
More than half of retailers pay up when hit by ransomware
New research from Sophos into ransomware in the retail industry shows that among organizations that had data encrypted, 58 percent paid the ransom to get their data back -- the second highest payment rate in five years.
The survey, of 361 retail IT and cybersecurity leaders across 16 countries, also finds that 46 percent of attacks began with an unknown security gap, while 30 percent exploited known vulnerabilities. 58 percent of victims with encrypted data paid, however, only 48 percent of attacks resulted in encryption. The median ransom demand doubled to $2 million from 2024 and average payment increased five percent to $1 million.
Ashampoo Backup Pro 27 adds streamlined interface and faster cloud backups
Ashampoo has released Backup Pro 27, an updated version of its backup software designed to help prevent data loss caused by drive failure, malware, or accidental deletion.
Aimed at both home and small business users, the new Ashampoo Backup Pro 27 improves how users create and manage backup plans, and offers faster performance and better support for modern Windows features.

Businesses at risk from boom in IoT devices
New research from Forescout Vedere Labs reveals that 65 percent of devices across organizations are no longer traditional IT. Of these 11 percent are network equipment, while 24 percent are part of the extended IoT, such as IoT, OT and IoMT.
Financial services (54 percent), healthcare (45 percent) and oil, gas and mining (40 percent) are the sectors that have the highest percentages of non-IT devices.

Freepik launches Freepik Spaces to power real time AI visual creation and collaboration
Freepik has introduced Freepik Spaces, a new product within its AI Creative Suite to allow creative teams to design, automate, and collaborate on visual projects in real time. The platform uses a node-based interface that brings the entire creative process onto one shared canvas, so teams can move from concept to campaign within a single environment.
Freepik Spaces is targeting creative directors, advertisers, marketers, filmmakers, innovation leads, and other professionals who work across visual media. Users can connect multiple AI tools and workflows within the same space, doing away with the need to switch between separate applications. The goal is to streamline production and make collaboration easier for distributed teams.

Human error is one of the biggest enterprise email risks
It’s known as an ‘ohno-second’ that moment in time when you realize you’ve clicked send on something you shouldn’t have. But it’s no laughing matter, a new survey of more than 300 security and IT professionals from Abnormal AI highlights the growing threat and business impact of legitimate email messages sent to the wrong recipient.
These misdirected emails can result in data breaches, regulatory violations, remediation costs, and reputational damage. The research shows 98 percent percent of security leaders consider misdirected email as a significant risk when compared to other data loss risks like malware and insider threats.

Trust in AI grows but implementation is slow
New research finds that business trust in autonomous AI is growing, with 57 percent of organizations saying they’re ‘very confident’ in the technology’s reliability in core business processes.
Yet, despite this increasing trust, implementation is lagging. The survey from Insight Enterprises shows that six in 10 organizations are stuck in pilot or experimental phases. Most are deploying AI in low-risk, narrowly defined areas, with only 24 percent using it in production for clearly scoped use cases.
Google Chrome can now fill in passport and driving license details and more
Google has, over the years, added a lot of time-saving features to Chrome. Chief among these are the autofill features which can make light work of filling in forms by automatically entering frequently used snippets of data such as names and addresses.
When it comes to shopping, Chrome can also enter your credit card details for you, so you do not have to keep tracking down the physical card. Now Google has announced new time-saving functions.

Google Translate is giving users a speed vs accuracy option thanks to Gemini
For business travelers, holidaymakers and many other people, Google Translate is an essential tool. Making it possible to understand and be understood in other countries and other languages, Google Translate is now gaining a new AI-powered feature.
You would imagine that when it comes to translating text between languages, accuracy would be what most people – if not everyone – would be most interested in. But with the latest Gemini-focused update, Google is giving users the option to choose between a fast translation and a more accurate one.
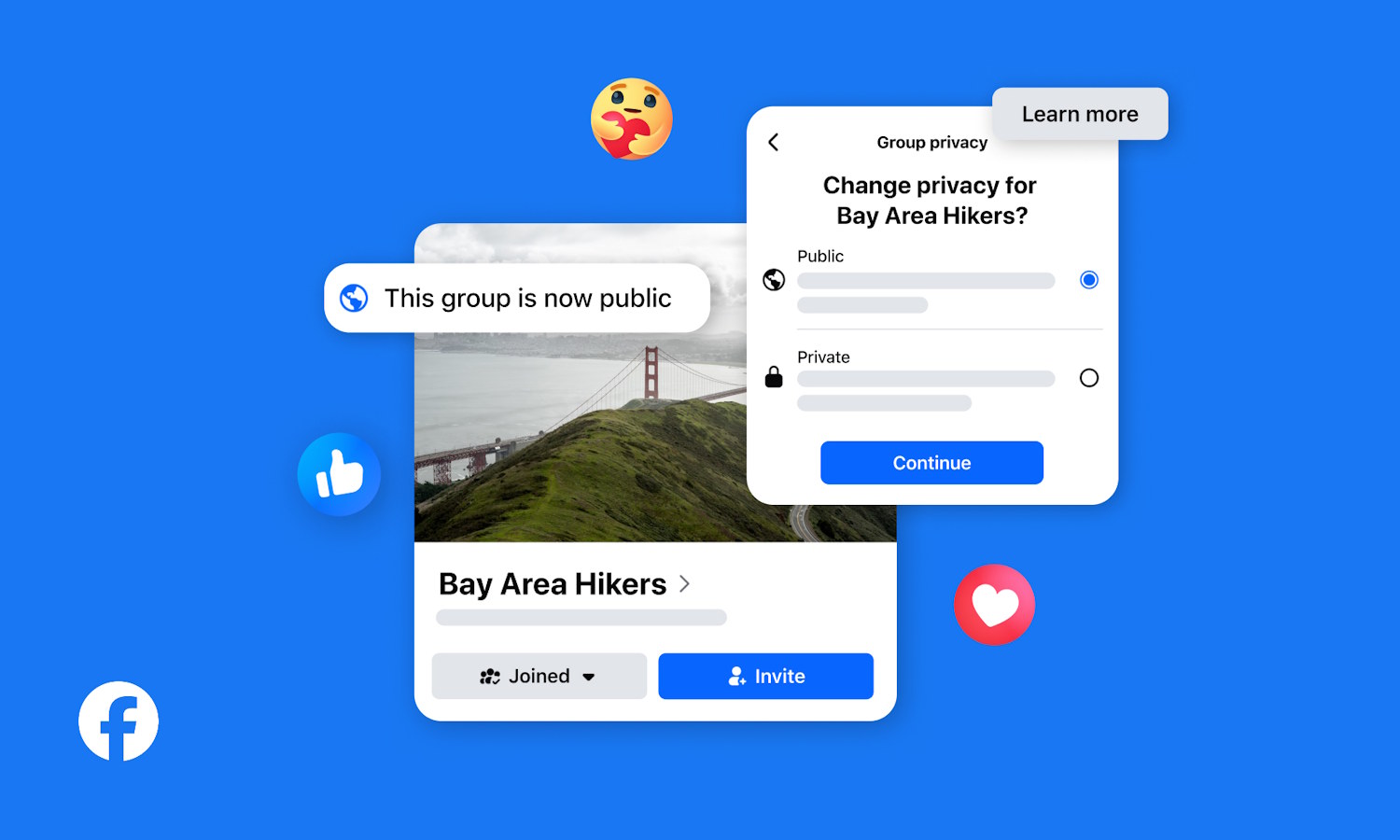
Facebook Group admins are gaining the option to switch group visibility from private to public
If you are in a Facebook Group which is private, you might want to keep an eye on things. Meta has just announced that Group administrators will be getting a new option that will enable them to change their group from private to public.
While Meta is promoting this as a way for group admins to “grow their communities”, there will be obvious privacy concerns for people who joined particular groups precisely because they were private. Meta believes, however, that it has things in control, insisting that member privacy can be maintained even if the switch from private to public is made.
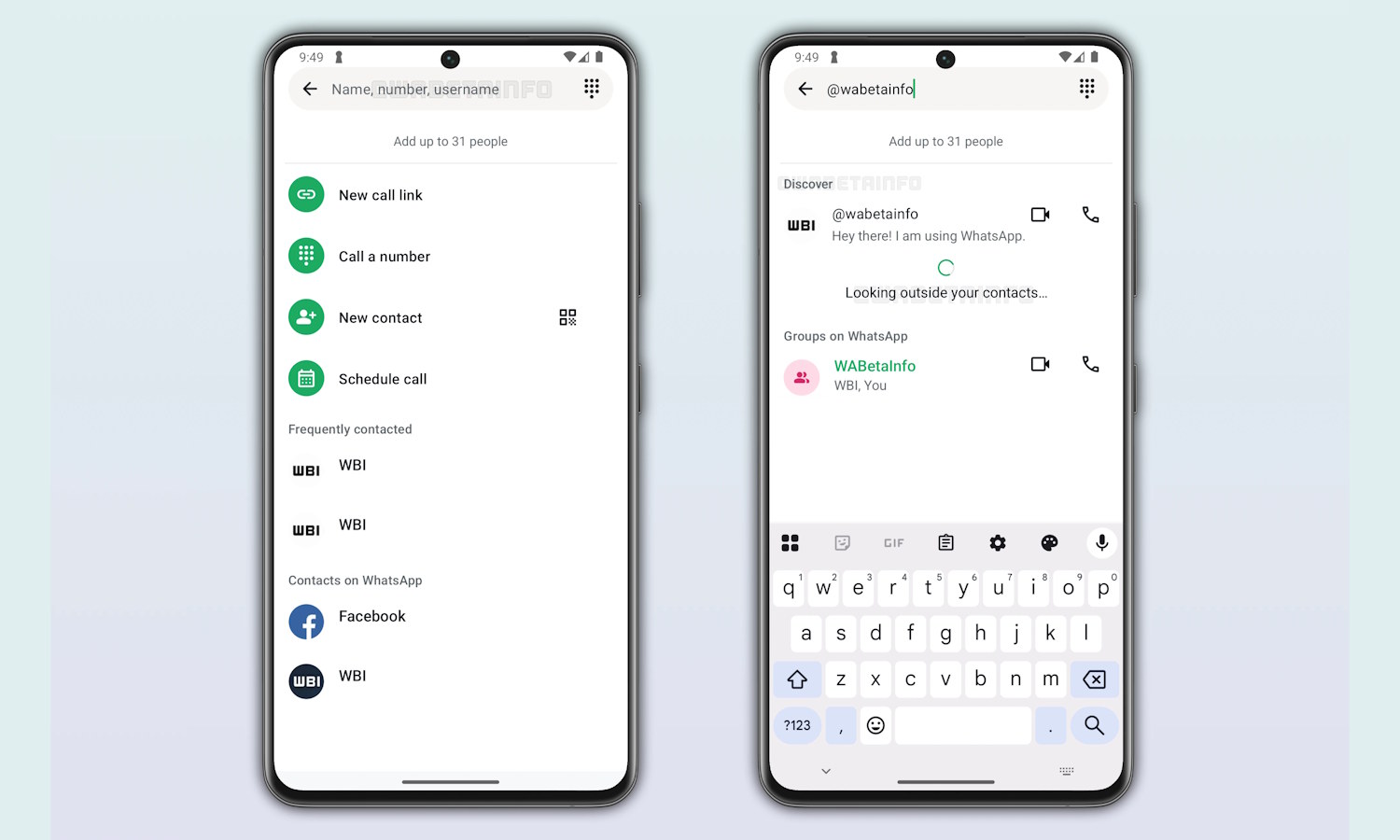
Latest beta release shows more of how WhatsApp usernames will work
WhatsApp has been working on a username feature for what feels like forever, with information gradually slipping out about how this much-requested option will work. There are various reasons for wanting usernames, not least of which is that it just makes sense because it is how just about every other social networking or messaging platform works.
We have already heard from Meta that it believes usernames will help to improve security, and now the latest beta version of the Android app shows us more. Specifically, this latest release shows us how it will be possible to search by username and place calls without the need to know someone’s phone number.

CrowdStrike report shows ransomware surging across Europe
European organizations are encountering ransomware at a record pace, according to CrowdStrike’s 2025 European Threat Landscape Report. The new study found that Europe accounted for nearly 22 percent of global ransomware and extortion victims, second only to the US.
With attacks taking just 24 hours on average, the report shows a worryingly aggressive and complex threat for businesses and governments across the region.

Agentic AI set to reach mass adoption in 2026
A new survey of global technology leaders across Brazil, China, India, Japan, the UK and US suggests that agentic AI will reach mass or near-mass adoption by consumers in 2026.
The study by IEEE shows top uses are likely to be personal assistant/scheduler/family calendar manager (52 percent), data privacy manager (45 percent), health monitor (41 percent), errand and chore automator (41 percent) and news and information curator (36 percent).

Durabook launches AI-powered R10 Copilot+ PC rugged tablet for field professionals
Durabook has announced the R10 Copilot+ PC 10-inch fully rugged tablet powered by Intel’s Core Ultra 200V series processor. Designed for harsh and demanding environments, the R10 combines high performance, AI-driven capabilities, and durability.
The R10 is one of the first available Copilot+ PC rugged tablets, adding new AI features while maintaining Durabook’s focus on field-ready resilience. The tablet can be used as a 2-in-1 device when connected to a detachable backlit keyboard.
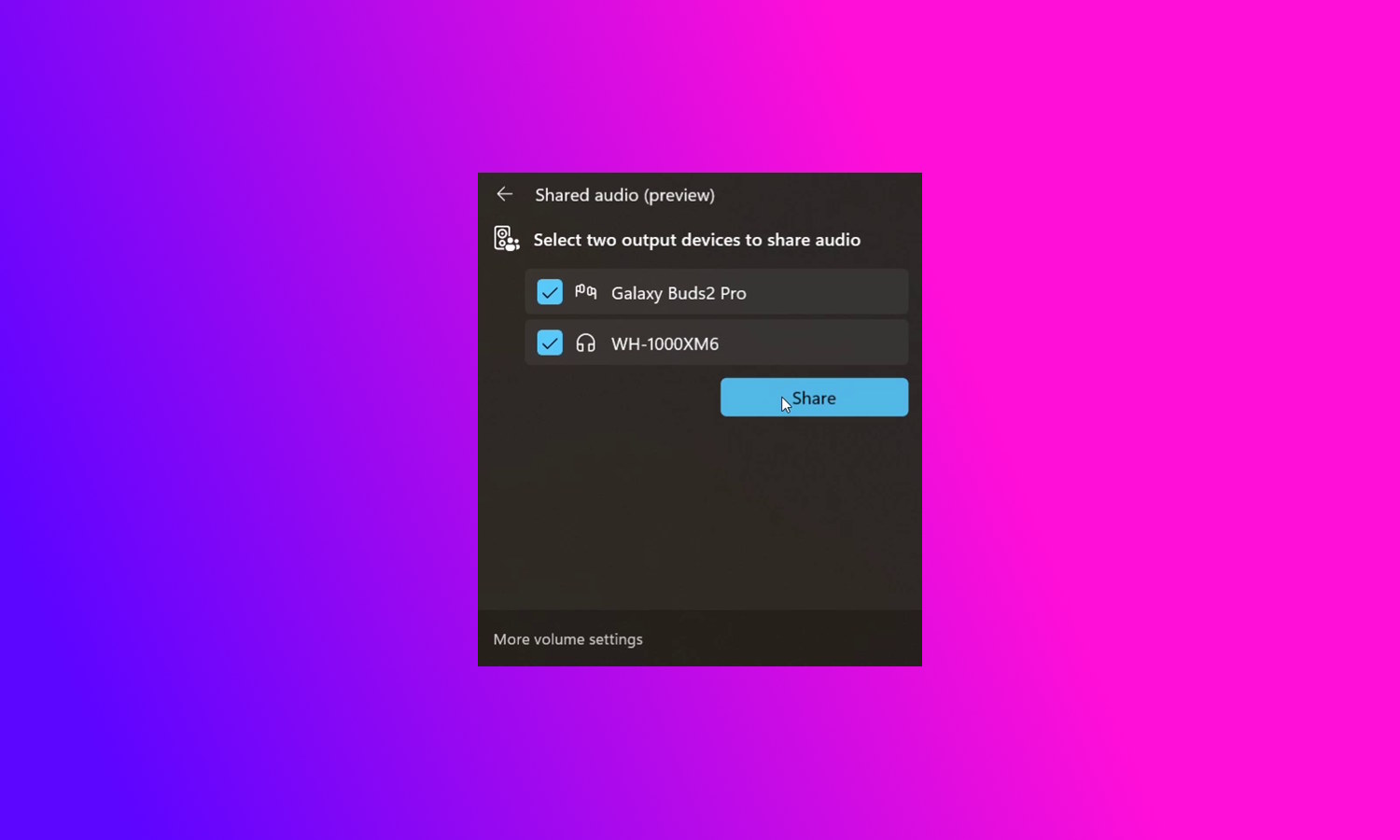
Microsoft makes shared audio Bluetooth feature available to more Windows 11 users
After a period of testing with a limited number of users, Microsoft is finally making a key component of Bluetooth LE Audio available to more people. What does this mean? That you can send audio from your Windows 11 computer to two audio devices at the same time.
This can be used to transmit music or other audio to two sets of speakers, or it could be used to allow to people to listen to the same thing on individual pairs of earphones. While the rollout of this feature remains a little limited in availability, it marks an important step towards general release.

When APIs become the enterprise backdoor -- securing AI’s most vulnerable link [Q&A]
APIs were once treated as behind-the-scenes connectors. Today, they are the enterprise nervous system, linking cloud workloads, data platforms, SaaS tools, and increasingly, autonomous AI agents. This centrality makes them irresistible targets.
According to multiple industry reports, API-related vulnerabilities are among the fastest-growing classes of security incidents. The problem isn’t just exposure; it’s amplification. A single unprotected API can open the door to everything it touches, from sensitive customer records to critical operational systems.
