risk of exposing valuable data. The problem is believed to affect millions of computers and servers.

Adwind remote access Trojan makes a comeback and it's got smarter
The Adwind cross-platform, malware-as-a-service Trojan has been around since 2012. Spread by phishing emails claiming to be invoices, purchase orders, and requests for quotations, it's aimed at high value targets like finance departments.
While it never completely disappeared in recent years the number of attacks did die down. However, security awareness training company KnowBe4 has noted an upsurge in Adwind emails during October of this year.
$31 million in tokens stolen from dollar-pegged cryptocurrency Tether
All eyes may be on the meteoric rise of Bitcoin at the moment, but it's far from being the only cryptocurrency on the block. Startup Tether issued a critical announcement after it was discovered that "malicious action by an external attacker" had led to the theft of nearly $31 million worth of tokens.
Tether is a dollar-pegged cryptocurrency formerly known as Realcoin, and it says that $30,950,010 was stolen from a treasury wallet. The company says it is doing what it can to ensure exchanges do not process these tokens, including temporarily suspending its backend wallet service.

MediaProjection vulnerability leaves 77 percent of Android phones open to screen and audio recording attacks
More than three quarters of Android phones are vulnerable to screen and audio recording by attackers. By exploiting the MediaProjection service, an attacker can easily trick a user into granting the relevant rights to a malicious app.
Although the vulnerability has been fixed in Android 8 Oreo, users running Lollipop, Marshmallow or Nougat remain at risk. MediaProjection is -- by design -- able to capture screen activity and audio, and it does have legitimate uses, but by using a technique known as tap-jacking permission can be given for it to be used for more nefarious things.

Authorities serve Apple with a warrant to access the Texas shooter's iPhone SE
Following the shooting in a Texas church a couple of weeks ago, it quickly emerged that the FBI was having trouble accessing data stored on the shooter's encrypted phone. While authorities refused to disclose the make and model of the device, when Apple said that it had contacted the FBI to offer help, it all but confirmed early reports that an iPhone was at the center of the case.
Now Apple has been served with a warrant to help local law enforcement officers to access messages, photos and other data stored on gunman Devin Patrick Kelley's iPhone SE.
