As device fingerprinting becomes more challenging new risk signals emerge
At Incognia, we speak with experts in the fields of risk, trust & safety, security, and data science every day, and in almost every one of these conversations, one or all of these recurring themes are mentioned:
1) Fraudsters and scammers are innovating at an accelerated pace, 2) Fraud detection technologies that were once extremely reliable have become less effective, specifically device fingerprinting, 3) Evaluating new risk signals is critical in an effort to continuously stay ahead of the fraudsters and scammers.

Why agentless security is not real security
Many security professionals have been misled into believing in the overhyped promise of agentless security. But it looks like the long-lasting 'agentless vs. agent' debate is finally over and the result is finally in -- if you want great cloud workload security, you need an agent.
This noteworthy outcome arose when two of the leading agentless-only vendors finally gave in and announced partnerships with agent-based runtime security and CWPP (cloud workload protection platform) vendors. This is big news, because both of these companies had previously, and persistently proclaimed, that agents are 'old school' and that 'agent-based security is dead'.

New product helps find threats hidden in graymail
'Graymail' refers to those emails that aren't quite spam but which aren't necessarily all that helpful either. Think things like newsletters, announcements, or advertisements that you may have opted into in the past but which have outlived their usefulness.
It presents a headache for security teams as it can be hard to distinguish from malicious content like reconnaissance attacks. Armorblox is launching a new product aimed at cutting the time security teams spend managing graymail and mitigating the security risks from malicious recon attacks.

The persistent accountant shortage sees firms struggling and SMBs turning to software as a savior
Within the last two years, droves of accountants and auditors across the U.S. have exited the financial field, severely limiting the services and expertise that accounting firms provide many small and midsize businesses (SMBs).
Unfortunately, America’s accountant shortage shows no signs of stopping, and many SMBs continue to face significant challenges when partnering with outside accounting firms. In fact, according to Capterra's Accounting Shortage Survey, 64 percent of SMBs are struggling to find outside firms that can handle their accounting and finance needs.

Vulnerability management made harder by complex supply chains
New research reveals that CISOs are finding it increasingly difficult to keep their software secure as hybrid and multicloud environments become more complex, and teams continue to rely on manual processes that make it easier for vulnerabilities to slip into production.
The study from Dynatrace shows 68 percent of CISOs say vulnerability management is more difficult because the complexity of their software supply chain and cloud ecosystem has increased.
Ubuntu 23.04 Lunar Lobster makes for easier enterprise deployment
From today, Ubuntu 23.04 (Lunar Lobster) will be available for download, publisher Canonical has announced. The release marks a significant step forward for enterprise deployment and customization.
A unified Ubuntu server and desktop installation engine, Subiquity, supports the same autoinstall configuration workflows for both desktops and servers, making life easier for admins. The Ubuntu 23.04 installer has a refreshed user interface with a modern but familiar first-time user experience, along with new enterprise management capabilities.

Number of ransomware victims increases by 25 percent
A new report based on publicly available resources finds a 25 percent increase in ransomware victims from Q4 2022 and a 27 percent increase compared to Q1 of the same year.
The study from GuidePoint Security's Research and Intelligence Team (GRIT) tracked 849 total publicly posted ransomware victims claimed by 29 different threat groups in the first quarter of this year.

Twitter quietly updates Hateful Conduct policy to remove protections for transgender users
Twitter has undergone some huge changes since Elon Musk took over at the social media platform, many of which have been very public. But others, like a recent update to its Hateful Content policy, have been quietly slipped out without announcement.
The policy change sees Twitter removing sections that specifically protected transgender users. This means that a long-standing ban on the purposeful deadnaming or misgendering of trans users has been lifted, leading to condemnation from LGBTQIA+ groups and angering the trans community.

Windows 11 Build 23440 lets you hide the date and time in the system tray
Microsoft today rolled out a new Windows 11 build to Insiders in the Canary Channel that brings Content Adaptive Brightness Control (CABC) to plugged in devices.
Insiders on the Dev Channel aren’t missing out though, as Windows 11 Build 23440 arrives today, with a decent amount of new features and fixes for testers in that channel.
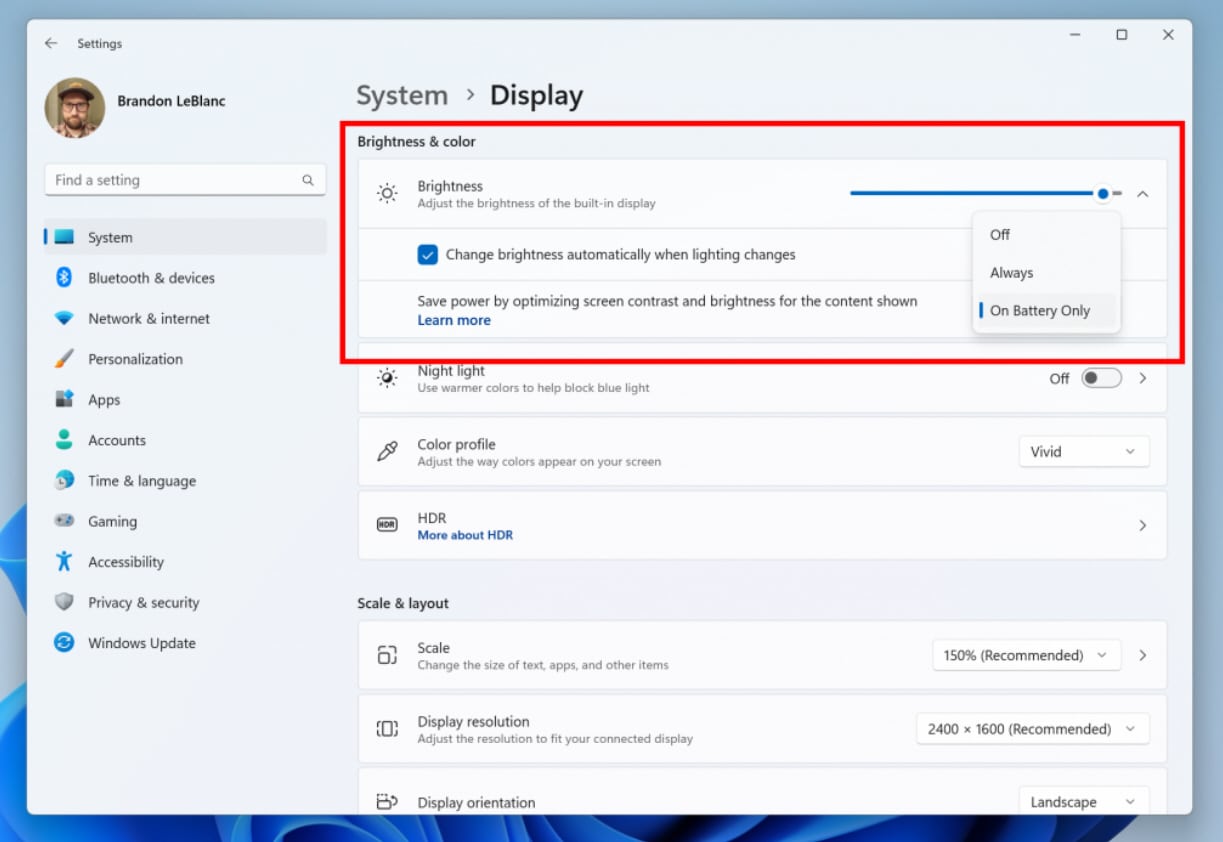
Experimental Windows 11 build brings Content Adaptive Brightness Control (CABC) to plugged in devices
Two weeks ago, Microsoft released a Windows 11 build to the Dev Channel which came with Content Adaptive Brightness Control (CABC) -- an energy-saving feature that works by dimming areas of the screen depending on the content that is being viewed. It was supposed to be something that would benefit all, including desktop users.
Shortly afterwards, Microsoft backtracked, and said the feature wouldn’t be available to desktops after all. From today, Canary Channel Build 25346 introduces CABC support for laptops and 2-in-1’s that are plugged into a charger.

Get 'Cybersecurity and Privacy Law Handbook' (worth $41.99) for FREE
Cybercriminals are incessantly coming up with new ways to compromise online systems and wreak havoc, creating an ever-growing need for cybersecurity practitioners in every organization across the globe who understand international security standards, such as the ISO27k family of standards.
If you’re looking to ensure that your company's data conforms to these standards, Cybersecurity and Privacy Law Handbook has got you covered.

Record number of software security flaws uncovered in 2022
A record 26,448 software security flaws were reported by CISA last year, with the number of critical vulnerabilities (CVEs) up 59 percent from 2021 at 4,135.
The 2023 Annual Threat Intelligence Report, from the Deepwatch Adversary Tactics and Intelligence (ATI) team, also shows that the conflict between Ukraine and Russia has unleashed a flurry of amateur and state-sponsored attacks and breaches on organizations and critical infrastructure.

Microsoft and Talon launch enterprise-grade ChatGPT
Enterprise browser specialist Talon Cyber Security has announced that it has integrated its secure enterprise browser with the Microsoft Azure OpenAI Service to provide enterprise-grade ChatGPT access to customers.
This allows organizations to maintain data protection, keeping data put into ChatGPT within their perimeter and preventing it from transferring to third-party services. When using ChatGPT in Azure OpenAI Service, the organization uses its own Azure resources, so sensitive data is not delivered to other locations, improving data security and reducing risk.

New tool makes it easier to manage machine identities
Thanks to increased cloud and container use there's a growing demand for machine identities, but delivering and managing those identities can present problems.
Machine ID specialist Venafi is launching a new tool called Firefly that enables security teams to easily and securely meet developer-driven machine identity management requirements for cloud native workloads by issuing machine identities, such as TLS and SPIFFE, locally and quickly across any environment.

Misconfigurations leave internet-facing servers open to attack
Issues with server configuration remain a major problem. Researchers at Censys have identified over 8,000 hosts on the internet misconfigured to expose open directories.
These directories contain potentially sensitive data, such as database information, backup files, passwords, Excel worksheets, environment variables, and even some SSL and SSH private keys. Exposure of these types of data in such an accessible manner can offer threat actors an easy way into an organization's network.
