5 big myths surrounding computer security and HIPAA compliance

For those in the States, the mad dash to compliance is unquestionably on. After years of taking a "wait and see" approach to Health Insurance Portability and Accountability Act (HIPAA) regulations surrounding medical office technology, healthcare providers (and related covered entities) are scrambling to get their systems and procedures in order. Big Brother has officially set a September 23, 2013 deadline for most new rules that put into place heightened protocols for how patient information (PI) is shared as well as how notifications about breaches need to be handled, among other things.
Naturally, a lot of my consulting clients in the healthcare industry are reaching out for professional help on how to get their IT systems in line as these deadlines approach. One of the biggest facets of the new HIPAA laws, which affects companies like mine that provide hands-on IT consulting, is that for the first time ever we are being considered "covered entities" in the same boat as the healthcare outlets themselves.
Any provider, for that matter, that is either storing or working with any aspect of patient data on behalf of a HIPAA-regulated entity is now being held to the same accountable standards as the primary outlet itself. This means IT consultants such as my company, cloud storage providers, email providers, data shredding companies -- if your hands are getting on patient information in the course of business, you are liable for ensuring strict levels of security and standards for your staff.
Much of the problem with the HIPAA regulations that have been on a staggered integration schedule is that there was no single place a covered entity could go to find out exactly what they needed to do and when they needed to get it done by. I'm not calling myself a HIPAA expert by any means, but I have gleaned a few things from the hours of research and time spent talking to other industry professionals wrangling with the same unknowns as I am. And that's exactly what I want to target in this article. With as much hot air out there, it's important that we distinguish the truths from the falsehoods.
Before I get into the meat of what I wish to cover, I want to make it entirely clear that much of what HIPAA regulations entail, especially surrounding technology usage, are far from being black and white. More accurately, the entire set of policies outlining proper technology integration with acceptable safeguards can be seen in shades of gray. With that being said, there are many items which will keep you on the straight and narrow a lot easier without having to second-guess what implications your decisions will have. I'll cover many of those items below.
This list is far from being all-inclusive, and depending on your (or your customers') circumstances there may be other aspects you need to take into consideration. Since the bulk of my background comes from helping smaller healthcare practices (25 and under) with their technology needs, I am going to preface my article with that understanding in place. Take my recommendations in the lens of being an IT service provider, not that of a healthcare legal expert. I'm curating my thoughts from experience in the field, interwoven with advice from other advocates in the industry.
Myth: Security Through Obfuscation Is Good Security
I've been helping more than a few clients lately (even some who are outside of healthcare) wade through fixing past mistakes about relying too heavily on "security via obfuscation", also known as "security through obscurity" to some. I catch these practices in use with new customers a few times a year, but this discredited approach to security is coming to the surface heavily now that most of the healthcare industry is being pushed under the HIPAA bus.
And it seems that the worst culprits are the small medical organizations, those with perhaps a single owner and a few assistants. These are the ones that tried for many years to do their own IT infrastructure work and are calling us for an SOS in the face of HIPAA. "Security through obfuscation" was an easy way out -- a cheap way to keep up a false sense of security. Checking the "box off the sheet" if you want to call it that. The US National Institute of Standards has formally decried the use of such tactics numerous times in official documents, and HIPAA is seemingly the needle breaking the camel's back.
What the heck does "security via obfuscation" look like? On the residential side of technology, it's employing SSID masking on your home wireless router to prevent others from "seeing your network". You can read up on how far debunked this practice has become, as even an amateur hacker can get around such lowly safeguards in a matter of minutes.
More importantly, on the commercial end of computer security, this comes in the form of (naively) believing that restricting internet access on portions of your computer network will keep you safer from malware and attackers. I am learning this mentality is fairly common in the small medical practice realm, as the time and energy to implement appropriate security hardware and procedures is costly in terms of consulting time and hardware/software.
Why does this form of obfuscation fall short in every regard? For one, many of these same offices allow for unfettered access to the internet by doctors or owners. These individuals are usually running sub-par antivirus software like AVG Free or Security Essentials and are actually letting in malware by the boatload. So yes, while their underlings are not given rights to use Internet Explorer themselves, their bosses are spreading enough malware to go around for everyone and then some.
Similarly, I consulted one office that completely placed most of the computers on a fully isolated network that had no physical access to an internet line. Wonderful -- except for that the fact that none of these systems were running antivirus software, and their patch condition was that of newly unboxed systems from a big box store. Flash drives were being shared between the isolated computers, with items being downloaded on heavily infected systems facing the internet with similar lowly security software. You can put the rest of the pieces together for how many holes that situation had. And this false sense of security is not uncommon. Business owners believe they are doing the right thing, but their methods are not matching their intentions.
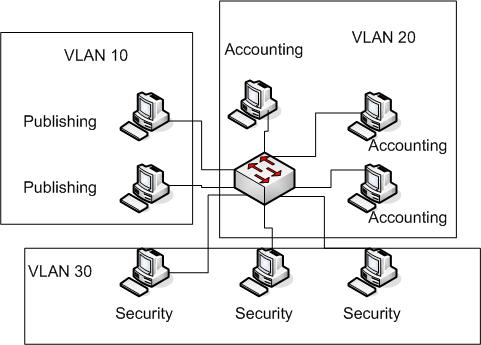
A simple technique for effective network segregation that requires little capital expenditure is called VLAN tagging, short for Virtual LAN. Different parts of your network can be logically separated into distinct "VLANs" and essentially create small quarantine zones between sets of machines that cannot speak to one another. This reduces data exposure, yet still allows internet connectivity for critical Windows Updates and antivirus definitions. We use this technology at our office to allow for safe virus disinfection on customer PCs. (Image Source: TheBryantAdvantage.com)
Time and time again, I am explaining to customers how "security via obfuscation" is a terrible, terrible idea this day in age. You are believing that by doing something as simple as segregating a portion of your network away from the internet, that you are actually gaining security. Absolutely incorrect. Systems that cannot get regular security patch updates, antivirus definition updates, and other critical software updates are much worse off than they would otherwise be in having connectivity to maintain healthy digital footprints.
And the bigger aspect at play here, which many medical offices keep forgetting, is all of the underlying aspects of Obamacare that are forcing digital transmission of customer information to and from government agencies like Medicare. There are stiff penalties that are being introduced for continuing on a strictly paper basis, as the increased time and energy it takes to process paperwork over digital submissions is sizable. Establishments that want to enjoy operating without incurring penalties have no choice but in getting their networks properly integrated with secure internet connections.
If you want to employ kosher network segregation, here are some recommendations for doing it right:
- Get a commercial security firewall. No, home level Linksys or Netgear boxes won't do in a business setting. These boxes do not have the advanced firewall capabilities and VLAN tagging that small-business-oriented boxes can provide. We routinely rely on Cisco's RV small business line of routers/firewalls for medical offices. They are cost effective; have enterprise-grade features; and have zero issues with cloud-hosted VoIP telephone service that many of our customers are moving to.
- Employ a managed switch that can handle VLANs. Managed switches are slightly more pricey than standard fare, but if you want to do network segregation the right way, you should be relying on VLAN tagging. Or, if you have a small office, you can just get a standard switch and pair it with a Cisco RV series router as stated above, and make use of VLAN tagging across all of the switch ports. Mixed in with firewall rules, you can have rock solid network segregation while still preserving internet access for critical updates and virus definitions. The best of both worlds. We love Netgear's business switches due to their excellent construction, lifetime warranties, and relatively low pricing for the quality.
- Invest in quality anti-malware/anti-virus software. AVG Free or Avast Free are not legal for commercial use, and doubly, they are terrible excuses for virus protection in the workplace where accuracy and performance are paramount. Our company relies solely on ESET Endpoint Antivirus for our commercial clients, as it is relatively well-priced and offers coverage for servers and workstations alike in their five-PC bundle packs at no premium. And compared to Kaspersky or Norton, the product has extremely low overhead -- an important necessity for machines that may not be the fastest and are running large medical practice suites.
If you were led down a path that believing in obfuscation was a good idea in the past, it very well might have worked decently before. But at a time now when HIPAA regulations are holding medical offices to higher standards with "reasonable expectations" placed on safeguarding data, you don't want to get caught relying on a security practice that has been debunked far and wide already.
Myth: We Use Office 365/Google Apps for Email and Are Therefore HIPAA Compliant
The marketing gods have a done a wonderful job in trying to give consumers a black and white realm of choices when it comes to HIPAA-compliant email platforms. But as I said previously, the "shades of gray" theory holds especially true when it comes to email hosting choices. There is also a clear distinction between an email platform being HIPAA-capable and HIPAA-compliant. I will be the first one to say that both Google and Microsoft's email platforms are fully HIPAA-capable. But in terms of 100 percent compliance, only Microsoft holds that distinction with Office 365. Whoa -- what?
Lots of discussion has been going on in forums, like this Spiceworks thread, on whether Google Apps is or isn't HIPAA-compliant for the medical industry. Email is a strange beast because its inherent usage involves data that is both at rest (stored by the provider) and data that is in transit (between email systems, like Google Apps to your customers). Both Office 365 and Google Apps have add-on services that can cover the "last leg" dilemma and encrypt the information to the end recipient. And both platforms encrypt all information stored at rest on their systems out-of-the-box. The key difference lies in which company is willing to uphold their legal responsibility in the form of a Business Associate Agreement (BAA).
Microsoft clearly touts that it will gladly sign one of these for any organization that needs it. You could scour the web quite a while (like I have) searching for similar openness from Google, but you will be hard-pressed to find it. It simply doesn't, and likely won't, be signing BAAs for the foreseeable future. I'm not entirely sure what its resistance to this may be at heart, but I simply have to believe that its legal team has determined that the platform has some holes which it just hasn't covered in terms of HIPAA liability. I'm not coming to conclusions, as there is no solid answer available, but I'm merely speaking from the position of a consultant that has had to research this for a number of hours already.
Some third parties have come out to try and fill this void by stating they will sign a BAA on Google's behalf, if coupled with services like Google's Message Encryption, but I am uncertain as to how much validity this approach holds. As a Google Apps reseller and certified consultant myself, I wouldn't offer this to my customers. I simply cannot put my name on the line on behalf of a multi billion dollar company to fulfill HIPAA requirements that they should be signing directly with clients. I don't have the deep pockets to cover myself if Google falters with its product, and am not about to get into such a legal black hole.

Achieving full HIPAA compliance with a BAA from Microsoft is as simple as following this link and signing in with your administrative Office 365 credentials. A screenshot of the PDF I was given (shown above) is just a sample of the full agreement Microsoft offers at no-cost. The whole process is a matter of a few clicks. Microsoft's transparency is reassuring and shows its commitment to a secure email service. Just one of the many reasons I think Office 365 is a no-brainer over the bevy of Hosted Exchange providers out there.
Another key aspect to bringing the email discussion back to reality is the over-reliance of transmission encryption by the medical industry in the form of TLS (Transport Layer Security). Numerous articles have been published, putting TLS reliance into question, such as this in-depth post, which highlights a few glaring holes of the technology as employed in modern email platforms. Placing your HIPAA compliance into the hands of belief that TLS usage alone is satisfactory for keeping patient information safe is slightly naive, if my research is steering me correctly.
For starters, TLS has a big flaw that few refuse to recognize: it has zero security effect on communications between a medical office, for example, and its patients on free email services like Gmail and Outlook.com. This is because TLS has to be enabled and properly configured on both the recipient and sending ends for a transmission to be considered 100 percent encrypted via TLS. If this is not the case, the message will either not be sent, or more likely, be sent anyway with no encryption of any sort -- rendering security in this situation completely moot.
The inherent issue with free email providers is that they do not have the capability to enable TLS on their addresses. This is usually handled at a provider level -- and the likes of Gmail and Yahoo Mail are not about to start providing TLS configuration services for their non-paying customers. It's far fetched and a simple non-starter. Some in the HIPAA compliance realm will bounce back and say that this is technically true, but if your customer has willfully stated in writing that they are comfortable with non-encrypted transmission of their patient information, then this substantiates an all-clear for sending data across an unencrypted line.
But just look at all the loopholes that this could open your medical practice up to. Do you have a full guarantee that you can reproduce that written confirmation of transmission acceptance from the patient if a breach occurred and you had to uphold your organization? Can you easily police your medical staff with dealing in getting these acceptances from patients in writing every single time, when needed? And are you aware and comfortable with the risks of what may happen if you are placed into a situation where data leakage may occur even in your best efforts of bypassing strict usage of encrypted TLS email end-to-end?
As you can see, the above questions have a lot of assumptions being made -- and for many medical offices, these "what ifs" are just a bit too much to handle. This is why most reasonable voices in the HIPAA medical tech compliance realm have been recommending (including my company) that offices invest in solutions that are relatively bullet-proof compared to the wishy-washy standard TLS. Since Office 365 has the easiest path towards full HIPAA acceptance with offices, products like Microsoft's own Exchange Hosted Encryption (EHE) are excellent choices that integrate extremely well with Office 365.
End-to-end encryption services that ensure data is controlled all the way until end-user authentication can be performed (through the use of a password to open the intended message after arrival) are vital towards leveraging an email system that will pass HIPAA inspection with relatively little issue.
For example, a medical provider using Office 365 with EHE now has full assurance that all email at rest (with Microsoft) is encrypted -- all messages in transmission are encrypted (by EHE) and any information being allowed into the eyes of an end user is being authenticated for identity before consumption (since all emails via EHE need passwords to open). This is full end-to-end compliance and exactly what the most stringent HIPAA inspectors will be checking for.
While I don't want to spend too much time on it, the same goes for using instant messaging or video messaging products that do not ensure full end-to-end encryption. One of the few products that are covered by HIPAA compliance for the business realm is Microsoft Lync (or Lync Online, for Office 365 customers) since it is innately controlled under Microsoft's broader HIPAA BAA. If you are messaging clients or others in the industry about patient information over untrusted channels (Skype, WebEx, etc) you may be at risk for violation if anything surfaced due to a related breach. If you are already invested in Office 365, do yourself a favor and just move to using Lync instead.
Myth: My Office Uses Windows XP and Server 2003, But It's OK -- We Have Great Antivirus
Another area that many medical practices have a false sense of security in comes in the form of still using Windows XP and to a lesser extent, Server 2003. Blogs for the medical industry have been covering this pending doom for a little while now, but seeing as Windows XP has its official death set for April 2014, offices are rushing to get this looming threat out the door.
Windows Server 2003, the backbone of many medical offices, is also facing its own end-of-life scenario with a little more breathing room for offices. That product brings its long fruitful life to a conclusion in July 2015 which means medical offices running practice suites or email systems on Server 2003 need to start getting into gear for upgrading or facing the consequences. As soon as these platforms lose support from their manufacturer (Microsoft), they bring the subsequent office into non-compliance without question.
Microsoft has been sounding the warning bells about the end of support for Windows XP, Office 2003, and Server 2003 for a while now. Its official End of Life information center for Windows XP and Office 2003 has some good baseline information on the what and why behind the pending deadline. You can't say that you weren't warned about these end-of-life dates.
There is no plausible, credible argument in the fact that if you are running excellent firewall or antivirus software safeguarding your machines, that you are given a pass on ridding your premises of end-of-life operating systems. Section 164.308(a)(5)(ii)(B) of the HIPAA Security Rules states that you must have "procedures for guarding against, detecting, and reporting malicious software". Placing all your eggs in the basket of an antivirus or firewall solution, while your underlying OS is basking in zero-day threats that will have no patching, is a falsehood you don't want to sit upon in the face of legal action. It won't stand up in court.
Here are some of the directives I'm recommending to customers lately who are scrambling to get off these dinosaur operating systems:
- Make a feasible plan of action to upgrade systems piecemeal. The "buy v. upgrade" debate is not one I'm going to outline in this article. But whichever route you go, it's important to keep costs in mind and smooth out a transition by handling systems in batches. It's not practical, both time-wise and cost-wise, to overhaul an office of 20 workstations and a server in one weekend. That's a recipe for disaster. Work with a trusted consultant to get a few systems done each week, reserving a weekend for moving the server on its own. While HIPAA compliance is important, keeping your business operating is also a part of this equation, too.
- Even isolated systems need to be upgraded. Along the same lines in the belief of "security via obfuscation" as I talked about above, some medical offices we are consulting with have a twisted belief that just because a machine doesn't touch the physical internet, that it is OK for it to continue forward on XP. Wrong! Nearly every computer in use at a medical office is somehow touching patient data or information, and it is held to the same standards as an internet-facing system. Instead of carving out islands of machines that can keep living out their lives on XP, spend your time more wisely and come up with a staggered approach to upgrading your whole computer landscape with Windows 7 or better (and Server 2008 R2 or better, on the server side).
- If you are replacing machines, go with warranty-backed business-oriented OEM systems. While I originally wrote about this argument in an article oriented towards those in the IT consulting community, the same validity to the debate applies to business owners choosing between custom built vs OEM-built computers. Don't believe in the falsehood that saving a few pennies on custom built systems is worth it in the end. As my article proved, most commercial computers (and servers) come with at least three-year warranties on parts and labor for the internals. Unless you plan on paying your IT consultant to do simple replacements on unnecessary part failures, or worse -- opting to handle it yourself as an internal IT guy -- something is going to give. OEM machines are better built, better backed, and generally extremely stable compared to whitebox computers. This isn't the 1990's anymore, and custom building is a relic of yesteryear.
The death of Windows XP and Server 2003 is not as scary if you have a logical plan of action for moving your office into the next generation. Waiting until the last minute is the worst thing you could do. Not only are mistakes in implementation more likely to occur, but labor costs will also come at a premium -- not to mention penalties for missing deadlines like Windows XP's end-of-life date.
Myth: Who Needs Encryption? We Already Lock Our Offices Every Night
Another big misconception offices have when it comes to safeguarding PI is that they place too much reliance on physical security. Camera systems, reinforced deadbolt locks, and internal locked server closets are all wonderful tools in the fight against theft. But what's your answer when the bad guys still get past your initial lines of defense, and end up making off with computer systems? Good question.
This very problem is a big topic locally for me right now, because an administrative office from a large medical group had its premises breached and computers stolen, over a month ago, here in my hometown of Park Ridge, IL. Nearly four million patient records with varying degrees of information, such as personal contact info, was on these systems. The victim at the heart of this story, Advocate Medical Group, is a multi million dollar medical organization with one of the best IT support staffs around. Even it got burned by IT security laziness.
The biggest factor in this leak was not the fact that physical premise security failed. It lies solely in the fact the organization admitted the computers in question had zero encryption technology in place. At best they had local Windows passwords setup, which we all know is useless as soon as a drive is removed from the host system and placed onto a third-party machine for viewing.
Physical security is not good enough on its own these days. Full system encryption, like offered by Windows BitLocker at no extra cost, is becoming a hard reality that we are recommending to our medical customers. A big downside for continuing on Windows XP and Windows Server 2003 is that the platforms have no out-of-the-box encryption options to cover all data at rest on the systems in play. Windows 8 and Windows Server 2008 were the first viable options that brought the easy to use BitLocker technology to the masses, and not employing them on upgrades you are implementing would be a silly oversight to miss.
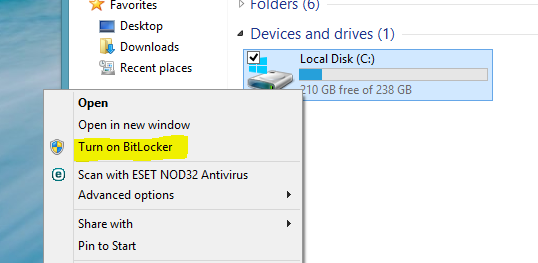
Cost-effective full disk encryption doesn't require expensive hard drives or custom software like TrueCrypt anymore. The above screenshot shows how easy it is for me to turn BitLocker on within my test Windows 8.1 Pro installation. The Pro and Enterprise editions of Windows 8/8.1 include BitLocker functionality built into the core operating system at no extra fee. Windows Server 2008/2012 has the same excellent functionality. Medical offices should heavily consider moving straight to Windows 8 from XP and bypass Windows 7 entirely for this stellar functionality alone.
I wrote an in-depth overview piece on which editions of Windows have BitLocker, how it works, and why it's such a wonderful free piece of technology. Configuration takes no more than 30 minutes per workstation (a server may take some more time, naturally) and it ensures that even in the case of theft, a hard drive from a stolen machine is useless for all intents and purposes. Data is scrambled to the thief unless they can provide the master decryption password -- which is another matter, and important that such passwords are not left in the open on post it notes.
When it comes to data encryption within your office walls, here are some good guidelines to follow:
- Windows BitLocker is free -- use it! An argument for moving to Windows 8 Pro on your next round of system upgrades is to leverage BitLocker at no extra cost. Windows 7 required you to have the Enterprise or Ultimate editions, a fairly high level of licensing that is not reasonable or cost-effective for small businesses. But seeing as even lowly business-oriented machines like Lenovo ThinkCentre desktops and Dell OptiPlex towers come with Windows 8 Pro nearly by default today, your choices are plentiful and price points are still great.
- Backups need to be encrypted, too. Any piece of storage medium that touches patient information or records needs to be safeguarded against potential theft. This includes backup flash drives and hard drives. Part of the reason I so heavily recommend cloud storage providers for backup today is because they generally have HIPAA compliance out of the box, and this saves some hassle on encrypting system backups locally. But regardless of path chosen, ensure the endpoint of data storage has proper encryption safeguards in use. Thumb drives and external hard drives are easy targets for even lowly criminals.
- Simplify your data footprint and reduce leak potential by leveraging the mature Windows Remote Desktop Services (RDS) technology. Every copy of Windows Server made since Windows NT 4 has had some form of what was previously known as Terminal Services, and now called Remote Desktop Services. We are heavily pushing its easiest to deploy option, Session Based Desktops, which is the modern equivalent of the old Terminal Services technology. You can allow employees to connect and handle all patient information from a central server desktop interface without allowing any patient data to leak onto individual workstations in the office. This reduces maintenance costs, data exposure, and potential for leaks of PI. It's a win-win for medical offices, and something we highly recommend considering in any upgrade planning.
Overlooking the obvious by placing too much reliance and trust in your physical security could end up costing you in the event that those safeguards tumble in the face of determined thieves. Full disk encryption, in the form of Windows BitLocker, is completely free and ensures any stolen equipment is uncrackable in the wrong hands. Now that's HIPAA compliance to the nth degree.
Myth: HIPAA Compliance for My Computer Systems Starts and Stops At the Technology Itself
Oh, so wrong once again. HIPAA considers technology infrastructure as key pieces to the compliance paradigm, but it is far from being the end all, be all to ensuring your office is holding itself to the standards expected. The broader discussion is as much one about the people, processes, and procedures in place as it is about the whiz-bang technology being employed. Don't allow any consultant to come in and tell you that "I can give you this, this, and this to get you fully HIPAA compliant for xx amount of money". Foolish thinking, but something I see and hear all the time.
One of the biggest facets that are underestimated regarding HIPAA and technology usage is the people side of things. Encrypted disk drives and email systems are wonderful -- but only when used in the proper hands. Employees that are left untrained in responsible computing in a medical environment are just as dangerous as handing the data outright to third parties. There is rightfully a lot of focus on the technology as of late, but leaving your workers in the dark about how they should be conducting themselves within the network of a covered entity is just as, if not more, important.
Processes are also a key game changer in the move to HIPAA compliance. Do you have processes in place for how patient data should be handled at each step of the way? Are you holding your workers accountable for following these procedures? What are the protocols for when customer information is left outside official channels? These are all questions that your organization needs to answer internally, either concurrently when technology upgrades are being done or even beginning the discussion well before any upgrades are in place. Waiting until new technology is set forth and allowing technical training to take all the focus after a rollout will undoubtedly leave workers in a position with little empowerment to do the right thing.
Bad habits also need to change as HIPAA compliance becomes ever more serious. Many of these items are common knowledge for the tech community, but those entrenched in the medical world are still behind in these office security best practices:
- Passwords and post-it notes don't mix. We said it before, but now it's critical. Post-it notes with passwords on computer screens is a habit which medical professionals need to break. If it's a password you can't remember, it's a bad password to begin with.
- Strong password enforcement on all critical systems is key. Having safe passwords on your email system, EMR suite, and office security system is great -- but don't let small items, like Windows passwords, fall through the cracks. Too many offices we work with brag about security but then make mistakes on machines which are heavily used to "make life easier" for some staff. This is a cardinal sin which could end up biting the establishment down the road.
- Consider cable locks for your actual computer equipment. Most thieves are criminals of opportunity. The easier the target, the more likely they are to make out with your electronics. It may not be the deterrent to stop the most dedicated thieves, but it could be the difference between getting ransacked and the criminal deciding it's simpler to get the office next door. Such security should undoubtedly be coupled with full disk encryption on all devices, as mentioned earlier, using technology like Windows BitLocker (which is free).
- Two-factor authentication is relatively cheap now -- consider it. Want to beef up authentication security on your Windows environment? Key fobs and smart cards are great, but they're expensive to deploy and maintain. PhoneFactor, for example, provides two-factor authentication technology for computer systems at the dirt cheap pricing of about $10-25 per year per user. It knows a thing or two about security -- Microsoft just bought the company out and is leveraging its technology as the official two-factor platform for Windows Azure (Microsoft's virtual desktop cloud infrastructure).
I can't reiterate enough how much user education and proactive training are key ingredients to a HIPAA-compliant medical environment. The above guidelines can help your organization stay ahead of the curve and ensure a solid path towards not only becoming compliant, but staying compliant for the long term.
If your medical office or similar "covered entity" is behind the curve on the newest HIPAA regulations, it may not be a bad idea to start reaching out to individuals who can help steer you in the right direction. In no way do I consider myself a HIPAA expert; but I have been keenly following the meandering progress of both HIPAA and Obamacare and how it is impacting the IT landscape for medical establishments. Much of what these laws entail are equal doses of common sense and infrastructure improvements.
There are a few neat resources which you can freely leverage in your own attempt to get up to par with what HIPAA entails. For starters, the United States Department of Health and Human Services provides this excellent collection of starter guides and outlines on operational best practices. You can also choose to use the free HIPAA Security Rule Toolkit which is distributed by the National Institute of Standards, and works on Windows, Mac OS X, and Linux systems in providing clear instructional assistance on compliance. HITECHAnswers.net also has a great collection of introductory readings on what covered entities are, baseline definitions of HIPAA regulations, and much more.
There is a lot of hot air and misconception out there in terms of what HIPAA compliance looks like. Wrangling the new laws is no small task, but with some elbow grease and a willingness to learn, you can ensure that your organization is following best practices for achieving and maintaining HIPAA compliance. September 23 is right around the corner. Where do you stand?
Photo Credit: Mark Carrel/Shutterstock
 Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.
Derrick Wlodarz is an IT Specialist who owns Park Ridge, IL (USA) based technology consulting & service company FireLogic, with over eight+ years of IT experience in the private and public sectors. He holds numerous technical credentials from Microsoft, Google, and CompTIA and specializes in consulting customers on growing hot technologies such as Office 365, Google Apps, cloud-hosted VoIP, among others. Derrick is an active member of CompTIA's Subject Matter Expert Technical Advisory Council that shapes the future of CompTIA exams across the world. You can reach him at derrick at wlodarz dot net.