
Business data at risk from oversharing
Sharing is caring, as the saying goes, but when it comes to business data oversharing is a big problem. A new report from Concentric AI shows the number of overshared files rose 60 percent in 2022 compared to 2021.
Largely this is down to the impact of hybrid remote work, cloud migration and information sprawl across on-premises and cloud data, as well as email and messaging environments on data security.

WithSecure creates an 'undo button' for ransomware
Ransomware attacks continue to plague organizations and can have an effect beyond the financial, damaging reputations and customer trust.
Now though WithSecure has developed a new technology called Activity Monitor that can essentially undo the damage malware can cause.

Google is giving Chrome a new Password Manager -- here's how to enable it
For anyone who struggles to remember the growing list of endlessly complicated passwords needed to gain access to the plethora of online accounts we all now have, a password manager is near-essential. Chrome, like many of the web browsers, has long-featured a tool for storing and automatically entering passwords, and now Google is giving it a much-needed upgrade.
Until now, Chrome's password manager has been functional, but far from being adorned with bells and whistles. Now Google is giving it a new user interface as well as an important injection of new features.

Ransomware detection improves but attacks persist
Defenders have become more successful at detecting and preventing ransomware, but even so its share of incidents declined only four percentage points from 2021 to 2022.
The latest X-Force Threat Intelligence Index from IBM Security also finds that attackers continue to innovate, with the average time to complete a ransomware attack dropping from two months down to less than four days.

Over 98 percent of organizations have misconfigured clouds
According to a new report, 98.6 percent of organizations have concerning misconfigurations in their cloud environments that can cause critical risks to their data and infrastructure.
The research from Zscaler finds cloud misconfiguration errors related to public access to storage buckets, account permissions, password storage and management, and more, have led to the exposure of billions of records.

Three out of four people feel unsafe online -- and cybersecurity doesn't help
A new report finds that even as internet users spend around a third of their lives online, most feel risks are increasing, and cybersecurity is too complex.
The report from F-Secure finds three out of four internet users worry about their safety online, while almost seven out of ten (69 percent) of those surveyed said they don't know who to trust online.

2023 needs to be a year of unification for cybersecurity
The past twelve months have been tough for a lot of organizations. From inflationary pressures to fears of a global recession, many economists have made pessimistic predictions about the year ahead. As a result, controlling and reducing costs is likely to be the focus for many companies in 2023.
Yet despite these economic stresses, IT spending has continued to rise. Gartner has estimated businesses spent around $4.5 trillion in 2022, up 3 percent year-on-year. While part of this spend is driven by digital transformation and the adoption of new technologies, a good part comes from unexpected expenses - especially when it comes to cloud where businesses can easily incur heavy costs without realizing it. Research finds that 80 percent of organizations lack awareness of how best to manage cloud computing, leading to overspending of between 20-50 percent.

Twitter is going to make you pay for some elements of 2FA -- act now to secure your account for free!
Two-factor authentication (2FA) is an important means of securing accounts, making it significantly harder for hackers to gain unauthorized access. So it is perhaps a little surprising that Twitter has announced that it is locking one of the most popular 2FA methods behind a paywall.
The company has announced that SMS-based two-factor authentication will only be available to paying Twitter Blue subscribers. The change will take effect on March 20, and after this date non-paying Twitter users will be limited to securing their account with either an authentication app or a physical security key.
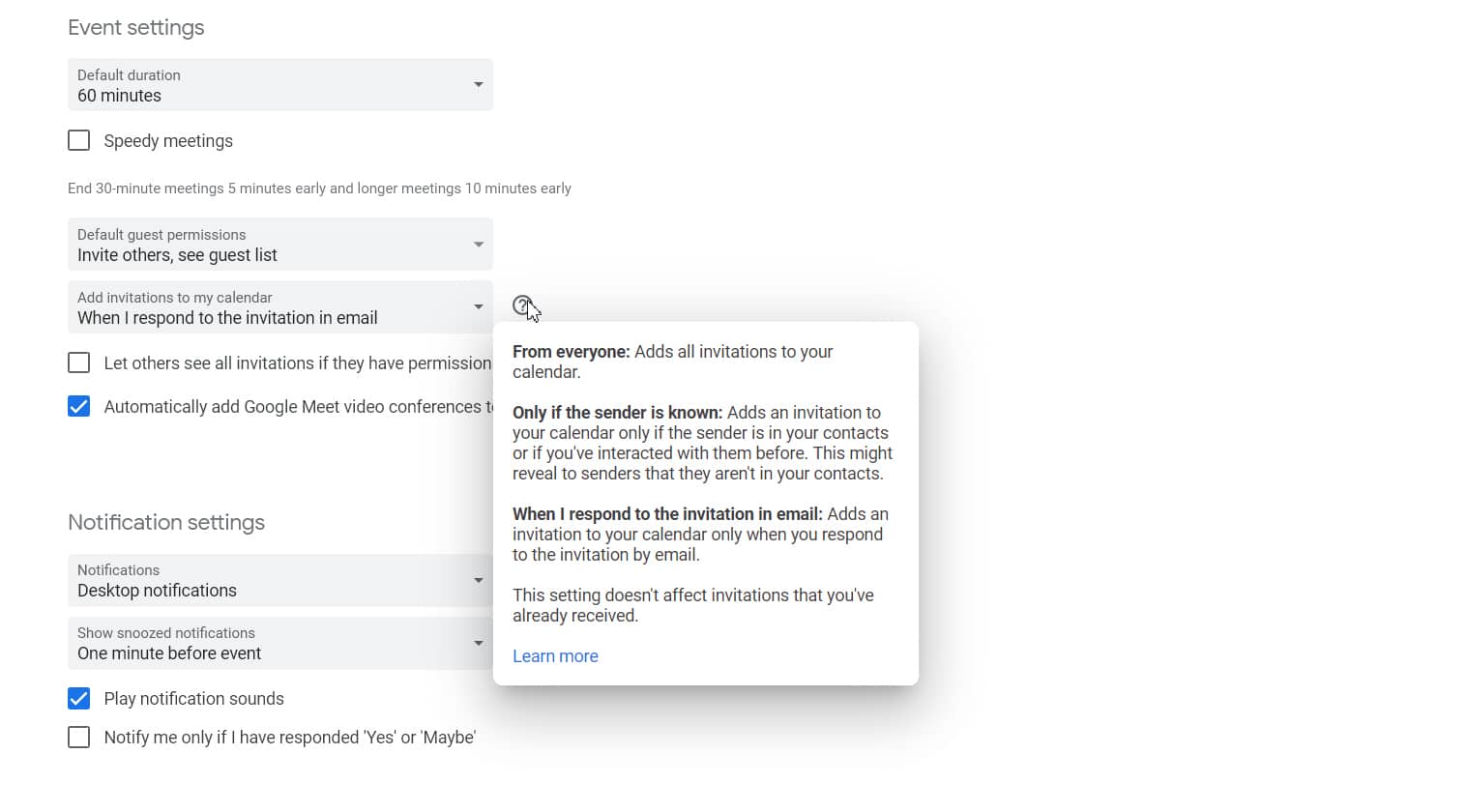
Google Calendar releases new spam protection
Spam in your calendar? It’s not something that most of us think about -- the word brings to mind email and phone calls and even just old-fashioned snail mail. But your online calendar is also a very real target and it may be growing worse.
It’s actually fairly ingenious; a spammer sends an invite to an event and, even if the email invitation goes to your spam folder, the event still goes to your Google Calendar. When you click on the event in your calendar it contains a malicious link. Even if you click 'decline' it can still take you to possible NSFW content, or worse. Plus, declining will simply cross out the appointment and leave the reminder behind.

Why BYOD could be the key to increased business productivity
A 'work device' isn’t what it used to be. Employees are no longer restricted to a single, company-issued device. Instead, they move between devices based on task, time of day, and location. One minute, they might be working at a desk on a Mac, while the next they are on the move, staying productive from an iPhone.
Research has shown that employees highly value the ability to choose which device(s) they use. In fact, 87 percent of respondents in an independent global survey, conducted by Vanson Bourne in 2021 said choosing their work device was important to them, and 89 percent said they’d even be willing to sacrifice part of their salary to be empowered to choose their own technology.

Cloud security: Top trends and threats to watch out for in 2023
As security professionals assess the cloud security challenges that lie ahead for the coming year, one thing is certain. Threat actors will continue to double down on their efforts, utilizing new techniques and refining pre-existing methods as they extend their ever-growing toolbox.
To help enterprises stay ahead of the game, our security research team has highlighted some of the top trends and attack vectors cloud security teams can expect to encounter in 2023.

Free tool helps identify firewall misconfigurations
Misconfigurations are often a source of security issues, especially when they relate to an organization's firewalls.
FireMon is launching a new, free firewall assessment tool that provides organizations with a comprehensive diagnostic report outlining the health of a firewall policy, complete with best practices and suggestions to improve their security posture.

Malicious DDoS attacks up by 150 percent
In 2022, the number of DDoS attacks grew 150 percent globally compared to the previous year, while the number of attacks in the Americas rose even faster, increasing 212 percent compared to 2021.
These figures are from the 2022 Global Threat Analysis Report released today by Radware which also shows the frequency of DDoS attacks saw a significant uptick. Globally, organizations mitigated an average of 29.3 attacks per day during the fourth quarter of 2022, 3.5 times more compared to 8.4 attacks per day at the end of 2021.

Microsoft fixes security issues in Windows 11 22H2 with KB5022845 update
With Patch Tuesday having rolled around once again, Microsoft has issued its regular batch of releases. We've already talked about the KB5022836 update for Windows 11 21H2, but if you're running Windows 11 22H2, you will need the KB5022845 update instead.
The KB5022845 update takes Windows 11 up to build 22621.1265, and it also includes the changes and improvements that were part of the KB5022360 update preview released last month.

Microsoft releases KB5022836 update to fix Windows 11 21H2 security issues
It is the time of the month when Microsoft releases updates for Windows, and as such the company has released a pair of patches for Windows 11. Specifically, we have two cumulative updates in the form of KB5022845 for Windows 11 22H2 and KB5022836 for Windows 11 21H2.
The KB5022836 update takes Windows 11 up to build 22000.1574, and it also includes the changes and improvements that were part of the KB5019274 update preview released last month.
