
Microsoft Edge is the best browser for Netflix -- the only that offers 1080p on the desktop
Internet Explorer has been much-maligned over the years, and Microsoft Edge sees the Redmond company trying to shake off the shackles of the past. Its latest marketing push finds Microsoft claiming that Edge is the best desktop web browser for Netflix viewing.
The reason? In addition to claims about greater battery efficiency, Microsoft's killer blow is that Edge is the only of the main desktop browsers to support 1080p viewing. It might seem like a surprising and audacious claim, but the test bears it out. Microsoft Edge has a serious unique selling point.

Android Pay lands in Australia
In Asia, cellphones have been used as payment methods for many years. In other parts of the world, however, it is only just starting to take off thanks to smartphones. Paying for things with my iPhone and Apple Pay feels like magic to me, although I am sure many millennials are hardly impressed.
Google has been working on competing against Apple Pay with its similarly named Android Pay, and it is slowly rolling out across the globe. Today, the search-giant's phone-based payment platform officially lands in Australia.

Google Hangouts 11 update drops merged conversations, gains video messaging
Google has its fingers in lots of messaging pies, and having added SMS support to Hangouts on Android, it wasn’t long before the merging of text and chat conversations was introduced. With the release of Hangouts 11, this changes.
With the new release, merged conversations are now gone -- SMS and chats are kept separate, but you won't lose anything -- perhaps in a bid to push people to its Messenger app to take care of texts. The same release also sees the addition of a long-awaited feature: the ability to send videos in a message.

Many companies continue to rely on Windows Server 2003
It seems that the constant expert warnings that legacy software should be avoided aren’t really resonating with businesses across the world. According to a new report by Spiceworks, more than half (53 percent) of companies all over the world have at least one instance of Windows Server 2003.
That wouldn’t be much of an issue if the operating system’s EOL (end of life) date wasn’t a year ago (July 14, 2015). After that date, Microsoft has officially ceased supporting the product, stopped releasing patches and new updates, which means that companies still using Windows Server 2003 are actually putting themselves at a lot of cyber risk.

Anonymous goes to war against police brutality in the US
The hacktivist collective Anonymous has launched a new operation which is designed to fight back against police brutality in the United States.
Inspired by recent events, which have seen innocent civilians murdered by police officers, and police officers murdered in retaliation, #OpBlackFlare is Anonymous’s intriguing -- and peaceful -- response to the situation.
ZTE Axon 7 affordable Android smartphone now available for pre-order in the USA
There is a semi-disturbing trend happening in the Android market nowadays -- very affordable smartphones. Before you call me nuts, it's true there is nothing inherently wrong with a consumer saving money, but a race to the bottom can hurt the platform overall. No-name manufacturers are leveraging decent specs and selling phones at insanely low prices, making profits tough for the big-name players. If Android becomes unprofitable, why will anyone bother?
ZTE is a lesser-known company in the USA, but I wouldn't categorize them as being "no-name". Today, it announces that its Axon 7 smartphone is coming to America, and at a rather affordable price. It's a nice balance, actually, as the specs are flagship-level, while the price tag is not overly low as to cannibalize the sales of others. It is a good blueprint of what specs/pricing for Android should be. You can pre-order this beautiful and powerful smartphone starting today.

Seagate cuts 14 percent of its workforce due to declining HDD sales
Dwindling demand for physical hard drives has already led Seagate to eliminate the jobs of 1,600 employees from its global workforce of 46,000 which spans across Asia, Europe, the Middle East and the Americas.
Now, the company has announced that it is planning to cut another 6,500 jobs or 14 percent of its remaining staff. The employees who have lost their jobs will be let go over the next 12 months and Seagate will end up paying out $164 million as a result.

How businesses are missing out on data analytics
Analytics is something that many enterprises are keen to make use of, but a new report finds that many businesses are approaching it in the wrong way.
The report from decision science and big data specialist MuSigma identifies gaps and shortcomings in traditional approaches to analytics and problem solving but also highlights that a majority of senior leadership believes analytics is affecting company strategy and results in positive ways.

Pokémon Go begins its European invasion
Pokémon Go is undoubtedly the hottest mobile game at the moment. In the first week after its release it has skyrocketed to the top of the free and top grossing charts on both the App Store and Google Play in Australia, New Zealand and United States.
Pokémon Go has already reached over 10 million installs on Google Play, which is very impressive when you consider that it is officially available only in the three aforementioned countries. However, this changes today as the makers of the game just added one more market to the list.
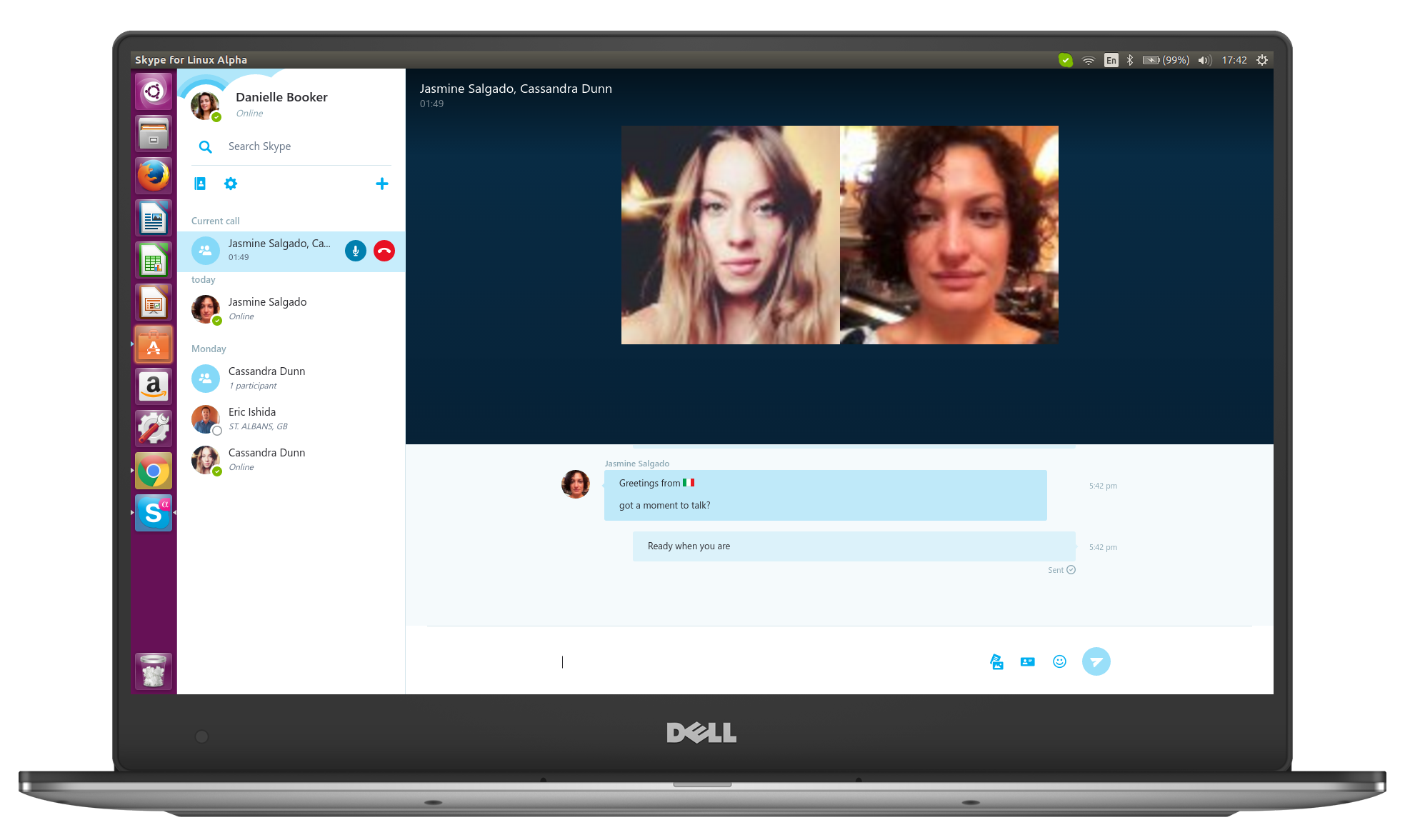
Skype returns to Linux!
For a long time I was very high on Skype. As a Windows, Linux, and iOS user, its cross-platform nature made it a dream. Unfortunately, Microsoft started neglecting the Linux desktop client, causing it to become outdated from a design perspective and not entirely functional. I assumed the Windows 10-maker simply no longer cared about Linux on the desktop.
I assumed wrong. Shockingly, Microsoft announces a new Skype client for Linux -- currently in Alpha. In other words, Skype for Linux is back, figuratively speaking. The company is pledging its support for desktop operating systems based on the open source kernel. Will Linux users embrace it?

CEO fraud scams target more than 400 businesses every day
More than 400 businesses get targeted by CEO fraud scams every day, a new report by security researchers Symantec says. CEO fraud is a type of scam in which cyber-criminals target financial staff, often posing as CEOs or other executives, and request large money transfers.
Even though it sounds too simple to work, its success rate is actually quite high, and relies mostly on putting financial staff under a lot of pressure through a sense of urgency, not giving them enough time to think things through.
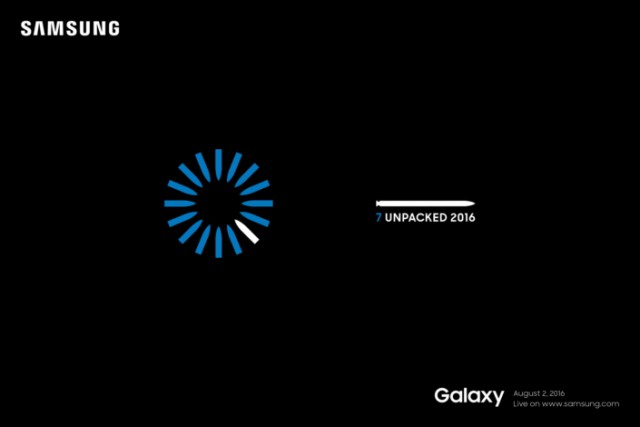
Samsung officially reveals the name, launch date of next Galaxy Note
Samsung typically launches new Galaxy Note flagships at IFA, but this year its next high-end phablet will arrive a bit sooner. The South Korean maker today announces that its second Unpacked event of 2016, which will see the latest Galaxy Note device or devices debut, will take place on August 2.
This announcement is different than what we have come to expect from Samsung, as, on top of the usual launch date, it also reveals the name of the Galaxy Note device and even hints at some of the changes that we should look forward to.

VirtualBox 5.1 promises better multi-CPU performance, wider hardware support
Oracle has released VirtualBox 5.1, a major new point release of its open-source virtual machine tool for Windows, Mac and Linux. The software enables users to run virtual PCs within a software environment.
Version 5.1 comes with the promise of improved performance, improved bug reporting and logging, wider support for different USB devices, multi-channel audio, flash storage emulation and better integration into Linux.

PC shipments continue to decline, but things are looking up
Worldwide PC shipments are still in decline, but they’re showing slow signs of recovery, according to new and preliminary market research results by Gartner. In the second quarter of 2016, 64.3 million units were shipped, equating to a 5.2 percent decline compared to a year before.
This is the seventh consecutive quarter PC shipments have been falling, but Gartner says there’s no reason to despair.

Thinking about Big Data -- Part three (the final and somewhat scary part)
In part one we learned about data and how it can be used to find knowledge or meaning. Part two explained the term Big Data and showed how it became an industry mainly in response to economic forces. This is part three, where it all has to fit together and make sense -- rueful, sometimes ironic, and occasionally frightening sense. You see our technological, business, and even social futures are being redefined right now by Big Data in ways we are only now coming to understand and may no longer be able to control.
Whether the analysis is done by a supercomputer or using a hand-written table compiled in 1665 from the Bills of Mortality, some aspects of Big Data have been with us far longer than we realize.


