
Obama is not going to pardon Edward Snowden -- and Trump certainly won't
Edward Snowden. A liberal darling, and simultaneously a figure of hate. His surveillance leaks are now legendary, and while the NSA whistle-blower hides away in Russia, there are calls for President Obama to issue a pardon before President Trump becomes a reality.
But Obama is having none of it. In an interview with Germany's Der Spiegel, the out-going president was asked bluntly about pardoning the former NSA contractor. His response was: "I can't pardon somebody who hasn't gone before a court and presented themselves". Obama, of course, could pardon Snowden if he wanted, regardless of whether he has faced trial, but he's not going to say that.
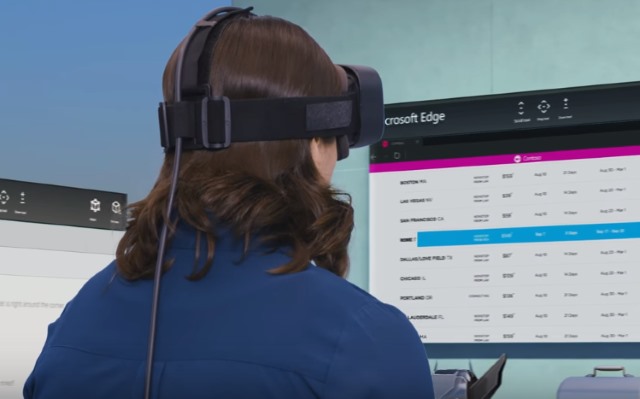
Microsoft reveals minimum specs for Windows Holographic compatibility
As Windows 10 evolves, Microsoft is incorporating a number of different technologies from 3D to mixed reality. The company's own AR/VR platform, Windows Holographic, has headsets like Oculus Rift, and the minimum spec for connected PCs is slowly starting to emerge.
As noted by the Verge, the latest insider builds of Windows 10 include a Windows Holographic First Run app that gives you the chance to test your computer to see if it is compatible with Windows Holographic. The minimum specs are surprisingly low.

Amazon Alexa continues its rollout to Fire tablets
If you happen to own the Amazon Echo and also happen to have a Fire Tablet sitting around, then you have an update for the tablet that has either arrived or soon will. Version 5.3.2 brings a very interesting feature that many users have been clamoring for.
This update rolls Alexa into the mix, bringing voice control to the handheld device. This means you can access the Echo from anywhere in your home, even out of voice range.

SoftwareOK unveils MultiClipBoardSlots
Freeware developer SoftwareOK has released MultiClipBoardSlots, a lightweight clipboard extension for Windows.
The program extends Windows with up to ten clipboards. You’re able to copy to any slot with Ctrl+<slot number> without overwriting anything else, and paste from it with Alt+<slot number>.

How secure are online retailers?
With Black Friday, Cyber Monday and the holiday season on the horizon, many people are going to be shopping online. But how much do you trust the sites you’re dealing with?
Password management company LastPass has released a report looking at each site's password requirements, how much information they store, and how much effort they put into helping customers follow good password security practices.

Intel will complete in the AI space with its Nervana platform
Intel has announced its plans to develop artificial intelligence (AI) and the chipmaker has claimed that within the next three years it will reduce the time needed to train a deep learning model by up to 100 times.
The company's AI development will be centered around its own Intel Nervana platform that is the result of its recent acquisition of Nervana Systems. Intel purchased the deep learning startup earlier this year for over $400 million and its technology will play a key role in its efforts to pursue AI.

How businesses should respond to unplanned downtime
Today's businesses face a wave of challenges when it comes to protecting their data. Securing data in the cloud, a rise in ransomware attacks, and increases in unstructured data all make it hard to plan operations effectively and can lead to unscheduled downtime.
Cloud data protection company Arcserve, however, sees this as an opportunity for organizations to re-assess their ability to cope with problems. The company has released a report setting out five strategies to help organizations prepare for and respond to unplanned downtime.

Saving the Internet of Things (IoT)
This is my promised column on data security and the Internet of Things (IoT). The recent Dyn DDoS attack showed the IoT is going to be a huge problem as networked devices like webcams are turned into zombie hoards. Fortunately I think I may have a solution to the problem. Really.
I’m an idiot today, but back in the early 1990’s I ran a startup that built one of the Internet’s earliest Content Distribution Networks (CDN), only we didn’t call it that because the term had not yet been invented. Unlike the CDNs of today, ours wasn’t about video, it was about the daily electronic delivery of PDF editions of newspapers and magazines. Canon told us that if the New York Times, say, would make a PDF version of its daily paper, the Japanese company would give an ink jet printer to every electronic subscriber, making their money solely on replacement ink cartridge sales. Communication would be between the CDN and printer with no PC involved. It was effectively an Internet of Things, circa 1994. Obviously, we failed, but learned a lot along the way.

Apple launches battery replacement program for iPhone 6s handsets with shutdown problems
Apple has launched its second repair program in quick succession, this time focusing on iPhone 6s handsets that suffer unexpected shutdowns. The program will see batteries replaced in a number of affected phones.
The battery replacement program comes hot on the heels of a repair program for iPhone 6Plus handsets afflicted with 'touch disease'. Apple stresses that the battery problems are not a safety issue such as seen with the Samsung Galaxy Note7, and advises customers with problematic handsets how to get a repair.

What you need to know about supply chain management
Supply chain management (SCM) is a vitally important business feature for many industries, having an impact on every aspect of the supply chain, from supplier to customer. Every detail of this process must be managed carefully, as even the smallest mistake could lead to delays, customer frustration and lost revenue.
What’s more, supply chain management does not only refer to the movement of physical products through the supply chain. Any data associated with these products, including invoices, schedules and delivery information, also needs to be managed appropriately to ensure that businesses have visibility and clarity across the length of the supply chain. When employed effectively, SCM can help reduce stock levels, boost transaction volume and increase revenue, which is why many businesses are now looking at software solutions in order to gain a competitive edge.

Samsung says batteries in the Galaxy S7 family are safe
Following on from the Note7 battery farce, Samsung is understandably keen to reassure customers -- and would be customers -- that its other phones are safe. Having lost untold billions of dollars because of exploding Note7s, the Korean company has taken the strange move of advising people that the Galaxy S7 family is safe.
In a weirdly proactive post in the Samsung Newsroom, the company points out that there have been no instances of internal battery failure in these devices. It does concede, however, that there have been instances of battery failure following external damage.

How will Facebook fight the fake news phenomenon? Poorly... and stupid, lazy users don't help
Facebook has many problems, but the most recent and prominent of them has been the issue of fake news. So serious is the problem, that some have blamed fake news stories on Facebook as being the reason Donald Trump is now president elect.
Mark Zuckerberg has made it fairly clear he doesn't subscribe to this particular idea, but he is certainly aware that fake news is a problem. Under pressure to do something about it -- bearing in mind that for a worrying percentage of people, Facebook is their only source of news -- Zuckerberg wants to not only make it clear that "we take misinformation seriously", but also that there are plans to tackle the problem. But they're not very good.

Sysinternals ships Sysmon 5.0, Process Explorer 16.20
Microsoft Sysinternals has released updates for some of its best tools, including Sysmon 5.0 and Process Explorer 16.20.
Sysmon gets a major update, with new support for recording file creations, Registry create and delete options, value sets and key and value renames.
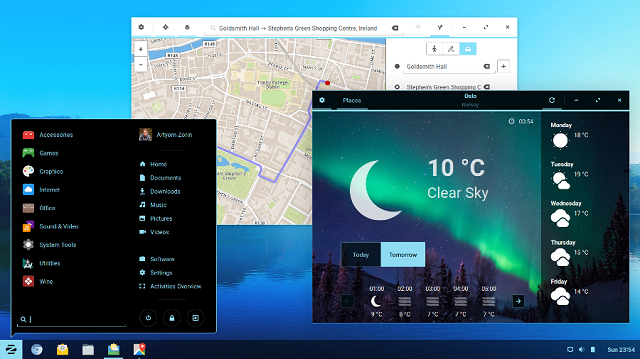
Zorin OS 12 Ubuntu-based Linux distribution now available -- a Windows 10 alternative
Windows 10 is a really great desktop operating system, but it is not for everyone. For those that care deeply about security and privacy, an open source Linux-based operating system is a wise alternative. The problem? Learning a new user interface can be hard for some. If you have always used a Windows OS in the past, moving to a desktop environment like GNOME or Unity can be confusing and scary.
Luckily, for those that have difficulty with change, there are some Linux-based operating systems that are designed for Windows-switchers. One fairly popular such offering, Zorin OS, has now reached version 12. It is designed to be familiar to former users of Microsoft's OS. While the company does charge for an "Ultimate" version, the "Core" edition of Zorin OS 12 is entirely free.

Prevent forced system shutdowns and restarts with shutdownblocker
Shutdownblocker is a simple tool which intercepts and blocks shutdown, restart, logoff and related commands.
The program offers some protection from user mistakes or poorly designed software which forces a restart, as well as preventing forced Windows 10 Update restarts.


