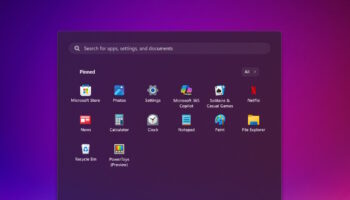
How to run Microsoft Copilot on older versions of Windows -- including XP, Windows 7, and Vista

While some Windows 11 users might prefer not to have Copilot included in Microsoft's latest operating system, there are also those using older, unsupported versions of Windows who would like to try the tech giant's AI assistant, if only to see what all the fuss is about.
Although Microsoft doesn’t provide Copilot for the likes of Windows XP, Windows 7, Vista, or Windows 8.1, you can still install and run it yourself.
Ransomware attacks rise over 60 percent

In the last year, the US has experienced a dramatic 63 percent increase in ransomware attacks, with the UK seeing an even greater rise of 67 percent.
The latest State of Ransomware report from Malwarebytes shows the share of attacks carried out by gangs outside the top 15 increased from 25 percent to 31 percent, indicating that ransomware is becoming more accessible to a broader range of cybercriminals.
Test your computer and smartphone's artificial intelligence capabilities with Geekbench AI 1.0
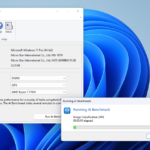
Primate Labs, the Canadian developer behind PC benchmarking tool Geekbench 6, has unveiled a new addition to its benchmarking family: Geekbench AI 1.0.
Available across the big five desktop and mobile platforms, Geekbench AI allows you to benchmark your devices using a series of frameworks to determine their AI capabilities. But why the need to test your own devices? The era of Artificial Intelligence is upon us, as tech companies fall over themselves in their attempts to convince us that computers can genuinely think for themselves. While the truth of AI -- more a case of machine learning than true intelligence -- doesn’t live up to the hype, that doesn’t mean the AI label is completely useless.
The power of knowledge automation in modern workplaces

Today’s corporate world requires significantly more from its employees than in the past. Staying competitive requires more than just keeping pace with industry trends -- it demands a proactive approach to innovation and efficiency.
As employees and organizations navigate this strive-for-efficiency backdrop, one solution has become abundantly clear: knowledge automation. This approach revolutionizes how businesses manage internal processes, particularly in corporate training and employee development.
Accusoft uses IBM AI to automate document tagging

Document processing specialist Accusoft is releasing new Auto Tagging and Classification modules within its PrizmDoc secure document viewer.
The modules use the IBM watsonx data and AI platform with the IBM Granite foundation model to automate manual tagging and classification providing consistency and ensures documents are meticulously organized, easily searchable, and compliant with regulations.
Enhancing availability, even when high availability is not required

Providing high availability (HA) protection for critical applications is a standard IT best practice. However, broader downtime protection best practices -- and options for delivering this protection -- are not as clearly defined. As a result, applications that are not considered mission critical are often left with minimal protection. Yet downtime for these non-mission critical applications can be more than a nuisance. It can impose a costly and disruptive burden on IT teams that must devote time and resources to bringing those applications back online.
Downtime can also be frustrating to end users whose work may be interrupted and put on hold. It may have downstream consequences for customer satisfaction as well.
A technical overview of Cisco IoT part 4: Advancing IoT knowledge -- Cisco Meraki, training resources and certification pathways

This is the fourth piece in the ongoing Cisco IoT technical overview series, following a detailed analysis of security essentials and industrial applications. This installment of the series explores Cisco Meraki, essential IoT skill sets and additional resources to enhance knowledge and expertise in this rapidly evolving field.
The Internet of Things (IoT) is an expanding area of networking with an ever-growing array of use cases. It is significantly impacting organizations across industries, particularly in healthcare and retail. IoT technology enhances operations by providing valuable security, cost-saving benefits, and new capabilities, such as improved inventory management and product innovation.
Over half of enterprises suffer data breaches in non-production environments

A new study shows 91 percent of organizations are concerned about the expanded exposure footprint across non-production environments (including software development, testing, and data analytics).
Once a production dataset is copied many times over into non-production environments, more workers have access to it and the data is no longer subject to the same strict security controls.
How radical transparency paves the way to more effective vulnerability management

Vulnerability management is one of the most painful challenges of cybersecurity. The lack of transparency in our industry isn’t helping matters. Vendors often work behind the curtain to fix the identified security flaws without effective communication or -- if they do communicate -- with significant delays in reporting.
However, there are signs of positive steps toward this much-needed transparency. In July, for example, the Microsoft Security Response Center announced that it will start issuing Common Vulnerabilities and Exposures (CVEs) for critical cloud service vulnerabilities. There have also been moves from legislators to ensure greater rigor in reporting, such as the EU's Cyber Resilience Act, which mandates that manufacturers of all connected and IoT devices report serious cyber incidents and unpatched vulnerabilities. This is essential for building trust among vendors, businesses, and stakeholders alike. Greater resilience starts with a common understanding.
Save $43.99! Get 'The Ultimate Kali Linux Book, Third Edition' for FREE

Embark on an exciting journey into the world of Kali Linux -- the central hub for advanced penetration testing, and harness Nmap, Metasploit, Aircrack-ng, and Empire.
Honing your pentesting skills and exploiting vulnerabilities or conducting advanced penetration tests on wired and wireless enterprise networks, Kali Linux empowers cybersecurity professionals. In its latest third edition, The Ultimate Kali Linux Book goes further to guide you on how to setup your labs and explains breaches using enterprise networks.
Tracing the destructive path of ransomware's evolution

The year is 1989. “Rain Man” wins the Academy Award for Best Picture. Motorola releases the world’s smallest and lightest phone. The Berlin Wall falls. Taylor Swift is born. It also begins the dawn of a new era of cyber extortion.
The AIDS Trojan arrived innocuously, distributed via floppy disk to public health professionals. But it harbored a nasty surprise. After the 90th PC reboot, it cryptographically locked victims’ hard drives, demanding a $189 payment to unlock files. While this attack was thwarted easily, it changed the game. Over the next 30 years, ransomware proliferated from curiosity to a catastrophic threat fueled by an unrelenting arms race between extortionists and security teams.
How the CrowdStrike outage can inform your customer service strategy

When a broken CrowdStrike update crashed Microsoft-run computers around the globe on July 19, affected leaders were faced with millions of blue screens, billions of dollars in losses and countless calls from unhappy customers. In addition to these tangible problems, leaders’ faith in the reliability of critical technological infrastructure was shaken. If a little bit of faulty code could result in a worldwide outage, was all this digital transformation worth it? Analog systems are rife with problems of their own. Still, those types of issues are typically from human error, not a catastrophic system failure. So is it time to accept digital defeat and course correct back to pen and paper basics? Quite the opposite.
The CrowdStrike incident affected almost every industry -- from airlines to banks to tiny tire stores attached to gas stations, business as usual was halted, and as a result, customer service requests skyrocketed across all affected sectors. But many organizations weren’t ready for an unexpected spike in customer service calls.
AI's rapid development is a security disaster waiting to happen

No matter how you look at it, AI is currently booming. The AI market is on track to reach $407 billion by 2027 (compared to $86.9 billion in 2024). Last year, ChatGPT became the fastest-growing consumer application in history when it reached 100 million monthly active users just two months post launch. McKinsey declared 2023 as Generative AI’s breakout year, and a follow-up 2024 survey found that the percentage of organizations using Generative AI jumped from approximately 50 percent to 72 percent from 2023 and 2024. Meanwhile, a culture shift within tech and business has accelerated AI adoption seemingly overnight.
Long before Generative AI entered the scene, tech C-suites were concerned about being left behind. AI’s disruptive potential has only exacerbated this. Companies with the bandwidth to do so are developing their own AI systems or converting existing ones over to AI. Such behavior is motivated primarily by reputation management. No major player wants to look like they were left behind as their competitors innovated to newer heights.
Save $21! Get 'Beginning Programming with Python For Dummies, 3rd Edition' for FREE

Beginning Programming with Python For Dummies is the trusted way to learn the foundations of programming using the Python programming language.
Python is one of the top-ranked languages, and there’s no better way to get started in computer programming than this friendly guide. You’ll learn the basics of coding and the process of creating simple, fun programs right away.
Kodi 21.1 'Omega' has arrived and you should download it now!

Five months ago, the stable version of Kodi 21 'Omega' was released, introducing a wealth of new features to the hugely popular home theater software. Additions include support for FFmpeg 6, DolbyVision on-the-fly profile conversion, and an in-game player viewer.
The Kodi Foundation is now hard at work on Kodi 22 'Piers', with an Alpha release expected soon. It hasn’t forgotten Kodi 21 users however, and a new build for that branch has just been released.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.