
Log PC activity in real time with Event Monitor Service
Security vendor NoVirusThanks has released Event Monitor Service (EMSvc), a Windows application which logs key system events in real time.
The package can track file creations, file deletions, PE files dropped to disk, created processes, loaded modules, loaded drivers and registry changes.

Microsoft releases Windows 10 Mobile Insider Preview Build 10586.122 -- here's what's new
While the Windows 10 Mobile roll out has yet to finally kick off, new preview builds are frequently released for users enrolled in the Windows Insider program. Microsoft is working on ironing out the kinks before unleashing its latest smartphone operating system, while trying to improve the user experience for those who have already purchased Windows 10 Mobile handsets.
And, now, early adopters are treated to Windows 10 Mobile Insider Preview Build 10586.122. This "cumulative update", which is offered in the Slow and Release Preview rings, adds support for new smartphones, a significant number of improvements to existing features and some bug fixes. Here's everything that you need to know about it.

Fake profiles on social media could become illegal
Facebook has faced a great deal of criticism over its real names policy, and a number of people have fallen foul of the rule that prevents users from assuming a pseudonym. UK law enforcement agencies are looking for ways to tackle the problem of online abuse perpetrated by trolls.
Among the suggestions put forward by the Crown Prosecution Service is that people who use fake social media accounts to harass and abuse others should be prosecuted. The proposals would normally only apply to adults, but children could be hit by the legislation in certain circumstances as well.
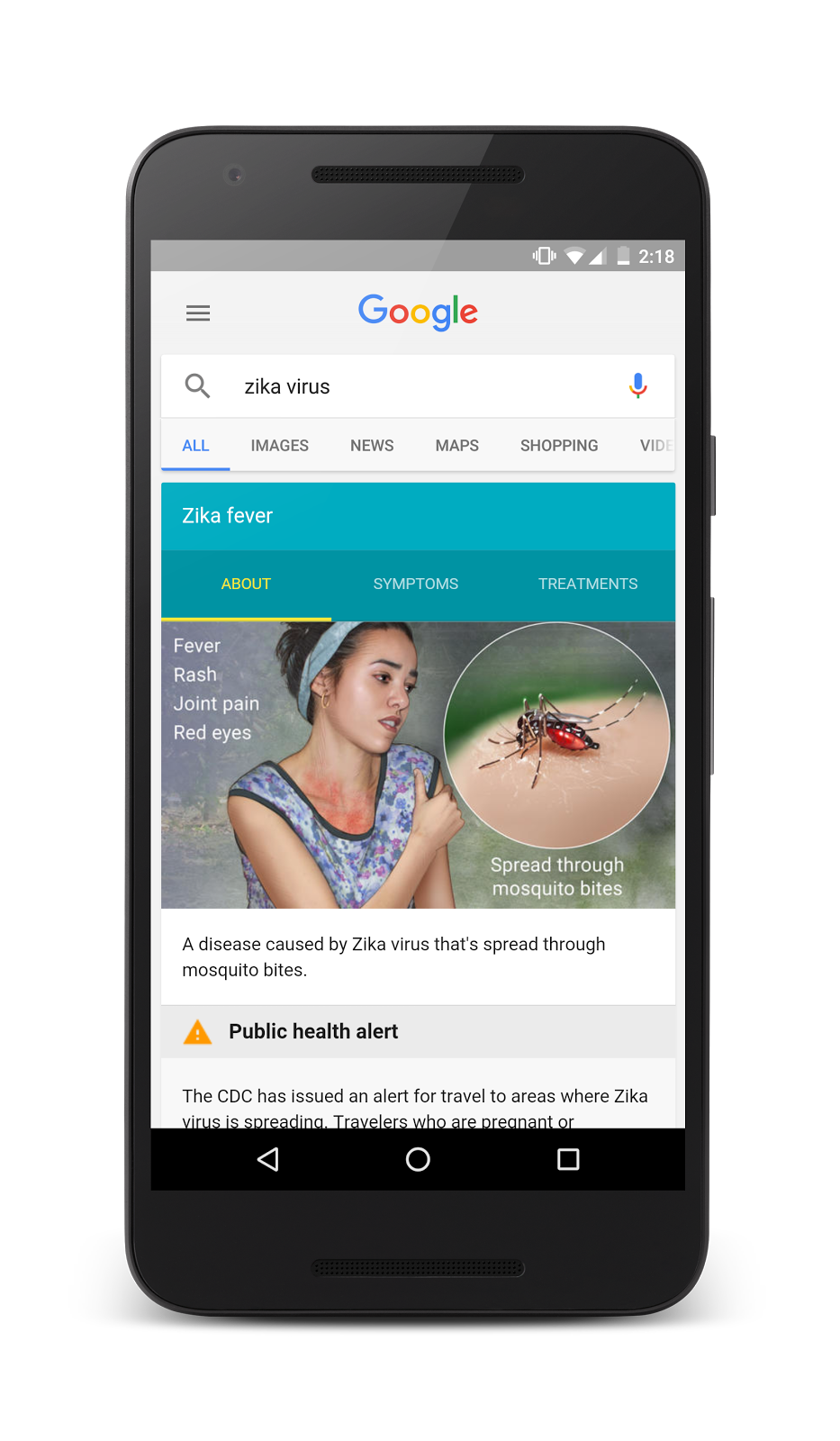
Google fights Zika virus with open source
Friends and colleagues often tell me I am a bit of a hypochondriac. As soon as a virus makes its way to the news, I am convinced I have it. Hell, I even bought respiratory face masks from Amazon in case Ebola somehow spread to Long Island! Ultimately, I end up looking foolish -- my fears were for naught.
The Zika virus has me worried, however, and this time, sadly, my fears are warranted. Carried by mosquitoes, the virus itself is usually fairly harmless to the infected, but can spread globally. The true devastation caused by Zika is birth defects for babies, such as microcephaly, caused by virus-infected mothers. Luckily, Google is working to fight the Zika virus by contributing money and resources and, more good news, the resulting platform will be open source.

Twitter to help UK prosecutors fight revenge porn and online abuse
Twitter has long-battled trolls and after launching various tools to help combat abuse, the social network is lending its support to the Crown Prosecution Service (CPS) in the UK. The social network is to work with prosecutors to provide training that will help the CPS to fight revenge porn, stalking and other forms of online abuse.
The move comes after a marked increase in the use of social media to perpetrate attacks on individuals, particularly women. But while levels of technical nous have generally increased, legal services have been slow to keep up with the latest changes. With new guidelines set to be published covering the persecution of women through social media, prosecutors are ready to call on Twitter's experience.

Here are the passwords cybercriminals are most likely to use in hacking attempts
The security group Rapid7 has released a new report that may prompt some alarm from web users who are heedless when it comes to choosing their online passwords.
Instead of using the passwords that internet users are the most likely to pick, the group took a different route and examined the passwords that cybercriminals are actually trying to use to hack into a number of systems including POS systems, kiosks, and computers.

Disable Windows 10's Microsoft Consumer Experience to take control of your Start menu
Microsoft's use of the Start menu to promote 'recommended apps' is nothing new, but recent builds of the operating system take things a step further. Install Windows 10 on a new computer, or create a new user account, and you'll find that a number of extra apps -- including Candy Crush Soda Saga, Flipboard, and Twitter -- appear in the Start menu.
Getting rid of these Start menu entries is simple enough, but the Microsoft Consumer Experience feature which is used to push the apps could be used to add links to more third party apps in future. Here's what you need to do to disable the Microsoft Consumer Experience and regain control of your computer.

Samsung now shipping 15.36TB PM1633a SSD -- world's largest capacity solid state drive
Back in the 1990's, my first-ever computer came with a 4GB hard drive. At the time, this was absolutely massive -- my computer-literate friends told me I would never need a bigger drive in my lifetime. Obviously, this thinking was wrong -- 4GB is considered rather small for a flash drive nowadays. Heck, when it comes to technology, never believe anything is "good enough", or that things won't get better and faster.
Today, Samsung begins shipping an SSD that makes large HDDs looks worthless by comparison. You see, the PM1633a is the world's largest solid state drive, with a capacity of 15.36TB! No, you aren't dreaming -- this is real.

The 'free ride' of BBC iPlayer viewing is over as license fee loophole is to be closed
Watch TV in the UK -- be it through an aerial, cable, or satellite -- and you have to pay for a TV license. The official line is that you need a TV license "if you watch or record programmes as they're being shown on TV or live on an online TV service" and this has long-meant that anyone time-shifting their viewing by watching shows on BBC iPlayer have been able to do so for free. This is set to change.
Having waxed lyrical about the threat of adblockers to the web, UK culture secretary John Whittingdale turned his attention to the BBC's streaming services. He plans to close a loophole that has permitted people without a TV license to watch non-live shows on iPlayer without paying a fee and -- more importantly -- without breaking the law. He says that this is 'wrong' and wants to bring the 'free ride' to an end.

It's time to get serious about Internet of Things
The Internet of Things (IoT) is the newest technology mega-trend, according to Goldman Sachs, and it’s easy to see why. Cisco’s IoT study suggests that the number of connected devices is expected to grow to 50 billion by 2020, leading to a global economic impact of $10 trillion.
Connected devices are set to change the very fabric of the world we live and work in. However, the buzz around gadgets such as connected fridges and smart kettles being developed by consumer goods manufacturers have been a distraction from the IoT’s true potential. Indeed, research from Embarcadero Technologies revealed that just 16% of those developing IoT solutions are targeting consumers.

Adblockers 'pose a threat to the survival' of news and music websites
Is adblocking good or evil? It's a discussion that has been rumbling on for some time, and it shows no signs of going away any time soon. The reasons for blocking ads are plentiful -- privacy, speed, annoyance -- but there's no getting away from the fact that ads mean revenue, and without this income many sites simply would not exist.
The latest figure to wade into the debate is the UK culture secretary John Whittingdale. While not going as far as calling for a ban on adblockers, he says that companies such as Adblock Plus are operating "modern-day protection rackets", ultimately threatening the existence of news sites.

Unified communication tools boost productivity and satisfaction for remote workers
Cloud unified communications specialist Outsourcery says that the full potential of remote working can only be achieved if strong UC tools are in place. Skype for Business, Slack or Trello, just to name a few, are proven to boost productivity and the possibility of working from virtually anywhere, anytime, has great effects on employee satisfaction.
There have been numerous studies about the benefits of remote working, and all of them came to the same conclusion -- this is something all of us should be implementing. One of those studies was recently published by Lancaster University’s Work Foundation, which suggests that by 2017, more than half of all UK businesses will have employed flexible working at some parts of their organization.

Hack the Pentagon!
The Pentagon is to run its own big bounty program, inviting white-hat hackers to test the security of its systems. It is not intended to be a free-for-all, and would-be hackers will be vetted before being given the go-ahead -- although of course there is nothing to stop anyone from trying to breach the defenses if they feel so inclined
The 'Hack the Pentagon' initiative was launched today by Defense Secretary Ash Carter. He said "I am confident that this innovative initiative will strengthen our digital defenses and ultimately enhance our national security". It is to be a carefully managed program which will only be open to US citizens, and networks relating to particularly sensitive material and weapons will be off-limits.

WinRT PDF found to be a possible vulnerability in Edge for Windows 10
With the introduction of Windows 10, Microsoft said goodbye to Internet Explorer, the aging Netscape killer, and hello to Edge. While the company has been increasingly vigilant about security and the nightmares of IE 6 have slowly faded away, with a new browser comes with the potential for new problems.
Security researcher Mark Yason of IBM thinks he may have found a potential path to attack. Yason plans to demonstrate the flaw at the upcoming RSA USA 2016 conference.

Hey, ladies! Google and the United Nations are celebrating your voices on YouTube
Regardless of sex or gender, everyone deserves to be heard. Nothing is more frustrating than feeling powerless and unimportant. By having an outlet to express yourself, you can gain self esteem, and ultimately, grow as a person.
Unfortunately, one of the most oppressed groups throughout history, women, have sometimes been made to feel powerless. They often make less money than men in the workforce, and frequently have to deal with sexual harassment and 'mansplaining'. Things can get even worse than that, including violence. Luckily, services such as YouTube can give voices to women that may not be heard otherwise, and today, Google is celebrating that fact.



