
Apple's CloudKit gets server API
Apple has made CloudKit much more appealing to developers by adding a server-side API to its framework. This will allow them to add much more functionality to apps that are powered by the service and to utilize it even when users have not interacted with iOS, Mac, or web apps.
Previously, CloudKit interaction was limited to the APIs that Apple provided in apps. It was useful for developers but did not give them the opportunity to implement more advanced features. Today’s modern apps make use of servers to perform tasks and collect information when a user is not using the app. With CloudKit’s new web API, developers can add these more advanced features into their apps using Apple’s tools instead of having to rely on third party services to do so.

New platform helps techies discover their market value
Not everyone is on the lookout for a new job, but it's always interesting to know what opportunities are available and what your worth might be.
San Francisco-based Woo is launching its platform for letting tech talent gauge their market value and find potential opportunities.
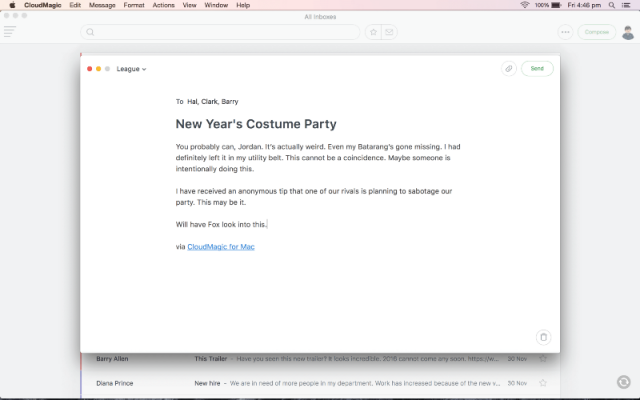
CloudMagic is a great cross-platform email app [Review]
Finding an email app that I can enjoy using has proven to be quite a challenge. I want an app that is available on multiple platforms, that works on smartphones, tablets and PCs equally well. I also want it to support all my favorite email services, and make it easy for me to sort all my messages quickly. Sounds simple, right?
Those are not outrageous requirements, yet, until recently, the only app that came close was Outlook. However, it is far from perfect, as it lacks an OS X version -- which forces me to either use a different app on my Mac or turn to the browser -- and it also has some usability issues, depending on the platform or the provider I am using. I said until recently because I now find CloudMagic to be a superior option.

Covertly monitor PCs and Macs with ActivTrak
ActivTrak is a professional cloud-managed service which can help you covertly monitor activity on PCs and Macs.
The system is extremely easy to set up, very difficult for others to spot, and provides a range of usage reports which you can access from anywhere.

US employees waste 30 percent of their work week on status meetings
Meetings are often seen as one of the great time wasters of the workplace. A new survey from business collaboration specialist Clarizen suggests that this is more than just supposition.
It reveals that US workers spend on average 11.8 hours per week preparing for and attending staus meetings. Assuming a 40 hour working week this means they could be wasting up to 30 percent of their time on them.

Google enables peer-to-peer support in Hangouts to improve call quality
Call quality and speed issues often make it difficult for users to fully embrace video and audio calling over the internet. To help solve this, Google has updated its video and audio communications service Hangouts by allowing peer to peer (P2P) connections for some users.
By incorporating this functionality into the back-end of its service the company expects call quality and the overall experience of its users to improve.

Cato Cloud aims to simplify network security
The growth of distributed enterprise networks and changes in traffic patterns as data moves to the cloud has presented companies with problems in ensuring that all of their information and endpoints are properly protected.
To address this, Israeli company Cato Networks is launching its new network security as a service (NSaaS) platform. Cato Cloud is aimed at making network security simple and cost-effective for the distributed, cloud-centric and mobile-first enterprise.

IT graduates are in high demand in UK
IT graduates are among the most sought after in the United Kingdom, a new report by CV-Library says.
CV-Library, an independent job site, says that the country grapples with the challenge of an impending skills shortage -- there were a total of 893 IT jobs for graduates in January 2016 alone. These jobs were the third most numerous, right behind education (1,139 jobs) and engineering (1,204 jobs).
Comcast partners with WeatherBug to help Xfinity customers with energy usage
Given the rising costs and environmental dangers of energy consumption, people are becoming increasingly concerned. There are a number of options coming onto the market that allow customers to monitor energy usage, a market created by climate change and a desire for cost savings.
Comcast is also in this game with its Xfinity Home offering, a service which allows for monitoring home automation, energy usage and home security. Now the company is partnering with Earth Networks' WeatherBug Home to improve its overall service.

What's really behind iPhone Error 53 -- and how can you fix it?
If you have an interest in Apple, or smartphones in general -- or even if you just follow tech news -- you can't help but have heard about the Error 53 problem that's affecting some iPhone users. In short, it seemed that people who had used non-authorized repairers to fix their home button ended up with a bricked phone after installing the latest iOS update.
This led to vocal outcries from not just upset iPhone owners, but also the tech community as a whole. Apple responded by saying that Error 53 was to "protect our customers", but what’s the real story? Is Apple really penalizing people who don’t take their iPhone to an Apple Store for repair? And, more importantly, what can you do if your iPhone has been bricked by Error 53?

Mark Zuckerberg is 'disappointed' at India Free Basics ban and vows to fight on
Facebook was dealt a blow today when its Free Basics program was banned in India for contravening net neutrality rules. As you would expect, Mark Zuckerberg is more than a little disappointed, but the Facebook founder says he remains "committed to keep working to break down barriers to connectivity in India and around the world".
In a somewhat bitter-sounding post on Facebook, Zuckerberg reiterated his belief that "everyone in the world should have access to the internet". But as well as hitting out at the Telecom Regulatory Authority of India (TRAI), he also says he wants to keep driving to connect the whole of India to the internet to "help lift people out of poverty, create millions of jobs and spread education opportunities".

Safer Internet Day: Earn yourself an extra 2GB of Google Drive cloud storage for free
It's hard -- although admittedly not impossible -- to have too much cloud storage space. It's possible that you were hit by the loss of Google Drive bonus storage last year, but now you have a chance to claw back an extra 2GB of space free of charge.
To celebrate, or perhaps promote, Safer Internet Day (what's that? 9 February is devoid of such a reminder in your calendar?!) Google is inviting people to perform a Security Check-up. It takes just a matter of moments, but as a reward for your time, you can bag yourself some extra space.

Online banking: How secure is it?
The latest bank in the UK to fall victim to a distributed denial of service (DDoS) attack was HSBC. It claimed that no customer data was compromised. In July last year, RBS and NatWest were also hit by DDoS attacks, which flooded their websites with traffic, temporarily shutting them down. This resulted in bad publicity and complaints from many customers. Fortunately, customer accounts were not compromised so the bad publicity was all the damage the attack caused.
DDoS attacks, where bad guys flood a website with so much work that they fold under the pressure, aren’t even strictly a security issue on their own. Unless the DDoS is part of a recipe to steal stuff, it’s a nuisance that is more about someone flexing their muscles than doing damage. Luckily in the cases of RBS, NatWest, and HSBC, no data was stolen; however, they do raise the question of whether online banking is secure. So is there a security issue at hand?

Energy industry is not prepared for cyber attacks
The energy industry is mostly unprepared for cyber-threats, a new study by Tripwire suggests.
The global provider of advanced threat, security and compliance solutions announced these results in a study conducted for it by Dimensional Research. The study looked at cyber-security challenges faced by organizations in the energy sectors, and includes answers from more than 150 IT professionals.

SSuite NoteBook Editor: not just another WordPad replacement
If you’ve tried your share of WordPad replacements then you’ll know they’re usually identikit me-too products with barely any interesting ideas of their own.
SSuite NoteBook Editor is a rare exception which manages to bring something a little more original to the standard text editing feature list.


