
We're living in a 'post-breach era' and no company is safe
The infamous Equifax data breach dominated headlines in 2017. The social security numbers, driver's license numbers, names, dates of birth, addresses -- and in some cases credit card numbers -- of 148 million individuals were exposed. With over half of the U.S. population affected, the credit reporting giant spent $1.4 billion in damage control, including paying customers out up to $20,000 and providing them with ongoing fraud assistance and monitoring.
This wasn’t the first breach of its kind to occur, and it certainly won’t be the last: Uber, Facebook, and Google have also been hit, to name a few. But perhaps the most alarming part about attacks like the Equifax breach is that -- at just over four years post-breach -- we’re still not out of the woods yet. And we might never be full. Major breaches leave us vulnerable long after the dust has settled. With more people’s personal identifiable information now readily available to be exploited, it’s only a matter of time.

Rise of the bots -- 42.3 percent of internet traffic in 2021 wasn't human
The latest Bad Bot Report from Imperva shows that bots are an increasingly significant part of the web, accounting for over 42 percent of traffic overall.
More concerning still is that bad bots accounted for a record-setting 27.7 percent of all global website traffic in 2021, up from 25.6 percent in 2020. The three most common bot attacks are account takeover, content or price scraping, and scalping to obtain limited-availability items.

Ransomware vulnerabilities increase as Russia-linked activity surges
The first quarter of 2022 has seen a 7.6 percent increase in the number of vulnerabilities tied to ransomware, with 22 new ones discovered.
The latest Ransomware Index from Ivanti, conducted with Cyber Security Works, shows that of those 22, 19 are connected to Conti -- a prolific ransomware group that pledged support for the Russian government following the invasion of Ukraine.

Enterprise SIEMs fall short on detecting attacks
Enterprise Security Information and Event Management (SIEM) tools are detecting fewer than five of the top 14 MITRE ATT&CK techniques employed by adversaries in the wild, according to a new report.
Analysis by AI-powered detection engineering company CardinalOps also shows SIEMs are missing detections for 80 percent of the complete list of 190+ ATT&CK techniques.

Three out of five organizations lose data due to email errors
Three out of five organizations experienced data loss or exfiltration caused by an employee mistake on email in the last 12 months, according to a new study.
Research from email security company Tessian and the Ponemon Institute shows 65 percent of over 600 IT security practitioners surveyed see email as the riskiest channel, followed by 62 percent for cloud file sharing and 57 percent for instant messaging.

IT pros feel the pressure to maintain organizations' security
As the number of breaches shows no sign of reducing, cybersecurity and development professionals are feeling the pressure to maintain their organizations’ security postures.
New research from Invicti Security finds DevSecOps professionals spend more than four hours each workday addressing security issues that never should have happened in the first place.

Twitter Facebook LinkedIn Spy
How do you know if you're being targeted by an agent of a foreign power? It used to be easy, as soon as he ordered red wine with his fish* you knew he wasn't the right sort of chap.
Nowadays when nation states are more likely to befriend you on social media in order to try to steal sensitive data you can no longer rely on the wine list to help you spot a bad guy.

26 percent still not using strong and unique passwords for work applications
A new study finds that 26 percent of UK respondents admit to not using strong and unique passwords for their various work applications.
Worse still, the report, from MFA provider Beyond Identity, shows 11 percent never change their work password, while almost a quarter (24 percent) maintain the same personal passwords.

Ensuring compliance in the modern enterprise [Q&A]
An increasing volume of regulations surrounding the security and privacy of data have been implemented in recent years. This represents a challenge for businesses that need to ensure they remain compliant.
The challenge has become even greater due to the pandemic and the consequent shift in working patterns. So how can enterprises ensure that they remain compliant and don't fall foul of the rules?

How the Okta breach exposed organizations' cybersecurity immaturity
In early March 2022, authentication security company Okta reported that there had been an attempt to compromise the account of a third-party customer support engineer from Sitel in January. The organization released a statement claiming that the matter had been investigated and contained.
Okta CSO David Bradbury later admitted that up to 366 customers may have been breached, apologizing for not notifying customers earlier. In the weeks since the attack, Okta has released a conflicting statement arguing that the attack affected just two customers, although this is perhaps naïve and hard to prove. Okta has said it recognizes the broad toll this kind of compromise can have on customers, but there is little to suggest that the attackers aren’t already lying dormant inside the networks of further customers.

Open source security plan aims to deliver on development, patching and more
White House officials, The Linux Foundation, OpenSSF and 37 private sector tech companies have announced a 10-point open source and software supply chain mobilization plan and $150 million of funding over two years.
At a summit meeting yesterday several participating organizations came together to collectively pledge an initial tranche of funding towards implementation of the plan. Those companies are Amazon, Ericsson, Google, Intel, Microsoft, and VMWare, pledging over $30M.

Emotet rockets to the top of the malware charts in Q1
The latest Threat Insights Report from HP Wolf Security shows a 27-fold increase in detections resulting from Emotet malicious spam campaigns in the first quarter of 2022.
Based on findings from millions of endpoints running HP Wolf Security, this makes Emotet the most seen malware family in the period accounting for nine percent of all malware captured.

The challenge of guarding against supply chain attacks [Q&A]
In recent years we've seen a trend towards attacks targeting the software supply chain rather than being directly against businesses.
Attacks can include poisoning the software components, stealing secrets to compromise an account, or modifying code repositories to allow for exploits.
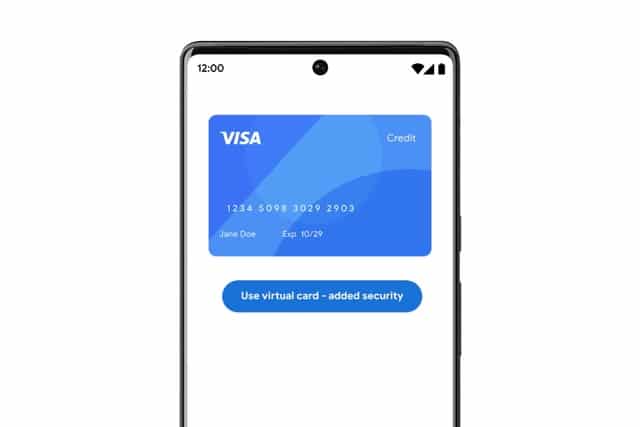
Google is bringing secure virtual credit cards to Chrome
Making payments online is fraught with potential dangers, and there is risk involved with making purchases with your credit card. To help offer a level of protection, many companies -- including the likes of Revolut -- enable their customers to create virtual, disposable credit cards.
Inspired by this, Google is building the same functionality into Chrome. The company announced the upcoming payment security feature at Google I/O, saying that there will be support for autofilling details to help speed up transactions.

Five years on from WannaCry -- what have we learned?
Today marks the fifth anniversary of the notorious WannaCry ransomware attack which hit a number of large organizations around the world and was many people's first encounter with ransomware.
Five years on then, what have we learned from the attack and what long-term effect has it had on the industry?
