
Google unveils Fitbit Ace LTE smartwatch for kids
In an era where parents grapple with balancing their children's independence with safety, Google steps in with a solution—the Fitbit Ace LTE. This new device is designed for kids aged 7 and older and marks Fitbit's latest foray into youth-oriented products. The Ace LTE is not just a tool for tracking physical activity but also a connected smartwatch that incorporates safety features such as reliable calling, messaging, and location sharing.
The Ace LTE aims to make physical activity enjoyable by merging exercise with digital play. It offers interactive 3D games that encourage kids to move more to unlock playtime. Utilizing the smartwatch's built-in features like haptics, sounds, and an accelerometer, these games create a captivating experience for young users. Kids can enjoy a variety of games, such as racing through space as a chicken in a bathtub or fishing at "Smokey Lake."

Tens of thousands of websites vulnerable to data breaches
Over 58,000 unique websites from around the world are vulnerable to data breaches and even complete takeovers according to new research.
The Cybernews research team has investigated publicly exposed environment files (.env) that should be kept private and protected at all costs. These files hold passwords, API keys, and other secrets that websites need to access databases, mail servers, payment processors, content management systems, and various other services.

Why cloud attacks no longer need malware [Q&A]
As organizations have come to rely more on the cloud, it's become an increasingly attractive target for cybercriminals seeking to steal data or extract ransoms.
In the past this has involved the use of malware, but as attackers get more sophisticated there’s a move towards different types of attack. We spoke to Shai Morag, SVP and general manager cloud security at Tenable, to discover more about these threats and how to tackle them.

Logitech announces MeetUp 2: AI-powered conference camera
Logitech has revealed the upcoming release of MeetUp 2, an AI-enhanced USB conference camera tailored for bring-your-own-device (BYOD) and PC-based setups in huddle and small meeting rooms. Building on the success of its predecessor, the best-selling Logitech MeetUp that has reached over one million units sold, this new model is set to launch in August.
Henry Levak, VP of Product at Logitech B2B, highlights the camera's innovative features, "MeetUp 2 leverages AI with RightSight 2 to create dynamic views that engage remote users effectively, alongside RightSound 2 for advanced voice equalization and noise suppression." This next-generation device also allows IT teams to monitor and update the system remotely, continually enhancing its capabilities.

Microsoft brings Copilot to Telegram
Microsoft has brought its AI-powered Copilot chatbot to the Telegram messaging platform in beta. Designed to enhance user interaction, it leverages Microsoft's GPT models and Bing Search capabilities to provide a wide array of services. These include answering queries with quick facts, offering travel advice, updating sports scores, and giving movie recommendations. Users can interact with Copilot by typing natural language commands, similar to messaging a friend.
To access Copilot, Telegram users can either follow a direct link if they are already using the Telegram app or web platform, or search for @CopilotOfficialBot in Telegram's search bar. Currently in beta, Copilot is free for all users and is available across various operating systems including Windows, macOS, Android, and iOS, as well as via web browsers.

DDoS cyber-attack targeting Internet Archive and the Wayback Machine
The DDoS cyber-attack currently targeting the Internet Archive and its Wayback Machine has entered its third day, causing intermittent disruptions in service. The nonprofit research library is best known for housing millions of historical documents, preserved websites, and media content.
The ongoing intrusion has involved the launch of tens of thousands of fake information requests per second, though the source of the attack remains unknown.

Microsoft Start Weather blows away the competition with AI-powered forecast accuracy
Microsoft Start Weather has been recognized as the “overall most accurate weather forecast provider globally” by ForecastWatch for the second consecutive year, relying on AI technology for enhanced forecasting accuracy.
This recognition followed an independent analysis involving 22 weather services, evaluated across 13 metrics throughout 2023. Microsoft Start Weather performed notably well in accuracy for predicting temperatures and cloud cover for short-term forecasts of 1-5 days.
Opera integrates Google Cloud’s Gemini models for enhanced browser AI
Opera has revealed a strategic partnership with Google Cloud to integrate Gemini models into its Aria browser AI, marking a significant advancement in browser technology. This collaboration will see the incorporation of Google's latest and most advanced large language model, Gemini, into Opera's Aria, which is powered by the multi-LLM Composer AI engine. This engine is uniquely capable of selecting the optimal model for different user tasks, enhancing performance and user experience.
The Gemini model is celebrated for its modern, powerful capabilities and user-friendly design, and its integration is expected to boost the accuracy and speed of information delivery to Opera users. "Our companies have been cooperating for more than 20 years, and we are excited to deepen this collaboration into the field of generative AI to further power our suite of browser AI services," said Per Wetterdal, EVP of Partnerships at Opera.

New Dashlane tool warns of compromised credentials
Leaked or stolen credentials remain a major cause of security breaches and reuse of passwords between accounts only compounds the problem.
Password manager company Dashlane is launching new automated tool to empower admins to proactively create a more security-conscious workforce and drive better credential security behavior across their organization, reducing the risk of credential theft.

90 percent of enterprises experience identity-related incidents
A new study from the Identity Defined Security Alliance (IDSA) finds that 90 percent of organizations experienced an identity-related incident in the past year and 84 percent suffered a direct business impact as a result.
The survey of over 520 identity and security professionals from organizations with over 1,000 employees finds the most significant impact, seeing a measurable rise this year, is distracting from core business (52 percent).

Budget is the top barrier to cloud security objectives
A new survey shows that 59 percent of executives say budget/cost is the top roadblock to achieving their cloud security objectives, followed by complexity (47 percent) and lack of skilled resources (41 percent).
The study from Gatepoint Research for Orca Security of 200 senior decision makers also reveals that 57 percent of respondents identify misconfigurations as their top cloud security risk, followed by unauthorized access (50 percent), data breaches (35 percent), insecure APIs (31 percent), lack of visibility (29 percent), and malicious insiders (12 percent).

Google Chromebooks democratize AI, offering an affordable alternative to pricey Microsoft Windows 11 Copilot+ PCs
In an effort to democratize Artificial Intelligence, Google is significantly enhancing its Chromebook lineup with AI-driven features, making cutting-edge functionality accessible on devices that don't break the bank. This initiative positions Google as a pioneer in offering powerful AI tools on affordable hardware, contrasting sharply with competitors like Microsoft, whose recently announced Copilot+ Windows 11 PCs come with a hefty $1,000+ price tag.
Notably, new Chromebook Plus models are stepping up their game by pre-installing the Gemini feature on the app shelf, enhancing user interaction right out of the box. As part of this initiative, Google is offering a complimentary one-year subscription to the Google One AI Premium Plan, valued at $240, with every new Chromebook Plus purchase.

Get 'Unlocking the Secrets of Prompt Engineering' (worth $35.99) for FREE
Unlocking the Secrets of Prompt Engineering propels you into the world of large language models (LLMs), empowering you to create and apply prompts effectively for diverse applications, from revolutionizing content creation and chatbots to coding assistance.
Starting with the fundamentals of prompt engineering, this guide provides a solid foundation in LLM prompts, their components, and applications. Through practical examples and use cases, you'll discover how LLMs can be used for generating product descriptions, personalized emails, social media posts, and even creative writing projects like fiction and poetry.
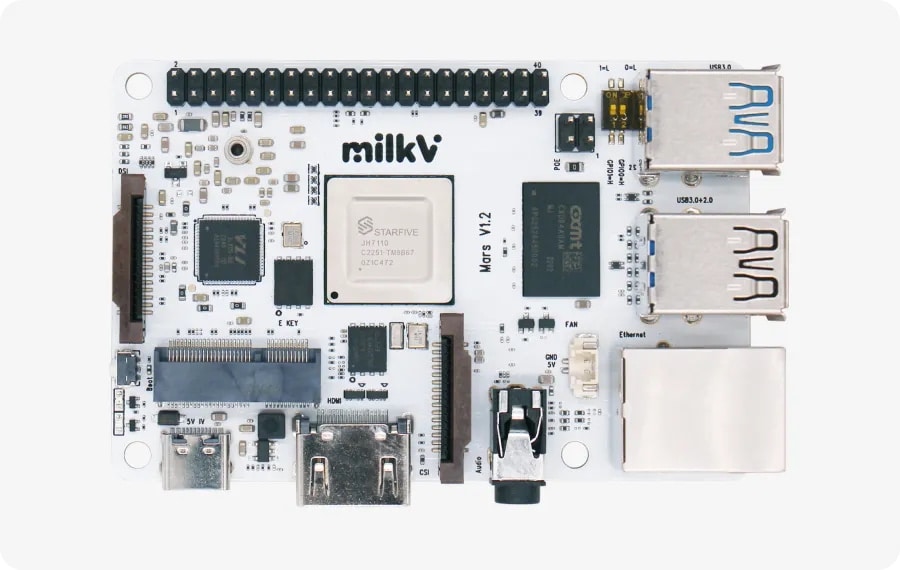
Ubuntu Linux 24.04 now optimized for Milk-V Mars RISC-V single board computer
Canonical has officially released the optimized Ubuntu 24.04 image (available here) for the Milk-V Mars, a credit-card-sized RISC-V single board computer (SBC) developed by Shenzhen MilkV Technology Co., Ltd.
The Milk-V Mars is the world’s first high-performance RISC-V SBC of its size. Powered by the StarFive JH7110 quad-core processor, the board is equipped with up to 8GB of LPDDR4 memory and supports various modern interfaces, including USB 3.0, HDMI 2.0 for 4K output, and Ethernet with PoE capabilities. It also offers comprehensive expansion options with M.2 E-Key and extensive MIPI CSI channels, making it an ideal choice for developers and tech enthusiasts.

Sabrent USB-C Enclosure for M.2 2230 PCIe NVMe SSDs simplifies upgrading Steam Deck, ASUS ROG Ally, Surface Pro 9, and more
Sabrent’s USB-C Enclosure for M.2 2230 PCIe NVMe SSDs (EC-NE30) offers a straightforward solution for handling your compact drives. Whether you need to prep an M.2 2230 SSD for your Steam Deck, ASUS ROG Ally, Surface Pro 9, or other portable gadgets, this enclosure has you covered.
How does it work? Simply insert the SSD, secure it with the latch, and connect via USB-C. This versatile enclosure is compatible with all major operating systems, including Windows, macOS, and Linux-based options, ensuring hassle-free setup with its integrated cable and plug-and-play functionality—no drivers needed.



