
deepin 15.10 is here -- download the most beautiful Linux distribution now!
Windows 10 is a functional operating system, but goodness, it is not at all attractive. When I use Microsoft's OS, I don't get feelings of joy or happiness. Windows 10's design is very bland and seemingly uninspired. By comparison, Apple's macOS makes me very happy. And yes, appearance matters -- a good user interface and design can motivate the user and help them to be more creative.
As great as macOS is, there is a Linux distribution that rivals its beauty. Called deepin, this operating system is now based on Debian Stable (previously Debian Unstable), and provides an absolutely drop-dead gorgeous user interface. In fact, I am confident to say it is the most beautiful Linux distro. The newest version, deepin 15.10, is now available for download. It is chock full of bug fixes, and also, many new features. One of the most significant changes is dde-kwin is now the default window manager. Users should experience improved performance as a result.

After launching Screen Time, Apple is interfering with competing third party parental control apps
With iOS 12, Apple introduced Screen Time, a feature that serves as a parental control tool and encourages periods away from the screen. Tim Cook said last year that he thought he used his phone too much (more recently adding, "we don't want people using their phones all the time"), and Screen Time is Apple attempt to muscle in on the countering of "phone addiction".
For those who are concerned about how much they are using their phone, or who are concerned about their children, it seems like a great feature. But for app developers who have spent years crafting tools that offered these options before Apple, the news is not so good. A new report reveals that Apple is interfering with apps that compete with Screen Time, even going as far as de-listing them without warning.
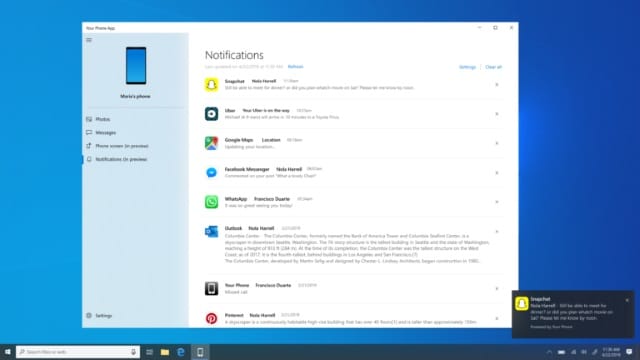
Windows 10 Insider Preview Build 18885 fixes drive letter assignment problems and brings Android notifications mirroring to Your Phone app
Microsoft has released Windows 10 Insider Preview Build 18885 (or Windows 10 20H1, if you prefer) to the Fast Ring. The big addition in this latest build is Android notification mirroring in Windows via the Your Phone app.
If you have an Android 7.0 handset, you can (probably, barring handset-specific compatibility issues) take advantage of the ability to see phone notifications in Windows 10. The range of phones that can use the "phone screen" screen mirroring option has been expanded as well. With Build 18885, Microsoft has also addressed the problem that was preventing people from installing updates when they had a USB drive or SD card connected.

Empowering the channel to make a success of cloud
In the fast-paced world of the IT channel, choosing the right partner can make or break a business. In an ideal world, the partnership delivers a result that’s greater than the sum of its parts -- after all that’s the whole point of the channel. A successful partnership should mean that customers benefit from outstanding technology, service and support, which in turn brings the partners sustained revenues and opportunities to grow sales. So often, however, partner selection is rushed and it’s unclear how the businesses will work to align their expertise and create a genuinely compelling proposition for customers.
Ineffective partnerships are a real threat to success, and that’s why we’re seeing a real push among Cloud Service Providers (CSPs) towards strategies to empower the channel and recognition that the first steps are selecting the right partners, followed by proactive investment in the ongoing relationship.
Best Windows 10 apps this week
Three-hundred-and-thirty-two in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Windows Store in the past seven days.
Lots of news this week: Microsoft Paint lives on, at least for now, Sets may be dead, and admins who upgrade devices to the May 2019 Update should make sure they unplug external USB drives or SD cards before doing so.

New York attorney general to investigate Facebook for scraping 1.5 million users' email contacts
Following the revelation that Facebook "unintentionally" scraped and uploaded 1.5 million users' email contacts, the New York attorney general's office has announced that it is opening an investigation into the social media giant.
Attorney general Letitia James said that it is "time Facebook is held accountable for how it handles consumers' personal information".

Windows 10 May 2019 Update needs more space than ever before
With the release of the May 2019 Update, Windows 10 is becoming more space-hungry than ever. For both the 32- and 64-bit versions of Windows 10 version 1903, Microsoft has increased the minimum storage requirements to 32GB.
For 32-bit users the new requirement is double what it used to be, while for 64-bit users there is a 12GB increase from the previous minimum of 20GB.

iFixit pulls damning Samsung Galaxy Fold teardown
The launch of the Samsung Galaxy Fold has been mired in problems, culminating in the company postponing the foldable phone. In addition to reports of serious screen issues from journalists with review handsets, Samsung was also hit with an iFixit teardown that highlighted numerous design flaws.
Now, following pressure from Samsung, iFixit has removed the teardown -- although the site stresses that it was under no obligation, legal or otherwise, to do so.

Kodi alternative Mobdro steals users' Wi-Fi passwords, seeks to access shared media and installed apps
Mobdro is a streaming app that can be installed on any Android device, including phones, tablets, Amazon's Fire TV Stick, and Google's Chromecast. It has been gaining in popularity for a while now, especially after all the negative press surrounding rival service Kodi.
However, Mobdro is now facing controversy of its own after a new malware report made a number of damning claims about it.

Compulab Airtop3 Linux Mint mini computer has fanless Intel Core i9 9900K and NVIDIA Quadro RTX 4000
The whir of a fan. This is a sound many computer enthusiasts know all too well. Whether it is a single fan in a laptop, or 12 fans in a gaming desktop, the noise can be distracting. While some folks learn to tune out fan noise (and some even end up liking it!), let's be honest, a silent PC is preferable for most. Unfortunately, passively cooled computers are often under-powered, meaning you must decide between performance and silence.
But what if you didn't have to pick? What if I told you a company is selling a mini computer with a passively cooled Intel Core i9 9900K? Yeah, you would probably think I am telling lies, but actually, it is the truth! The Compulab "Airtop3," as it is called, features that high-end processor (plus others) and does not have a fan! In addition, the edge server can be configured with an NVIDIA Quadro RTX 4000 (or GeForce GTX 1660 Ti) and is loaded to the gills with connectivity options. Not to mention, the diminutive computer looks very beautiful too. Best of all, it can be configured to ship with Linux Mint!

Shocking! Apple launches voluntary recall and exchange program for some power adapters
Apple has announced a voluntary recall of some of its AC wall plug adapters and Apple World Travel Adapter Kits over fears that they could cause electric shocks.
While the number of known incidents is low -- Apple says there have been just six worldwide -- there is a risk of the wall plug adapters breaking and causing a shock if touched. The recall relates solely to three-prong wall plug adapters, not USB power adapters. Anyone who has one of the adapters can obtain a replacement free of charge.

Email threats become more focused and malware gets harder to detect
Spam emails containing malware significantly dropped in 2018, to just six percent, down from 26 percent in 2017. But at the same time malware is becoming more sophisticated and harder to detect.
These are among the findings of the latest Global Security Report from Trustwave. The largest single category of malware encountered is downloaders at 13 percent.

Ransomware detections up 200 percent with businesses the main target
The latest quarterly threat research from Malwarebytes for Q1 2019 reveals a 200 percent jump in ransomware and continued increase in business targets for cyberthreats.
This shift back to ransomware comes in the wake of a continued decline in cryptomining, as well as an increased focus on mobile attacks and large-scale business invasions.

Leak shows that the OnePlus 7 Pro is not going to be cheap
While Samsung's problematic Galaxy Fold was vying for attention by not only being a foldable smartphone, but also an extraordinarily expensive one, handsets from OnePlus have been notable for their low price tags.
The launch of the OnePlus 7 series is just around the corner, and the specs we've seen have hinted that this is not going to be a cheap phone. Now leaked pricing appears to confirm this.

Microsoft drops password expiration policies from Windows 10 1903 security baseline
In new draft security baseline documentation, Microsoft has scrapped the policy that requires users to change their passwords on a regular basis.
The new security settings apply to Windows 10 version 1903 and Windows Server version 1903, and the change sees Microsoft conceding that its policy of forcing periodic password changes is "an ancient and obsolete mitigation of very low value". The company has a series of suggestions for how to better improve password security.



