Most enterprises expect systems to be attacked but there's confusion around responsibilities

A new survey of over 500 security and IT operations leaders worldwide shows that 61 percent believe that data loss within the next 12 months due to increasingly sophisticated attacks is ‘likely’ or ‘very likely’.
The study from Commvault, with research carried out by IDC, reveals that in many cases, senior executives/line-of-business leaders are minimally engaged in their company's cyber preparedness initiatives -- just 33 percent of CEOs or managing directors and 21 percent of other senior leaders are heavily involved.
Almost half of SMBs have experienced a cybersecurity incident in the last year

A new report from business software company Sage shows that 48 percent of SMBs have experienced a cyber security incident in the past year.
In addition the study of over 2,000 SMB decision makers around the world finds 51 percent say keeping on top of new threats is their biggest challenge and 44 percent say economic uncertainty and the cost of living has reduced cybersecurity budgets.
Silicon Power unveils XPOWER XS80 PCIe Gen5 SSD

Silicon Power chose the stage of PAX at the Melbourne Convention and Exhibition Centre (MCEC) to unveil its newest solid state drive. Called “XPOWER XS80,” this PCIe Gen5 SSD marks a significant milestone in high-performance storage solutions tailored for gaming.
Harnessing the power of the latest PCIe Gen5 technology coupled with NVMe 2.0 support, and a 232-layer 3D NAND flash, the XS80 transcends the ordinary, offering a data transfer rate that is twice that of Gen4 and quadruple that of Gen3. This SSD is crafted to meet the demands of modern-day gaming, ensuring that gamers no longer have to compromise on performance.
Microsoft releases experimental Windows 11 Build 25967 with new Settings homepage
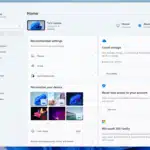
Microsoft continues to add new features to Windows 11, and Windows Insiders in the Canary Channel get to try out some of the more experimental ones.
New in Build 25967, released today, is a redesigned homepage in Settings that offers a "dynamic and personalized experience". Microsoft says it provides an overview of your device, quick access to key settings, and helps manage your Microsoft account.
Exploring how AI-powered chatbots are changing the business world [Q&A]

Thanks to high-profile tools like ChatGPT, we've witnessed AI appearing in more and more areas and projects this year. Next week sees the launch of the latest Chatbot Summit, held at ExCel London on October 11-12, bringing together industry experts to share practical skills, knowledge, and insights.
We spoke with Chatbot Summit 2024 founder and executive chairman, Yoav Barel, to discuss the impact of AI technology and how businesses can prepare, as well as what summit attendees can expect from the event.
Illuminate your Windows 11 experience with Dynamic Lighting

As technology continues to evolve, so do the ways in which we interact with our devices. The integration of "Red, Green, Blue" (RGB) lights within various gadgets has opened up a realm of personalization, allowing users to create unique environments that extend beyond the screen. Microsoft has recognized this trend and with its latest feature update, unleashes the power of Dynamic Lighting on Windows 11.
The Dynamic Lighting feature in Windows 11 embodies a step towards a more unified and interactive user experience. It finally grants users the liberty to control their RGB devices right from the Windows Settings -- something many of us have been waiting for. This means you can now extend your Windows accent color to the devices around you, synchronize RGB effects across devices from different brands, and have finer control over how apps manage your device’s lights.
Attackers exploit inbox rules to avoid detection

New research shows that if an attacker has compromised an email account they can use inbox rules to hide in plain sight while they quietly move information out of your network via your inbox and hide security warnings.
The report from Barracuda reveals techniques including setting a rule to forward to an external address all emails containing sensitive and potentially lucrative key words such as 'payment' or 'confidential' to steal information or money.
Advances in predictive analytics expand organizational data intelligence

When it comes to data analytics, most organizations have historically focused primarily on descriptive and diagnostic capabilities. Descriptive analytics explains what is happening in an IT system and uses analysis levers including analyzing trends, mining patterns, and detecting changes and anomalies. Diagnostic analysis encompasses functions including critical path analysis, bottleneck analysis, fault propagation models, and root-cause analysis to explain why something is happening in the system.
With an increased focus on instrumentation and observability, allied to significant advances in AI, enterprises are now looking beyond simply what happened and why, and seeking to apply advanced intelligence to draw valuable predictive insights from data. IT leaders are looking for insights that can inform them about what is likely to happen in the future and how to prepare for it, for example:
Microsoft releases Windows Subsystem for Linux 2.0.0 with fixes and experimental new features
Microsoft's love for Linux shows no signs of waning, with the company releasing an update-packed pre-release build of WSL 2.0.0.
There are many changes in Windows Subsystem for Linux 2.0.0, and as this is a pre-release version it’s perhaps to be expected that many of the new additions are described as "experimental". One of the biggest new features is experimental.autoMemoryReclaim which shrinks the WSL VM in memory by reclaiming cached memory.
TCL's 2023 Fire TV models will elevate your NFL Football viewing experience

Today we have some exciting news, fellow NFL Football fans. TCL has announced its latest TV models for the U.S. market, boasting the integration of Fire TV in both its QLED Q Class and Smart S Class series. These TVs should provide an excellent viewing experience for watching football.
The integration of Fire TV in their latest lineup offers an enriched user experience, blending a user-friendly interface with access to a plethora of entertainment options - be it streaming services with over 200,000 movies and TV episodes, Amazon Luna cloud gaming, or conventional satellite and cable content.
Making IT sustainability a part of the digital employee experience

Sustainable IT is no longer merely a good practice driven by customer demands; it has evolved into an imperative in response to shifting employee expectations and corporate responsibility around ecological consciousness. In today's digital workplace landscape, more than 80 percent of leaders are placing a heightened emphasis on environmental sustainability. Cloud providers, executives, software engineers, IT teams and even corporate boards of directors are increasingly thinking green because of the impact that adhering to environmental, social and governance (ESG) standards will have on our future and the next generation of leaders. And on top of that, the business landscape is incentivizing green behavior. A recent survey by CloudBolt found that two-thirds of IT leaders say cloud provider’ sustainability initiatives are a key factor in determining with whom they do business.
Companies who drive sustainability transformation also enhance corporate reputation and performance, appealing to environmentally conscious customers. Firms adopting sustainable practices, like energy optimization, realize significant cost reductions. Integrating Sustainable IT into the digital employee experience is also a pivotal element of this transition, fostering a gratifying workplace for employees.
Uncovering the market in vulnerability exploits

It won't come as any surprise that there's a thriving market among threat actors for the latest vulnerability exploits. A new report from Flashpoint lifts the lid on this world and reveals the exact vulnerability exploits that were listed for sale, purchased, and/or traded in the first half of 2023.
One of the most expensive was a remote code execution exploit for Adobe Commerce -- the eCommerce platform formerly known as Magneto -- which was listed for sale at $30,000. A Citrix ShareFile exploit was priced at $25,000.
How to speed up File Explorer in Windows 11

The vast majority of software bugs are, almost by definition, a problem. A bug can cause unexpected behavior, reduce performance, and cause endless other issues. But there is a bug in Windows 11's File Explorer that actually makes it better.
If you've ever thought that File Explorer would benefit from a speed boost, there's some good news. A strange bug can be exploited to noticeably improve performance in a split second.
As the cookie crumbles, ID resolution reignites customer experience

In today's digital world, one customer can have multiple identifiers. These identifiers track customer information, transactions, and interactions as they engage with a business through its web browser, mobile app, and in-store. Each of these touchpoints might capture different data about the customer, creating different identifiers. This can lead to customer data ending up in disconnected silos throughout the organization, impacting the company’s ability to target marketing and advertising efforts.
Without a comprehensive view of a customer's journey, brands struggle to understand consumers’ needs, creating a bad customer experience (CX). In fact, CX quality fell for 19 percent of brands last year, with 49 percent of customers stating they left a brand they had originally been loyal to in the last 12 months due to poor CX. With customer loyalty at stake, it’s more important than ever that brands use identity resolution (ID) resolution to improve CX, increase retention, and drive revenue.
Debian-based antiX-23 (Arditi del Popolo) is the Systemd-free Linux experience of your dreams

If you're one to favor choice, versatility, and independence from the systemd behemoth, then you're in for a treat. Say hello to antiX-23 (Arditi del Popolo), a new release based on Debian Bookworm that stands as a powerful testament to the open-source community's flexibility.
With its myriad flavors and options, this Linux distro invites you to experience computing on your own terms. The new release adds some in-house spices like zzzFM/IceWM as the default desktop and the IceWM Control Centre. Plus, the Onboard virtual keyboard and magnus screen magnifier are now standard.
Recent Headlines
Most Commented Stories
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.