
PorteuX Linux 1.7 released with smaller ISOs and performance optimizations
PorteuX 1.7 has been released, bringing various updates and optimizations to the lightweight Linux distribution. One of the key highlights of this release is the reduced size of the ISOs compared to previous versions, thanks to numerous optimizations that aim to enhance overall performance and stability.
Several fixes have been made, including addressing issues with the run-pipewire and gui-cheatcode-loader scripts, which previously ran indefinitely in the background. The release also resolves problems with LXDE freezing when dragging files from Engrampa over the file manager’s side panel and fixes a notification bug related to ‘sticky keys’ in Xfce 4.18.

Western Digital celebrates 20 years of My Passport with a special edition drive
Western Digital has been helping people store their digital lives on the go for two decades. To mark the 20th anniversary of its popular My Passport drive, the company has released a special edition - the My Passport Ultra, 20th Emerald Anniversary Edition. First launched in 2004, the My Passport drive now boasts capacities as large as 6TB, a massive increase from the original 40GB model.
This special edition drive sports a beautiful emerald color, which Western Digital says symbolizes loyalty, peace, and security. It’s not just about looks, though. The My Passport Ultra continues the company’s tradition of durability and reliability, offering a sleek anodized metal enclosure for extra protection. It works right out of the box with Windows, Mac, and even mobile devices, making it a versatile choice for today’s tech-savvy users.

Are we starting to give up on cyber hygiene?
A new survey of over 7,000 individuals suggests a growing wave of pessimism among workers regarding cybersecurity practices.
The study from CybSafe and the National Cybersecurity Alliance shows 53 percent believe staying safe online is possible, down by five percent from last year, while only 60 percent think online safety is worth the effort, marking a nine percent drop.

Cyber resilience vs. cybersecurity: Which is more critical?
Today, it’s not ‘if’ but ‘when’ any organization will be compromised. So, while it’s essential to strengthen cybersecurity across the entire organization, it’s also imperative to plan for a significant cyber-attack and the worst-case scenario. No business can be 100 percent secure but they can be resilient. Resilience is about continuing to thrive amidst adversity. This is why cyber resilience can be more important than cybersecurity. Every organization can take positive actions to improve their cyber resilience today, ensuring they can continue to win even if they are affected by an incident. They can start by having the right mindset and instilling a culture of cyber security and cyber resilience.
Strong cyber resilience will enable an organization to continue to operate key business processes, even when they are under attack. This means keeping people safe, guaranteeing data security, and protecting their reputation with their customers, partners, suppliers, industry and government regulators and other key stakeholders. Having a strong cyber resilience will save stress, time and money -- it will give you a return on your investment -- and you’ll be better prepared for uncertainty in the future.

Maximizing Microsoft Copilot's potential: The critical role of tenant consolidation
Microsoft recently reported that tens of thousands of working professionals are using Microsoft Copilot in their everyday operations. Experts expect this number to grow significantly as the tool integrates more seamlessly into workplace environments, driving productivity and efficiency. However, many companies may not realize that to get the most benefit from Copilot, they should consolidate tenants.
Let’s take a closer look at the benefits of tenant consolidation and how working professionals can leverage Microsoft Copilot to the fullest. With tenant consolidation, companies can transform operations and future-proof their organization amid remote workforces, economic pressures and security concerns, among other developing industry factors.

Save $25.99! Get 'Artificial Intelligence and Machine Learning Fundamentals' for FREE
Machine learning and neural networks are pillars on which you can build intelligent applications. Artificial Intelligence and Machine Learning Fundamentals begins by introducing you to Python and discussing AI search algorithms.
The book covers in-depth mathematical topics, such as regression and classification, illustrated by Python examples. As you make your way through the book, you will progress to advanced AI techniques and concepts, and work on real-life datasets to form decision trees and clusters.
Microsoft Office 2024 unveils new Fluent design, updates apps to match latest Microsoft 365 release
Subscription-based software isn’t everyone’s cup of tea. Some of us would prefer to pay a one-off fee upfront for a software package we know will last us years without any significant changes. Thankfully, Microsoft caters to both types of user, both with the subscription-based Microsoft 365 range of products and now with a brand new version of its flagship product, Microsoft Office 2024.
Office 2024, which starts from $149.99 for its Home edition, replaces Microsoft Office 2021 and brings the feature set bang up to date. It’s also joined by a new Office LTSC 2024 release aimed firmly at larger organizations who want an on-premises edition for a disconnected or restricted environment.

Cyberrisk quantification and how to measure it [Q&A]
Enterprises face an increasing range of cybersecurity risk, but quantifying and managing those risks can be a difficult task.
Recent Gartner research shows that more companies are trying to roll out cyber risk quantification (CRQ) in order to get a greater understanding of their risk profile.

Hanging on the telephone set to be replaced by messaging services
It was 175 years ago that Italian inventor Antonio Meucci came up with the technology that would later be improved and popularized by Alexander Graham Bell to become the telephone.
New research from cloud communications company Sinch finds that newer technologies are starting to change how we communicate -- particularly with businesses -- offering richer, more interactive, and personalized experiences.

Ransomware still a major threat despite disruption to RaaS groups
Ransomware remains a formidable threat facing organizations, with 49 active groups impacting more than 1,000 publicly posted victims in the third quarter 2024, according to a new report.
The report from GuidePoint Security's Research and Intelligence Team (GRIT) shows threat actors are increasingly leveraging legitimate services and platforms to deliver targeted phishing messages. While the abuse of trusted notification services is not a new approach to delivering malware, the research team has recently observed novel -- and progressively sophisticated -- delivery techniques.
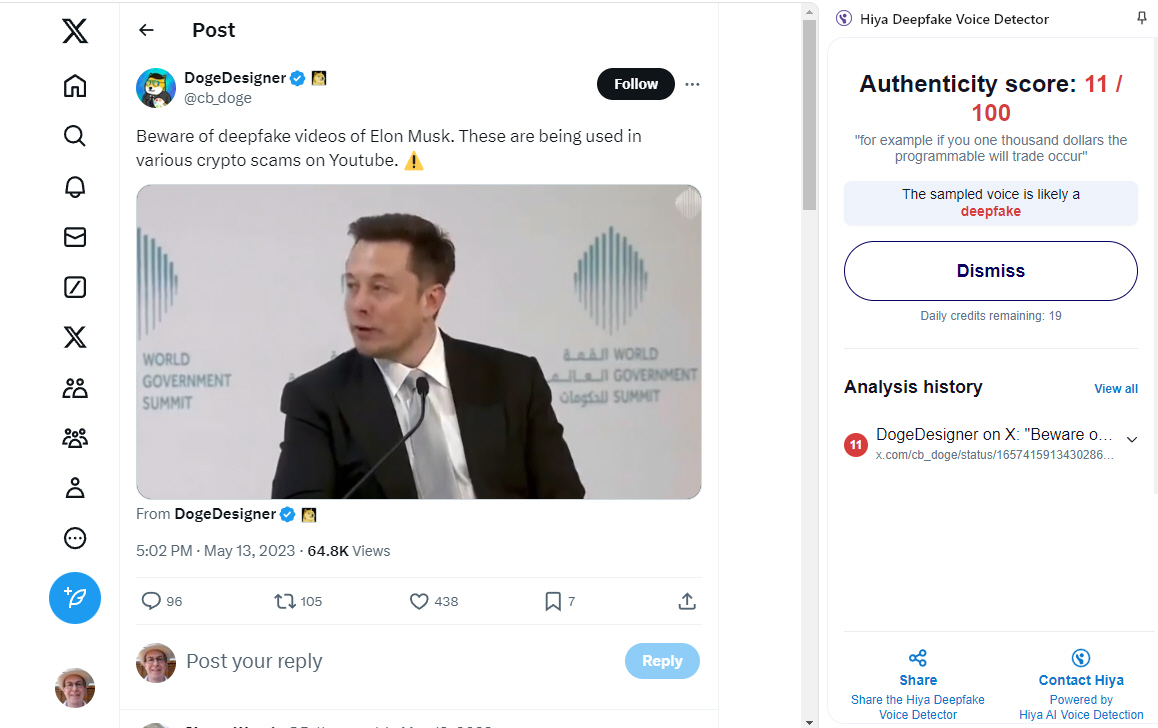
New Chrome extension helps spot deepfakes
Deepfakes are becoming more of a problem and particularly around election times they can seek to influence voters views. They're also getting better so it can be hard to know if what you're watching or hearing is real or fake.
To combat this issue voice security company Hiya has launched a new plugin for the Chrome browser designed to identify video and audio deepfakes with up to 99 percent accuracy, by simply analyzing a few seconds of audio/voice.

Business overconfident and underprepared for cyber threats
A new report from digital transformation consultancy Gemserv, based on a survey of CISOs at 200 large UK and EU enterprises, finds most believe boards are overconfident of their understanding of cybersecurity issues, and are failing to provide CISOs with the support they need to properly protect the organization.
According to the findings, 88 percent of CISOs think the threat landscape is becoming more complex, with 37 percent not confident they have the resources they need. 44 percent struggle to recruit and retain the skilled people they need, amid a 3.2m 'workforce gap' for IT talent.

Winamp source code vanishes from GitHub
Winamp was a beloved media player for tech fans of a certain age, and there was much excitement when the software was made open source. At least it was sort of open source; restrictions on use were such that many people questioned the validity of labelling it as such when it appeared on GitHub less than a month ago.
But all of a sudden the source code is no longer available. Llama Group has now deleted the GitHub repository where the code had been published and, while there has been no official announcement made, there is speculation that the deletion came because of licensing issues with bundled codecs.

Samsung unveils industry’s first 24Gb GDDR7 DRAM for AI and advanced computing
Samsung has introduced the first-ever 24Gb GDDR7 DRAM, designed to offer high capacity and speeds exceeding 40Gbps. This new memory aims to support a range of applications, including AI computing, data centers, gaming consoles, and autonomous driving technologies.
Validation of the GDDR7 with major GPU customers is set to begin this year, with production expected to start early next year. Samsung’s use of three-level Pulse-Amplitude Modulation (PAM3) signaling contributes to a 25 percent speed improvement over previous versions, and the memory’s performance can reach up to 42.5Gbps in ideal conditions.

TCL LINKPORT IK511 brings 5G RedCap connectivity to T-Mobile
TCL has introduced its new 5G connectivity device, the LINKPORT IK511, created in partnership with T-Mobile. The device allows laptops and tablets to connect to T-Mobile’s 5G standalone (SA) network, utilizing 5G RedCap technology, which offers a more secure and reliable connection than traditional Wi-Fi and 4G LTE. The TCL LINKPORT IK511 is powered by Qualcomm’s Snapdragon X35 5G Modem-RF system.
5G RedCap, also known as Reduced Capability, provides a more affordable entry into 5G networks. The TCL LINKPORT IK511 is the first 5G RedCap device available commercially in North America and works exclusively on T-Mobile’s 5G SA network, which is the only nationwide 5G SA network in the United States.
