
Fake bank apps found on Google Play store
Cybersecurity company ESET has discovered six fake banking and personal finance apps on the Android store. The apps had been installed more than 1,000 times total before being taken down by Google.
ESET believes all of the apps are the work of a single attacker. They have impersonated six banks from New Zealand, Australia, the United Kingdom, Switzerland and Poland, and the Austrian cryptocurrency exchange Bitpanda.

Sapho brings machine learning to the enterprises
Access to up to date information is essential for businesses, but as data proliferates it's too often the case that people spend time searching for the information they need to do their jobs.
Employee experience portal Sapho is integrating machine learning into its product so that metrics that are typically hard to access, due to complex applications or time-consuming dashboards, will now be delivered directly to employees without needing them to conduct an information search.

Credential stuffing attacks target financial services
A new report from cloud delivery company Akamai reveals that the financial services industry has become a prime target for credential stuffing botnets.
Between May and June 2018, Akamai detected more than 8.3 billion malicious login attempts. However, many botnets attempt to remain in stealth mode for as long as possible.
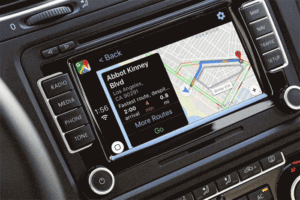
Google Maps 5.0 for iOS offers CarPlay support with iOS 12
Before any trip, I like to research. Where’s the best place to eat, pick up a decent coffee on the way, other interesting points of interest and more.
Google Maps makes this easy. Research online, add a new folder to your places and start saving pointers along your intended route. When you land, simply refer to Google Maps and navigate to your saved locations. Easy. Well, it would if your hire car let you use Google Maps.

Sony copies Nintendo with PlayStation Classic mini gaming console
Sony's original PlayStation is an iconic console, right up there with Atari 2600, Nintendo Entertainment System, and Sega Genesis. The CD-based gaming system was wildly popular, thanks to a fantastic game library and impressive graphics (for the time). Tragically, I never owned one, as I instead opted for the Sega Saturn. Thankfully, I was able to play Sony's console when visiting friends and family, but I digress.
Following the success of Nintendo's mini NES and SNES consoles, Sony is looking to capitalize on the trend with the all-new PlayStation Classic. Just as with Nintendo's offerings, Sony has shrunken the PlayStation to a diminutive state and embedded several games -- you are limited to the included titles.

After Torvalds' apology, the Linux community is adopting a new code of conduct
Following years of questionable behavior and ranting, the grandfather of Linux Linus Torvalds issued an apology and announced his intention to take a break from kernel work. Now the Linux community is adopting a new code of conduct to help make the environment more welcoming.
Based on the Contributor Covenant, the new Code of Conduct seeks to make participating in the community "a harassment-free experience for everyone, regardless of age, body size, disability, ethnicity, sex characteristics, gender identity and expression, level of experience, education, socio-economic status, nationality, personal appearance, race, religion, or sexual identity and orientation".

Chrome OS 69 rolls out with Linux app support and new Material Theme
Google is in the process of rolling out Chrome OS 69 to the stable channel, giving more users the chance to enjoy the new Material Theme and take advantage of new features such as support for Linux apps.
The updated look will be familiar to Android users -- rounded corners abound -- and there are numerous other changes and additions including a new Night Light mode, better dictation options, and an updated Files app.

Microsoft releases Windows 10 October 2018 Update Build 17763 to the Fast ring
Three days ago, Microsoft rolled out Windows 10 Build 17760 to Windows Insiders. This build for the forthcoming October 2018 Update (aka Redstone 5) was the first with "no known issues”, showing how close we're getting to the actual release.
Since then, however, the company has found and fixed a number of additional problems, and encountered a couple more which will be addressed in a subsequent build.

Logitech unveils K600 TV Keyboard
Nowadays, it seems like everyone owns either a smart TV or a media box. They are a great way to consume streaming media, including Netflix, Hulu, and more.
The problem? Searching for content using a remote can be very tedious. Quite frankly, it can be maddening to search for movies, TV shows, and music using an on-screen keyboard. Sure, voice search is a passable alternative, but it’s far from perfect. In an effort to improve both navigation and search on smart TVs and media boxes, Logitech unveils an elegant new product. Called K600 TV Keyboard, it features a full keyboard, trackpad, and d-pad.

Half of adults look for online recommendations rather than ask their partners
More than half of adults worldwide are more likely to consult digital resources than their significant other (SO) for recommendations for products and services according to a new report by cloud database company DataStax.
In the US, 64 percent of adults choose digital resources over their SO, in the UK it's 61 percent, and Germany, 52 percent. The French, however, are still inclined to the offline approach with only 45 percent of adults choosing digital resources over their SO.

Android emulator BlueStacks 4 brings massive performance improvements
The latest version of the popular Android emulator for Windows, BlueStacks 4, is now available, bringing with it a huge performance boost over its predecessor. The new release also sees the emulator jumping from KitKat to Nougat as its base -- specifically Android 7.1.2.
The developers say that BlueStacks 4 is many times faster than the Samsung Galaxy S9+ -- or "any mobile on Earth" according to the blurb -- and features Hyper-G Graphics for unparalleled visuals in games. But besides performance, there are lots of other changes in the latest version of this emulator.

Employees engage in unsafe online behavior despite understanding risks
A survey of more than 400 full-time employees in the US shows that, despite having a general understanding of security risks, people still tend towards unsafe behavior.
The study by Spanning Cloud Apps finds many are under-prepared for the increasing sophistication and instance of ransomware and phishing attacks. More than half (55 percent) admit to clicking links they don't recognize, 59 percent say they would allow a colleague to use their work computer and 34 percent are unable to identify an insecure eCommerce site.

93 percent of execs report positive long-term outlook for mainframes
Far from them being the technology of the past, attitudes towards mainframes are increasingly positive according to a new survey.
The study from IT solutions company BMC finds 93 percent of executives and 92 percent of all respondents view the mainframe as a strong long-term platform -- the highest level in five years.

Enterprises need to adopt 'zero-trust' security posture
Privileged access management specialist Thycotic has released the results of its latest survey, conducted at this year's Black Hat, on hackers' perspectives on vulnerabilities and the attack vectors they find easiest to exploit.
It shows that 50 percent of hackers surveyed -- 70 percent of whom describe themselves as ethical -- say they easily compromised both Windows 10 and Windows 8 within the past year.

Everything removed or deprecated in the Windows 10 October 2018 Update
Microsoft is introducing a number of new features in Windows 10 1809, aka the October 2018 Update, including a dark theme for File Explorer, a new screenshot tool, and clipboard, search, Notepad, and Edge improvements. Sadly what promised to be the big new feature, Sets, hasn't made it into the OS this time around.
With each new Windows 10 update, some existing features get dropped, or stop being actively developed. Here are all the features that have been removed or deprecated in this forthcoming release.



