Persistent security gaps found in hybrid identity systems

Organizations are continuing to struggle to identify and address security vulnerabilities in hybrid identity systems such as Active Directory, Entra ID, and Okta.
This is among the findings of a new report, from AI-powered identity security and cyber resilience company Semperis, which is based on results from Purple Knight a free Active Directory security assessment tool by Semperis that has been downloaded by 45,000+ organizations.
OT security becomes a board priority for enterprises

Operational technology (OT) can often be a cybersecurity weak spot for enterprises, relying as it does on older hardware and operating systems that are hard to update.
It’s no surprise then that a new report from Fortinet shows there has been a significant increase in the global trend towards corporations planning to integrate cybersecurity under the CISO or other executives.
New Red Hat Enterprise Linux for Business Developers is available for free

Linux stalwart Red Hat has announced the general availability of Red Hat Enterprise Linux for Business Developers. Designed for enterprise development use, the new platform is free of charge as Red Hat seeks to make things easier and more accessible for business development teams.
The new self-service offering is made available through the Red Hat Developer Program with the aim of simplifying an increasingly complex IT landscape. Red Hat is looking to assist development teams in building, testing and iterating on applications more quickly and on the same platform that underpins production systems across the hybrid cloud at no cost.
Elon Musk shunned by Linda Yaccarin as she steps down as CEO of X
Linda Yaccarin has made the surprise announcement that she is stepping down from her position as CEO of X.
Having been the head of Elon Musk’s social media platform for two years, Yaccarin has not given any reason for her decision to leave. However, her announcement comes after xAI’s Grok chatbot spewed out a series of antisemitic content.
YouTube is fighting AI slop with new monetization guidelines

YouTube has become overrun with mass-produced content generated by artificial intelligence. Known as AI slop, such content has spread cancerously across the video platform as pseudo creators seek to make a quick buck.
Now Google has had enough. Seeking to de-incentivize the creation of such content, it is updating YouTube policies so that it will be much more difficult to make money from AI slop.
Microsoft admits Windows Server Update Services sync is failing

Following complaints from users about problems with Windows Server Update Services, Microsoft has spoken out. The company has confirmed that WSUS has suffered issues preventing synchronization and deployment of updates.
This is a serious headache for businesses and organizations that rely on WSUS to manage Windows updates across networks. Reports of errors have been popping up for a couple of days, with scheduled synchronization actions showing to have failed in event logs.
Nvidia becomes world’s most valuable public company at $4 trillion

Nvidia has become the world’s first public company to hit a $4 trillion market valuation, marking a major milestone in the tech and finance industries.
Reuters reports the tech giant’s shares climbed to a record high of $164 on Wednesday, driven by continued investor enthusiasm around AI and its dominant role in powering that growth.
Back to the office means back to basics on security

The shift to remote work was hastened by the Covid-19 pandemic, pushing companies to quickly adapt to employees working from home. Years later, remote and hybrid work remain common, offering a high degree of flexibility that many workers now take for granted.
Businesses have increasingly begun encouraging employees to return to the office, if only part-time. Leaders point to benefits like easier collaboration, improved team dynamics, and a clearer boundary between work and home life.
AI-generated deepfakes used to drive attacks

As generative AI tools have become more powerful, affordable and accessible, cybercriminals are increasingly adopting them to support attacks, these range from business fraud to extortion and identity theft.
A new report from Trend Micro shows that deepfakes are no longer just hype but are being used in real-world exploitation, undermining digital trust, exposing companies to new risks, and boosting the business models of cybercriminals.
Enterprise tech executives cool on the value of AI

Although enterprise AI investment continues to accelerate, executive confidence in the strategies guiding this transformation is falling according to a new report.
The research from Akkodis, looking at the views of 500 global Chief Technology Officers (CTOs) among a wider group of 2,000 executives, finds that overall C-suite confidence in AI strategy dropped from 69 percent in 2024 to just 58 percent in 2025. The sharpest declines are reported by CTOs and CEOs, down 20 and 33 percentage points respectively.
Microsoft adds features and boosts Windows 11 security with KB5062553

Microsoft has released the KB5062553 update for Windows 11 24H2. Billed primarily as a security update for the operating system, it is actually more than that – much more.
As is the case with Microsoft’s monthly security updates, it also includes the non-security improvements, fixes and additions that were previewed last month. One of the key new arrivals here is the new PC-to-PC migration experience which uses the Windows Backup app to ease the process of moving to a new computer.
Google launches Manage Subscriptions for Gmail to kill unwanted email
Keeping on top of emails can feel like a full-time job, but Google is making things easier for Gmail users. We learned about the Manage Subscriptions feature earlier in the year, but it is now starting to hit inboxes.
Everyone receives huge volumes of emails these days, and a lot of time can be spent sorting the wheat from the chaff, determining which email need attention and which are junk to be deleted. Google’s new Manage Subscription option provides a way to quicky see a list of the mailing lists you have subscribed to.
Global PC market rises, but Trump tariffs unsettle US demand
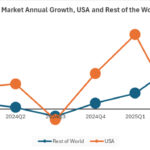
PC shipments rose 6.5 percent year over year in the second quarter of 2025, reaching 68.4 million units globally, according to preliminary data from IDC. While international demand remained strong, vendors in the United States appear to be approaching the looming Trump tariff deadlines with growing caution.
IDC’s latest Worldwide Quarterly Personal Computing Device Tracker shows broad-based PC market momentum across many regions. The continued shift to Windows 11 and an aging installed base have helped sustain replacement demand in both the consumer and commercial sectors.
Google Maps finally lands on Garmin devices for on-wrist navigation

Google Maps is so ubiquitous that it is hard to imagine that there are any unsupported platforms remaining, but there are still a few. This is highlighted by arrival of Google Maps for Garmin smartwatches via the Connect IQ Store.
This free app means that owners of key Garmin devices can now benefit from turn-by-turn navigation on their wrist. The newly released app is targeted primarily at walkers, cyclists and runners, but it can also be used when driving or performing other activities if this feels helpful to users.
Decentralization and why it's a turning point for tech [Q&A]

Mainstream developers and users are increasingly seeking alternatives to big tech’s centralized servers and cloud-based systems.
Issues like data breaches, censorship, and monopolization are driving this trend. We spoke to Mathias Buus Madsen, CEO of Holepunch, about why decentralization matters and how we can expect the trend to develop.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.