
In macOS Sierra, Safari 10 will simply ignore Flash in favor of HTML5
Flash -- despite the best efforts of many -- is not quite dead. It continues to hang around like a festering scab, just waiting to be cast off forever. With macOS Sierra, Apple is playing its part in consigning Flash to the history books, pushing HTML5 to the fore.
Following in the footsteps of Google Chrome, starting with Sierra, Apple's Safari will ignore Flash even if the legacy plugin is installed. HTML5 will be favored for each and every site -- a marked difference from Chrome which maintains a list of exceptions (such as YouTube) which could still make use of Flash.

Major websites are vulnerable to advanced bots
Pretty much every top website, in retail, financial services, consumer services, OTA members (Online Trust Alliance), news and media, and top US government agencies, is vulnerable to advanced bots, new research says.
Bot detection and mitigation company Distil Networks, analyzed 1,000 top websites in these verticals, and how they behave against crude, simple, evasive and advanced bots. All of the verticals performed quite well against crude bots, (75 percent in consumer services, 70 percent in government, 65 percent in financial services, 64 percent in news and media, 78 percent in retail and 67 percent in OTA members), but when it comes to advanced bots, one percent is the best result found.

Most countries unprepared for General Data Protection Regulation
The EU's General Data Protection Regulation (GDPR) intended to strengthen data protection is due to come into force in May 2018, yet new research from content management company Metalogix shows IT professionals in many countries aren't prepared for it.
Among the top IT considerations for a cloud archiving solution, GDPR readiness ranked only fourth, named by 26 percent, behind security (79 percent), administrative control (50 percent), and service level agreements (44 percent).

Apple: Developers must use App Transport Security by 2017
Apple has announced that the deadline by which app developers must enable App Transport Security (ATS) in all apps is 1 January 2017. ATS is not a new feature of iOS 10, having been introduced in iOS 9 and it increases the security of data transferred over the web by apps.
With ATS enabled, apps are forced to use the far more secure HTTPS rather than HTTP, and this is something we've become accustomed to looking out for when browsing the web. At the moment, developers are able to disable ATS, but from the end of the year this will no longer be possible.

New solution helps enterprises keep track of data
Data growth presents a number of problems for enterprises. Aside from the obvious ones like the need for extra storage, there's the risk that employees often unwittingly store sensitive data in unsafe locations within local and network storage, professional email accounts and the cloud.
Security software company Ground Labs is launching a new data discovery solution that scans for 100 different data points and personally identifiable information (PII), so organizations can protect critical information at every endpoint without relying on traditional perimeter security methods.

Why is Microsoft buying LinkedIn? [Q&A]
Major tech companies rarely manage to surprise us, but Microsoft did it earlier this week when it announced the acquisition of LinkedIn. The software giant is spending an enormous sum -- $26.2 billion, to be exact -- to get its hands on the popular business-focused social network. The new Microsoft likes to take chances, and this high-profile purchase is certainly proof of that.
CEO Satya Nadella says that buying LinkedIn will allow Microsoft to "change the way the world works", but what is its motivation behind the purchase, how does it tie into its current strategy, and what do the two companies stand to gain from it?

Retailers aren't spending on the right areas to protect data
The retail sector has been the subject of some of the most high profile data breaches in recent years. Add to this the willingness of customers to switch allegiance in the event of a breach and it's clear the industry needs to take security seriously.
A new survey from enterprise data protection specialist Vormetric in conjunction with 451 Research focuses on retail companies, detailing IT security spending plans, perceptions of threats to data, rates of data breach failures and data security stances.
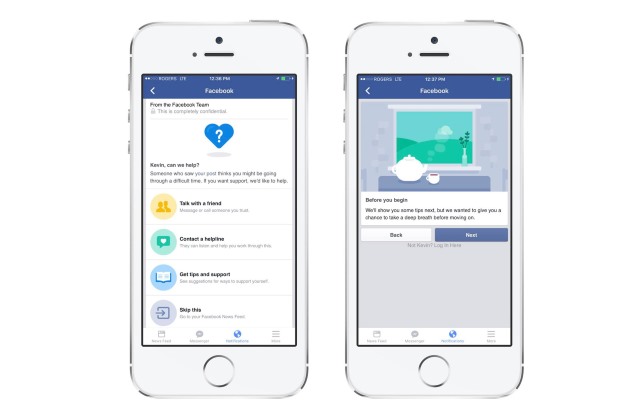
Facebook rolls out suicide prevention tools around the world
Facebook has announced that an updated batch of suicide prevention tools are being rolled out globally. It's a feature that has been available in some parts of the English-speaking world for a little while, but now the social network has decided to offer them up to everyone.
The aim is to make it easier for people to reach out to friends who they believe may be either suicidal, or at risk of self-harming. The tools have been developed in conjunction with people with experience of suicide and self-harm, as well as mental health charities. In addition to giving Facebook users the chance to reach out to those they may be concerned about, Facebook is also providing a round-the-clock worldwide team to whom concerns can be voiced.

Scan and audit your network with JDisc Discovery
JDisc Discovery is an industrial-strength network scanning, inventory and reporting tool. The program quickly checks your entire network (up to 25 devices with a free license), identifies hardware and devices, and collects details on hardware, software and device configuration.
JDisc Discovery is aimed at big business and network geeks, but its core features aren’t difficult to access. To launch your first scan, all you have to do is click a "Play" icon and watch as JDisc scans its way across your local network.

Facebook denies being pro-Brexit, but removes pro-Brexit status option anyway
In the US, Facebook has been hit with accusations of having a anti-conservative bias in its news coverage. In the UK, the social network stands accused of being pro-Brexit in the upcoming EU referendum.
The Brexit-related accusations came about after it was noticed that Facebook offered a readymade status update proclaiming to be "in favour of leaving the EU", but didn’t have a balancing pro-remain option as easily accessible. Despite this, Facebook categorically denies any form of bias.

New automation capabilities help keep IT in control of SaaS
Business IT is undergoing a major shift as many organizations get closer to adopting a fully cloud-based approach. But this means that IT departments inevitably give up some degree of control over data governance, security and overall data management.
Security automation specialist BetterCloud is launching a new automation engine called Workflows that orchestrates critical, complex processes to ensure accuracy, precision, and compliance across SaaS applications.

Napster's back! (soon)
Taking more than a little inspiration from Game of Thrones, music streaming service Rhapsody has announced a rebranding. 'Napster is coming', proclaims the Rhapsody blog. This is a name that should be very familiar, particularly to old-school pirates.
Napster is a name deeply entrenched in P2P history, but turned its back on its naughty ways following its acquisition by Roxio and then Best Buy. Five years ago, Rhapsody swallowed up Napster and now the company feels it's time to revive the name.

IT vs security pros: Handling appsec
A new report into corporate app security, conducted by runtime application security visibility and protection company Prevoty, shows significant discrepancies between IT and security professionals, when it comes to app security.
The report, entitled "The Real Root Cause of Breaches -- Security and IT Pros at Odds Over AppSec", is based on a poll of more than 1,000 IT and security professionals and says there are major divides in how these two groups handle app updates, app security tuning and backlogging.

Logitech unveils '2016 Party Collection' of mobile mice for Windows, macOS, and Linux
I recall a time when all PCs and accessories, such as mice and keyboards, only came in an ugly shade of beige. Later, black would become all the rage, but Steve Jobs and Apple broke all the rules with the iconic "Bondi Blue" iMac.
Nowadays, computers and accessories come in a cornucopia of colors an styles -- even multi-color LED lights to make them shine like a lava lamp. Today, Logitech unveils some funky mobile mice with its all-new "2016 Party Collection". Not only do they feature wild colors, but fun patterns and designs too. I rather love the flamingos!

Ubuntu 'Snap' now universal -- coming to Linux distros like Fedora, Arch, OpenSUSE, and more!
My biggest complaint about Linux based desktop operating systems is fragmentation. There are too many desktop environments, too many package managers, heck, too many distros! Not only can end-users be negatively impacted by too many choices, but more importantly, developers can be spread too thin. Ultimately, the Linux community ends up being unfocused and unable to move the desktop dial.
Today, something miraculous happens. Believe it or not, the Linux Community largely bands together to embrace Ubuntu's "Snap" packages. Yes, you are reading that correctly -- competing Linux-based operating systems like Fedora, Gentoo, Arch, and more, will utilize the now-universal "Snap," meaning Linux software can be made to install regardless of distro. This should be particularly brilliant for operating systems optimized for mobile and IoT.



