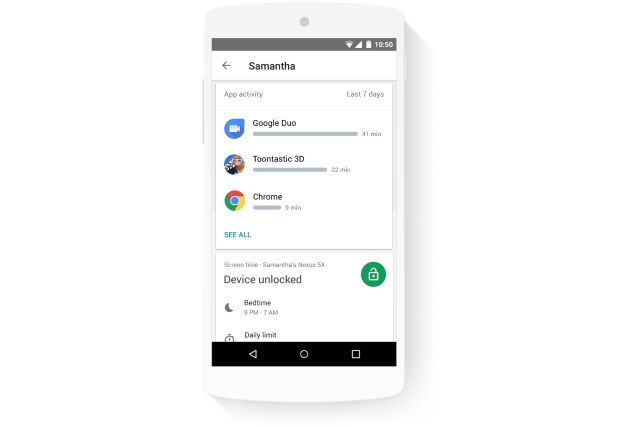
Google launches Family Link parental control solution for Android
After a period of beta testing, Google's new parental control system for Android and iOS -- Family Link -- has been launched to the public. Google says that the feature makes "Android better for kids and families," and it places parents in control of what their kids can do.
The feature is available to everyone in the US without the need for an invite (the beta period was invite-only), and Google describes the tools as being a way to bring kids and their parents into the Android ecosystem. It can be used from an Android phone or an iPhone to control kids' use of an Android device.

PSA: Google quietly discontinues NFC Smart Unlock without explanation
Android users have been slowly discovering that Google has killed off NFC Smart Unlock. The feature, which makes it possible to unlock a phone with an NFC device such as a ring or bracelet, has been discontinued without explanation.
Earlier in the month, Android users started to post messages on Google's Issue Tracker website, indicating that the feature was no longer available to them. Three weeks later, Google has finally responded, indicating that NFC Smart Unlock has been deprecated.

OnePlus 5 is not your typical flagship [Review]
There are few smartphones that attract as much attention as a new OnePlus flagship. And it is easy to understand why. You get pretty much everything that you expect from a flagship device, but at a fraction of the cost. That recipe has not changed with this year's OnePlus 5.
Though it has not changed dramatically on the outside, the new "flagship killer" is more powerful and exciting than ever. It's also more expensive, which brings up an interesting question: Is the OnePlus 5 still special in today's crowded market?

Ex-Googler sets up his own futuristic church and is creating an AI god for you to worship
Anthony Levandowski -- a former Googler famous for building the company's self-driving car -- has set up a non-profit religious corporation called Way of the Future. The founding of the "church" has just been unearthed by Wired through state filings in California.
The purpose of the Way of the Future is to "develop and promote the realization of a Godhead based on artificial intelligence and through understanding and worship of the Godhead contribute to the betterment of society."

Splunk will use machine learning to improve its enterprise solutions
Splunk has revealed plans to boost the power of its enterprise software offerings thanks to the power of machine learning.
Speaking at the opening keynote of the company’s conf2017 event in Washington, Splunk chief product officer Richard Campione highlighted how machine learning could help the company’s customers get even more insight out of their data.

System76 Pop!_OS Beta Ubuntu-based Linux distribution now available to download
Next month, a new era of Ubuntu begins. Unity is dead, and GNOME 3 takes over as the default desktop environment. While this change was for the best, it was still shocking for many. For a company like System76, for instance, that sells computers pre-loaded with Ubuntu, this was problematic. Why? Well, the company essentially lost control of the overall user experience by relying on vanilla Ubuntu. It was being forced to follow Canonical's path.
To solve this, and regain some control, System76 has been developing its own operating system called "Pop!_OS." No, it is not reinventing the wheel here -- it will still use Ubuntu as a base, and GNOME will be the desktop environment. The company is customizing the operating system, however, with things like fonts, themes, and icons, to create something truly unique. This could lead to an improved user experience. Today, the first official beta of the operating system becomes available for download.

Inadequate processes for managing accounts and access create major security risks
Poor management of user accounts is leaving organizations open to security and compliance risks according to a new report.
Identity and access management specialist One Identity surveyed over 900 IT security professionals, in conjunction with Dimensional Research, and finds that what should be security best practices -- such as swift removal of access to corporate data and applications, dormant account identification, and role administration -- continue to be a challenge for many enterprises.

Attackers impersonate bank emails to cash in on post-Equifax fears
In the wake of the recent breach at credit agency Equifax it's only natural that people are keeping a close eye on their bank statements and credit reports.
Of course the bad guys know this too and a new report by Barracuda Networks looks at an email attack that is impersonating a 'secure message' from financial institutions.
Internet Explorer users beware: the address bar is leaking everything you type
A bug has been uncovered in Internet Explorer which makes it possible for websites to view anything that is typed in to the address bar. This means that web addresses and search terms could be accessed by a hacker or malicious website.
The vulnerability was discovered in the very latest version of Internet Explorer, and Microsoft is yet to release a patch for it. Discovered by security researcher Manuel Caballero, the attack can be made completely invisible to a victim.

New DevOps toolkit automates database changes to remove bottlenecks
DevOps is a popular choice with companies looking to streamline software delivery, but it often encounters a road block when changes to databases are needed.
In businesses databases are often historically developed and need to be managed differently due to their complexity and their sometimes sensitive nature. Systems management and security company Quest Software is launching a new toolkit to help organizations automate database changes within their existing DevOps processes.

Apple launches new privacy page and reveals all about Face ID
Apple has launched a revamped privacy page proclaiming that its products are "designed to protect your privacy." Describing privacy as "a fundamental human right," the page explains the privacy functions of apps, Siri, Apple Pay and Touch ID.
The company describes not only how it protects personal data with encryption, but also how it responds to government and legal requests for data. Apple has additionally published a paper which goes into some detail about how the Face ID feature of the iPhone X works -- and reveals its limitations.

Nokia 3310 with 3G coming mid-October
When HMD announced a revamp of the famous Nokia 3310 early this year, one of the first things that stood out was the limited cellular support. The new Nokia 3310 only works on 2G networks.
While that may be fine in some parts of the globe, there are many markets which no longer support anything below 3G. And that means the new 3310 is useless there. HMD has addressed this in a new version of the device.
Firefox 56 unveils improved preferences, paves the way for Firefox Quantum
Mozilla has released Firefox 56, with Firefox for Android 56.0 due imminently. Firefox 56’s chief highlight is the rollout of Firefox Screenshots to all users. The built-in tool for capturing, saving and sharing screenshots from the browser was made available to a subset of users with the previous release.
The announcement comes with news of Firefox 57, which has been billed by Mozilla as "our biggest release of the year." It will unveil portions of a new next-generation browser engine as well as a major design refresh to fit in better with modern operating systems.

IT maturity improves in small and medium sized businesses
A new study by IT management specialist Kaseya looks at IT department practices and for the second year in a row finds a growing level of maturity in SMBs and mid-market companies.
Kaseya uses an IT Management Maturity Model that divides companies into five levels, from the lowest 'Reactive' through 'Efficient', 'Proactive' and 'Aligned' up to the highest 'Strategic'.

Mark Zuckerberg denies Facebook is anti-Trump
Yesterday, Donald Trump used his favorite medium of Twitter to complain that -- as well as some media outlets -- Facebook was opposed to him. Mark Zuckerberg has now responded, speaking out to deny the claim.
He said: "Trump says Facebook is against him. Liberals say we helped Trump. Both sides are upset about ideas and content they don't like. That's what running a platform for all ideas looks like." The Facebook founder also backtracked on his earlier dismissal of the social network's influence on the election as "crazy."



