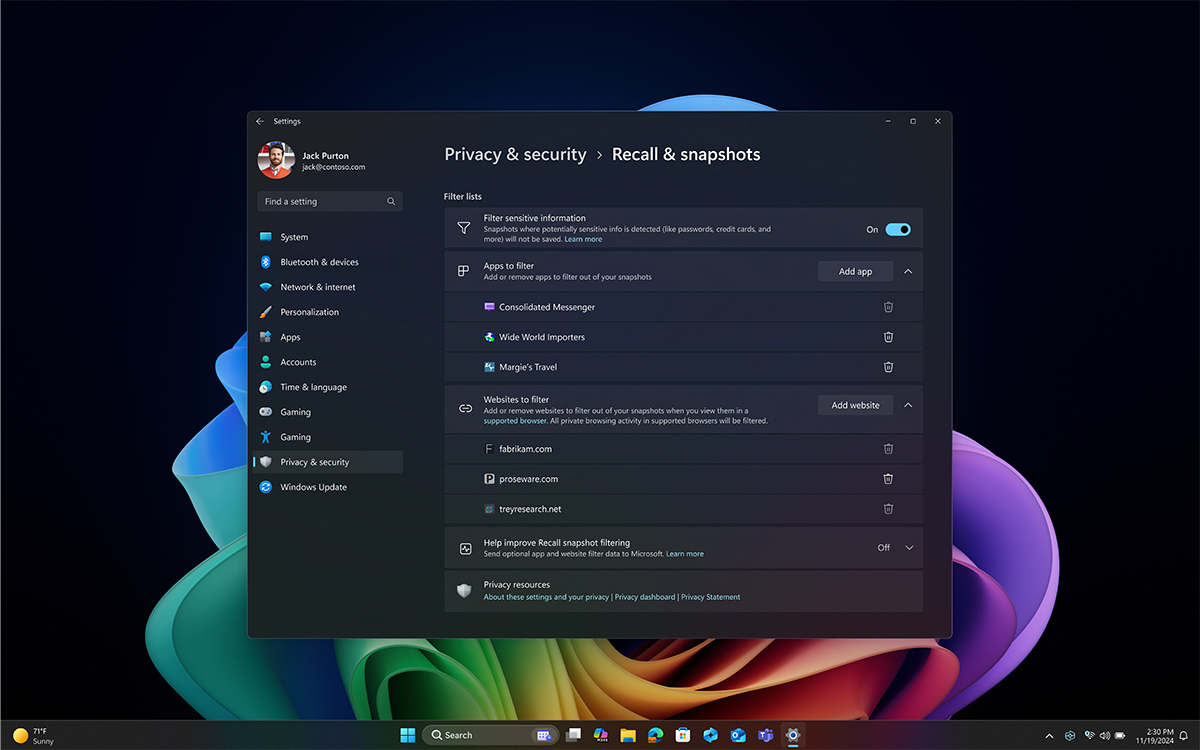
'One of the most secure experiences we have ever built' -- Microsoft overhauls controversial Recall feature with enhanced privacy and security controls
It’s fair to say Microsoft’s Recall feature for Copilot+ PCs proved to be incredibly divisive when the company announced it earlier this year. The tool is designed to retrieve and summarize relevant information from your past interactions, documents, and apps, providing quick context and insights.
Recall works by taking “snapshots” of your screen at regular intervals and storing them either locally on your device or synced through Microsoft 365. Users can search these snapshots using natural language to locate specific content, such as images or text they've viewed on their PC. While some users praise the feature's convenience, others have raised concerns about privacy and data security due to the extensive integration required for Recall to function effectively. Companies concerned with safeguarding sensitive data are understandably the most wary.
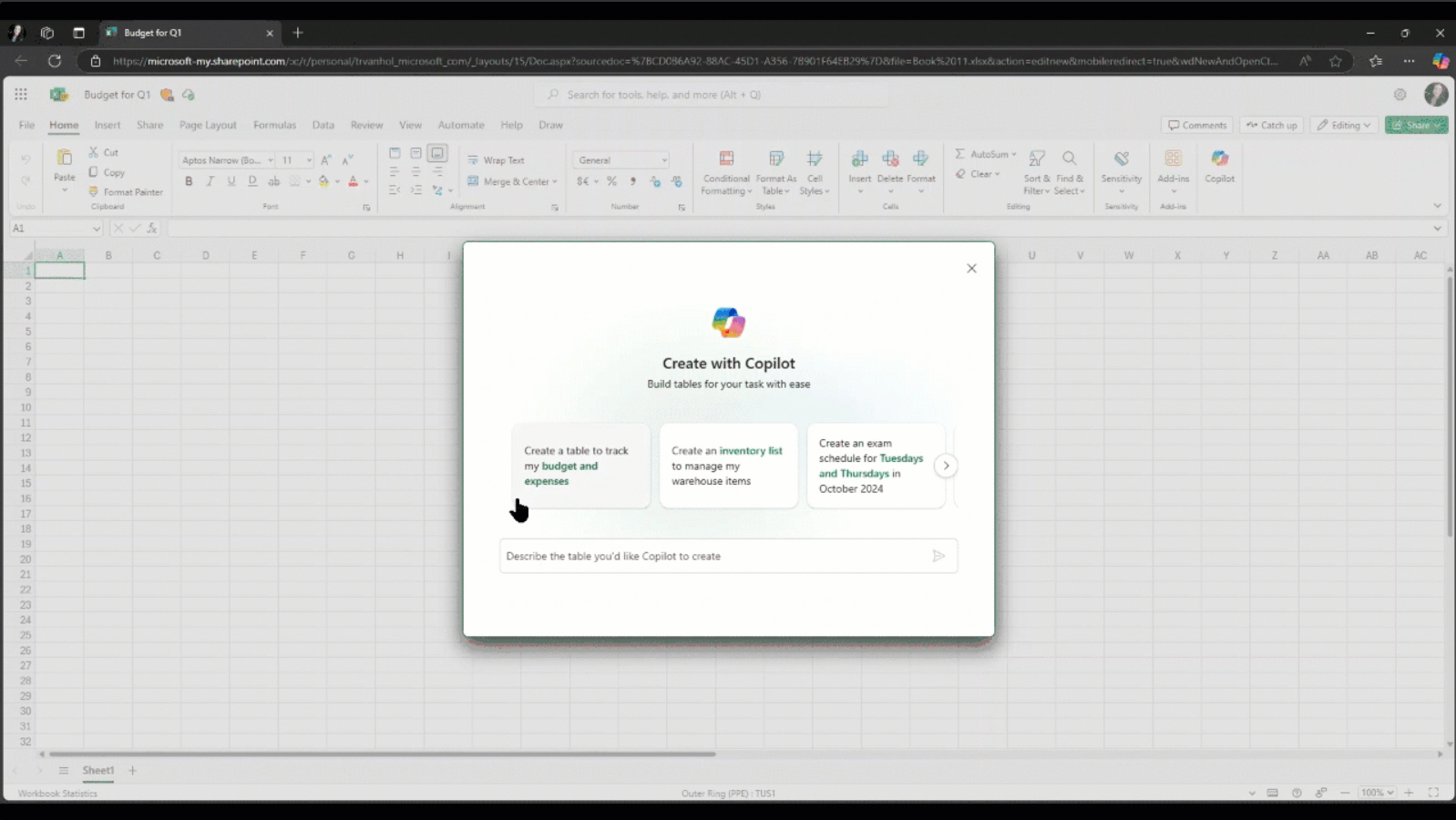
Microsoft brings AI-powered Copilot features to Excel, PowerPoint, Outlook, and more
At its Ignite 2024 conference, Microsoft today introduced a raft of new features for Copilot, its AI assistant. These include AI agents in Microsoft 365 that can take on unique roles, and Copilot Actions that let users delegate repetitive tasks.
For many people, however, the most exciting updates will likely be the new AI tools for creating custom content and managing tasks more efficiently in Microsoft 365 which are being introduced to Excel, PowerPoint, Outlook, and OneNote.

Use of GenAI in development raises security concerns
Most developers (85 percent) and security teams (75 percent) have security concerns over relying on GenAI to develop software.
A report from Legit Security, based on a survey of over 400 security professionals and software developers across North America, finds 96 percent of security and software development professionals report that their companies use GenAI-based solutions for building or delivering applications.

Businesses taking longer to recover from cyber incidents
In 2024, businesses have reported taking an average of 7.3 months to recover from cybersecurity breaches -- 25 percent longer than expected and over a month past the anticipated timeline of 5.9 months.
This is among the findings of the latest Global Security Research Report from Fastly which also shows that recovery times are even worse for companies that planned on cutting back cybersecurity spending. They faced an average of 68 incidents each -- 70 percent above the average -- and their recovery times stretched to 10.9 months.

Corsair introduces K65 Plus Wireless keyboard and M75 Wireless mouse in new Mac-friendly colors
Corsair has announced new Glacier Blue and Frost color options for its K65 Plus Wireless keyboard ($179.95) and M75 Wireless mouse ($129.95), designed specifically for Mac users. Both products are now available at Apple Store Online, with the Frost version also available in U.S. Apple Store locations and Glacier Blue expected soon.
“We are thrilled to bring Corsair high-performance input devices in exclusive and fun new colors to Mac users,” said Thi La, President and COO of Corsair. “Purpose-built for gaming and productivity on Mac, everyone from students, creators, businesses and more are going to love them. The K65 Plus Wireless Keyboard and the M75 Wireless Mouse truly are the perfect blend of Apple aesthetics and performance.”

The future of facilities management software [Q&A]
The facilities management sector is in the midst of a digital evolution, driven by trends such as sustainability and smart buildings, and there are also increased regulatory demands in the mix.
We spoke to Phil Meyers, CEO of mpro5, to discuss what this means for facilities management software providers.

Tiny11core maker updated to support Windows 11 24H2
For fans of debloating Windows, Tiny11 has been a godsend. The free utility has made it possible to debloat Windows 11 and shrink the installation footprint of the operating system far beyond what many people thought possible.
Now there is a new version of the decrapifier available, updated with full support for the recently released Windows 11 24H2.

Linux 6.12 officially released
Linus Torvalds has officially released Linux 6.12, confirming that the last week of development went as planned, allowing the project to stick to its typical release schedule. Torvalds mentioned that the merge window for the next development phase is opening, and he acknowledged the developers who submitted their pull requests early. He asked users to test this release to ensure no unnoticed issues remain before integrating further changes.
Linux 6.12 is packed with fixes and refinements aimed at improving stability and performance. While there are no major overhauls in this version, it does bring a substantial number of changes spread across different areas of the kernel. Developers worked on CPU architectures, GPU drivers, network functionalities, and memory management to address various bugs and make minor improvements.

McAfee reports rise in AI scams and deepfake threats for holiday shoppers
McAfee has released its 2024 Global Holiday Shopping Scams Study, providing insight into how AI-driven scams and deepfake technology are increasingly affecting shoppers during the holiday season. The research highlights that these advanced scams are becoming harder to identify, causing many consumers to change their shopping behavior to avoid potential risks.
The study surveyed 7,128 adults across seven countries, including the U.S., Australia, India, the UK, France, Germany, and Japan, and was conducted online in November 2024.

Meet Daisy, the AI granny designed to waste scammers' time
We all know how frustrating it can be to get scam phone calls, whether they're pretending to be your bank or trying to claim your computer needs fixing.
Of course it can be fun to keep them talking and string them along for a while, but most of us don't have the time to do that. Now though UK telco Virgin Media O2 has created an AI pensioner specifically designed to waste the scammers' time so we don't have to.

TEAMGROUP announces T-CREATE EXPERT P32 desktop external SSD
Content creators know that handling massive amounts of data is part of the job. TEAMGROUP’s creator-focused brand, T-CREATE, is addressing this need with its new T-CREATE EXPERT P32 desktop external SSD.
Offered in both 8TB and 16TB variants, the T-CREATE EXPERT P32 provides a welcome solution for expanding storage for videos, photos, and other essential files. The USB 3.2 Gen2x2 Type-C interface supports up to 1,800 MB/s speeds and works with both USB Type-C and Thunderbolt devices. However, while those speeds are nothing to scoff at, it’s worth noting that there are faster drives on the market offering superior performance.
Best Windows apps this week
Six-hundred-twenty-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft removed Actions from the Microsoft Store. Actions replicated the instant gaming feature of mobile operating systems. In other words, it allowed you to play some games directly without installation.

How enterprises can maximize the value of automation [Q&A]
The idea of automating processes has of course been around since the industrial revolution. But even though we've moved on from the Spinning Jenny to artificial intelligence, automation has lost none of its importance.
So how can enterprises ensure that get the most from their automation in today’s complex world? Devin Gharibian-Saki, SVP of strategic automation at Redwood Software, believes that part of the key is to have an automation fabric. We talked to him to learn more.

You can now easily download Windows 11 ISOs for Arm-based PCs
Showing its continuing, and growing, love of Arm-based systems, Microsoft has now released an ISO image of the Arm edition of Windows 11.
In making the ISO available, Microsoft has just made life a whole lot easier for those who have embraced Arm. While it was not impossible to obtain Windows 11 for Arm previously, there were off-putting hoops to jump through, but the direct download is very welcome.

Google is making YouTube and other services delightfully free of political ads... in Europe
The nature of modern-day politics means that parties of all colors, all leanings, spend millions on advertising -- it is something that was painfully apparent during the run-up to the US presidential election. Technology firms and social media platforms are under a lot of pressure to take steps to prevent election interference, and to increase transparency.
This is something that has been playing out in Europe with regulation on Transparency and Targeting of Political Advertising (TTPA) due to come into force in the EU. With concerns about the, “operational challenges and legal uncertainties” this could lead to, Google has announced that it will not only will stop serving political advertising in the European Union, but will do so before the TTPA comes into force.


