
iBUYPOWER offers Intel Core Ultra 200S series processors in custom gaming PCs
iBUYPOWER, a system integrator known for custom and pre-built gaming computers, has announced that Intel’s new Core Ultra 200S series processors are now available in its gaming PC lineup. Starting today, customers can configure their iBUYPOWER systems with these processors, which come with a three-year labor and two-year parts warranty.
The Intel Core Ultra processors are designed to improve gaming performance with AI-based features and advanced computing capabilities. iBUYPOWER customers can use these processors to optimize their setups, benefiting from AI-powered auto-framing, creative task acceleration, and enhanced data security with three built-in AI accelerators.
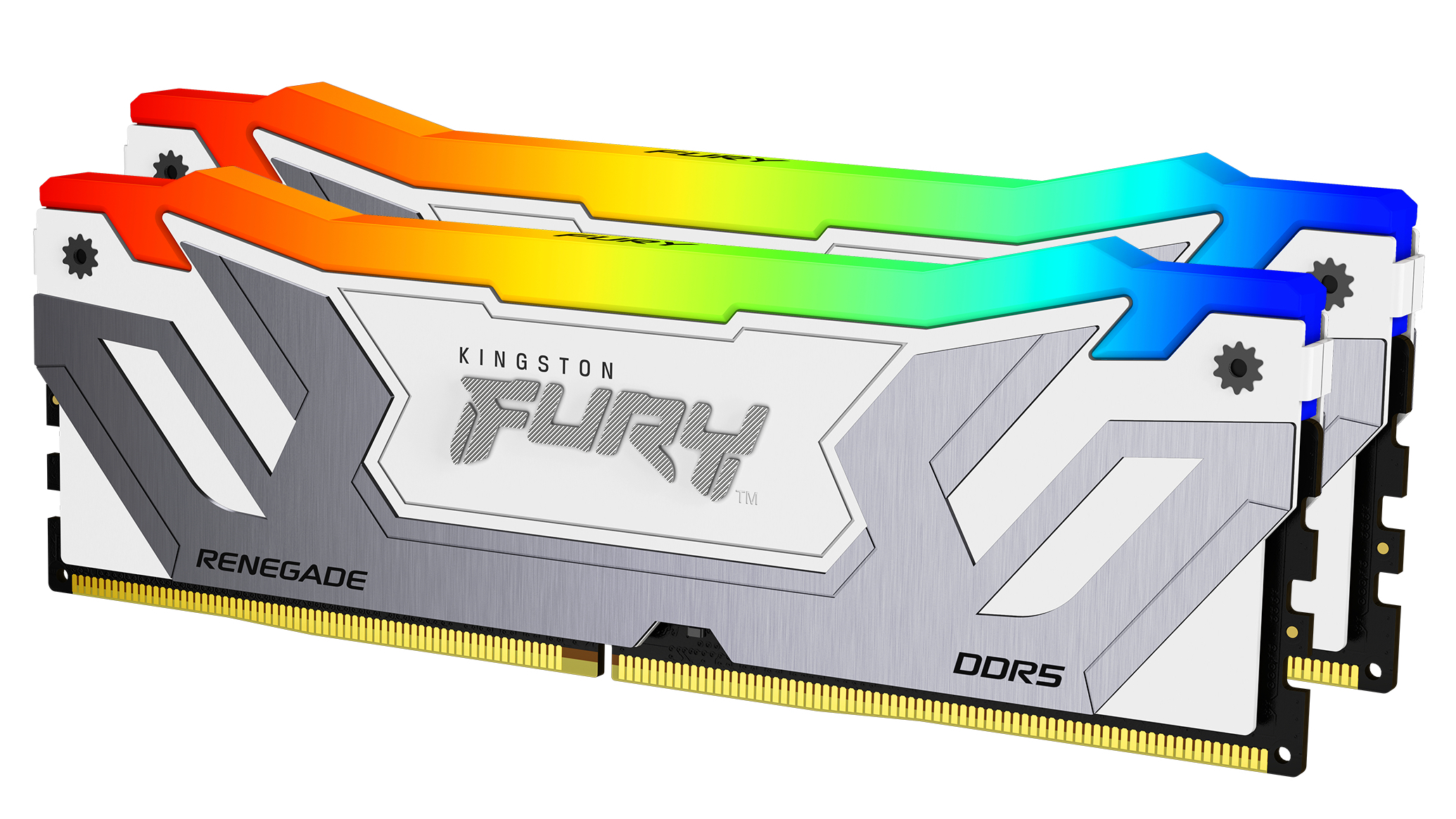
Kingston Fury Renegade DDR5 CUDIMMs to launch with Intel 800 series chipset compatibility
Kingston Technology has just announced the Kingston FURY Renegade DDR5 CUDIMMs, designed to take advantage of Intel’s upcoming 800-series chipset. This chipset, formerly known as Arrow Lake, is the first to use Clock Drivers on CUDIMMs. At a speed of 6400MT/s DDR5, JEDEC now requires a Client Clock Driver (CKD) on UDIMMs and SODIMMs, which improves signal integrity. To distinguish these advanced modules, JEDEC has labeled them as CUDIMMs and CSODIMMs.
Kristy Ernt, DRAM business manager at Kingston, highlighted the appeal of these new modules: “The introduction of overclockable DDR5 CUDIMM modules allows us to reach a broader range of professionals who demand top-tier performance and want to push the limits of their systems without compromising signal integrity.”

Save $35.99! Get 'The Data Science Workshop, Second Edition' for FREE
With so much data being generated, there is immense scope to extract meaningful information that’ll boost business productivity and profitability. By learning to convert raw data into game-changing insights, you’ll open new career paths and opportunities.
The Data Science Workshop begins by introducing different types of projects and showing you how to incorporate machine learning algorithms in them. You’ll learn to select a relevant metric and even assess the performance of your model. To tune the hyperparameters of an algorithm and improve its accuracy, you’ll get hands-on with approaches such as grid search and random search.
Tor Browser 14.0 amps up privacy, but drops support for older Windows and macOS systems -- are you still protected?
The Tor Project has announced the release of Tor Browser 14.0 for Windows (both 32-bit and 64-bit), Mac, Linux, and Android. The browser offers increased privacy to users by redirecting their internet traffic through the open Tor network.
Tor Browser 14.0 updates the browser’s underlying code to the latest Firefox ESR release -- 128 -- while also introducing new improvements that allow its fingerprinting protections to work with several new features introduced in Firefox’s latest ESR release.

Satechi introduces Qi2 Trio Wireless Charging Pad with foldable design
Satechi has launched the Qi2 Trio Wireless Charging Pad, a new accessory designed to charge multiple devices using the latest Qi2 technology. The charging pad can simultaneously provide 15W of power to a Qi2-enabled iPhone or smartphone, 5W to AirPods, and 5W to an Apple Watch, including fast charging for Apple Watch Series 7, 8, 9, Ultra, and Ultra 2.
An upgraded version of the Trio Wireless Charger With Magnetic Pad, the Qi2 Trio features a foldable design that can function as both a flat charging dock and a stand, supporting portrait and landscape orientations. It also works with iOS 17’s StandBy Mode and watchOS’s Nightstand Mode. The pad comes with a 45W US power adapter, UK and EU travel adapters, and a USB-C cable to keep things organized.

MIXX launches StreamQ C4 noise cancelling wireless headphones for $49.99
MIXX has introduced its StreamQ C4 noise cancelling wireless headphones to the US market. These headphones offer features such as active noise cancellation (ANC), transparent mode, quick charging, hands-free calling, and voice assistant compatibility.
The StreamQ C4 headphones provide up to 40 hours of battery life on a full charge. A quick 15-minute charge can deliver up to 8 hours of additional playtime. The active noise cancellation feature helps reduce external noise, while the transparent mode allows users to hear important sounds from their environment, such as traffic.

Google launches new AI risk assessment tool
Last year Google launched its Secure AI Framework (SAIF) to help people safely and responsibly deploy AI models.
Today it's adding to that with a new tool that can help others assess their security posture, apply these best practices, and put SAIF principles into action.

AI expected to be the most important tech in 2025
A new study by the IEEE -- the world's largest technical professional organization -- focuses on on what are likely to be the most important technologies in 2025 along with future technology trends, including expectations for AI's market growth, benefits, uses, and skill sets.
The study surveyed over 350 CIOs, CTOs, IT directors, and other technology leaders in Brazil, China, India, the UK and US at organizations with more than 1,000 employees, it finds that 58 percent believe AI will be the most important tech next year, while 26 percent say cloud computing and 24 percent robotics.

Free dark web reports reveal organizations'exposed information
Most cyberattacks are carried out using compromised credentials, but it can be hard for businesses to know if their information has been leaked.
In order to make it easier to discover leaked data, Quadrant Information Security is launching a free Dark Web Reports service offering insights into compromised credentials and leaked information and actionable advice on how to address them.

Apps, analytics and AI: 4 common mistakes
The app economy is big business. Apple’s App Store ecosystem alone generated a staggering $1.1 trillion in total billings and sales for developers in 2022. But as users demand more relevant and immediate experiences, often driven by AI, developers increasingly need competitive advantages to stand out.
Real-time analytics, supercharged by generative AI, can provide a critical edge by allowing developers to extract key insights and quickly adapt their apps to reflect changing user expectations. But only 17 percent of enterprises today have the ability to perform real-time analysis on large volumes of data, and adoption remains slow. Meanwhile, even when companies are able to perform real-time analytics, there are several common mistakes that can prevent them from reaping its full benefits:
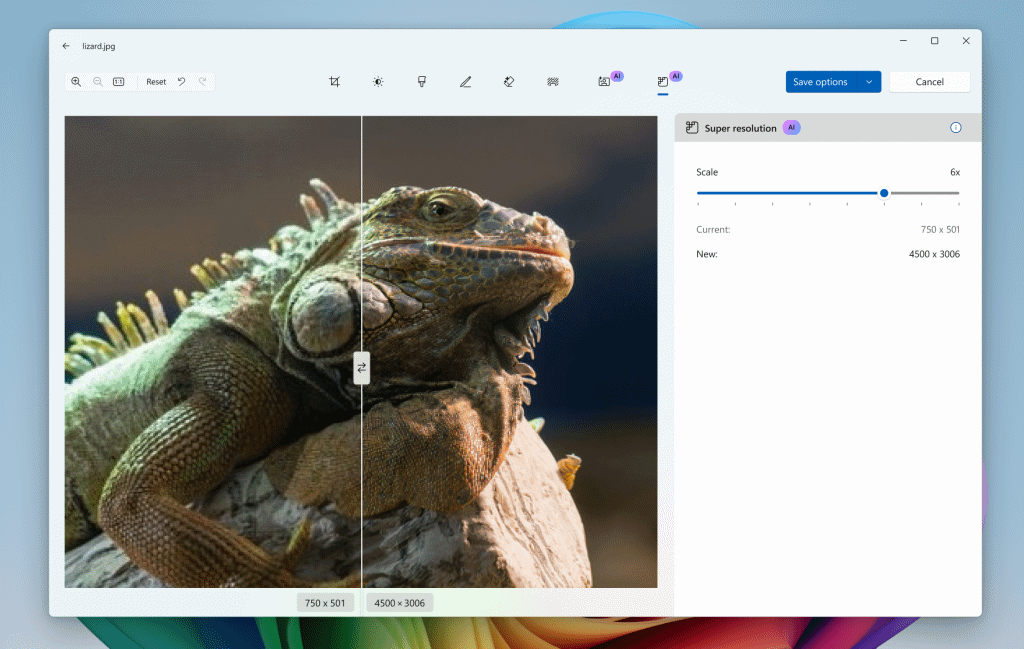
Microsoft creates a new reason to buy an AI-powered Copilot+ PC -- image upscaling in Microsoft Photos
Image upscaling has existed as a technology for a number of years, but the results for both videos and still images have proved somewhat mixed. But with the continuous creeping development of AI, Microsoft has just added a preview of super resolution for Copilot+ PCs to its Photos app.
While there are updates and new features for both the Windows 10 and Windows 11 versions of Microsoft Photos, image upscaling is only available to Snapdragon-powered Copilot+ PCs with Windows 11, version 24H2 and higher in the Canary, Dev, and Release Preview Channels. A powerful new OCR feature is available to everyone, however.

Microsoft releases Windows 11 update with revamped Start menu, printer fixes, and new Copilot button remapping
Microsoft has released the KB5044380 update for Windows 11, a preview version of the update that will roll out to everyone next Patch Tuesday. There is quite a lot to be found in this particular release including the previously announced ability to remap the Copilot key on a keyboard if you don’t like its default function.
As this is a preview update there are no security fixes, but problems with multi-function printers, Microsoft Teams, and high battery usage have all been addressed. There are numerous tweaks, fixes and additions that are available immediately to anyone installing the KB5044380 update, but there are also some that are subject to a more gradual rollout.

McAfee and Yahoo News partner to introduce AI-powered deepfake image detection
McAfee has announced a new partnership with Yahoo News, integrating its AI-powered deepfake image detection technology into the platform’s content quality system. This collaboration is designed to help Yahoo News quickly identify images that may have been created or modified using AI, with the goal of maintaining credibility and ensuring that content meets editorial standards.
McAfee’s deepfake image detection tool will flag AI-generated images, which are then reviewed by the Yahoo News editorial standards team. The integration provides a scalable and efficient method to detect manipulated content, offering additional resources to ensure that Yahoo News continues to deliver trusted journalism. This detection is currently being applied to content in the U.S. only.

Third-party JavaScript tags put security at risk
While businesses understand that third-party JavaScript tags collect information, only 13 percent are confident they understand what information they collect and only 26 percent are aware that tags can leak their private user data to other organizations.
A new report from the Jscrambler platform for client-side protection, with research conducted by Dimensional Research, shows 97 percent of respondents say they know that third-party tags collect sensitive or private information regularly.

Employees lack fundamental security awareness
Many executives are concerned about their employees' level of cyber risk awareness, with a new survey showing that 70 percent believe their employees lack critical cybersecurity knowledge, up from 56 percent in 2023.
The study, of 1,850 executives across 29 countries, from Fortinet also shows that over 60 percent of respondents expect more employees to fall victim to attacks in which cybercriminals use AI.
