Google researchers reveal flaws in Safari that could be exploited to track users
Apple's Safari web browser was found to have multiple security flaws that allowed for user's online activity to be tracked, say Google researchers.
In a yet-to-be-published paper, the researchers reveal issues in a Safari feature which is actually supposed to increase user privacy. The Intelligent Tracking Prevention (ITP) feature found in the iOS, iPadOS and macOS version of the browser is meant to block tracking, but vulnerabilities mean that third parties could have accessed sensitive information about users' browsing habits.
You can still get Windows 7 updates without paying a penny to Microsoft
It can hardly have escaped your attention that Windows 7 has now reached end of life. For companies and enterprise customers unwilling to pay for Extended Security Updates, this means there will be no more updates. The average home user who has decided to stick with Windows 7 has been completely abandoned by Microsoft, leaving them with an operating system that could be found to contain an endless number of security vulnerabilities.
But, actually, there is another option for home users, and it does not involve paying any money to Microsoft. We're talking micropatches. Specifically, we're talking about micropatches from 0patch. We've covered the work of this company in the past, including its recent fix for the Internet Explorer vulnerability.

BenQ TK850 4K UHD HDR-PRO DLP projector is ready for Super Bowl LIV
Super Bowl LIV is a little more than a week away, airing on February 2 -- a Sunday, of course. If you are planning on watching the game at home, I hope your television is up to the task. True, no one needs a fancy TV to watch football, but having a quality picture definitely makes the big game more enjoyable.
But what if you didn't watch the Super Bowl on a TV? No, I don't mean actually going to the stadium and being a spectator -- tickets are insanely expensive. Actually, I am proposing a different alternative -- watching Super Bowl LIV with a projector. You see, BenQ has a new model that is hitting stores just in time for the "big game." Called "TK850," the DLP projector offers some impressive features, such as 4K resolution and HDR-PRO. It will put some televisions to shame. BenQ says the video the TK850 outputs will look great even in a very bright room -- a bold claim.
0patch releases micropatch for Internet Explorer vulnerability -- including for Windows 7
At the end of last week, a serious vulnerability was discovered in Internet Explorer, affecting all versions of Windows. Not only is the bug (CVE-2020-0674) being actively exploited, but for Windows 7 users the vulnerability was exposed right after their operating system reached the end of its life.
Even for users of newer versions of Windows, and despite the severity of the security flaw, Microsoft said it would not be releasing a patch until February. Stepping in to plug the gap comes 0patch with a free micropatch for all versions of Windows affected by the vulnerability.

Microsoft exposed 250 million customer service and support records in massive privacy blunder
A new report reveals how Microsoft exposed nearly 250 million Customer Service and Support records online late last year.
The security research team at Comparitech discovered five servers, each of which contained the same 250 million logs of conversations with Microsoft support agents and customers. The records, which spanned 2005 to December 2019, were accessible to anyone with internet access; no password protection or encryption was used.
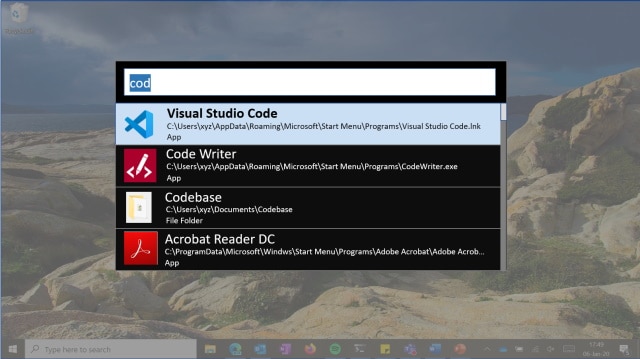
Microsoft has a new PowerToy utility on the way -- PowerLauncher
Over the last nine months Microsoft has been drip-feeding us new PowerToys for Windows 10. So far we've seen FancyZones, Shortcut Guide and PowerRename, and now the company is preparing to add another one.
PowerLauncher is -- or will be -- a quick launch tool for launching apps, and it's aimed at power users. Not only is it open source like the rest of the PowerToy collection, there is the promise that it will be extendible through the use of plugins.

Windows 7 desktops are turning black
Anyone who has decided to stick with Windows 7 now that the operating system has reached end of support has probably seen the full-screen warning advising them that it's time to upgrade to Windows 10. But while this warning was known about in advance, some Windows 7 hold-outs are now reporting something peculiar post January 14 -- a black desktop.
On the last day of support for Windows 7 Microsoft issued one final update, and it seems that this update has been causing problems with desktop wallpapers.

Wine 5.0 launches with multi-monitor support, application fixes and gaming improvements
When it comes to running Windows applications and games on Linux and macOS, Wine is the go-to tool for many people. Now Wine 5.0 has been released and it includes significant changes that make it even more useful.
After a series of betas and release candidates, the stable version of Wine 5.0 is here. It features multi-monitor support, numerous fixes for problematic games and applications, Vulkan 1.1 support, and more.

Chromebooks get 8 years of updates, and Microsoft's Windows 10 is the big loser
Many people publicly deride Chromebooks, but that is largely because of their ignorance. For instance, some will say the computers are nothing more than a "glorified web browser." Actually, Chromebooks run a secure Linux distribution called "Chrome OS." While the operating system does focus heavily on the web, that really isn't a problem nowadays. Since Wi-Fi is ubiquitous these days, doing all of your computing on the web is actually ideal. Who the heck isn't constantly connected to the internet anyway?
But OK, if you have a need for offline computing, that is totally possible too. Not to mention, Chromebooks can now run both Android apps and traditional Linux desktop programs -- there is a huge library of useful software just waiting to be installed.

Happy 20th birthday, SD card!
Back in the day, when you bought, say, a digital camera, there were different storage card types used by various manufacturers. For example, Sony had its own Memory Stick, while Olympus used xD cards. For consumers, this was a nightmare, as it meant changing the brand of your camera or other device could mean your memory cards would no longer work.
Thankfully, as time marched on the computer industry largely rallied around the SD (Secure Digital) card and micro SD card, which have essentially become the standards we all know and love. Believe it or not, the first-ever SD card was sold 20 years ago! Can you guess how much data it held? A laughable (by today's standards, at least) 8MB. Nowadays, you can score a 1TB SD card (1,000,000MB) without breaking the bank. This 1TB Lexar model, for instance can be had for less than $300.
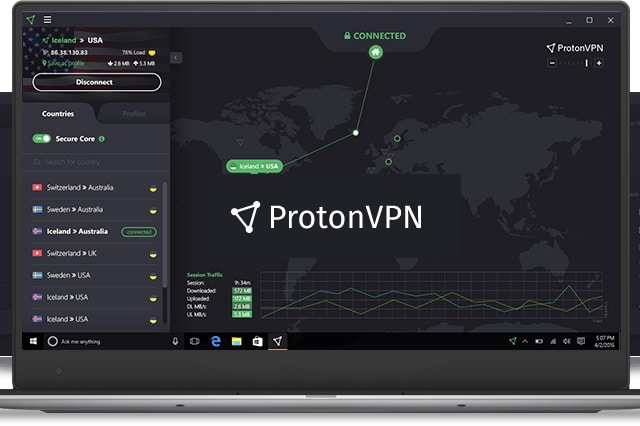
ProtonVPN goes open source to build trust
Proton Technologies has announced that it is open sourcing its VPN tool, ProtonVPN.
The Swiss firm says that not only is it releasing the source code for its VPN tool on all platforms, but also that it has conducted an independent security audit. Created by CERN scientists, ProtonVPN has amassed millions of users since it launched in 2017 and the decision to open source the tool gives users and security exports the opportunity to analyze the tool very closely.

Plugable launches affordable 512GB variant of its excellent Thunderbolt 3 NVMe SSD
If you own a Thunderbolt 3 computer, and you have a need for external storage, I highly recommend you buy a TB3 solid state drive. The speed provided by a Thunderbolt 3 NVMe SSD is simply amazing -- it puts a USB hard disk drive or external SATA SSD to shame.
Aren't sure which model to buy? You should check out our review of the Plugable Thunderbolt 3 NVMe SSD here. The drive is fast, well-built, and very attractive. The problem? It is a bit expensive -- although worth every penny (if you can afford it). For instance, the 1TB variant costs $299, while the 2TB model is $499. If you don't need that much capacity, and would rather save some money, I have some good news. Starting today, Plugable is launching a 512GB version of its popular drive that costs less than the two aforementioned models.
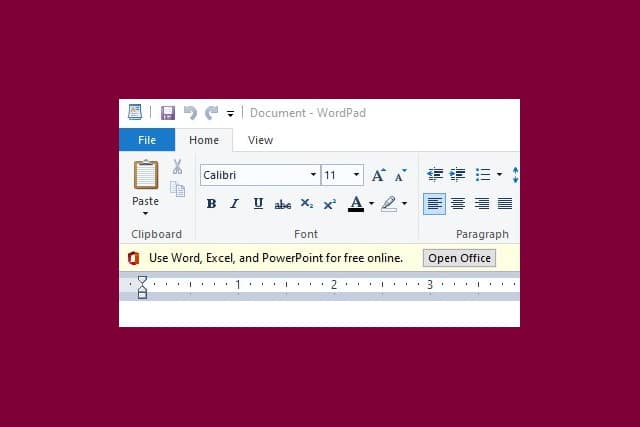
Microsoft is testing ads in WordPad in Windows 10
Over the years Microsoft has taken numerous controversial decisions with Windows 10, including installing sponsored apps, using the Start menu to advertise apps it thinks you might be interested in, and -- of course -- the various forms of data-collecting telemetry.
Now it has been discovered that more ads could be on their way. A Windows researcher has uncovered ads in WordPad encouraging people to try out Word, Excel and PowerPoint online.

You can buy the official Kubuntu 'Focus' Linux laptop now
Ubuntu is one of the most popular Linux-based desktop operating systems in the world. Why? Well, it is easy to use, preloaded with useful software, and has one of the best online communities.
Not everyone likes the default GNOME desktop environment, however, so some folks opt for different flavors of Ubuntu, such as Xububtu (which uses Xfce) or Kubuntu (which uses KDE Plasma). Speaking of the latter, today, you can buy an official Kubuntu laptop. Called "Focus". It is an absolutely powerhouse with top specs.

AI -- separating the reality from the hype to deliver better solutions [Q&A]
Artificial intelligence is making its way into more and more areas of our lives. But how much of this is hype and how much is genuine innovation? And can improved AI learning models deliver better commercial solutions?
We spoke to Ben Lamm, CEO of Hypergiant Industries, a company at the cutting edge of solving problems with AI, to find out.
