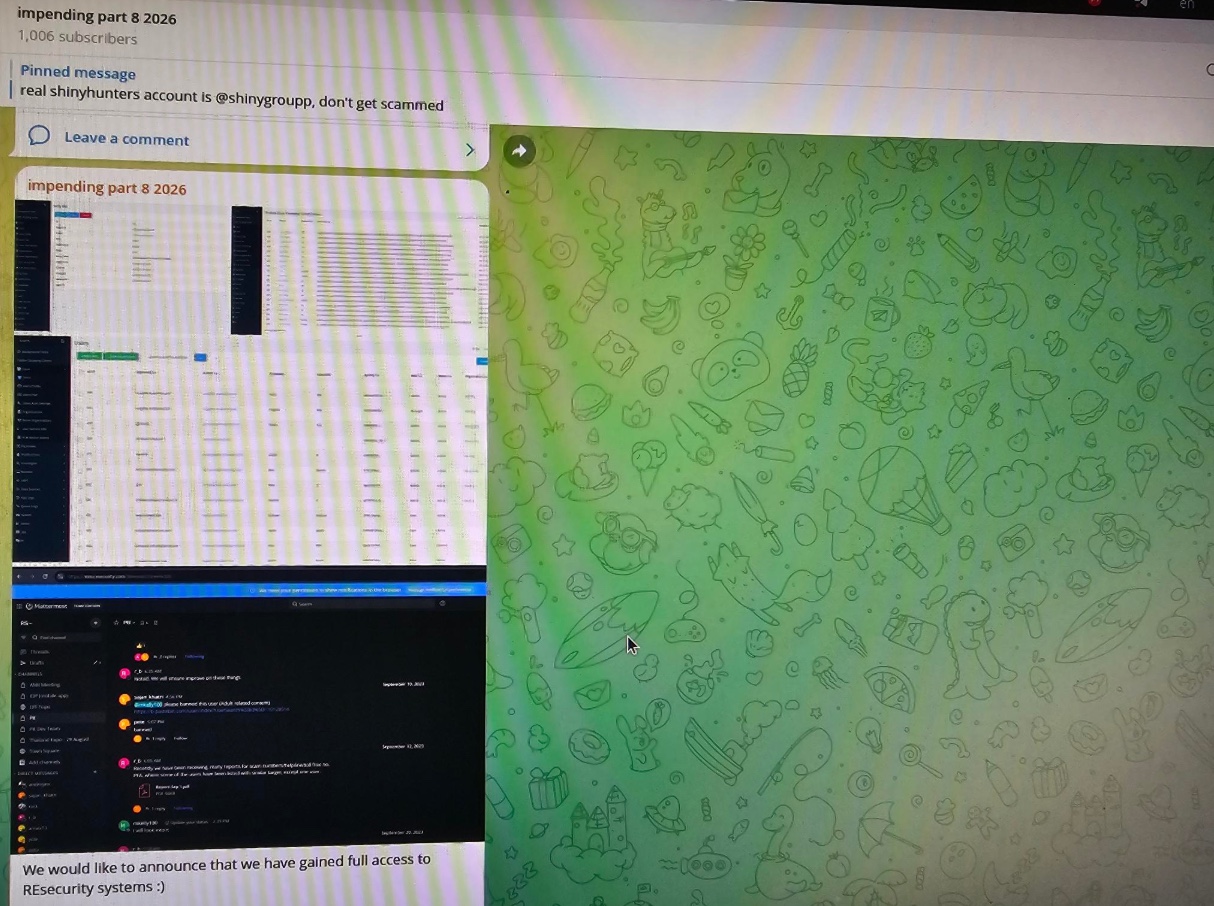
Resecurity says security breach was nothing more than hackers duped by a honeypot
A hacking group claiming to have breached the defenses of Resecurity and gained access to internal data was actually fooled by a honeypot stuffed with synthetic data, says the security firm at the center of the story.
Dating back a few weeks, the data breach was originally thought to have been the work of the notorious ShinyHunters group. It is now clear that this group was not involved, and that no real data was accessed.

Microsoft makes securing files faster with hardware-accelerated BitLocker
If you have use BitLocker to secure files within Windows 11, you will almost certainly have noticed something of a performance hit. Microsoft is not unaware of this, and is taking steps to help improve things.
The company is rolling out hardware-accelerated BitLocker, which should help to provide a speed boost on systems with NVMe drives. The new approach helps to avoid bottlenecks which can massively impact on performance.

Nissan confirms customer data was involved in Red Hat security breach
Back in September, US software firm Red Hat suffered a security breach. The incident was not acknowledged until October, but even now the full impact of the breach is unfolding.
Japanese car maker Nissan has just confirmed that it was indirectly affected by the Red Hat security breach. As a result of this, detailed contact information for thousands of customers were accessed by hackers.

US slaps a ban on foreign-made drones and components
Ever mindful of security, the US has announced a ban on new foreign-made drones and components key to their manufacture. The Federal Communication Commission’s public notice says that uncrewed aircraft systems (UAS) “pose an unacceptable risk to the national security of the United States or the security and safety of United States persons”.
The ban only applies to new devices and components, so anything which has already made its way into the US is unaffected. In implementing a blanket ban on all foreign-produced drones, there has been no need to publish a list of affected models.

SoundCloud warns of data breach with ‘limited data’ of a fifth of its users
Following a period of instability over the last few days, SoundCloud has confirmed a data breach by “a purported threat actor group”. The streaming service says that it “detected unauthorized activity in an ancillary service dashboard” and that an investigation found that “certain limited data that we hold” had been accessed.
SoundCloud says that while around 20 percent of users’ data was involved, “the data involved consisted only of email addresses and information already visible on public […] profiles”.

Google is discontinuing its dark web report security tool
Google has suddenly – and quietly – announced that its dark web report is to be discontinued. Designed to scan the dark web for leaked personal data, Google has decided that the tool is no longer needed.
There is not long to go until the tool shut down. In just a month’s time, there will be no more scanning of the dark web for data; one month after this, the dark web report will disappear entirely. Here’s what you need to know.

Microsoft massively expands the scope of its bounty program
Microsoft is just one of many technology firms that have a bounty program that offers financial rewards for anyone who discovers security flaws in its products and services. The company has just announced a huge expansion of the scheme so it even covers problems found in third party code.
Vice President of Engineering at Microsoft Security Response Center, Tom Gallagher, announced the broadened scope at Black Hat Europe. He stressed that “keeping our customers secure is our top priority”.

Firewalla Orange is a pocket-sized WiFi 7 router with multi-gigabit firewall
Firewalla has announced Firewalla Orange, a portable multi-gigabit firewall and WiFi 7 router built to bring Zero Trust protection to networks in homes, offices, and travel setups. It’s the latest product in the company’s range of cybersecurity devices that includes Firewalla Purple and Firewalla Gold SE.
The new product delivers an advanced security stack that includes intrusion prevention, VqLAN microsegmentation, device isolation, GEO-IP filtering, VLAN support, and Active Protect rules that shut down threats in real time. It’s rated for more than 2Gbps of packet processing, so can support cloud services, smart home devices, and remote work activity.

Microsoft fixes years old actively exploited .lnk flaw in Windows
Microsoft has addressed a security flaw in Windows that has been exploited since at least 2017. The company has not made an official announcement about the fix, but it was spotted by 0patch.
The flaw is known as the Microsoft Windows LNK File UI Misrepresentation Remote Code Execution Vulnerability and has been tracked as CVE-2025-9491. The fix was included in the November batch of updates for Windows.

Tor is switching to the Counter Galois Onion encryption algorithm
Tor (The Onion Router) is switching its encryption algorithm to help boost security and privacy. The change is being introduced to protect users against certain types of attack, and sees the browser adopting a new “research-backed new design” called Counter Galois Onion.
The algorithm that is being updated is the one used to encrypt user data as it travel across a circuit via multiple relays. In making the switch, Tor concedes that its previous encryption design “looks funny”, hence the need to replace it.

Wyze launches new Window Cam for indoor window-mounted security
Wyze has announced the Wyze Window Cam, a compact camera designed to give users exterior-style security from inside their homes. The camera mounts directly to a window and uses a wide aperture lens and sensors to deliver clear, bright color footage even in low light.
The Window Cam can be used to monitor driveways, gardens or front or back-facing areas. It attaches to the interior side of a window using nylon fastener strips, avoiding the need for tools or permanent fixtures. Wyze bundles a long power cable and clips for any necessary routing.

Microsoft to make Sysmon a native Windows 11 tool
Windows 11 power users will be pleased to learn that Microsoft is planning to bring the Sysmon (System Monitor) tool to Windows as a native utility. Usually part of the Sysinternals suite of utilities, Sysmon will be integrated into not only Windows 11, but also Windows Server 2025 starting next year.
The announcement was made not by Microsoft, but by Sysinternals creator Mark Russinovich. He says that by integrating the Sysmon utility into Windows, administrators will simplify deployment and bring additional functionality.
Google to use Android developer verification to allow safe app sideloading
Like Apple, Google has gradually made it more difficult to install apps from outside its own store. But the company is aware that neither users nor developers necessarily want to be tied to just the Play Store – this is why it has come up with the Android developer verification program.
The idea is that Google will check and verify developers so the users know they can be trusted. Now the company has an update based on early feedback it has received.

Microsoft is killing off Defender Application Guard for Office
More than a year-and-a-half after announcing its retirement, Microsoft has revealed its plans to fully remove Defender Application Guard from Office.
The journey has been a long a slow one for the this security feature which isolates untrusted Office documents in a virtualized contained. Deprecation was first announced way back in November 2023, and the process of complete removal will not be finished until the end of 2027.
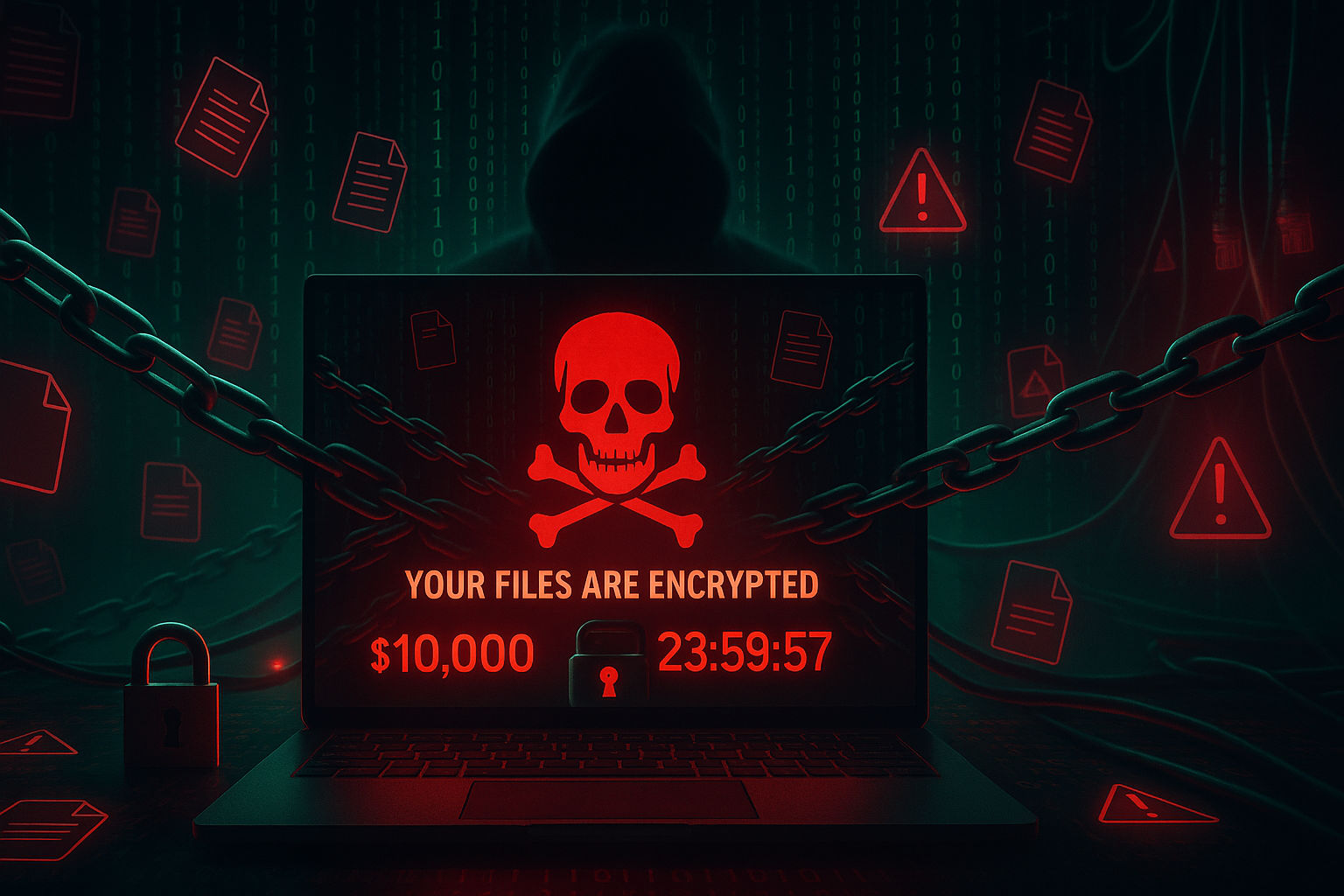
ESET brings its ransomware protection to home and small business users
ESET has added new ransomware recovery and scam protection capabilities to its consumer and small business products. The security firm's latest offerings, ESET HOME Security and ESET Small Business Security, bring its enterprise-grade Ransomware Remediation feature to homes and small offices for the first time.
Ransomware incidents remain among the most damaging forms of cybercrime worldwide. ESET’s Ransomware Remediation system automatically creates encrypted backups when a threat is detected, so that users can restore any affected files once the attack has been neutralized, hopefully minimizing downtime and data loss.
